Twelve Linux Security Tips
- Transfer
 We live in dangerous times: almost every day new vulnerabilities are discovered, exploits are created on their basis, and an ordinary Linux home computer and a server on which a huge organization depends can be hit.
We live in dangerous times: almost every day new vulnerabilities are discovered, exploits are created on their basis, and an ordinary Linux home computer and a server on which a huge organization depends can be hit. You may pay attention to security and periodically update the system, but usually this is not enough. Therefore, today we will share twelve tips for improving the security of Linux-based systems on the example of CentOS 7.
Terminal protection
In order to increase the security of the system, you can protect console access to it by restricting the root user in the use of certain terminals. This can be done by specifying the terminals that the superuser can use in the file
/etc/securetty. It is recommended, although not necessary, to allow the superuser to log in from only one terminal, leaving the rest to other users.
Password Reminder
Nowadays, a complex password is an absolutely necessary thing. However, it is even better when passwords are regularly changed. It’s easy to forget about it, so it’s good to use some kind of system mechanism for reminders about the age of the password, and when it needs to be changed.
We offer you two ways to organize such reminders. The first is to use the command
chage, the second is to set the required default values in /etc/login.defs. The command call
chagelooks like this:$ chage -M 20 likegeeksHere we use the key
-Min order to set the expiration date for the password in days. You can use this command without keys, then it will itself offer to enter the necessary value:
$ chage likegeeksThe second way is to modify the file
/etc/login.defs. Here is an example of what the values we are interested in might look like. You can change them to the ones you need:PASS_MAX_DAYS 10
PASS_MIN_DAYS 0
PASS_WARN_AGE 3Remember that if you are playing the role of administrator, you should encourage users to use complex passwords. You can do this with pam_cracklib .
After installing this program, you can go to
/etc/pam.d/system-authand enter something like the following:password required pam_cracklib.so minlen=12 lcredit=-1 ucredit=-1 dcredit=-2 ocredit=-1Sudo notifications
The team
sudo, on the one hand, makes life easier, and on the other, it can cause Linux security problems that can lead to irreparable consequences. Settings sudoare stored in a file /etc/sudoers. Using this file, you can prevent ordinary users from running certain commands on behalf of the superuser. In addition, you can make the team sudosend an email when using it by adding the following to the above file:mailto yourname@yourdomain.comYou must also set the property
mail_alwaysto on:mail_always onSSH protection
If we are talking about Linux security, then we should also think about the SSH service. SSH is an important system service, it allows you to remotely connect to the system, and sometimes this is the only way to save the situation when something goes wrong, so we are not talking about disabling SSH.
Here we use CentOS 7, so the SSH configuration file can be found at
etc/ssh/sshd_config. Scanners or bots used by attackers try to connect to SSH using the default port 22. It is common practice to change the standard SSH port to another, unused port, for example, to
5555. The SSH port can be changed by setting the desired port number in the configuration file. For example, like this:Port 5555In addition, you can restrict SSH login to the root user by changing the parameter value
PermitRootLoginto no:PermitRootLogin noAnd, of course, it’s worth disabling password authentication and using public and private keys instead:
PasswordAuthentication no
PermitEmptyPasswords noNow let's talk about SSH timeouts. The problem of timeouts can be solved by setting some parameters. For example, the following settings imply that packets that support the connection will be automatically sent after a specified number of seconds:
ServerAliveInterval 15
ServerAliveCountMax 3
TCPKeepAlive yesBy setting these parameters, you can increase the connection time:
ClientAliveInterval 30
ClientAliveCountMax 5You can specify which users are allowed to use SSH:
AllowUsers user1 user2Permissions can also be assigned at the group level:
AllowGroup group1 group2SSH protection using Google Authenticator
For even more reliable SSH protection, you can use two-factor authentication, for example, using Google Authenticator. To do this, you must first install the appropriate program:
$ yum install google-authenticatorThen run it to verify the installation:
$ google-authenticatorYou also need the Google Authenticator app installed on your phone.
Edit the file
/etc/pam.d/sshdby adding the following to it:auth required pam_google_authenticator.soNow it remains only to report all this SSH, adding the following line to the file
/etc/ssh/sshd_config:ChallengeResponseAuthentication yesNow restart SSH:
$ systemctl restart sshdWhen you try to log in using SSH, you will be prompted for a verification code. As a result, now SSH access to your system is much better protected than before.
Monitoring file systems with Tripwire
Tripwire is a great tool for enhancing Linux security. This is an intrusion detection system (HIDS).
Tripwire's goal is to track file system activity, keep track of who changes files, and when these changes occur.
In order to install Tripwire, you need access to the EPEL repository. This is a simple task, it can be solved with the following commands:
wget http://dl.fedoraproject.org/pub/epel/7/x86_64/e/epel-release-7-9.noarch.rpm
$ rpm -ivh epel-release-7-9.noarch.rpmAfter installing the EPEL repository, you can install Tripwire:
$ sudo yum install tripwireNow create a key file:
$ tripwire-setup-keyfilesYou will be prompted to enter a complex password for the key file. After that, you can configure Tripwire by making changes to the file
/etc/tripwire/twpol.txt. It is not difficult to work with this file, since each line is equipped with a meaningful comment. When the configuration of the program is completed, it should be initialized:
$ tripwire --initThe initialization, during which the system is scanned, will take some time, depending on the size of your files.
Any modifications to protected files are regarded as intrusion, the administrator will be notified about this and he will need to restore the system using files that he does not doubt the origin of.
For this reason, necessary system changes must be confirmed by Tripwire. To do this, use the following command:
$ tripwire --checkAnd here is another recommendation regarding Tripwire. Protect files
twpol.txtand twcfg.txt. This will increase system security. Tripwire has many options and settings. You can view help on it like this:
man tripwireUsing Firewalld
Firewalld is a replacement for
iptables, this program improves the Linux network security. Firewalld allows you to make changes to settings without stopping current connections. The firewall works as a service that allows you to add and change rules without restarting and uses network zones. To find out if it is currently running
firewalld, enter the following command:$ firewall-cmd --state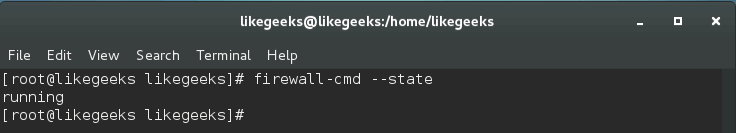
You can view the predefined network zones as follows:
$ firewall-cmd --get-zones
Each of these zones has a certain level of confidence.
This value can be updated as follows:
$ firewall-cmd --set-default-zone=You can get detailed information about a specific zone as follows:
$ firewall-cmd --zone= --list-all You can view the list of all supported services with the following command:
$ firewall-cmd --get-services
Then you can add new services to the zone or remove existing ones:
$ firewall-cmd --zone= --add-service=
$ firewall-cmd --zone= --remove-service= You can display information about all open ports in any zone:
$ firewall-cmd --zone= --list-ports You can add ports to the zone and remove them from it like this:
$ firewall-cmd --zone= --add-port=
$ firewall-cmd --zone= --remove-port= You can configure and port forwarding:
$ firewall-cmd --zone= --add-forward-port=
$ firewall-cmd --zone= --remove-forward-port= Firewalld is a very advanced tool. The most remarkable thing about it is that it can work normally, for example, when making changes to settings, without restarting or stopping the service. This distinguishes it from the means
iptableswhen working with which the service must be restarted in similar situations.Migrating from firewalld to iptables
Some prefer the firewall
iptablesthe firewall firewalld. If you use firewalld, but want to go back to iptables, doing it is quite simple. First disable
firewalld:$ systemctl disable firewalld
$ systemctl stop firewalldThen install
iptables:$ yum install iptables-services
$ touch /etc/sysconfig/iptables
$ touch /etc/sysconfig/ip6tablesNow you can start the service
iptables:$ systemctl start iptables
$ systemctl start ip6tables
$ systemctl enable iptables
$ systemctl enable ip6tablesAfter all this, restart your computer.
Compiler Limit
The attacker can compile the exploit on his computer and upload it to the server of interest to him. Naturally, with this approach, the presence of compilers on the server does not play a role. However, it is better to restrict compilers if you do not use them to work, as is the case in most modern server management systems.
To get started, list all the compiler binaries from the packages, and then set the permissions for them:
$ rpm -q --filesbypkg gcc | grep 'bin'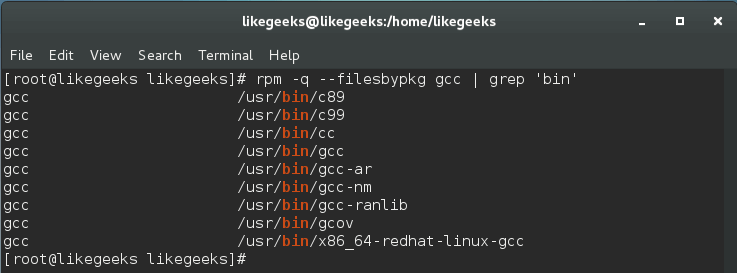
Create a new group:
$ groupadd compilerGroupThen change the compiler binary group:
$ chown root:compilerGroup /usr/bin/gccAnd one more important thing. You need to change the permissions of these binaries:
$ chmod 0750 /usr/bin/gccNow any user who tries to use
gccwill receive an error message.File Modification Prevention
Immutable files cannot be overwritten by any user, even with root privileges. The user cannot modify or delete such a file until the immunity flag is set, which can only be removed by the root user.
It is easy to notice that this feature protects you, as a superuser, from errors that can disrupt the system. Using this approach, you can protect configuration files or any other files as you wish.
To make any file immune, use the command
chattr:$ chattr +i /myscript
The immunity attribute can be removed with the following command:
$ chattr -i /myscript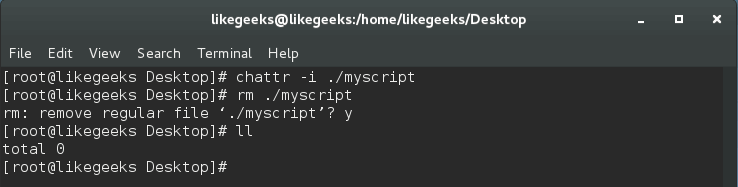
This way you can protect any files, but remember that if you processed binary system files in this way, you cannot update them until you clear the immunity flag.
Managing SELinux with aureport
Often SELinux forced access control system is turned off by default. This does not affect the performance of the system, and working with SELinux is quite difficult. However, to improve security, SELinux can be enabled, and you can simplify the management of this mechanism using
aureport. The utility
aureportallows you to create reports based on audit log files .$ aureport --avc
The list of executable files can be displayed with the following command:
$ aureport -x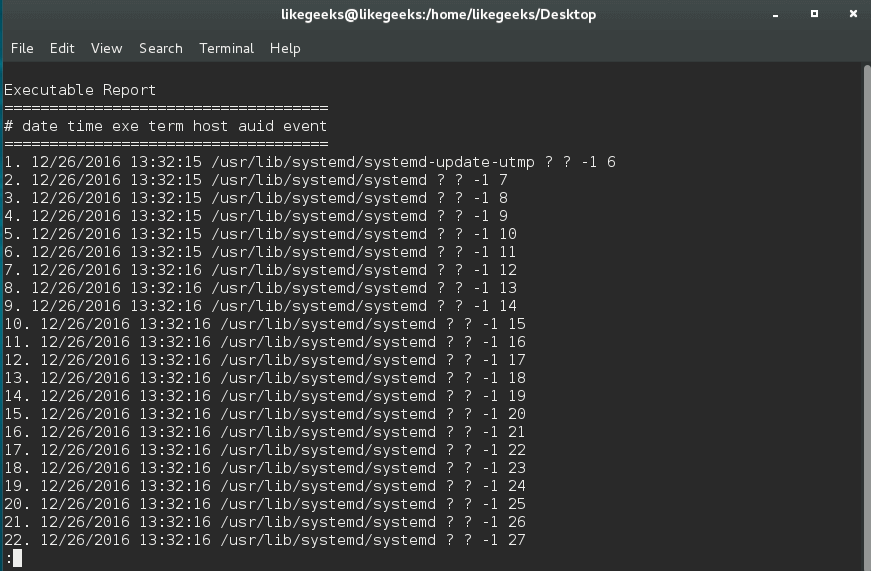
Can be used
aureportto create a full authentication report:$ aureport -au -i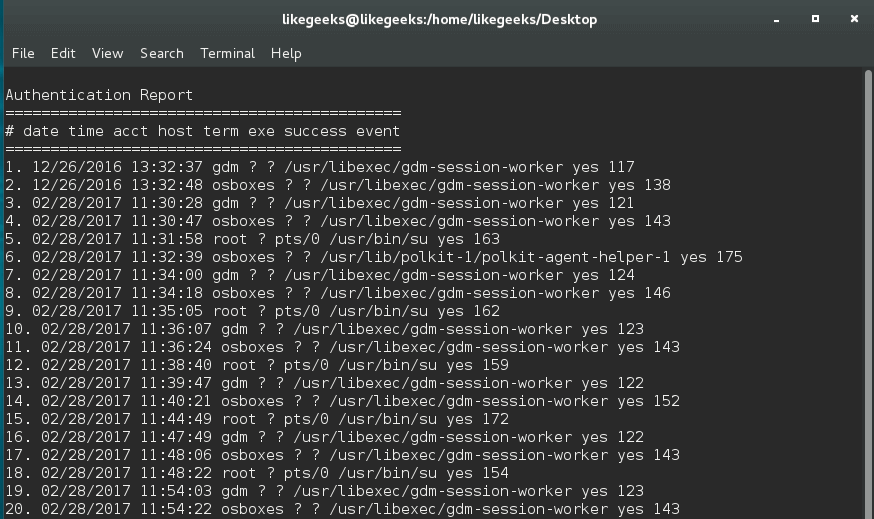
You can also display information about failed authentication attempts:
$ aureport -au --summary -i --failed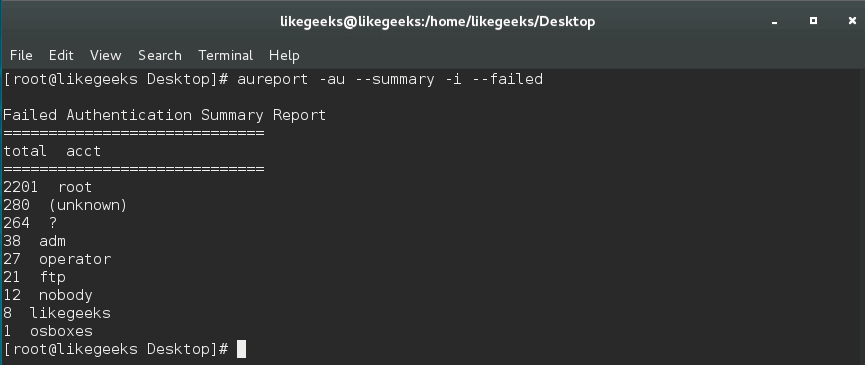
Or perhaps a summary of successful authentication attempts:
$ aureport -au --summary -i --success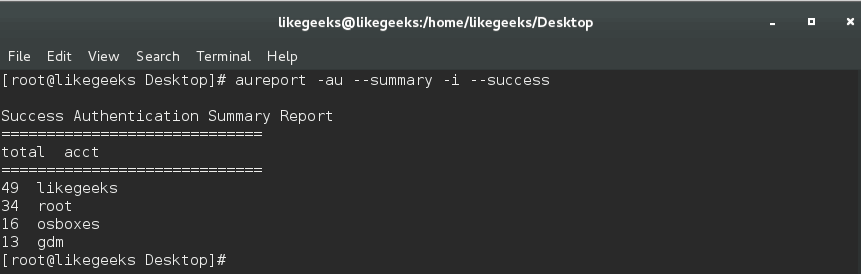
The utility
aureportgreatly simplifies the work with SELinux.Using sealert
In addition to this,
aureportyou can use the good Linux security tool called sealert. You can install it like this:$ yum install setoolsNow we have a tool that will issue alerts from the file
/var/log/audit/audit.logand give us additional information about the problems identified by SELinux. You can use it like this:
$ sealert -a /var/log/audit/audit.log
The most interesting thing here is that in the alerts you can find tips on how to solve the corresponding problems.
Summary
We hope the tips given here help you make your Linux installation safer. However, when it comes to protecting information, it is impossible, by applying certain measures, to assume that now nothing threatens you. Vigilance and caution should always be added to any security software.
Dear readers! Do you know any simple but unobvious ways to improve Linux security?
