Four months after detection, the malware Windshift for Mac is still not detected by antivirus.

Source: ASSOCIATED PRESS
In an ordinary situation, any kind of malware, after detecting one of the anti-virus companies, begins to be detected by the anti-virus software of other companies within a day or two (if not several hours). Recently it was discovered that a virus for Mac, which was found four months ago, is still not detected by antivirus software - none other than Kaspersky and ZoneAlarm.
According to information security experts, Windshift (this name was received as malware) is a project of a cybercrime group from the Middle East. About the virus was repeatedly told and written, for example, here and here .
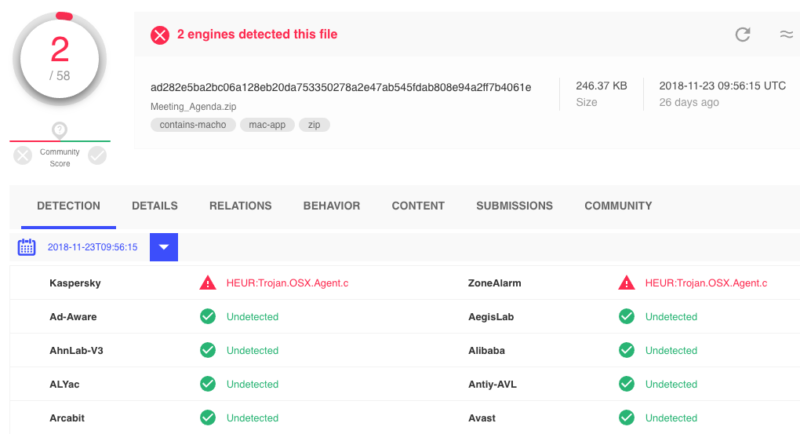
MacOS security specialist Patrick Wardle published a comprehensive analysis of the malware last week . To study the virus, the expert installed it, and immediately checked how well the antivirus systems deal with the danger. As it turned out, only Kaspersky and ZoneAlarm are “familiar” with this malware, other companies do not know anything about it.
Apple, as experts have found out, is also familiar with malware, since the digital certificates with which the software is signed are revoked (CSSMERR_TP_CERT_REVOKED). However, after checking the VirusTotal service, through which the files related to the malware were run, it turned out that they were almost not detected. In most cases, the service did not detect any problems - only two suppliers of antivirus solutions identified the presence of malware.
All this may indicate that Apple does not provide antivirus developers with definitions (definitions) of well-known malware companies. Providing this data is a common (even routine) practice in the world of antivirus software. Sharing this data helps services and antivirus software to quickly learn how to detect the presence of new malware. If no one gives information about this, then antivirus developers do not know anything about malware.
The principle of the malware itself is quite simple. Initially, phishing e-mail messages are sent to potential victims. They contain the URL of the page with the .zip file containing the malware. Once the file download is complete, the malware tries to start using a custom URL, which is not too difficult to do. During an attempt to go to this URL, the already opened page from which the malware is downloaded makes a request to install third-party software. After installation, the malware works in the system, providing a replacement for the URL of regular pages.
By the way, if the owner of the infected system is connected to the local network, then the malware automatically penetrates other devices connected to the same network.
Now the virus is almost harmless, because the servers to which it has accessed are deactivated and do not work. In addition, the latest versions of the Safari browser now show a notification if the custom URL system is enabled. And if the user even decides to continue, the Gatekeeper security feature is activated, which will let the Mac owner know that his system is trying to install some file.
Not so long ago, journalists from a number of publications tried to find out from Apple what the company did to eliminate the threat. The corporation replied that the problem has been solved and will no longer be relevant for its users. However, it is unclear what exactly was done and why Apple does not provide information about the threat to anti-virus services. It may well be that this situation is repeated with other malware, and not just Windshift, so this line of company behavior is difficult to explain in terms of caring for its users.
The exchange of data on malware between individual organizations that fight viruses is of great importance for information security. If companies did not make an exchange, the normal work of identifying dangerous evil men and their liquidation would have become impossible. Unfortunately, Apple does not provide information on how it participates in data exchange programs between anti-virus specialists. As a result, situations like this become possible.
