Attack DHCP part 3. DHCP + Apple = MiTM

In this article I will talk about how to implement MiTM of any Apple device in a WiFi network. Before reading this article, I strongly recommend that you familiarize yourself with the first and second part.
The limitations are the same:
- We must be connected to the attacked access point.
- We should be able to listen to broadcast traffic on the network.
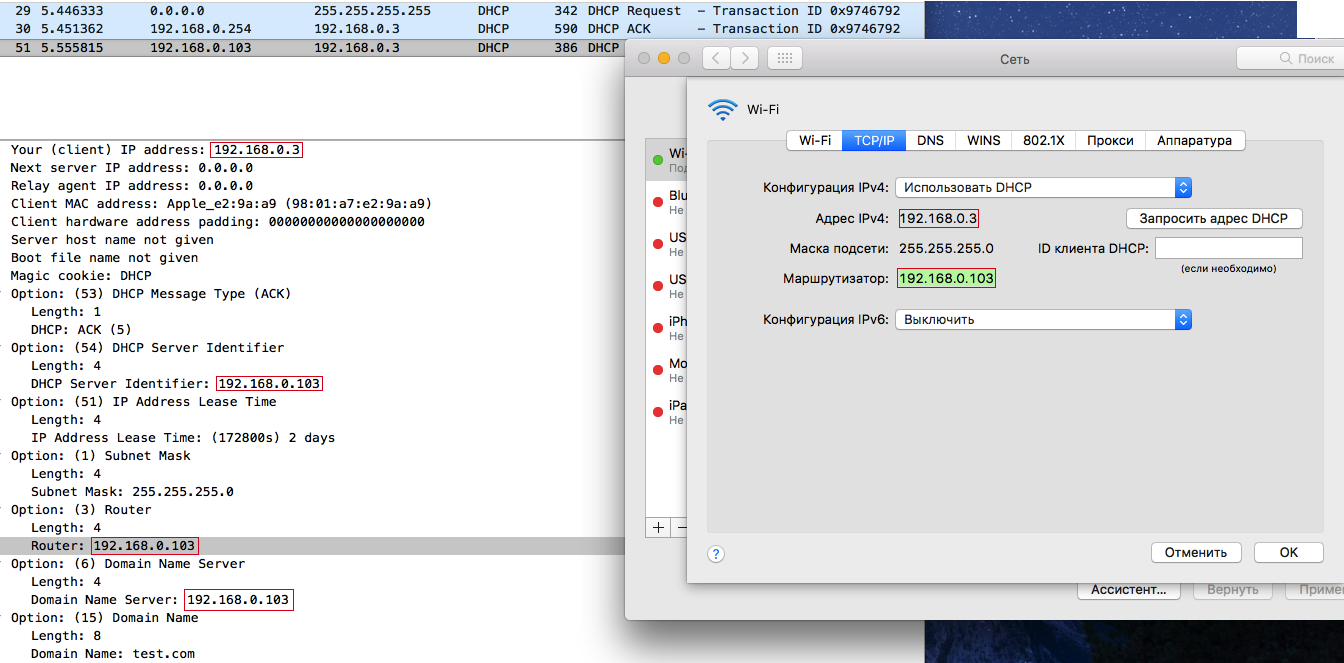
As it turned out, macOS and iOS surpassed everyone in terms of obtaining network settings via DHCP . When these operating systems send DHCPREQUEST , the DHCP server responds with DHCPACK , and they set the network settings from the server response. It seems so far everything is like everyone else:

But the problem is that the DHCPREQUEST broadcast and the attacker, as a rule, can intercept him without any special problems, extract the xid and chaddr fields from him to form the correct DHCPACK . But the attacker will send DHCPACK , of course, later than the legitimate DHCP server, that is, his answer will come second. All other DHCP clients on other OSs will simply ignore the second DHCPACK, but not macOS and iOS.
What network settings do these operating systems expose? Answer : those settings that will be contained in the second DHCPACK (in the attacker's DHCPACK).
Video demonstration of the bug in the DHCP client on macOS:
Do you think this bug or feature? I thought a bug and just in case I made an application for Apple Bug Reporter this application for more than a month, but I have not received a single comment from Apple experts.
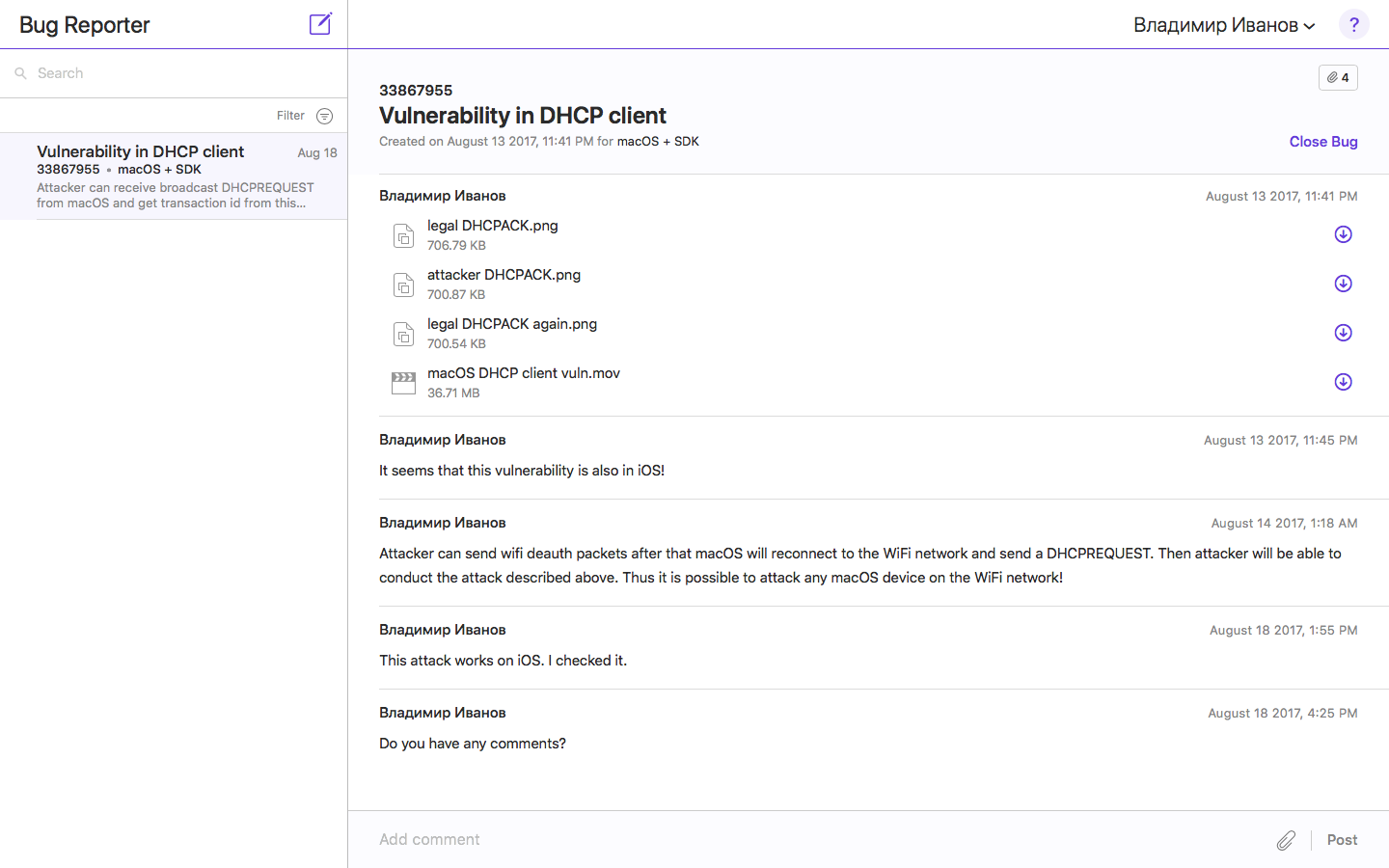
I did not stop at the application in Apple Bug Reporter and wrote a letter to product-security@apple.com

Apple specialists were not at all quick, but still answered and said that their DHCP client works in accordance with RFC 2131. That is, this is not a bug at all, it's a feature. That's all.

Afterword
For the laziest , I prepared the script apple_wifi_mitmer.py , which automatically finds all Apple devices on a Wi-Fi network, deauthenticates them and produces MiTM.
In the script arguments, you just need to specify the name of the wireless interface that is already connected to the Wi-Fi network under study, and another wireless interface for sending deauth packets.
Video demonstration of the apple_wifi_mitmer.py script :
Does it work on the new iOS 11? Answer: Yes, it works.
