Stantinko: large-scale adware campaign since 2012
Adware is not the easiest type of malware to analyze. Having discovered the complex threat of Stantinko, we did not immediately understand what it was: adware, malware, or spyware. It took time to identify its goals and patterns, since the threat leaves few traces on the infected machine. Understanding the Stantinko ecosystem is about how to assemble a puzzle.
Stantinko specializes in advertising fraud, but stands out against the general background of technical complexity. Code encryption and operational adaptation to protect against antivirus detection allowed Stantinko operators to remain out of sight for at least five years. In addition, the attention is attracted by the scale of Stantinko - this is one of the most common cyber threats in Russia, with about 500,000 devices in the botnet.

To infect the system, Stantinko operators mislead users who are searching for pirated software and downloading executable files, sometimes disguised as torrents. Next, FileTour, the initial vector of infection, defiantly installs many programs to distract the user's attention from the hidden installation of the first Stantinko service in the background. Video 1 shows how a user launches a malicious .exe file.
Video 1. A user downloads and runs a malicious file
. Stantinko operators manage and monetize a botnet, mainly by installing malicious browser extensions for unauthorized use of ads and click fraud. The problem is that they do not stop there. Malicious services allow you to execute anything on an infected system. We observed the sending of a full-featured backdoor, a bot for mass search on Google, as well as utilities for brute force attacks on the Joomla and WordPress control panels (designed for hacking and possible resale).
The figure below shows the full scheme of the Stantinko cyber campaign, from the infection vector to constant services and the corresponding plug-ins.
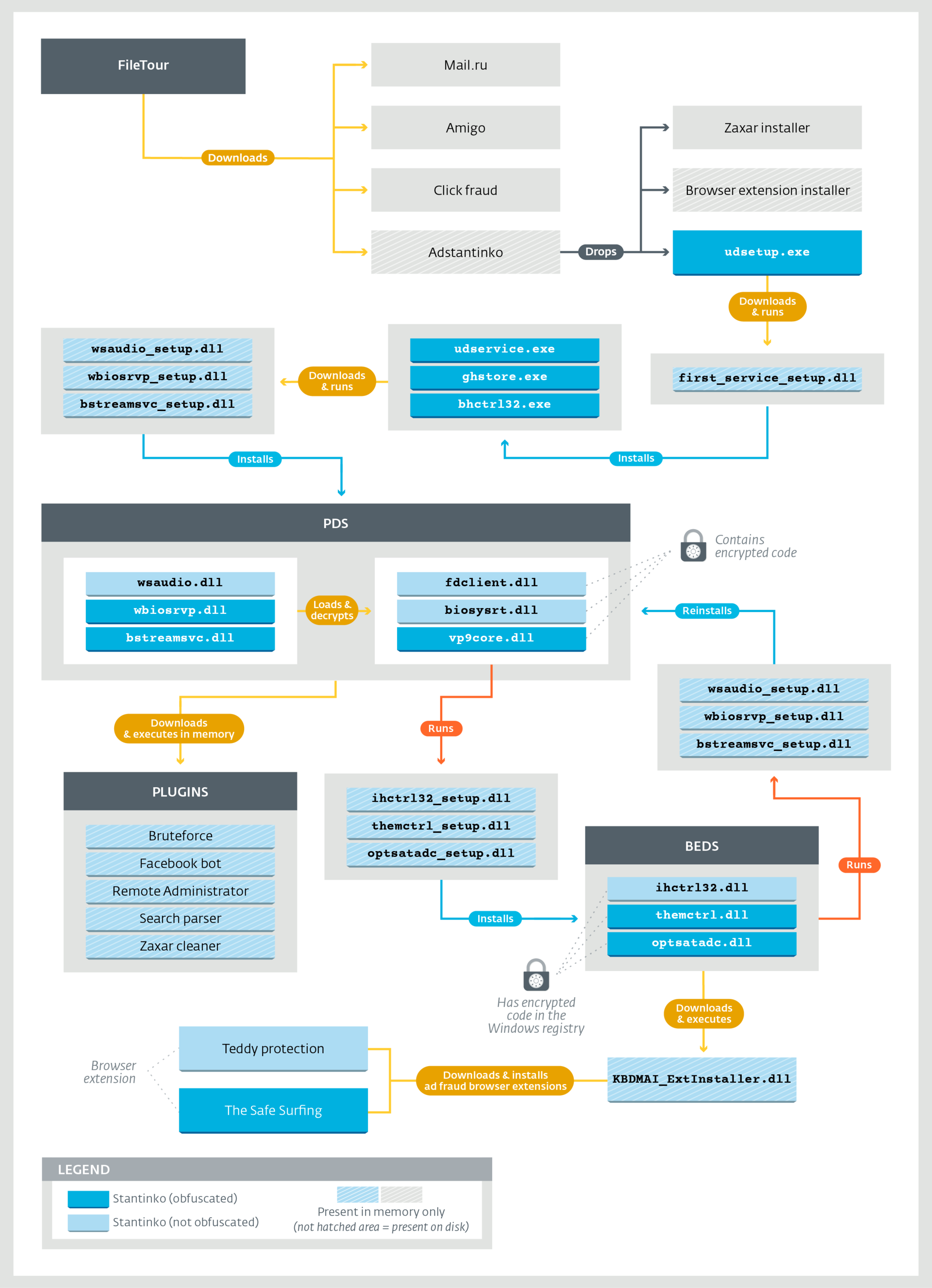
Figure 1. The full Stantinko threat diagram
A characteristic feature of Stantinko is to bypass antivirus detection and counteract reverse engineering that defines malicious behavior. A comprehensive threat analysis requires several components - a bootloader and an encrypted component. Malicious code is hidden in an encrypted component located either on disk or in the Windows registry. The code is downloaded and decrypted by a seemingly harmless executable file. A key is generated for each of the infections. Some components use the bot identifier, while others use the serial number of the victim's PC hard drive volume. Detection by unencrypted components is an extremely difficult task, since artifacts stored on disk do not show malicious behavior before execution.
In addition, Stantinko provides a recovery mechanism. After a successful infection, two malicious services are installed on the victim’s machine with the Widnows operating system, which start with the system. Services can reinstall each other if one of them is deleted. Thus, in order to successfully eliminate the threat, you must delete two services at the same time. Otherwise, the C & C server will forward a new version of the remote service that has not yet been discovered, or contains a new configuration.
The main functionality of Stantinko is the installation of the malicious browser extensions The Safe Surfing and Teddy Protection on the infected system.. At the time of analysis, both extensions were available in the Chrome Web Store. At first glance, these are legitimate browser extensions that block unwanted URLs. But when installed as part of the Stantinko scheme, the extensions get a different configuration that contains click fraud and unauthorized ad serving rules. Video 2 shows the installation process for The Safe Surfing extension . By clicking on the link, the user is redirected to the Rambler search engine.

Figure 2. Teddy Protection in the Chrome Web Store

Figure 3. The Safe Surfing in the Chrome Web Store
Video 2. Redirecting traffic to the Rambler
Stantinko website - a modular backdoor. Its components include a bootloader that allows you to execute any Windows executable file that is transferred by the C & C server directly to memory. This function is implemented in the form of a flexible plug-in system that allows operators to execute anything they want on an infected system. The table below describes the known Stantinko plugins.

Stantinko developers use methods that are more common in APT campaigns. However, their main goal is money. Operators offer their services in the most profitable computer crime markets.
First, clickfraud today is a major source of revenue for the cybercriminal ecosystem. A study by White Ops and the National Association of Advertisers (USA) estimated the global cost from click fraud in 2017 at $ 6.5 billion.
As described above, Stantinko installs two browser extensions - The Safe Surfing and Teddy Protectionthat show ads or redirect. This allows Stantinko operators to receive money for the traffic they provide to advertisers. The figure below shows the forwarding scheme.

Figure 4. Clickfraud, redirect process.
Traditional clickfraud schemes are based on a series of redirects between several ad networks in order to “wash” traffic. But in the case of Stantinko, the operators are closer to the advertisers - in some cases (see Figure 4), the user gets to the advertiser's website directly from the Stantinko network. This means that the attackers behind the Stantinko campaign can not only effectively hide malware, but also disrupt the traditional advertising economy, and it gets away with it.
Secondly, Stantinko operators are trying to access the control panels of sites on Joomla and WordPress. The attack is built on brute force with enumeration of logins and passwords on the list. The goal is to guess the password by trying tens of thousands of combinations. Hacked accounts can be resold and further used to redirect site visitors to a set of exploits or to host malicious content.
Thirdly, our study revealed how Stantinko works in social networks. We already described this type of fraud in the Linux / Moose report . The scheme really makes a profit - 1000 Facebook likes cost about $ 15 (even if they are generated by fake accounts in the botnet).
Stantinko operators have developed a plugin that interacts with Facebook. Among other things, he can create accounts, like the page and add friends. To circumvent captcha on Facebook, it uses a special service (in Figure 5). The scale of the Stantinko network is an advantage for operators, since it allows them to distribute requests between all bots - this complicates the task of Facebook in recognizing fraud.

Figure 5. Captcha bypass service used by Stantinko
Stantinko is a botnet that specializes in advertising fraud. Advanced technologies, including code encryption and code storage in the Windows registry, allowed operators to go unnoticed for five years.
In addition, Stantinko operators were able to put in the Chrome Web Store two browser extensions that performed unauthorized advertising. One of them first appeared on the Chrome Web Store in November 2015.
The user is unlikely to notice the presence of Stantinko in the system, since the threat does not overload the CPU. On the other hand, Stantinko brings losses to advertisers and significant revenue to operators. In addition, the presence of a full-featured backdoor allows attackers to monitor all infected machines.
Main conclusions:
Infection indicators are available on our GitHub account . For any questions regarding Stantinko, including sample transfer, write to threatintel@eset.com.
Stantinko specializes in advertising fraud, but stands out against the general background of technical complexity. Code encryption and operational adaptation to protect against antivirus detection allowed Stantinko operators to remain out of sight for at least five years. In addition, the attention is attracted by the scale of Stantinko - this is one of the most common cyber threats in Russia, with about 500,000 devices in the botnet.

Overview
To infect the system, Stantinko operators mislead users who are searching for pirated software and downloading executable files, sometimes disguised as torrents. Next, FileTour, the initial vector of infection, defiantly installs many programs to distract the user's attention from the hidden installation of the first Stantinko service in the background. Video 1 shows how a user launches a malicious .exe file.
Video 1. A user downloads and runs a malicious file
. Stantinko operators manage and monetize a botnet, mainly by installing malicious browser extensions for unauthorized use of ads and click fraud. The problem is that they do not stop there. Malicious services allow you to execute anything on an infected system. We observed the sending of a full-featured backdoor, a bot for mass search on Google, as well as utilities for brute force attacks on the Joomla and WordPress control panels (designed for hacking and possible resale).
The figure below shows the full scheme of the Stantinko cyber campaign, from the infection vector to constant services and the corresponding plug-ins.

Figure 1. The full Stantinko threat diagram
Key parameters
A characteristic feature of Stantinko is to bypass antivirus detection and counteract reverse engineering that defines malicious behavior. A comprehensive threat analysis requires several components - a bootloader and an encrypted component. Malicious code is hidden in an encrypted component located either on disk or in the Windows registry. The code is downloaded and decrypted by a seemingly harmless executable file. A key is generated for each of the infections. Some components use the bot identifier, while others use the serial number of the victim's PC hard drive volume. Detection by unencrypted components is an extremely difficult task, since artifacts stored on disk do not show malicious behavior before execution.
In addition, Stantinko provides a recovery mechanism. After a successful infection, two malicious services are installed on the victim’s machine with the Widnows operating system, which start with the system. Services can reinstall each other if one of them is deleted. Thus, in order to successfully eliminate the threat, you must delete two services at the same time. Otherwise, the C & C server will forward a new version of the remote service that has not yet been discovered, or contains a new configuration.
The main functionality of Stantinko is the installation of the malicious browser extensions The Safe Surfing and Teddy Protection on the infected system.. At the time of analysis, both extensions were available in the Chrome Web Store. At first glance, these are legitimate browser extensions that block unwanted URLs. But when installed as part of the Stantinko scheme, the extensions get a different configuration that contains click fraud and unauthorized ad serving rules. Video 2 shows the installation process for The Safe Surfing extension . By clicking on the link, the user is redirected to the Rambler search engine.

Figure 2. Teddy Protection in the Chrome Web Store

Figure 3. The Safe Surfing in the Chrome Web Store
Video 2. Redirecting traffic to the Rambler
Stantinko website - a modular backdoor. Its components include a bootloader that allows you to execute any Windows executable file that is transferred by the C & C server directly to memory. This function is implemented in the form of a flexible plug-in system that allows operators to execute anything they want on an infected system. The table below describes the known Stantinko plugins.

Monetization
Stantinko developers use methods that are more common in APT campaigns. However, their main goal is money. Operators offer their services in the most profitable computer crime markets.
First, clickfraud today is a major source of revenue for the cybercriminal ecosystem. A study by White Ops and the National Association of Advertisers (USA) estimated the global cost from click fraud in 2017 at $ 6.5 billion.
As described above, Stantinko installs two browser extensions - The Safe Surfing and Teddy Protectionthat show ads or redirect. This allows Stantinko operators to receive money for the traffic they provide to advertisers. The figure below shows the forwarding scheme.

Figure 4. Clickfraud, redirect process.
Traditional clickfraud schemes are based on a series of redirects between several ad networks in order to “wash” traffic. But in the case of Stantinko, the operators are closer to the advertisers - in some cases (see Figure 4), the user gets to the advertiser's website directly from the Stantinko network. This means that the attackers behind the Stantinko campaign can not only effectively hide malware, but also disrupt the traditional advertising economy, and it gets away with it.
Secondly, Stantinko operators are trying to access the control panels of sites on Joomla and WordPress. The attack is built on brute force with enumeration of logins and passwords on the list. The goal is to guess the password by trying tens of thousands of combinations. Hacked accounts can be resold and further used to redirect site visitors to a set of exploits or to host malicious content.
Thirdly, our study revealed how Stantinko works in social networks. We already described this type of fraud in the Linux / Moose report . The scheme really makes a profit - 1000 Facebook likes cost about $ 15 (even if they are generated by fake accounts in the botnet).
Stantinko operators have developed a plugin that interacts with Facebook. Among other things, he can create accounts, like the page and add friends. To circumvent captcha on Facebook, it uses a special service (in Figure 5). The scale of the Stantinko network is an advantage for operators, since it allows them to distribute requests between all bots - this complicates the task of Facebook in recognizing fraud.

Figure 5. Captcha bypass service used by Stantinko
Conclusion
Stantinko is a botnet that specializes in advertising fraud. Advanced technologies, including code encryption and code storage in the Windows registry, allowed operators to go unnoticed for five years.
In addition, Stantinko operators were able to put in the Chrome Web Store two browser extensions that performed unauthorized advertising. One of them first appeared on the Chrome Web Store in November 2015.
The user is unlikely to notice the presence of Stantinko in the system, since the threat does not overload the CPU. On the other hand, Stantinko brings losses to advertisers and significant revenue to operators. In addition, the presence of a full-featured backdoor allows attackers to monitor all infected machines.
Main conclusions:
- About 500,000 computers compromised by Stantinko
- The main goals are Russia (46%) and Ukraine (33%)
- Stantinko operators monetize the botnet by installing browser extensions for unauthorized ad serving
- The components remaining on the disk use a custom code obfuscator, which complicates the threat analysis process.
- In most Stantinko components, malicious code is hidden inside legitimate free open source software that has been modified and recompiled
- Stantinko installs several permanent services that can restore each other, preventing removal from the system
- The most common use of Stantinko is advertising fraud. However, its capabilities are much wider. We watched the sending of a full-featured backdoor for remote administration, a bot for mass search on Google and utilities for brute force attacks on the Joomla and WordPress control panels
Infection indicators are available on our GitHub account . For any questions regarding Stantinko, including sample transfer, write to threatintel@eset.com.
