JaCarta PKI and OpenVPN for Windows
This article describes how to configure two-factor authentication for JaCarta PKI smart cards and USB tokens based on X.509 digital certificates in OpenVPN.
This solution allows you to refuse the password authentication of the user. The implementation of this solution is a fundamental decrease in the influence of the human factor on the security of the system.
OpenVPN is a free open source Virtual Private Network (VPN) technology for creating encrypted point-to-point or server-client channels between computers. It allows you to establish connections between computers located behind a NAT-firewall, without the need to change their settings.
JaCarta PKI is a line of PKI tokens manufactured by Aladdin R. D. for strict authentication of users in corporate systems, secure storage of key containers of software cryptographic information protection and digital certificates.

This manual describes the process of setting up the simplest scenario of a VPN connection between a client and a server. The construction of complex networks is not considered in this manual.
JaCarta Single Client software is a software package designed to work with all models of JaCarta and eToken tokens and smart cards.
To be able to authenticate with OpenVPN using a digital certificate, the client and server must have digital certificates issued by a trusted certificate authority. The client must trust the server certificate, and the server must trust the client certificate.
Breach of trust in the server or client certificate will result in the inability to establish a VPN connection.
Consider the process of issuing keys and certificates using the tools offered by OpenVPN itself .
Go to the easy-rsa directory, which is located in the OpenVPN installation directory and run init-config.bat. As a result of the work, the vars.bat file will be created, which must be edited to adapt to your environment:
set HOME =% ProgramFiles% \ OpenVPN \ easy-rsa - set the working directory
set KEY_CONFIG = openssl-1.0.0.cnf - set the Openssl configuration file
set KEY_DIR = keys - set the directory for storing keys
set KEY_SIZE = 1024 - set the key size
set KEY_COUNTRY = US - specify the country
set KEY_PROVINCE = CA - specify the area
set KEY_CITY = SanFrancisco - specify the city
set KEY_ORG = OpenVPN - specify the name of the organization
set KEY_EMAIL=mail@host.domain - specify the e-mail
set KEY_CN = changeme - specify the common name ( common name)
set KEY_NAME = changeme - specify the name
set KEY_OU = changeme - specify the organizational unit
The following sections remain unchanged:
set PKCS11_MODULE_PATH = changeme - path to the pkcs # 11 module
set PKCS11_PIN = 1234 - PIN code for the smart card You
need to generate keys for TLS. Create empty files to store indexes and serial numbers. To do this, run (executed once):
Generate a certificate authority key (run once). Run:
In the dialog, specify the name of the desired Certification Authority.
Generate a Diffie-Hellman key file (server only, run once).
Run:
Generate a private key and server certificate.
Run:
As a result, a key and a certificate with the name of the machine (server) will be generated.
Now you need to create keys and certificates for client machines. Generate a PKCS # 12 file for each client machine.
To do this, run:
As a result, a PKCS # 12 file with the name of the client machine will be generated. This will need to be generated for each machine.
Edit your server configuration file, set the correct network settings.
Please note that you must correctly specify the path to the key and certificate files. Excerpt from the configuration file:
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS # 12 formatted key file
# (see "pkcs12" directive in man page).
ca C: \ CERTIFICATE_CERTIFICATE_CERT_path_path \ ca.crt
cert C: \ CERTIFICATE_CERT_WAY_SERVER \ server.crt
key C: \ SERVER_KEY_SERVER \ server.key
# Diffiellman
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh C: \ PUT_K_DIFPHI-HELLMAN_FILES \ dh1024.pem
Install the JaCarta Single Client and JaCarta SecurLogon software from the official website of Aladdin R.D.
"JaCarta SecurLogon" is a software solution that provides a simple and quick transition from regular passwords to two-factor authentication when logging into Microsoft Windows and accessing network resources using the JaCarta token.
Select the PKI tab and initialize the token.
Initializing a key will delete all data on it. If the key contains the information you need, including keys and certificates for other systems, do not initialize the key.
Using the JaCarta Single Client PC, import the PKCS # 12 file previously generated for the client to the token. The keys and certificate will appear on the token, they can be seen in the "JaCarta Single Client" window. Install the certificate from the token in the personal storage of the computer.
Copy the sha1 fingerprint of the personal certificate, it will be required for further configuration.
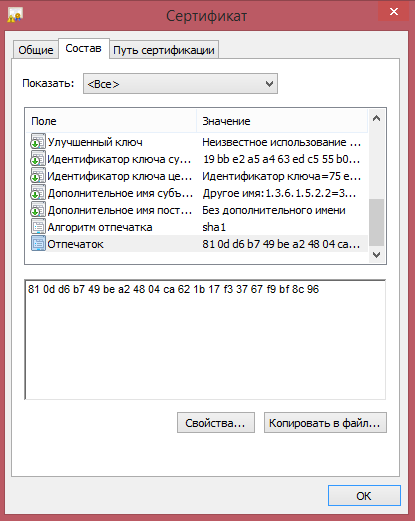
You will also need a Certificate Authority certificate obtained during server setup. Install the certificate in the repository of trusted root certificate authorities, and save it locally.
Edit your client configuration file, set the correct network settings.
In the cryptoapicert field, specify the fingerprint of the user certificate.
In the ca field, specify the path to the Certificate Authority certificate.
Excerpt from the configuration file:
# SSL / TLS parms.
# See the server config file for more
# description. It's best to use
# a separate .crt / .key file pair
# for each client. A single ca
# file can be used for all clients.
cryptoapicert "THUMB: 81 0d d6 b7 .... PRINT OF CLIENT CERTIFICATE "
ca C: \ WAY TO CERTIFICATE CENTER CERTIFICATE \ ca.crt
Launch OpenVPN on the server and client.
If the configuration is correct, you will be asked to enter the PIN code for the token, and the VPN connection will be successfully established.
The most popular way to generate keys and issue certificates is to use a Certification Authority, for example, based on the Microsoft Certification Authority. To configure OpenVPN, this method of generating keys and issuing a certificate is also suitable.
For the server, generate keys and a server authentication certificate on the Certification Authority, export them to the PKCS # 12 file.
In the settings of the server side of OpenVPN, instead of cert and key, you must specify pkcs12:
ca C: \ CERTIFICATE_CERTIFICATE_CENTER PATH \ ca.crt
pkcs12 C: \ SERVER_CERT_path \ server.p12 The
root certificate must be ca.
Setting up templates for issuing keys and certificates for a token is described in the instructions for the “Single JaCarta Client” and “JaCarta SecurLogon”. For the client, generate keys and a client authentication certificate on the Certification Authority. At the same time, importing the pkcs # 12 file into the token is not required. Other settings of the client part are performed similarly.
This solution allows you to refuse the password authentication of the user. The implementation of this solution is a fundamental decrease in the influence of the human factor on the security of the system.
About OpenVPN
OpenVPN is a free open source Virtual Private Network (VPN) technology for creating encrypted point-to-point or server-client channels between computers. It allows you to establish connections between computers located behind a NAT-firewall, without the need to change their settings.
About JaCarta PKI
JaCarta PKI is a line of PKI tokens manufactured by Aladdin R. D. for strict authentication of users in corporate systems, secure storage of key containers of software cryptographic information protection and digital certificates.

Tuning progress
Description of the demo stand
- Server - Microsoft Windows Server 2012, OpenVPN.
- Client - Microsoft Windows 8.1 with the installed driver "Single Client JaCarta" version 2.9 or higher, OpenVPN .
This manual describes the process of setting up the simplest scenario of a VPN connection between a client and a server. The construction of complex networks is not considered in this manual.
JaCarta Single Client software is a software package designed to work with all models of JaCarta and eToken tokens and smart cards.
Server Tuning
To be able to authenticate with OpenVPN using a digital certificate, the client and server must have digital certificates issued by a trusted certificate authority. The client must trust the server certificate, and the server must trust the client certificate.
Breach of trust in the server or client certificate will result in the inability to establish a VPN connection.
Consider the process of issuing keys and certificates using the tools offered by OpenVPN itself .
Go to the easy-rsa directory, which is located in the OpenVPN installation directory and run init-config.bat. As a result of the work, the vars.bat file will be created, which must be edited to adapt to your environment:
set HOME =% ProgramFiles% \ OpenVPN \ easy-rsa - set the working directory
set KEY_CONFIG = openssl-1.0.0.cnf - set the Openssl configuration file
set KEY_DIR = keys - set the directory for storing keys
set KEY_SIZE = 1024 - set the key size
set KEY_COUNTRY = US - specify the country
set KEY_PROVINCE = CA - specify the area
set KEY_CITY = SanFrancisco - specify the city
set KEY_ORG = OpenVPN - specify the name of the organization
set KEY_EMAIL=mail@host.domain - specify the e-mail
set KEY_CN = changeme - specify the common name ( common name)
set KEY_NAME = changeme - specify the name
set KEY_OU = changeme - specify the organizational unit
The following sections remain unchanged:
set PKCS11_MODULE_PATH = changeme - path to the pkcs # 11 module
set PKCS11_PIN = 1234 - PIN code for the smart card You
need to generate keys for TLS. Create empty files to store indexes and serial numbers. To do this, run (executed once):
- vars.bat;
- clean-all.bat.
Generate a certificate authority key (run once). Run:
- vars.bat;
- build-ca.bat.
In the dialog, specify the name of the desired Certification Authority.
Generate a Diffie-Hellman key file (server only, run once).
Run:
- vars.bat;
- build-dh.bat.
Generate a private key and server certificate.
Run:
- vars.bat;
- build-key-server.bat <machine name>.
As a result, a key and a certificate with the name of the machine (server) will be generated.
Now you need to create keys and certificates for client machines. Generate a PKCS # 12 file for each client machine.
To do this, run:
- vars.bat;
- build-key-pkcs12.bat <machine name>.
As a result, a PKCS # 12 file with the name of the client machine will be generated. This will need to be generated for each machine.
Edit your server configuration file, set the correct network settings.
Please note that you must correctly specify the path to the key and certificate files. Excerpt from the configuration file:
# Any X509 key management system can be used.
# OpenVPN can also use a PKCS # 12 formatted key file
# (see "pkcs12" directive in man page).
ca C: \ CERTIFICATE_CERTIFICATE_CERT_path_path \ ca.crt
cert C: \ CERTIFICATE_CERT_WAY_SERVER \ server.crt
key C: \ SERVER_KEY_SERVER \ server.key
# Diffiellman
# Generate your own with:
# openssl dhparam -out dh2048.pem 2048
dh C: \ PUT_K_DIFPHI-HELLMAN_FILES \ dh1024.pem
Client Setup
Install the JaCarta Single Client and JaCarta SecurLogon software from the official website of Aladdin R.D.
"JaCarta SecurLogon" is a software solution that provides a simple and quick transition from regular passwords to two-factor authentication when logging into Microsoft Windows and accessing network resources using the JaCarta token.
Select the PKI tab and initialize the token.
Initializing a key will delete all data on it. If the key contains the information you need, including keys and certificates for other systems, do not initialize the key.
Using the JaCarta Single Client PC, import the PKCS # 12 file previously generated for the client to the token. The keys and certificate will appear on the token, they can be seen in the "JaCarta Single Client" window. Install the certificate from the token in the personal storage of the computer.
Copy the sha1 fingerprint of the personal certificate, it will be required for further configuration.

You will also need a Certificate Authority certificate obtained during server setup. Install the certificate in the repository of trusted root certificate authorities, and save it locally.
Edit your client configuration file, set the correct network settings.
In the cryptoapicert field, specify the fingerprint of the user certificate.
In the ca field, specify the path to the Certificate Authority certificate.
Excerpt from the configuration file:
# SSL / TLS parms.
# See the server config file for more
# description. It's best to use
# a separate .crt / .key file pair
# for each client. A single ca
# file can be used for all clients.
cryptoapicert "THUMB: 81 0d d6 b7 .... PRINT OF CLIENT CERTIFICATE "
ca C: \ WAY TO CERTIFICATE CENTER CERTIFICATE \ ca.crt
Check
Launch OpenVPN on the server and client.
If the configuration is correct, you will be asked to enter the PIN code for the token, and the VPN connection will be successfully established.
Other ways to get keys and certificates
The most popular way to generate keys and issue certificates is to use a Certification Authority, for example, based on the Microsoft Certification Authority. To configure OpenVPN, this method of generating keys and issuing a certificate is also suitable.
For the server, generate keys and a server authentication certificate on the Certification Authority, export them to the PKCS # 12 file.
In the settings of the server side of OpenVPN, instead of cert and key, you must specify pkcs12:
ca C: \ CERTIFICATE_CERTIFICATE_CENTER PATH \ ca.crt
pkcs12 C: \ SERVER_CERT_path \ server.p12 The
root certificate must be ca.
Setting up templates for issuing keys and certificates for a token is described in the instructions for the “Single JaCarta Client” and “JaCarta SecurLogon”. For the client, generate keys and a client authentication certificate on the Certification Authority. At the same time, importing the pkcs # 12 file into the token is not required. Other settings of the client part are performed similarly.
