Cloud-AI - Artificial Intelligence in the Cloud Finding 10 LinkedIn Vulnerabilities
- Transfer
In 2015, the CloudSek project team set out to develop an artificial intelligence system that can interact with the Internet as a reasonable person. The first prototype of the system was presented to the public in March 2016 at the NullCon conference. Since then, the project has had several breakthrough discoveries that we want to talk about today.
People(in fact, not all) understand what to do on the site or in the mobile application, based on previous experience and using visual cues. We understand where the “button" is by the inscription on it, by its shape and even by the size and color of the objects. Old-type computer systems do not use previous experience in solving new problems. This call was accepted by developers from CloudSek. They developed a system based on artificial intelligence, which navigates through websites as a person developing on their own experience.
CloudSek uses training with partial involvement of the teacher (Semi-supervised learning) - for some precedents, the pair “situation, the required solution” is set, and for the part - only “situation”. People have created a huge number of ways and notation of mechanisms for interacting with web interfaces. This data is used to train CloudSek's Cloud-AI system, until the model independently performs the necessary tasks successfully. This approach helps to cope with difficult situations. Learning with signal reinforcement only from a reinforcement learning environment, and not from a teacher, as in CloudSek, would be less time-consuming in solving such problems. After 14 months of training, tagging different web interface options and creating a control dataset,
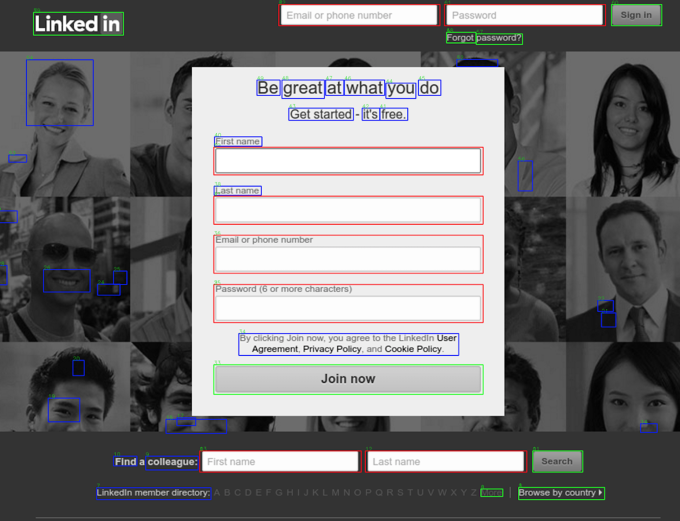
Cloud-AI successfully recognizes and classifies input forms, buttons, and link navigation with minimal error. With Cloud-AI, you can effectively interact with mobile, web or almost any application that uses a graphical user interface.
In 2015, Amazon released Amazon Echo, a personal assistant with artificial intelligence that can hear, understand and answer any question. Google is already testing autopilot cars in several cities. Companies create technologies that help people in their daily activities. CloudSek uses artificial intelligence to create agents that can navigate the Internet and complete complex, but boring and time-consuming tasks.
The idea of automating web tasks is nothing new. However, a developing automated system that can interact and navigate through any user interface on the network is something completely different, and the game is worth the candle. Amazon Echo can place an order for you through Amazon's shopping portal. But Echo is not able to order goods for you through Alibaba or another service with an API unknown to him. In the future, we will be able to use Cloud-AI to order anything anywhere via the Internet and perform other complex tasks, saving time.
Cloud-AI is fast and accurate, it is used by CloudSek to create x-Vigil and CloudMon products.
CloudSek uses Cloud-AI as an automated security monitoring of web applications and cloud infrastructure instead of manual testing, while increasing the capacity of the system after each test.
Insecure Direct Object References were one of the most well-known security issues on Facebook. Applications often use the real name or object key when creating web pages, not always performing user authorization checks for the target action. This creates a security hole in applications.
For example, the delete account function:
The attacker
CloudSek used the Cloud-AI system to interact with many popular and modern web applications to automatically test vulnerabilities. The main goal was unsafe direct links to objects. Among the tested platforms was LinkedIn, chosen because of the fame and simplicity of the interface.
The project team discovered 10 vulnerabilities through insecure direct links to objects on LinkedIn. These bugs would be very difficult to find manually and almost impossible using traditional automated tools. The LinkedIn team has been notified of these vulnerabilities. Here are a few already fixed:
Although all the bugs were fairly simple, it took a lot of effort to find them. Cloud-AI filled out numerous user forms and followed behavioral patterns to achieve vulnerabilities. Such vulnerabilities are often overlooked by existing automated tools and by manual testing.
There is an opportunity that allows recruiters to share the contacts of selected candidates with other hiring managers. The request below will send the candidate profile to another user. Changing the id value in the request for the victim id allows you to get an email for this id.
To find this request, Cloud-AI successfully performed several actions:
a) Logged in to LinkedIn;
b) Reached by links to the opportunity to share a resume;
c) Opened the correct form to fill out;
d) I wrote a message and pressed the desired button to confirm.
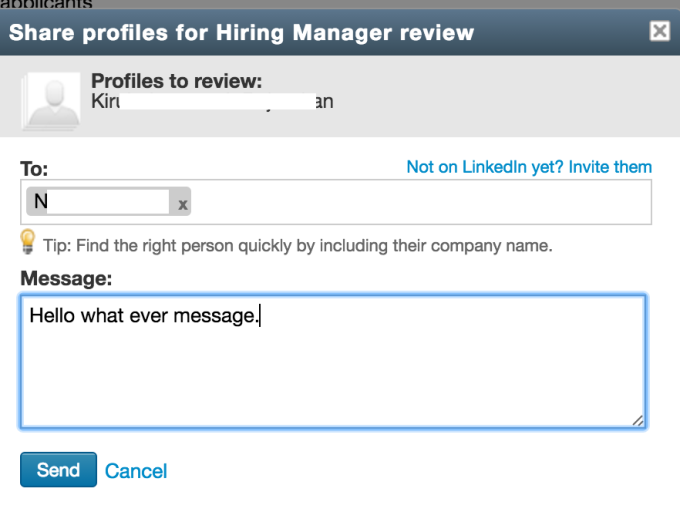
Cloud-AI independently fills out the necessary forms. The
response contained the email addresses of other users.

Other bugs are relatively similar. It is important that Cloud-AI has successfully completed the GUI chain of actions to achieve the vulnerability.
Changing memberIds in the next request allows the cracker to see the victim’s summary.
Only people who were looking for work through LinkedIn were vulnerable. Therefore, this did not affect all users.
A request that allows you to delete all invitations on LinkedIn by changing the request-id.
A request that downloads subtitles (transcripts) of all videos without any authentication.

After receiving reports of vulnerabilities found, the LinkedIn team fixed them within 24 hours. Therefore, all the described hacking opportunities should be read in the past tense.
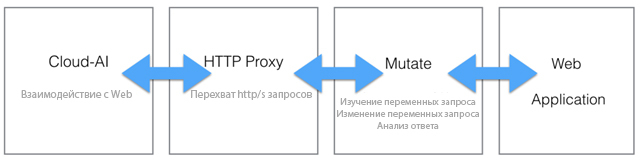
All data received by Cloud-AI was passed through a proxy server, which parsed the HTTP request into variables. Sending requests with variables changed in the mutation module allowed us to find security problems. Before notifying LinkedIn developers, the CloudSek team manually checked for vulnerabilities.
The system module, which acts as a proxy server and performs mutations, is now in the public domain .
Cloud-AI is gathering more and more information about how people interact with web interfaces. This allows the team to tune the system to more complex actions. The plans include the integration of training opportunities with reinforcement signals from the interaction environment (reinforcement learning). This will allow you to achieve the maximum number of actions that Cloud-AI can perform as a regular user.
An API is also expected to allow everyone to automate their tasks using Cloud-AI. We must remember that new technologies do not come without dangers. Cloud-AI can become a dangerous weapon if it falls into the wrong hands.

Cloud-AI from CloudSek
People
CloudSek uses training with partial involvement of the teacher (Semi-supervised learning) - for some precedents, the pair “situation, the required solution” is set, and for the part - only “situation”. People have created a huge number of ways and notation of mechanisms for interacting with web interfaces. This data is used to train CloudSek's Cloud-AI system, until the model independently performs the necessary tasks successfully. This approach helps to cope with difficult situations. Learning with signal reinforcement only from a reinforcement learning environment, and not from a teacher, as in CloudSek, would be less time-consuming in solving such problems. After 14 months of training, tagging different web interface options and creating a control dataset,

Cloud-AI successfully recognizes and classifies input forms, buttons, and link navigation with minimal error. With Cloud-AI, you can effectively interact with mobile, web or almost any application that uses a graphical user interface.
Introduction
In 2015, Amazon released Amazon Echo, a personal assistant with artificial intelligence that can hear, understand and answer any question. Google is already testing autopilot cars in several cities. Companies create technologies that help people in their daily activities. CloudSek uses artificial intelligence to create agents that can navigate the Internet and complete complex, but boring and time-consuming tasks.

The idea of automating web tasks is nothing new. However, a developing automated system that can interact and navigate through any user interface on the network is something completely different, and the game is worth the candle. Amazon Echo can place an order for you through Amazon's shopping portal. But Echo is not able to order goods for you through Alibaba or another service with an API unknown to him. In the future, we will be able to use Cloud-AI to order anything anywhere via the Internet and perform other complex tasks, saving time.
Cloud-AI is fast and accurate, it is used by CloudSek to create x-Vigil and CloudMon products.
- x-Vigil scans various Internet resources, social media platforms and forums, recognizing a wide range of information security threats and alerting them in real time without manual intervention.
- CloudMon monitors the insecurity of the Internet infrastructure (cloud applications, websites) to identify critical security issues.
CloudSek uses Cloud-AI as an automated security monitoring of web applications and cloud infrastructure instead of manual testing, while increasing the capacity of the system after each test.
Cloud-AI: Case studies and results in the field of information security applications
Insecure Direct Object References were one of the most well-known security issues on Facebook. Applications often use the real name or object key when creating web pages, not always performing user authorization checks for the target action. This creates a security hole in applications.
For example, the delete account function:
http://domain.com/delete-account.php?userid=5555The attacker
User-id = 5555is easily replaced by the victim's User-id value to detect such vulnerabilities. The task of finding such known security errors is difficult for an automated tool due to the inaccessibility of the target action. The reason for this is the need for multi-step interaction with the interface. Manual testing of each such bug will take a lot of time. CloudSek used the Cloud-AI system to interact with many popular and modern web applications to automatically test vulnerabilities. The main goal was unsafe direct links to objects. Among the tested platforms was LinkedIn, chosen because of the fame and simplicity of the interface.
LinkedIn Data Leak Testing
The project team discovered 10 vulnerabilities through insecure direct links to objects on LinkedIn. These bugs would be very difficult to find manually and almost impossible using traditional automated tools. The LinkedIn team has been notified of these vulnerabilities. Here are a few already fixed:
- Email leak for id of any user.
- Leak email users, phone numbers and resumes.
- Delete all user prompts.
- Download subtitles for all videos in Lynda Online Course Library.
- Download all exercise files without purchasing a premium Lynda account.
Although all the bugs were fairly simple, it took a lot of effort to find them. Cloud-AI filled out numerous user forms and followed behavioral patterns to achieve vulnerabilities. Such vulnerabilities are often overlooked by existing automated tools and by manual testing.
1) Email leak for id of any user
There is an opportunity that allows recruiters to share the contacts of selected candidates with other hiring managers. The request below will send the candidate profile to another user. Changing the id value in the request for the victim id allows you to get an email for this id.
POST /cap/candidate/forwardProfilesAjax HTTP/1.1
Host: www.linkedin.com
csrfToken=ajax&newHiringManagerMemberIds=&forwardTo=&msgBody=Hello&_action_forwardProfilesAjax&projectId=&memberIds=[Victim ID]To find this request, Cloud-AI successfully performed several actions:
a) Logged in to LinkedIn;
b) Reached by links to the opportunity to share a resume;
c) Opened the correct form to fill out;
d) I wrote a message and pressed the desired button to confirm.

Cloud-AI independently fills out the necessary forms. The
response contained the email addresses of other users.

Leak of names and email addresses of victims
Other bugs are relatively similar. It is important that Cloud-AI has successfully completed the GUI chain of actions to achieve the vulnerability.
2) Leak email users, phone numbers and resumes
Changing memberIds in the next request allows the cracker to see the victim’s summary.
GET /cap/applicant/profileExportPdf?trackingSearchId=[id]&memberIds=[Victim IDs]Only people who were looking for work through LinkedIn were vulnerable. Therefore, this did not affect all users.
3) Delete all user prompts
A request that allows you to delete all invitations on LinkedIn by changing the request-id.
POST /people/invites/withdraw?isInvite=true HTTP/1.1
Host: www.linkedin.com
Connection: close
csrfToken=[]&Ids={victims request-id }
4) Download subtitles for all videos in Lynda Online Course Library
A request that downloads subtitles (transcripts) of all videos without any authentication.
GET /ajax/player/transcript?courseId=496475&videoId=5093285) Download all exercise files without buying a premium Lynda account
GET /ajax/course/518763/download/exercise/543328
After receiving reports of vulnerabilities found, the LinkedIn team fixed them within 24 hours. Therefore, all the described hacking opportunities should be read in the past tense.
Method and OpenSource Code

HTTP mutation module
All data received by Cloud-AI was passed through a proxy server, which parsed the HTTP request into variables. Sending requests with variables changed in the mutation module allowed us to find security problems. Before notifying LinkedIn developers, the CloudSek team manually checked for vulnerabilities.
The system module, which acts as a proxy server and performs mutations, is now in the public domain .
The future of Cloud-AI
Cloud-AI is gathering more and more information about how people interact with web interfaces. This allows the team to tune the system to more complex actions. The plans include the integration of training opportunities with reinforcement signals from the interaction environment (reinforcement learning). This will allow you to achieve the maximum number of actions that Cloud-AI can perform as a regular user.
An API is also expected to allow everyone to automate their tasks using Cloud-AI. We must remember that new technologies do not come without dangers. Cloud-AI can become a dangerous weapon if it falls into the wrong hands.
