Mobile bankers spread on Google Play under the guise of weather applications
The specialists of our virus laboratory found on the Google Play service two modifications of the banking Trojan.Android/Spy.Banker. The Trojan spread under the guise of legitimate weather forecast applications.
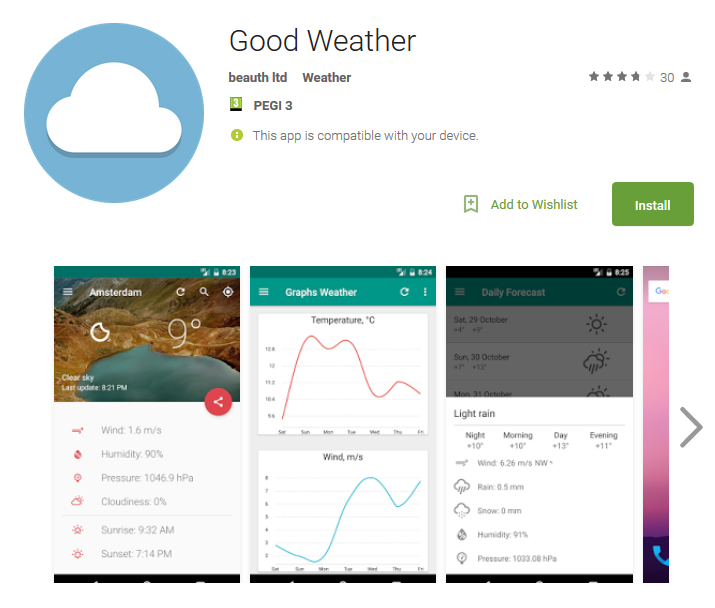
The first version - a trojan that imitates the Good Weather application - appeared on the store on February 4 and was deleted two days after the ESET request. The program focused on 22 banking applications used in Turkey. In two days, up to 5,000 users downloaded the fake application.
The second version appeared on February 14 and was distributed until the 20th inclusive, disguising itself as the World Weather application. The functionality of the trojan has not changed in comparison with the first modification, but now the program has been redirected to 69 applications of British, Austrian, German and Turkish banks. After an ESET request, the malicious applications were removed, and on February 23, the hosting company disconnected the C&C server.
Functionality
During installation, the trojan receives permission to intercept text messages. After that, he asks for administrator rights and gets access to change the screen lock password and the screen lock function. Having received these functions, the trojan is ready for malicious activity.
The trojan copies the main functionality of a legitimate application - it adds a weather forecast widget to the main screen. In parallel with this, it sends information about the device to the command C&C server in the background.
The program provides a notification function, which is used after establishing communication with the command C&C server. The Trojan can send fake notifications to infected devices - “important messages” of the corresponding bank, prompting the user to launch one of the target banking applications.

When the user launches the target application, the trojan displays a fake login and password input screen, and then transfers the entered data to the C&C command server. The function of intercepting text messages allows you to bypass two-factor authentication based on SMS.
We assume that the screen lock function is used in the next stage, when attackers try to cash out funds from a compromised account - in order to hide the theft from the victim.
Open source
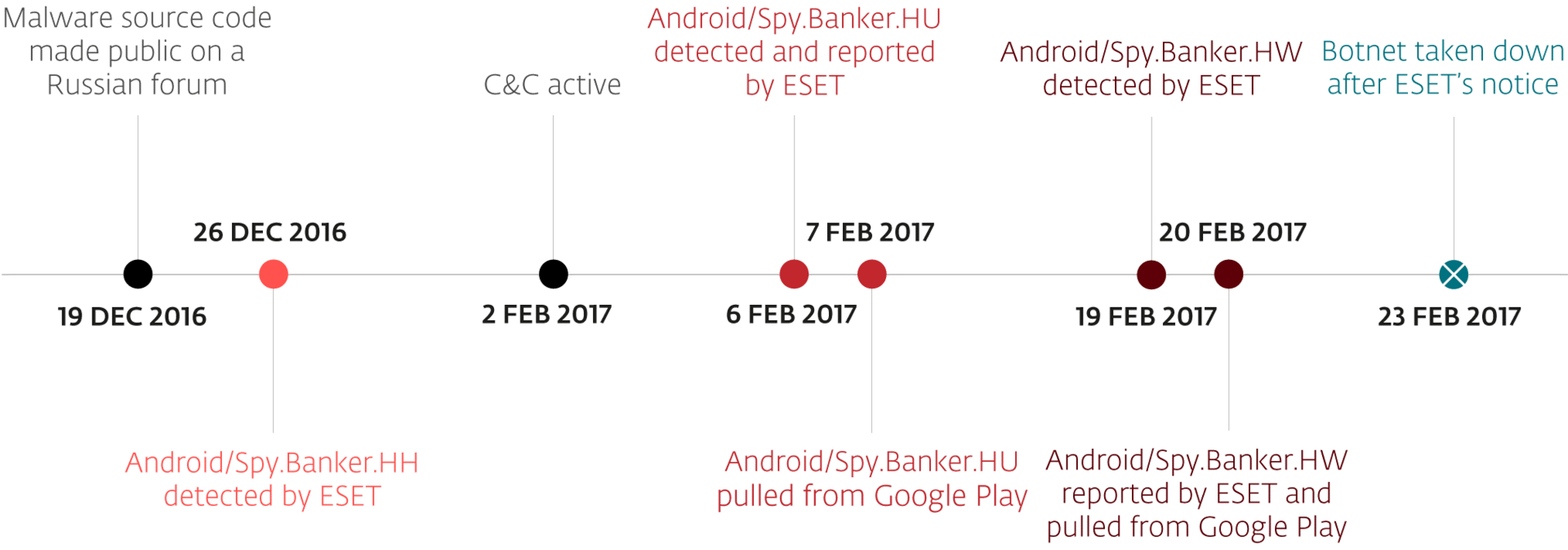
Further research on the Trojan led to some interesting discoveries. As it turned out, both modifications are written on the basis of open source code, which was published on the Web. “Written from scratch” (according to the authors), the Android bot code template has been available on the Russian-language forum since December 19, 2016.

We found out that Doctor Web analyzed an early version of this trojan - our products have been detecting it since December 26, 2016 as Android / Spy.Banker.HH. But the early modification is not directly related to the versions that we found on the Google Play service (despite the fact that it is detected with the same name). We confirmed this by gaining access to the command server control panel (see below) and collecting information about the versions of the trojan that infected more than 2800 devices.
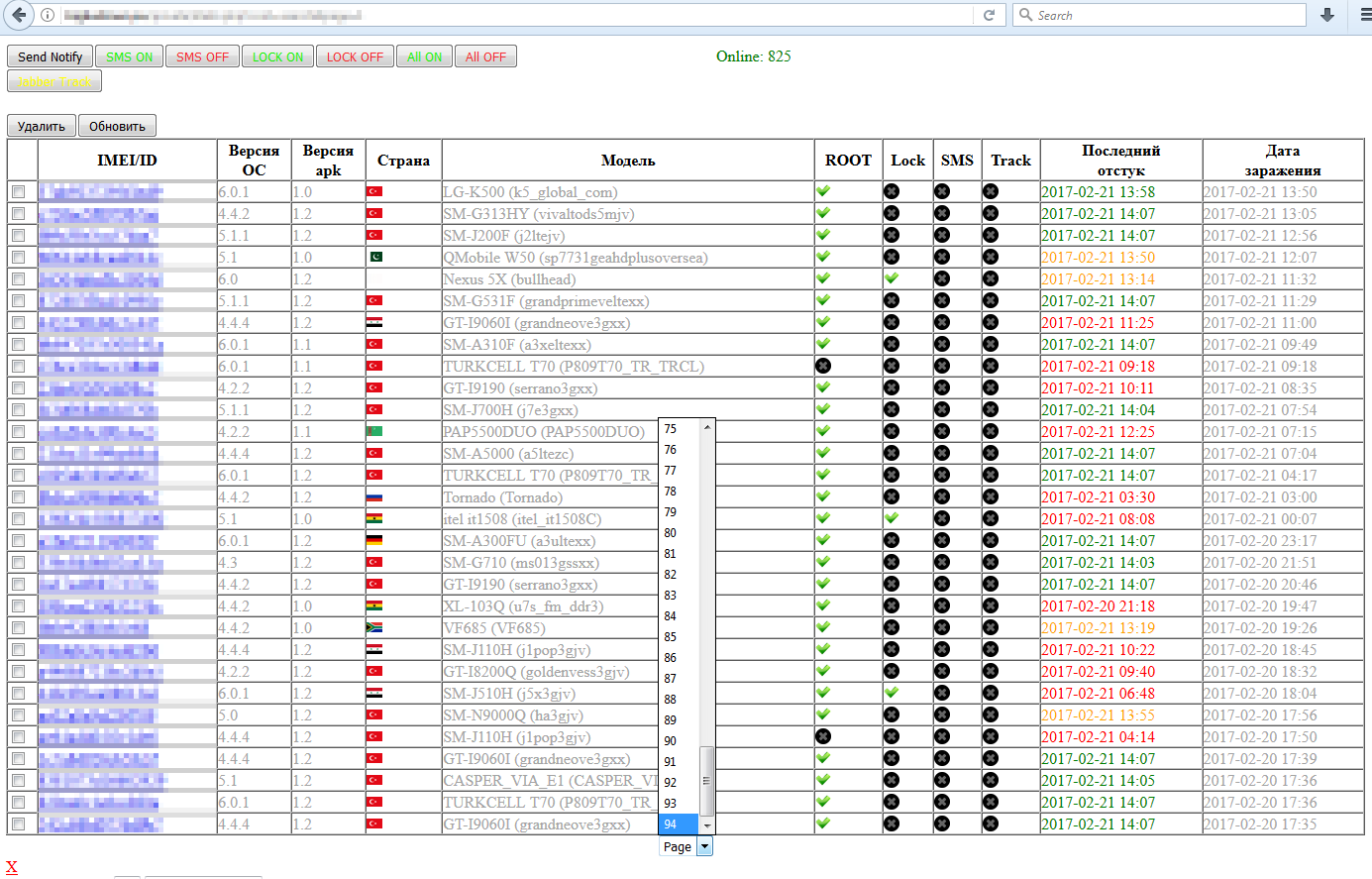
Interestingly, the command server, effective from February 2, 2017, is available to all who have URLs, without authorization.
Prevention
Just in case, we list the basic precautions to prevent infection by a mobile banker.
Google Play uses security mechanisms to prevent malware from entering the store. Not always successful, but on third-party sites such options are not provided in principle. Download applications from the official store whenever possible.
When downloading the application and after starting, pay attention to requests for rights and permissions. If the request is not directly related to the functionality, refuse to install or at least read user reviews.
Use a reliable anti-virus product for Android.
If a malicious application has already been installed, you can use a mobile antivirus to clean it up or remove the malicious application manually after disabling administrator rights.
Detection by ESET products :

The first version - a trojan that imitates the Good Weather application - appeared on the store on February 4 and was deleted two days after the ESET request. The program focused on 22 banking applications used in Turkey. In two days, up to 5,000 users downloaded the fake application.
The second version appeared on February 14 and was distributed until the 20th inclusive, disguising itself as the World Weather application. The functionality of the trojan has not changed in comparison with the first modification, but now the program has been redirected to 69 applications of British, Austrian, German and Turkish banks. After an ESET request, the malicious applications were removed, and on February 23, the hosting company disconnected the C&C server.

Functionality
During installation, the trojan receives permission to intercept text messages. After that, he asks for administrator rights and gets access to change the screen lock password and the screen lock function. Having received these functions, the trojan is ready for malicious activity.
The trojan copies the main functionality of a legitimate application - it adds a weather forecast widget to the main screen. In parallel with this, it sends information about the device to the command C&C server in the background.
The program provides a notification function, which is used after establishing communication with the command C&C server. The Trojan can send fake notifications to infected devices - “important messages” of the corresponding bank, prompting the user to launch one of the target banking applications.

When the user launches the target application, the trojan displays a fake login and password input screen, and then transfers the entered data to the C&C command server. The function of intercepting text messages allows you to bypass two-factor authentication based on SMS.
We assume that the screen lock function is used in the next stage, when attackers try to cash out funds from a compromised account - in order to hide the theft from the victim.
Open source
Further research on the Trojan led to some interesting discoveries. As it turned out, both modifications are written on the basis of open source code, which was published on the Web. “Written from scratch” (according to the authors), the Android bot code template has been available on the Russian-language forum since December 19, 2016.

We found out that Doctor Web analyzed an early version of this trojan - our products have been detecting it since December 26, 2016 as Android / Spy.Banker.HH. But the early modification is not directly related to the versions that we found on the Google Play service (despite the fact that it is detected with the same name). We confirmed this by gaining access to the command server control panel (see below) and collecting information about the versions of the trojan that infected more than 2800 devices.

Interestingly, the command server, effective from February 2, 2017, is available to all who have URLs, without authorization.
Prevention
Just in case, we list the basic precautions to prevent infection by a mobile banker.
Google Play uses security mechanisms to prevent malware from entering the store. Not always successful, but on third-party sites such options are not provided in principle. Download applications from the official store whenever possible.
When downloading the application and after starting, pay attention to requests for rights and permissions. If the request is not directly related to the functionality, refuse to install or at least read user reviews.
Use a reliable anti-virus product for Android.
If a malicious application has already been installed, you can use a mobile antivirus to clean it up or remove the malicious application manually after disabling administrator rights.
Detection by ESET products :
- Android / Spy.Banker.HH
- Android / Spy.Banker.HU
- Android / Spy.Banker.HW
