Providers are infected with the DNS server cache by manipulating DNS responses from legitimate authoritative DNS servers
A serious problem of our time is information security threats, that is, classes of threats implemented using internetworking protocols. One of these protocols is the domain name system protocol - DNS.
Among the threats that use the domain name system, there are threats based on the modification of DNS transaction packets and aimed at creating a false route on the network. Their potential danger lies in the possibility of interception of data transmitted between clients of network services and servers of these services.
Tracking the modification of DNS transaction packets, with a potentially high risk of implementation of attacks in information systems, is rather difficult, therefore such attacks as:
The subject of infection of the cache of DNS servers of providers has long been eradicated, however, using a practical example, we will show how it is quite simple to make clients of a particular Internet provider “go to” the IP address we need, instead of the correct one for a given domain, without hacking and not infecting trojans, thereby giving us full control over the traffic associated with a particular DNS zone.
Imagine a fragment of the global Internet from a client PC to some remote web service, as well as other network elements related to the domain name system
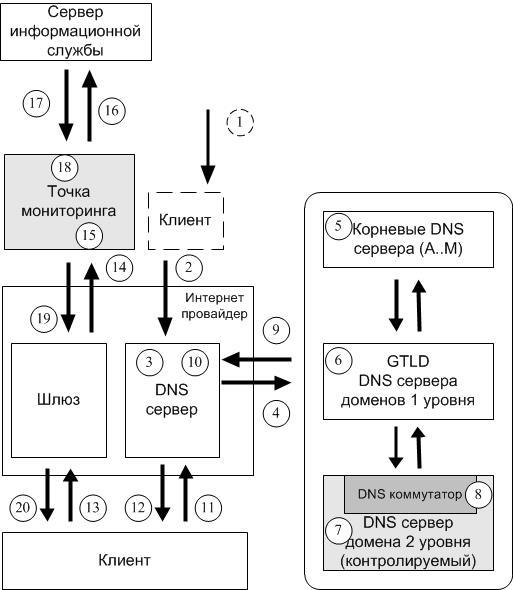
A typical computer network that implements IP address spoofing for a target domain includes the following elements:
For the successful implementation of our plan, a number of conditions must be met:
To initiate the monitoring process, it is necessary to make a request for resolving the DNS name from the zone for which the controlled DNS server is responsible. Thanks to this, it becomes possible to generate a DNS response to the received request with the specified parameters.
According to the recommendations of RFC 1034, RFC 1035, which establish the operating procedure, specification and application of the domain name system, the so-called “Additional” fields are allowed to be added when generating a DNS response. These fields are necessary for recording the IP addresses of auxiliary nodes of various types, including to prevent repeated access to the DNS server, in cases where, for certain reasons, the primary node, the record of which is transmitted in the "Answer" field, is unavailable.In the case of applying the proposed approach, the “Additional” field contains the IP address that is mapped to the domain name of the target information service, but actually belongs to the monitoring point - the firewall.
Such a task (adding the field we need) can be assigned to a script that simulates the operation of a legitimate DNS server responsible for any DNS zone, and no matter what level ...
After resolving the given DNS name, the caching DNS server of the Internet service provider (ISP) receives a DNS response, then if there are no entries in its cache corresponding to the entries from the additional fields of the DNS response, it places these entries in the cache memory. Thus, records are stored in the cache of the DNS server of the Internet service provider that establish the correspondence between the domain names of the information services for which monitoring will be carried out and the IP address belonging to the monitoring point. From this moment, if the client generates a DNS query for resolving the host name of the target information service with the domain name stored in the provider’s cache and saved from additional fields received after processing the DNS request of the “auxiliary” client,
Thus, the client obtains the domain name resolution of the requested information service with the IP address received from the controlled DNS server and stored at the time of processing the client’s request by the Internet provider in the provider's cache. Moreover, the IP address does not belong to the target information service requested by the client, but to the monitoring point. Accordingly, further, the client contacts the target information service at the IP address belonging to the monitoring point.
When a client contacts the received IP address to a monitoring point at which, based on predefined parameters of the network security policy, a number of control actions are performed. These actions include:
At the monitoring point - ITU, Network Address Translation (NAT) is implemented, which ensures its "transparent" work from the point of view of the client and the target information service.
Verification of the submitted surveys was carried out using a test bench in the form of a computer network with the following elements:
Between all objects of a computer network network interaction is configured. The principle of operation of a computer network is as follows.
Between DNS servers, zone forwarding is configured in such a way that receiving a request for domain name resolution from a zone for which another DNS server is responsible, the current DNS server generates and sends a repeated DNS request to it and, after receiving a response from it, generates and sends a DNS response to the client who generated the first request, while simultaneously placing a response from the second DNS server in their cache memory. Thus, the operation of the DNS server of the Internet service provider is simulated.
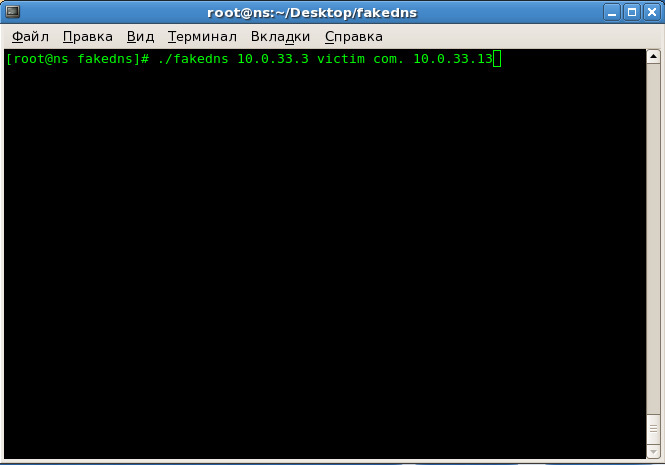
At the 1st stage, the “fakedns” script is launched on the DNS server responsible for the ".b" zone, which implements the operation of the DNS switch. The script’s task is to process the received DNS request for resolving the domain name from the “.b” zone and add an additional field “Additional” for the given domain name (in the example, “victim.com”) to the DNS, corresponding to the target information service for which monitoring and security management of network interactions with the client will be carried out, and with the specified IP address (in the example - “10.0.33.13”) corresponding to the monitoring point - the firewall. The script “fakedns” is run with the given parameters, simulating the operation of the DNS switch by ** command **
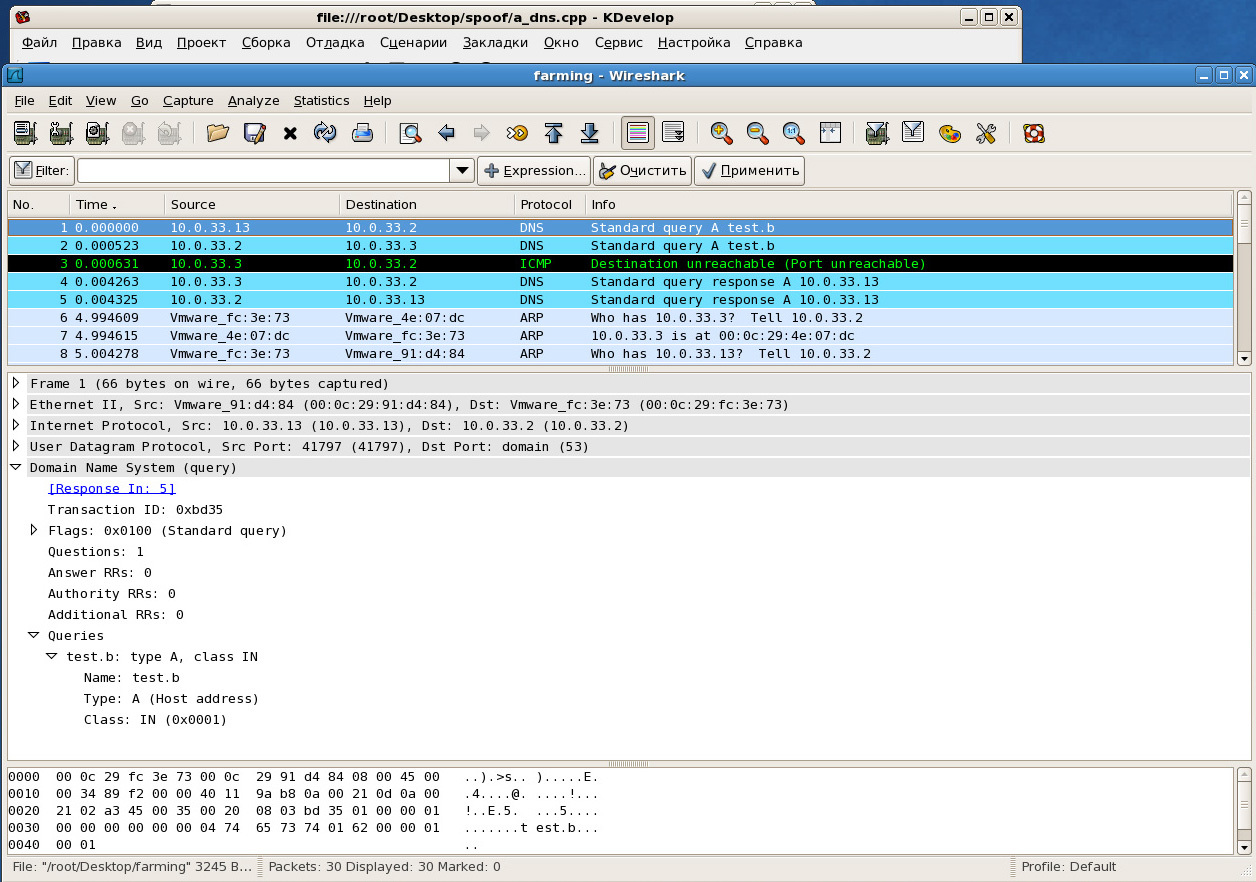
At the 2nd stage, a DNS query is generated and transmitted for the domain name “test.b” from the client to the domain name system consisting of the DNS server “ns.a” and the DNS server “ns.b”. In this case, the primary DNS server (DNS server of the Internet provider) for the client is the DNS server "ns.a".
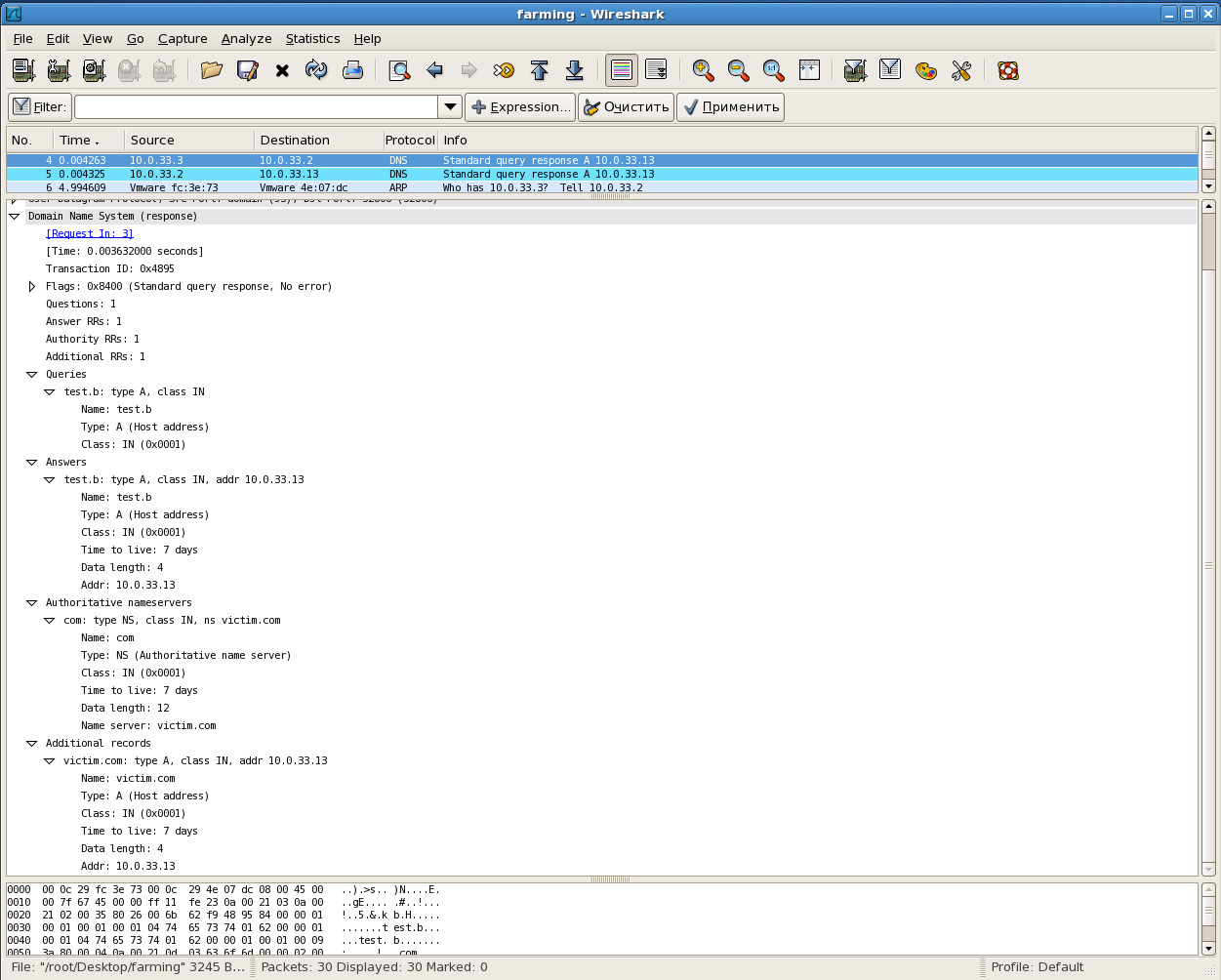
At the 3rd stage, a DNS response is generated and transmitted for the domain name “test.b” with an additional field “Additional” and the specified domain name “victim.com”, corresponding to the information service that is assigned the specified IP address “10.0.33.13 "Corresponding to the monitoring point.
At the 4th stage, the presence of the victim.com domain name in the DNS server cache “ns.a” is checked in the cache of the DNS server, corresponding to the information service, but with the IP address corresponding to the monitoring point - “10.0.33.13”.
Verification is carried out by
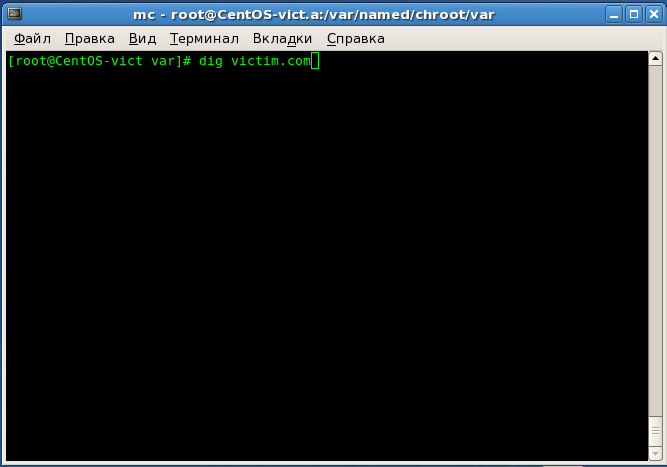
At the 5th stage, a response is received about the availability of the victim.com domain name in the DNS cache of the DNS server “ns.a”.
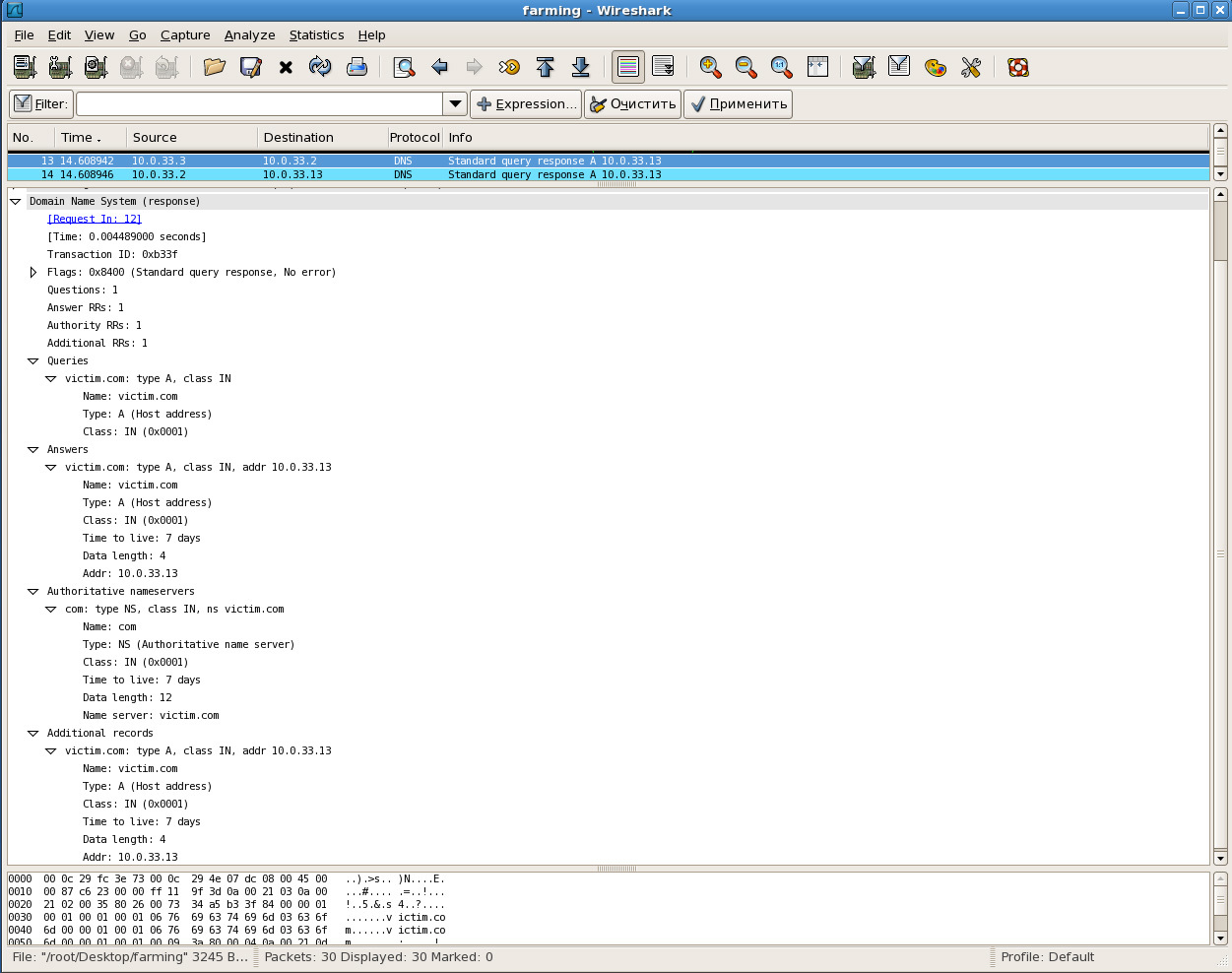
Obviously, upon further contact of the client with the “victim.com” node by the IP address from the received DNS response, the call will occur at the IP address specified in the parameters to the “fakedns” script and the corresponding monitoring point - the firewall.
Verification of this fact is carried out by the team

Based on the presented materials of the experiment, it can be concluded that, when the above conditions are met and the additional field “Additional” is added to the DNS switch when processing the request for resolving the domain name of the target information service, it becomes possible to control the network interaction of the client and specified information services depending on their location and topology of the computer network. In addition, it becomes possible to monitor and control the network interaction of the client and the specified information services both at the stage of establishing a connection session and at the stage of information exchange, which is not good ...
Among the threats that use the domain name system, there are threats based on the modification of DNS transaction packets and aimed at creating a false route on the network. Their potential danger lies in the possibility of interception of data transmitted between clients of network services and servers of these services.
Tracking the modification of DNS transaction packets, with a potentially high risk of implementation of attacks in information systems, is rather difficult, therefore such attacks as:
- network traffic analysis;
- substitution of a trusted network object;
- imposing a false route;
- implementation of a false network object.
The subject of infection of the cache of DNS servers of providers has long been eradicated, however, using a practical example, we will show how it is quite simple to make clients of a particular Internet provider “go to” the IP address we need, instead of the correct one for a given domain, without hacking and not infecting trojans, thereby giving us full control over the traffic associated with a particular DNS zone.
Imagine a fragment of the global Internet from a client PC to some remote web service, as well as other network elements related to the domain name system

A typical computer network that implements IP address spoofing for a target domain includes the following elements:
- Client PC (Client).
- Internet Service Provider (consisting of a caching DNS server, gateway).
- Auxiliary client.
- Domain Name System.
- Monitoring point (firewall, filter, proxy server).
- Information Service Server.
For the successful implementation of our plan, a number of conditions must be met:
- There is a controlled DNS server responsible for any (any) zone of the domain name system.
- The client is served by an Internet provider with a caching DNS server, or another DNS server is known whose services the client uses, and this server is a caching server.
- At the time of receiving the DNS response from the monitored DNS server, there is no record with the target DNS name of the information service node in the cache of the DNS server of the Internet service provider.
- At the monitoring point, there is a database of IP addresses and domain names of the target information services, for which monitoring and management of network interactions with the client is carried out.
To initiate the monitoring process, it is necessary to make a request for resolving the DNS name from the zone for which the controlled DNS server is responsible. Thanks to this, it becomes possible to generate a DNS response to the received request with the specified parameters.
According to the recommendations of RFC 1034, RFC 1035, which establish the operating procedure, specification and application of the domain name system, the so-called “Additional” fields are allowed to be added when generating a DNS response. These fields are necessary for recording the IP addresses of auxiliary nodes of various types, including to prevent repeated access to the DNS server, in cases where, for certain reasons, the primary node, the record of which is transmitted in the "Answer" field, is unavailable.In the case of applying the proposed approach, the “Additional” field contains the IP address that is mapped to the domain name of the target information service, but actually belongs to the monitoring point - the firewall.
Such a task (adding the field we need) can be assigned to a script that simulates the operation of a legitimate DNS server responsible for any DNS zone, and no matter what level ...
After resolving the given DNS name, the caching DNS server of the Internet service provider (ISP) receives a DNS response, then if there are no entries in its cache corresponding to the entries from the additional fields of the DNS response, it places these entries in the cache memory. Thus, records are stored in the cache of the DNS server of the Internet service provider that establish the correspondence between the domain names of the information services for which monitoring will be carried out and the IP address belonging to the monitoring point. From this moment, if the client generates a DNS query for resolving the host name of the target information service with the domain name stored in the provider’s cache and saved from additional fields received after processing the DNS request of the “auxiliary” client,
Thus, the client obtains the domain name resolution of the requested information service with the IP address received from the controlled DNS server and stored at the time of processing the client’s request by the Internet provider in the provider's cache. Moreover, the IP address does not belong to the target information service requested by the client, but to the monitoring point. Accordingly, further, the client contacts the target information service at the IP address belonging to the monitoring point.
When a client contacts the received IP address to a monitoring point at which, based on predefined parameters of the network security policy, a number of control actions are performed. These actions include:
- Analysis of the transaction received from the client.
- Development and application of control actions.
- Audit of received transactions and actions performed.
- Formation of a request to an information service based on data from a received client transaction.
At the monitoring point - ITU, Network Address Translation (NAT) is implemented, which ensures its "transparent" work from the point of view of the client and the target information service.
Verification of the submitted surveys was carried out using a test bench in the form of a computer network with the following elements:
- A DNS server based on BIND 9.4 software, responsible for the zone ".a", with the domain name "ns.a".
- A DNS server based on BIND 9.4 software, responsible for the ".b" zone, with the domain name "ns.b".
- Client PC with IP address 10.0.33.13.
- The monitoring point is a firewall with an IP address of 10.0.33.13.
Between all objects of a computer network network interaction is configured. The principle of operation of a computer network is as follows.
Between DNS servers, zone forwarding is configured in such a way that receiving a request for domain name resolution from a zone for which another DNS server is responsible, the current DNS server generates and sends a repeated DNS request to it and, after receiving a response from it, generates and sends a DNS response to the client who generated the first request, while simultaneously placing a response from the second DNS server in their cache memory. Thus, the operation of the DNS server of the Internet service provider is simulated.
At the 1st stage, the “fakedns” script is launched on the DNS server responsible for the ".b" zone, which implements the operation of the DNS switch. The script’s task is to process the received DNS request for resolving the domain name from the “.b” zone and add an additional field “Additional” for the given domain name (in the example, “victim.com”) to the DNS, corresponding to the target information service for which monitoring and security management of network interactions with the client will be carried out, and with the specified IP address (in the example - “10.0.33.13”) corresponding to the monitoring point - the firewall. The script “fakedns” is run with the given parameters, simulating the operation of the DNS switch by ** command **

At the 2nd stage, a DNS query is generated and transmitted for the domain name “test.b” from the client to the domain name system consisting of the DNS server “ns.a” and the DNS server “ns.b”. In this case, the primary DNS server (DNS server of the Internet provider) for the client is the DNS server "ns.a".
Request Structure

At the 3rd stage, a DNS response is generated and transmitted for the domain name “test.b” with an additional field “Additional” and the specified domain name “victim.com”, corresponding to the information service that is assigned the specified IP address “10.0.33.13 "Corresponding to the monitoring point.
DNS response packet structure

At the 4th stage, the presence of the victim.com domain name in the DNS server cache “ns.a” is checked in the cache of the DNS server, corresponding to the information service, but with the IP address corresponding to the monitoring point - “10.0.33.13”.
Verification is carried out by

At the 5th stage, a response is received about the availability of the victim.com domain name in the DNS cache of the DNS server “ns.a”.
DNS response structure

Obviously, upon further contact of the client with the “victim.com” node by the IP address from the received DNS response, the call will occur at the IP address specified in the parameters to the “fakedns” script and the corresponding monitoring point - the firewall.
Verification of this fact is carried out by the team

Based on the presented materials of the experiment, it can be concluded that, when the above conditions are met and the additional field “Additional” is added to the DNS switch when processing the request for resolving the domain name of the target information service, it becomes possible to control the network interaction of the client and specified information services depending on their location and topology of the computer network. In addition, it becomes possible to monitor and control the network interaction of the client and the specified information services both at the stage of establishing a connection session and at the stage of information exchange, which is not good ...
