ICS information security: Don Quixote in the era of cyber weapons
This article systematizes the requirements for information security (IS) of industrial control systems. The requirements are selected from the currently available standards, primarily from NIST SP 800-82 “Guide to Industrial Control Systems (ICS) Security” and the new revision of the ISA / IEC 62443 series “Security for Industrial Automation and Control Systems” .
Industrial control systems interact with objects of the physical world and provide protection against accidents and disasters. In the English language literature, process control systems are called Industrial Control Systems (ICS) or Industrial Automation and Control Systems (IACS). In the world of IT technologies, they can be compared with Don Quixote, who remained faithful to simple, but not very fashionable principles in a long-changing world.
Therefore, a parallel was drawn with functional safety and a set of requirements was considered, which would ensure both sides of the safety of industrial control systems, both functional and informational.
Similar problems should be addressed for other cyber-physical systems, including IoT and embedded control systems.
What is the difference between process control systems and other information (IT) systems?
Before considering the issue of information security, it would be good to first understand, and what, in fact, is such in ICS, that the issues of their protection and security should be considered separately from the whole world of other IT?
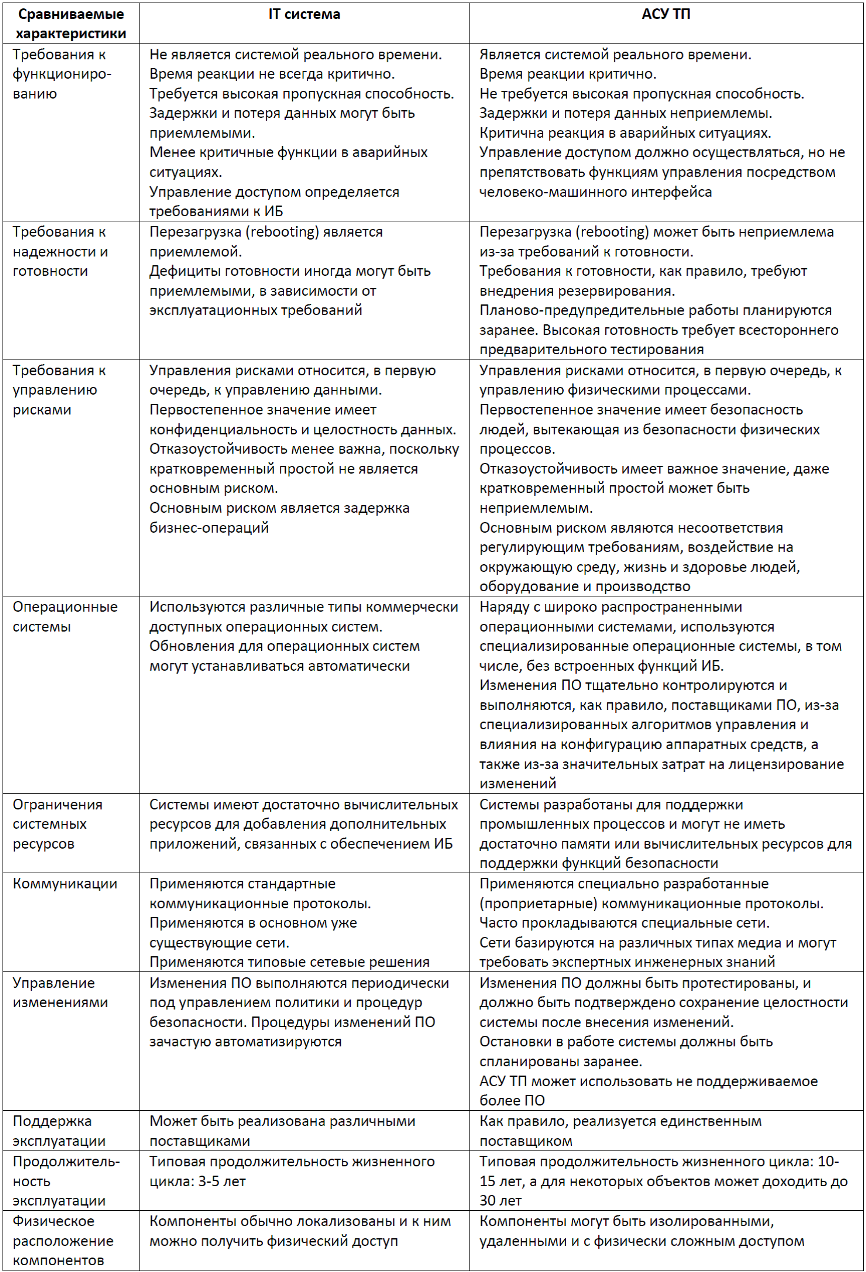
A good comparative analysis answering this question is contained in the already mentioned NIST SP 800-82. The following is a fragment of this document with comparative characteristics of industrial control systems and an abstract information system (IT system). One can argue with some points, however, it must be remembered that the table makes an attempt to concentrate as much as possible on possible differences, which, however, may not be inherent in a particular information system (for example, in a banking system, availability and speed of access are critical )
Comparative analysis of information (IT) systems and process control systems
So what is the problem with information security of process control systems?
In addition to the fact that information security is a problem in itself, the situation in the field of industrial control systems has its own specifics due to the presence of several factors.
Often, all IS maintenance is reduced to consideration of the IS management system (ISMS), although ISMS is a necessary but not sufficient condition for IS provision for ICS. In addition, three levels must be considered in the management of IS automatic process control systems: 1) an enterprise, 2) a program for the development and operation of a series of automatic control systems, 3) a single automatic control system. This is not always remembered, and there is a substitution of concepts when, for an automated process control system, as a technical object, they try to fulfill all the requirements for the ISMS and miss the functional and technical characteristics.
It also happens that information security is considered only from the point of view of high-tech, as a stream of “black” innovations (Stuxnet, BlackEnergy, etc.) and, accordingly, a set of certain measures to protect against them.
Nevertheless, a systematic approach that includes organizational and technical measures (the triad "People - Processes - Technologies") is reasonable.
Another point is the avalanche increase over the past 5-10 years, the number of standards in the field of information security. Many standards are actively being refined and expanded, which creates some chaos in the requirements.
I tried to take into account the standards and technical docs on industrial control systems, as well as those sources to which they refer. The following extensive list was obtained:
- the ISO / IEC 27000 series “Information technology - Security techniques - Information security management systems” is well known to everyone, and it has been discussed many times on the hub, standards are translated into Russian and accepted as GOST R ;
- three parts of ISO / IEC 15408 “Information technology - Security techniques –Evaluation criteria for IT security” or the so-called “Common Criteria” are also translated into Russian and accepted as GOST R ;
- a series of standards ISA / IEC 62443 “Security for Industrial Automation and Control Systems”; these standards require the most careful attention, since they are an "encyclopedia" of information security systems; the first edition was developed by the International Society of Automation (ISA) in the 2000s, and then adapted as a standard by the International Electrotechnical Commission (IEC, IEC in English); in the Russian Federation, some parts of 62433 are also accepted as GOST R ; ISA is currently developing the next edition of 62433; development is behind schedule, but now there is something to read about ; the figure below shows the structure of the planned ISA / IEC 62443 series;

Figure 1. Structure of the ISA / IEC 62443 series of standards.
- The publications of the States National Institute of Standards and Technology (NIST) on the topic of information security include three series: SP 500 Computer Systems , SP 800 Computer Security , SP 1800 Cybersecurity Practice Guides ; NIST developed its own ISMS ( NIST SP 800-53 “Security and Privacy Controls for Federal Information Systems and Organizations” ), as well as the Cybersecurity Framework (SCF) ; but we are most interested in NIST SP 800-82 “Guide to Industrial Control Systems (ICS) Security” ;
- Publications of North American Electric Reliability Corporation (NERC) under the general title Critical Infrastructure Protection (SIP), related primarily to energy systems;
- Cybersecurity Capability Maturity Model (C2M2) , developed by the Department of Energy (DOE);
- Recommended practices developed by the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) , part of the Department of Homeland Security, DHS;
- Framework Control Objectives for Information and Related Technologies (COBIT) , developed by the International Professional Association ISACA;
- Critical Security Controls for Effective Cyber Defense (CIS CSC) framework developed by Center for Internet Security;
- you can also list the standards developed for individual industrial sectors, for example, the AGA 12 series from the American Gas Association (AGA), the API Guide 1164 from the American Petroleum Institute (API), the IEC 62645 standard “Nuclear power plants - Instrumentation and control” used at nuclear power plants systems - Cybersecurity requirements ”, etc.
So, there are many standards, they all represent the subject of information security, they talk about the same thing, but often in different words. The task of harmonizing requirements will be solved in the next section. There is one good news that brightens up the situation somewhat. Almost all standards and technical docs in the field of information security, especially in the field of information security systems, are written in understandable technical language. In this they compare favorably with other standards, for example, in terms of the functional safety of industrial control systems.
Now one more question remains: how to combine the requirements for information security with the requirements for functional security (FB) ? The latter is important in that process control systems manage potentially dangerous physical objects, and this is where their main risks are.
It happens that information security experts do not fully feel the specifics of ICS, that is, if the system is not attacked, then there is no problem. But threats and risks come not only from intruders, but also from incompetent personnel, equipment failures, and environmental influences. And these issues have long been resolved within the framework of the FB through the application of methods for ensuring reliability and managing life cycle processes.
It is also true that the “reliable” are also skeptical about security, not seeing any special problems in cyber threats. Security systems (emergency protection, PAZ) are extremely conservative, since they require large costs for licensing and certification. For example, for nuclear power plants, licensing costs can be up to 10% of the project cost.
So, there is no other way than the interdisciplinary integration of efforts and knowledge. Harmonization of requirements for information security and financial security will also be discussed later in this publication.
The general picture of requirements for information security of
industrial control systems When any technical system associated with possible risks is considered, the algorithm for generating requirements for it is as follows:
- rank the risk levels, associate risks with the functioning of the system, and, thus, rank the required levels of system security;
- identify measures aimed at achieving the required risk levels; in large blocks, such measures are: management system, life cycle processes, technical countermeasures to protect against disruption of health due to failures and / or external influences.
When I thought about this, the overall picture appeared to me in this way.
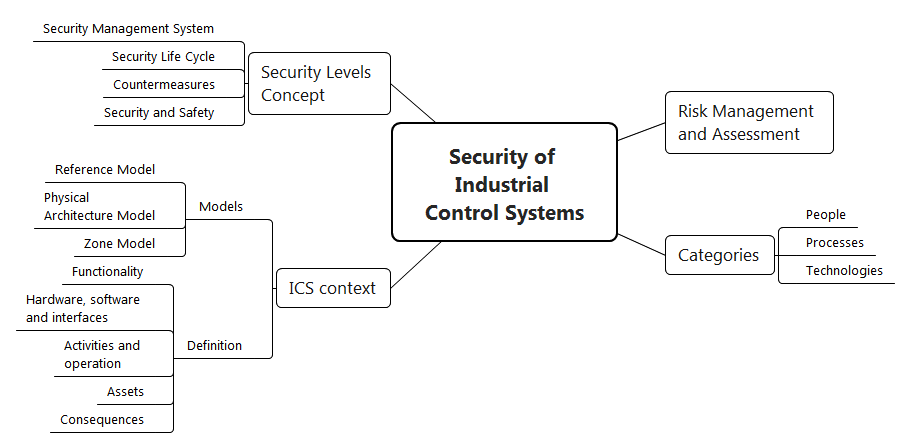
Figure 2. The concept of information security
At the forefront is risk management. The IS context includes an assessment of threats, vulnerabilities and risks, together with an interconnected process of applying countermeasures to reduce risks. The organization of work to ensure an acceptable level of risk is determined by the categories of "people", processes "," technology ".
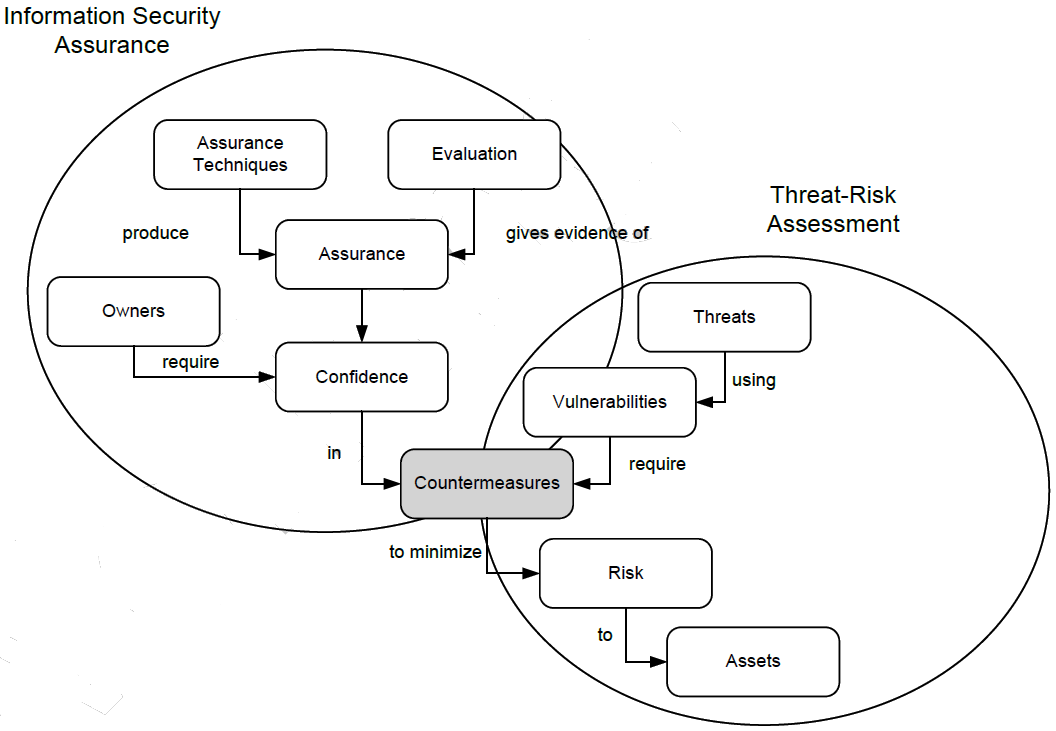
Figure 3. The context of ensuring and assessing information security (source: ISA / IEC 62443)
It is necessary to dwell in more detail on the features of the description of industrial control systems and the concept of information security.
Description of process control systems
To describe the features we will deal with three types of process control models that are proposed to be considered in the interests of information security.
First of all, this is a reference model of automated process control systems that defines five levels:
- Level 4: enterprise management;
- Level 3: operational production management;
- Level 2: management and monitoring of physical processes (SCADA);
- Level 1: local process and equipment control, including protection and safety functions (Control System);
- Level 0: physical process and equipment (sensors and actuators).
What is usually meant by an automatic process control system, in fact, occupies levels 0, 1, and 2.
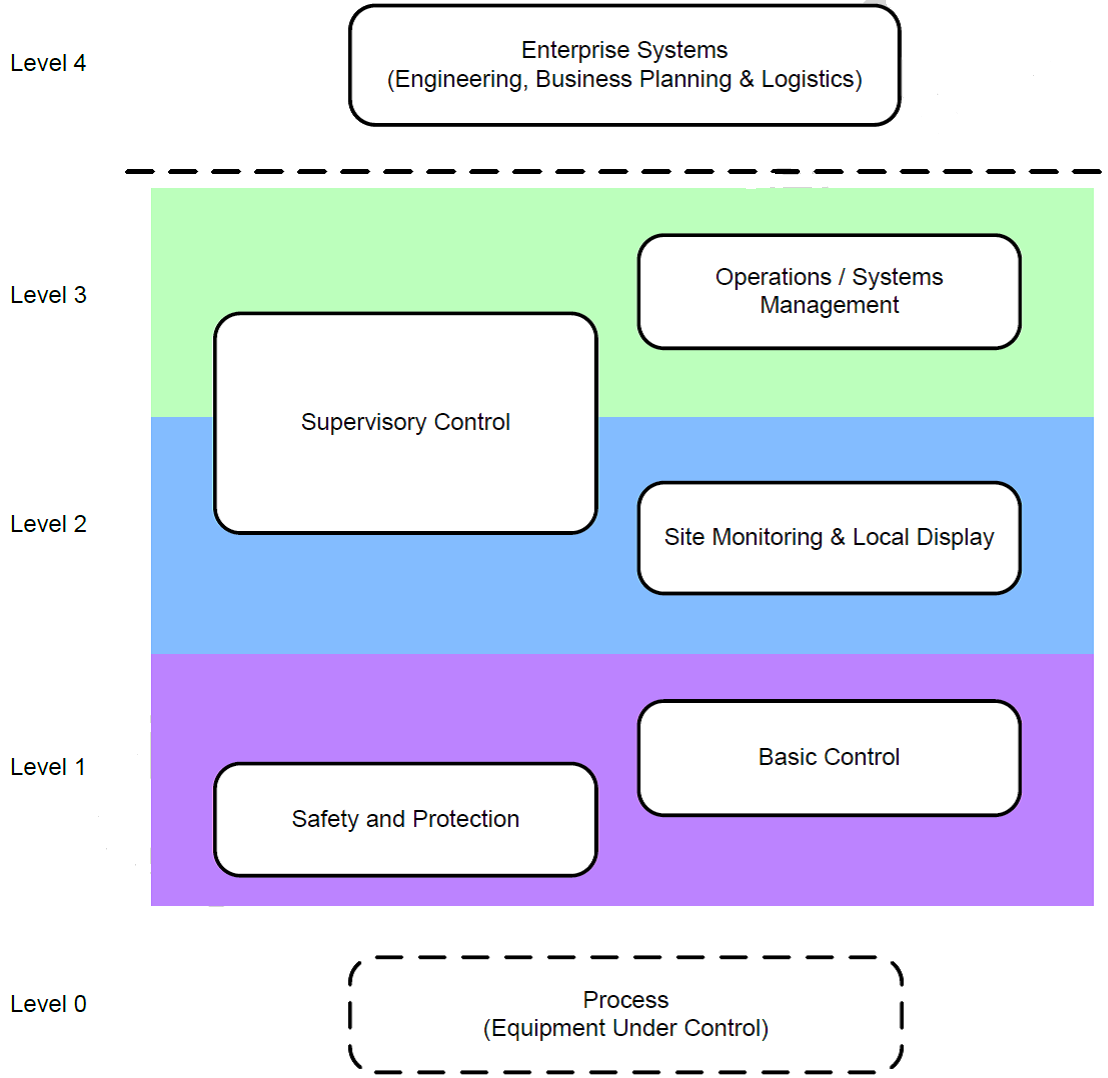
Figure 4. Reference model of an automatic process control system (source: ISA / IEC 62443)
The physical architecture model of an automatic process control system is the most common. It describes the physical components interconnected through networks.

Figure 5. Model of the physical architecture of industrial control systems (source: ISA / IEC 62443)
The automated process control system zoning model can be obtained from the previous model by dividing into groups depending on the requirements for the level of IS security, functional purpose and implemented IS policies. This model is the basis for the analysis of threats, vulnerabilities, risks and countermeasures to reduce risks to the required level.

Figure 6 Zoning model of industrial control system (source: ISA / IEC 62443)
Further, the process of providing information security depends on determining how the automatic control system is used at the target. Such a description includes:
- functions performed;
- applicable software, hardware and network components and interfaces;
- criteria for the implementation of target processes (efficiency, safety, environmental friendliness, etc.);
- tangible and intangible assets involved in the scope of industrial control systems (production facilities, intellectual property, business reputation, product quality, personal and environmental protection equipment, etc.);
- analysis of undesirable consequences consisting in possible financial damage, as well as damage to life and health of people, the environment, production, confidential information and public image.
The concept of ensuring information security
Levels of information security
The basis of the concept of information security is the division of ICS into IS levels (Security Level, SL). IS levels are determined depending on the characteristic threats and vulnerabilities, risks, target functions of parts and components of ICS, and related security policies.
It is believed that the IS levels are borrowed from previously proposed and successfully used in ACS TP levels of the FB, also called the Safety Integrity Level (SIL) .
In the standards, you can find several approaches to the separation of process control systems at the Security Level. We will focus on the zoning proposed all in the same ISA / IEC 62443:
- Security Level 0 (No specific requirements or security protection necessary); determining the level for which IS support measures are not necessary gives rise to some uncertainty, since it is not clear whether IS support can be abandoned at all; in practice, one can be guided by a specific situation and proceed from the principle of reasonable sufficiency; usually the zero level is set not for zones in general, but for individual components, which for some reason do not reach the next level Security Level 1;
- Security Level 1 (Protection against casual or coincidental violation); protection against accidental or coincident IS violations is provided, first of all, by procedural means;
- Security Level 2 (Protection against intentional violation using simple means with low resources, generic skills and low motivation); starting from the second level, protection against malicious violations is considered; the second level deals with ordinary non-specialized attacks, such as viruses or the use of known vulnerabilities; usually such attacks are automatically reflected;
- Security Level 3 (Protection against intentional violation using sophisticated means with moderate resources, ICS specific skills and moderate motivation); at this level, it is necessary to provide protection against intruders with sufficient knowledge and resources to launch an attack on the target system; such attackers exploit little-known vulnerabilities in operating systems and industrial protocols, as well as software tools that require special knowledge;
- Security Level 4 (Protection against intentional violation using sophisticated means with extended resources, ICS specific skills and high motivation); This level differs from the previous one in that here the attacker attracts significant resources, for example, an organized group can use a cluster of computers with high computing power for a long time.
Within the same equipment placement zone (see the automated control system zoning model) it is advisable to provide the same IS level, and between the zones information exchange is carried out through controlled channels and from top to bottom, that is either at the same level of information security, or from a higher security level to a lower security level, but not vice versa.
For each of the IS levels in the automated process control system, several groups of requirements are defined:
- identity and authentication management;
- control over the use of resources;
- ensuring integration (integrity);
- ensuring data confidentiality;
- availability of resources;
- control and restriction of data flows;
- reaction time to events.
Accordingly, the scope of the requirements described below for ISMS, the life cycle of industrial control systems and protective countermeasures depends on the established IS level.
Information Security Management System A
lot of materials already exist on the issue of organizing ISMS. It is important to remember that the ISMS management can be installed at several levels: 1) an enterprise, 2) a program for the development and operation of a series of process control systems, 3) a single process control system.
For the enterprise level ISMS, as for the management system, the Deming cycle is implemented: Plan - Do - Check - Act.
For the ISMS used in the framework of projects for the development of industrial control systems, the life cycle is implemented, which is discussed below.
Information Security Life Cycle
For ACS TP, a V-shaped life cycle is implemented, which is characterized by the implementation of verification and validation measures (reviews, analysis or testing after each of the development stages). An example of a software development life cycle for an automatic process control system is presented below.
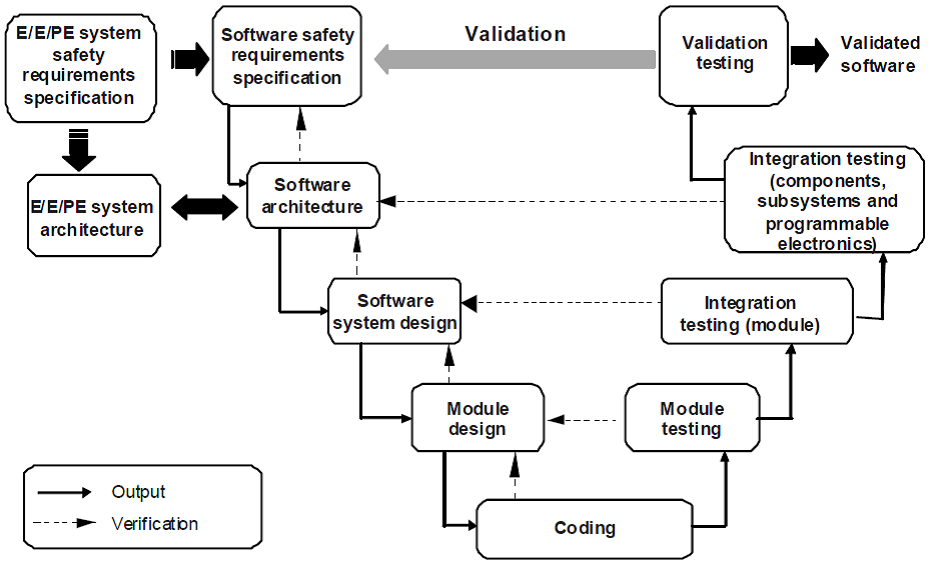
Figure 7. V-shaped process life cycle of automated process control software (source: IEC 61508)
This life cycle implements the requirements for the FB and is therefore called the Functional Safety Life Cycle. In order to comply with the Security Life Cycle, information security requirements must be specified in the specification. Requirements for information security should include the implementation of measures aimed at reducing the risks of countermeasures, such as ensuring confidentiality, integration and accessibility, management of identification and authentication, etc. These requirements are then implemented and verified at all stages of the life cycle.
An important concept of information security is Defense in Depth, which also came from the field of information security. "Defense in depth" is similar to a multi-level defense in depth, when, after an attacker penetrates through one of the defense levels, he meets with a new, possibly fundamentally different defense of the attacked object.
The relationship of information and functional safety
In publications on the topic of functional safety, I was able to reduce the whole variety of requirements to several groups:
- Functional Safety Management;
- implementation of the Functional Safety Life Cycle;
- protection against systematic failures in system and software design (System and Software Failures Avoidance);
- Protection against random hardware failures (Random Failures Avoidance).

Figure 8. The concept of functional safety requirements
If you project these groups of requirements into the IS area, the picture will be approximately the same.
Firstly, based on the role of automated process control systems in providing FB and IS, gradation and separation of systems into levels is performed. Safety Integrity Levels (SIL) are introduced to ensure and evaluate the FB, and Security Levels (SL) are introduced to ensure and evaluate the BF.
Secondly, within the ISMS, information security management should be implemented. Since many of the processes of information security and financial security have an intersection, coordination between them must be implemented.
Thirdly, as was shown above, the development, verification and validation processes aimed at providing both FB and IS can be implemented within a single life cycle (Safety & Security Life Cycle).
Fourthly, in the field of FB and IS there are common risks caused by possible hardware failures. Methods of protection against such failures are backup, diagnostics, protection against interference and other extreme influences, etc. Thus, the same countermeasures are used to ensure IS and FB.
Fifthly, the so-called systematic failures arise in automatic process control systems caused by deficiencies in software design and the system component. The same flaws lead to vulnerabilities that could be exploited by cybercriminals. A number of countermeasures can be used to provide both IS and FB (for example, access control to equipment and information). Thus, there is a need for coordination between countermeasures aimed at ensuring IS and FB.
And finally, within the framework of IS and FB management, measures should be evaluated to ensure these two components of security.
All of the above is presented in the diagram, which can be the basis for coordinating activities to ensure IS and FB.

Figure 9. The concept of harmonized requirements for functional and information security
Conclusions
Features of ensuring information security of industrial control systems are that such systems interact with the processes of the physical world and their primary property is to protect people and the environment from technological risks. Information security of ICS is important, since vulnerabilities can be used just for a physical attack by people, the environment and tangible assets.
In view of the foregoing, the provision and assessment of information and functional safety of industrial control systems should be coordinated within the framework of a single life cycle (Safety & Security Life Cycle).
The solution to the problem of information and functional safety of industrial control systems lies in both organizational and technical areas.
The organizational component, in the first place, is the constant training of personnel and the development of a safety culture in every possible way.
Among the technical measures for the protection of automated process control systems, the most effective is the placement of equipment and software in areas with different levels of information security (Security Level), among which the zone with the emergency protection system (PAZ) has the highest level. Another effective technical measure may be the use of specialized (proprietary) software, such as operating systems and network protocols.
To protect against attacks and cyber incidents, it is necessary to distinguish between random (vulnerabilities caused by random equipment failures) and systematic (vulnerabilities caused by design flaws) components.
To effectively eliminate the first type of vulnerabilities, it is necessary to call upon the good old theory of reliability, supplemented by methods for ensuring functional safety, such as data and power backups, diagnostics, physical protection, transferring equipment and the control object to a safe state, etc.
Other vulnerabilities can and should be eliminated within the framework of experience already gained by the industry, guided by the concept of building defense in depth (Defense in Depth). However, the mechanisms of hacker attacks will also develop, and there can be no zero risk.
The goal of ASU TP has always been a noble service to humanity by protecting it from technological risks. However, as a result of dirty cyber-intrigues, this part of the IT world was completely unprepared for modern realities, speaking with spears at the ready against cyber-weapon windmills.
Obviously, the methods of struggle must be adequate, and in cyber-warfare, ICS are obviously doomed to defeat. Therefore, Don Quixote (ACS TP, and especially emergency protection) must fight with problems in technological processes, and this battlefield must be separated and protected from the rest of cyberspace.
