Retefe malware is used to compromise online banking users
A malicious program called Retefe specializes in compromising users of various banks, including Tesco Bank. Customers of this bank have recently undergone mass account compromise. Retefe is used by cybercriminals to steal online banking data, which can then be used to carry out fraudulent transactions.

According to the BBC news portal , about 40 thousand suspicious banking transactions were recorded over the weekend, with half of them accounted for illegal write-offs of funds. Later, representatives of Tesco Bank confirmed that about 9 thousand customers of the bank suffered as a result of the compromise.
Tesco Bank security specialists decided to temporarily block the possibility of conducting transactions using online banking. At the same time, such functions of bank customers as cash withdrawal, payments using a card chip and its PIN code, and other operations related to paying bills remained active.
Analysis of malware instances by ESET analysts shows that it is aimed at compromising banks from a rather long list of different countries of the world. Note that the malicious campaign began, at least as far back as February 2016. Note that Retefe malware was already actively used by attackers before this campaign, but at the same time, the attackers used other methods of spreading it.
If a user tries to connect to an online banking system from a malware list on a compromised system, Retefe modifies the web page of the online banking site and tries to steal confidential login information.
The initial malware infection occurs through a file that is written in JavaScript and is detected by ESET antivirus products as JS / Retefe . As a mechanism for its distribution, the attackers chose the method of email attachments, disguising it as an invoice, an order notification, etc. After launching, it installs several of its components into the system, including the Tor anonymous network service. These malicious components are used to configure the proxy server when working with banking websites.
When a user tries to access an online banking site, he secretly redirects to a fake copy of this website. Retefe also adds a fake root digital certificate to the system that is disguised as legitimate. For disguise, false information is used that the certificate was issued and confirmed by a well-known certification authority Comodo. This technique significantly complicates the detection of malicious activity by the user. It is obvious that this problem has no relation to the security of a particular bank.

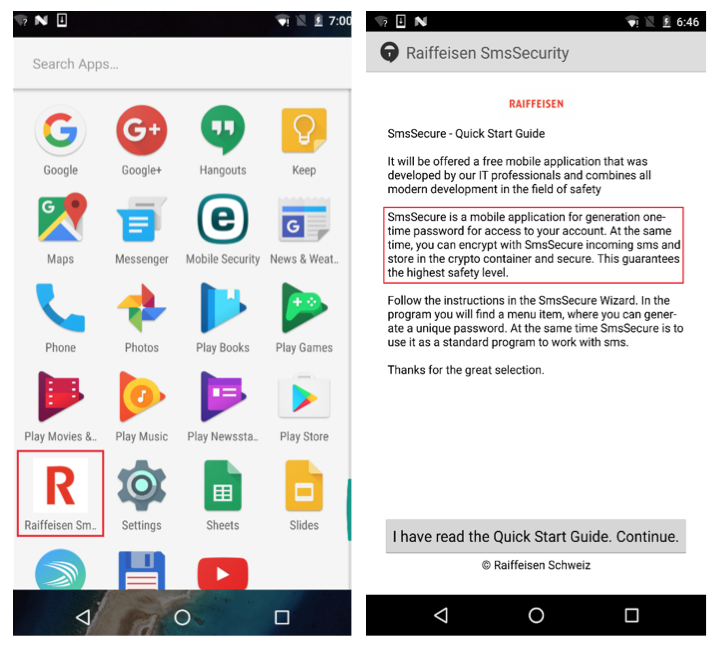
Malicious code can successfully compromise all major web browsers, including Internet Explorer, Mozilla Firefox and Google Chrome. In some cases, Retefe tried to convince the user to install a mobile component that is detected by ESET antivirus products like Android / Spy.Banker.EZ . This mobile component is used to bypass two-factor 2FA authentication. Below are screenshots of this mobile component.


ESET analysts also analyzed another version of the malware, which is detected as JS / Retefe.B . This modification uses a rather cumbersome method of accessing the anonymous Tor network. It does not consist in using the Tor network directly, but through the Tor2Web service.
Retefe was under the lens of antivirus researchers earlier, when earlier this year the malware was actively used to compromise UK banks. Since then, the authors have added a mobile component to it, and also expanded the list of goals.
The users of the online banking services listed below are advised to manually check for the following indicators of compromise by the malware, or use the following ESET web page to check.
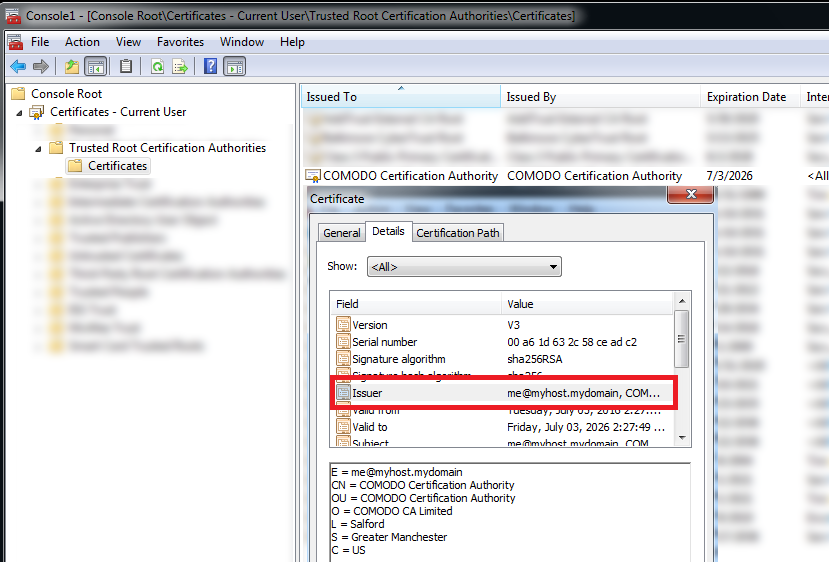
One indicator of compromise is the presence of a fake root digital certificate, which was allegedly issued by a Comodo certification authority. In this case, the email address of the issuing organization corresponds to the address me@myhost.mydomain.
For the Mozilla Firefox web browser, open the certificate manager .

For other web browsers, the presence of a certificate can be checked using the MMC (Microsoft Management Console).
We observed two such fake certificates, information about which is presented below.
Another indicator of compromise is the presence of a malicious Proxy Automatic Configuration (PAC) script in the system , which points to the following .onion domain.
In this case, the% onionDomain% variable is an onion domain arbitrarily selected from the configuration file. The variable% random% is a string of eight characters of the alphabet A-Za-z0-9. % publicIP% points to a public address. An example of such a link is provided below.

A compromising indicator is the presence of the Android / Spy.Banker.EZ malware on the Android device .
If a Retefe malware infection is detected, the following steps must be performed to eliminate this infection.
1. If you used one of the online banking systems that the malware is intended to compromise, change your password to access your online banking account, and also check for the presence of illegitimate operations with a bank account.
2. Remove the Proxy Automatic Configuration (PAC) script from the system

3. Remove the above digital certificate from the system.
4. As a proactive defense, use a reliable security tool with the security function of online banking operations.
The following is a list of online banking websites that Retefe aims to compromise.

According to the BBC news portal , about 40 thousand suspicious banking transactions were recorded over the weekend, with half of them accounted for illegal write-offs of funds. Later, representatives of Tesco Bank confirmed that about 9 thousand customers of the bank suffered as a result of the compromise.
Tesco Bank security specialists decided to temporarily block the possibility of conducting transactions using online banking. At the same time, such functions of bank customers as cash withdrawal, payments using a card chip and its PIN code, and other operations related to paying bills remained active.
Analysis of malware instances by ESET analysts shows that it is aimed at compromising banks from a rather long list of different countries of the world. Note that the malicious campaign began, at least as far back as February 2016. Note that Retefe malware was already actively used by attackers before this campaign, but at the same time, the attackers used other methods of spreading it.
If a user tries to connect to an online banking system from a malware list on a compromised system, Retefe modifies the web page of the online banking site and tries to steal confidential login information.
The initial malware infection occurs through a file that is written in JavaScript and is detected by ESET antivirus products as JS / Retefe . As a mechanism for its distribution, the attackers chose the method of email attachments, disguising it as an invoice, an order notification, etc. After launching, it installs several of its components into the system, including the Tor anonymous network service. These malicious components are used to configure the proxy server when working with banking websites.
When a user tries to access an online banking site, he secretly redirects to a fake copy of this website. Retefe also adds a fake root digital certificate to the system that is disguised as legitimate. For disguise, false information is used that the certificate was issued and confirmed by a well-known certification authority Comodo. This technique significantly complicates the detection of malicious activity by the user. It is obvious that this problem has no relation to the security of a particular bank.

Malicious code can successfully compromise all major web browsers, including Internet Explorer, Mozilla Firefox and Google Chrome. In some cases, Retefe tried to convince the user to install a mobile component that is detected by ESET antivirus products like Android / Spy.Banker.EZ . This mobile component is used to bypass two-factor 2FA authentication. Below are screenshots of this mobile component.



ESET analysts also analyzed another version of the malware, which is detected as JS / Retefe.B . This modification uses a rather cumbersome method of accessing the anonymous Tor network. It does not consist in using the Tor network directly, but through the Tor2Web service.
Retefe was under the lens of antivirus researchers earlier, when earlier this year the malware was actively used to compromise UK banks. Since then, the authors have added a mobile component to it, and also expanded the list of goals.
Checking the system for infection
The users of the online banking services listed below are advised to manually check for the following indicators of compromise by the malware, or use the following ESET web page to check.
One indicator of compromise is the presence of a fake root digital certificate, which was allegedly issued by a Comodo certification authority. In this case, the email address of the issuing organization corresponds to the address me@myhost.mydomain.
For the Mozilla Firefox web browser, open the certificate manager .

For other web browsers, the presence of a certificate can be checked using the MMC (Microsoft Management Console).

We observed two such fake certificates, information about which is presented below.
Serial number: 00: A6: 1D: 63: 2C: 58: CE: AD: C2
Valid from: Tuesday, July 05, 2016
Expires: Friday, July 03, 2026
Issuer: me@myhost.mydomain, COMODO Certification Authority
Serial number: 00: 97: 65: C4: BF: E0: AB: 55: 68
Valid from: Monday, February 15, 2016
Expires: Thursday, February 12, 2026
Issuer: me@myhost.mydomain, COMODO Certification Authority
Another indicator of compromise is the presence of a malicious Proxy Automatic Configuration (PAC) script in the system , which points to the following .onion domain.
hxxp: //%onionDomain%/%random%.js? ip =% publicIP%
In this case, the% onionDomain% variable is an onion domain arbitrarily selected from the configuration file. The variable% random% is a string of eight characters of the alphabet A-Za-z0-9. % publicIP% points to a public address. An example of such a link is provided below.
hxxp: //e4loi7gufljhzfo4.onion.link/xvsP2YiD.js? ip = 100.10.10.100

A compromising indicator is the presence of the Android / Spy.Banker.EZ malware on the Android device .
If a Retefe malware infection is detected, the following steps must be performed to eliminate this infection.
1. If you used one of the online banking systems that the malware is intended to compromise, change your password to access your online banking account, and also check for the presence of illegitimate operations with a bank account.
2. Remove the Proxy Automatic Configuration (PAC) script from the system

3. Remove the above digital certificate from the system.
4. As a proactive defense, use a reliable security tool with the security function of online banking operations.
The following is a list of online banking websites that Retefe aims to compromise.
* .facebook.com
* .bankaustria.at
* .bawag.com
* .bawagpsk.com
* .bekb.ch
* .bkb.ch
* .clientis.ch
* .credit-suisse.com
* .easybank.at
* .eek .ch
* .gmx.at
* .gmx.ch
* .gmx.com
* .gmx.de
* .gmx.net
* .if.com
* .lukb.ch
* .onba.ch
* .paypal.com
* .raiffeisen .at
* .raiffeisen.ch
* .static-ubs.com
* .ubs.com
* .ukb.ch
* .urkb.ch
* .zkb.ch
* abs.ch
* baloise.ch
* barclays.co.uk
* bcf .ch
* bcj.ch
* bcn.ch
* bcv.ch
* bcvs.ch
* blkb.ch
* business.hsbc.co.uk
* cahoot.com
* cash.ch
* cic.ch
* co-operativebank.co.uk
* glkb.ch
* halifax-online.co.uk
* halifax.co.uk
* juliusbaer.com
* lloydsbank.co.uk
* lloydstsb.com
* natwest.com
* nkb.ch
* nwolb.com
* oberbank.at
* owkb.ch
* postfinance.ch
* rbsdigital.com
* sainsburysbank.co.uk
* santander.co.uk
* shkb.ch
* smile.co.uk
* szkb.ch
* tescobank.com
* ulsterbankanytimebanking.co.uk
* valiant.ch
* wir.ch
* zuercherlandbank.ch
accounts.google.com
clientis.ch
cs.directnet.com
e-banking.gkb.ch
eb.akb.ch
ebanking.raiffeisen.ch
hsbc.co.uk
login.live.com
login.yahoo.com
mail.google.com
netbanking.bcge.ch
onlinebusiness.lloydsbank .co.uk
tb.raiffeisendirect.ch
uko.ukking.co.uk
urkb.ch
wwx.banking.co.at
wwx.hsbc.co.uk
wwx.oberbank-banking.at
wwwsec.ebanking.zugerkb.ch
