Solar Dozor - what is behind the stars?
During the work with the Watch we have seen everything. But there is always one thing - at the first meeting, the system leaves very few people indifferent. One group of clients meets the demonstration with the words: “Well, finally! DLP, where everything is simple and clear! ". However, they are wrong. Another something like “Yes, this is a toy of some kind. It will not be powerful enough for us. ” But they are wrong. So what's behind the stars?

As in the previous article , the issues of technical requirements, stability and completeness of control will be left out of the brackets. Zoo software, the scale and tasks of all are different, and DLP - a piece of fine mental organization. As a result, about what vendor on the square or shout, those who “fell”, “braked”, “could not” will come running first. [ And it just so happened that we are just ready to help - “lift”, “speed up” and “pull”. But that's another story. ]
Let's return to the fact that, like any information system, Dozor tries to balance between power and simplicity. Yes, so that both components unscrew the maximum. But is it possible?
Meets us simplicity - dashboard. Everything is beautiful, clear, in pictures. The dashboard of the head - in general a fairy tale - trends on violations, TOP violators, assessment of the load on the team. But what is behind this, where does all this content come from?
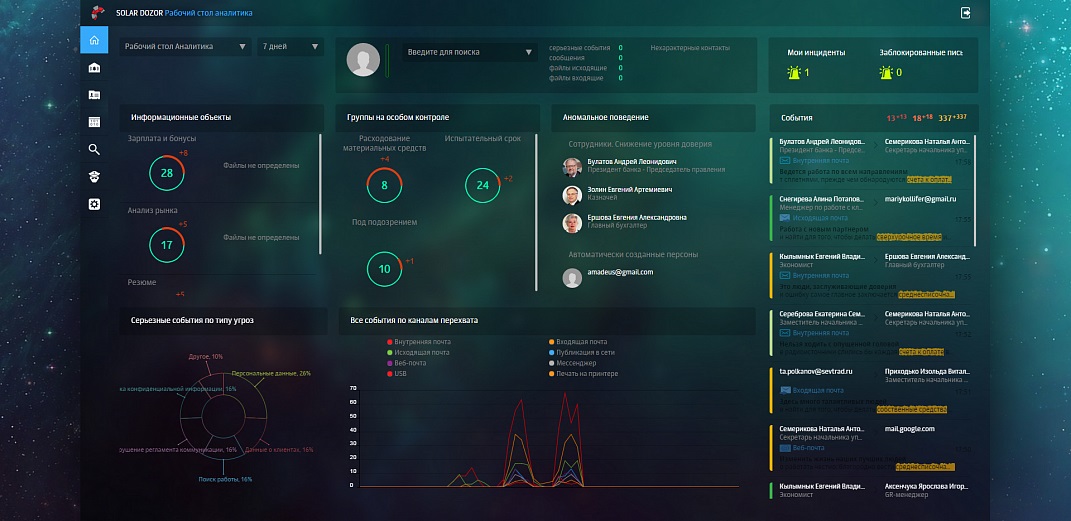
1. Desktop (dashboard)
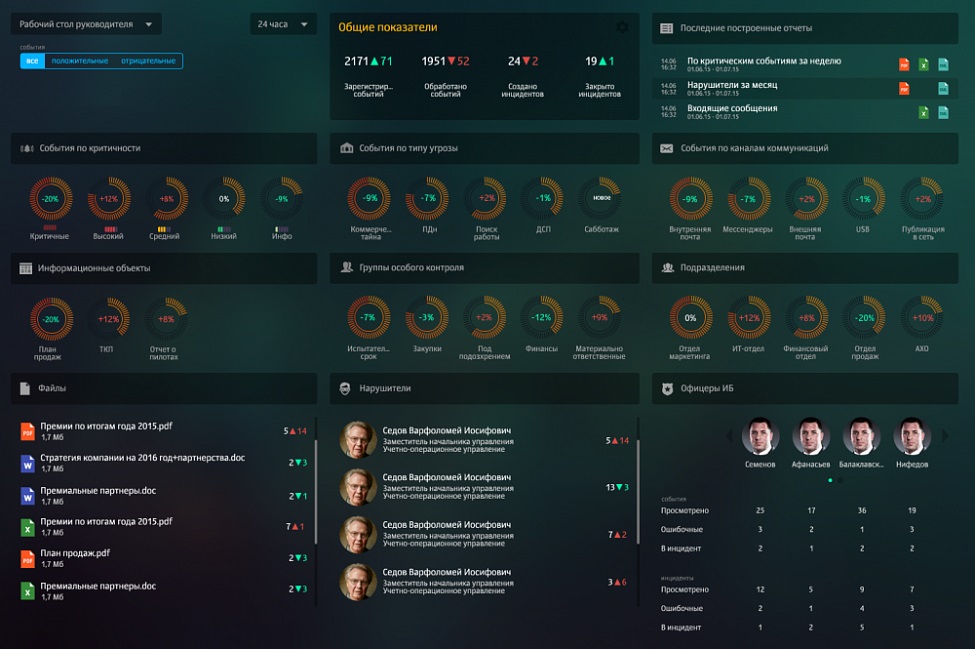
2. Desktop manager
At the heart of everything is the principle of operating information objects. And here it is, the moment where the functional displaces visibility. We have quite a big team and after the first acquaintance with the system we spent a lot of time, slides and felt-tip pens to understand what was going on here. In short and simplifying, the system using a policy consisting of rules that operate with information objects, specified criteria with the ability to use templates, creates events from messages that can become incidents.

3. At what level are you now?
A little scary, right? The good news is that it is not necessary to understand this to work with the system. At least the whole team. Find / hire / rent the person who sets it all up. For everyone else, let magic fly the plane.
4. Scheme for identifying critical information
The most important thing is that the system generates “events” from the information flow — notifications that something is probably wrong. And then again, beauty. The event has a beautiful card, which briefly describes who did what and in what way. For simplicity, the cards are ranked by severity and type of action (again magic). It remains to carefully look at her and check whether the spell worked correctly.
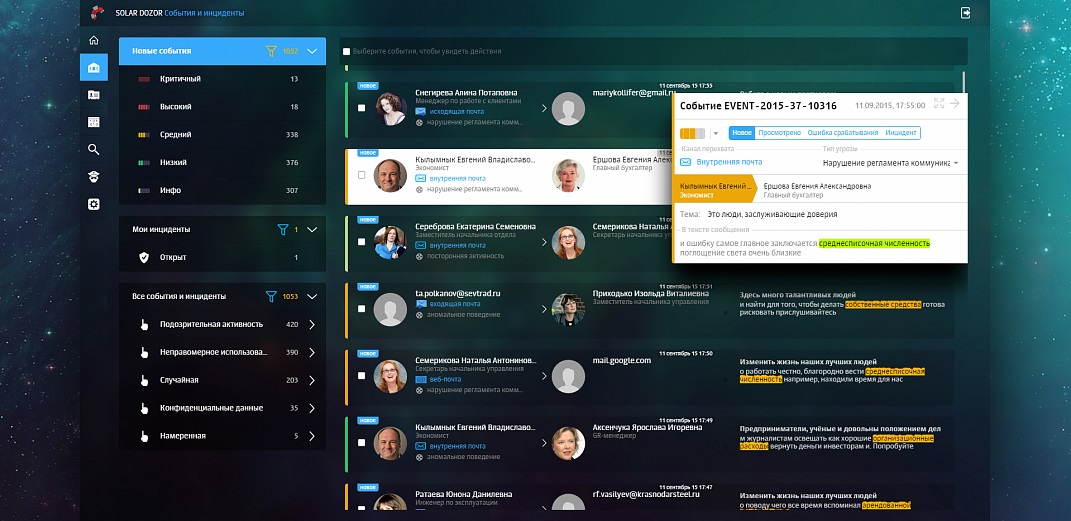
5. Events in the system
In one click we give the wrong to our magician to "finish it", and fix the correct one as an incident. Fixed? We shout to the next room: “Colleagues, take to work!”. But no, the system asks to designate the person in charge. Assign - the most responsible receives a notification. As a result, each event has a status, and each incident - responsible. Lost nothing. The system took into account the statuses and considers those very trends. Beauty.
What else is this magic capable of? Interrupt data transfer if they are classified as an information object. Issue warnings of a potential violation (on the same principle). Suspend mail to quarantine (and immediately notify about it on the dashboard). Modify letters, removing critical objects. Distribute violators to special control groups.
With the main routine sorted out. Next - look into the past - search. And once again we are greeted by beauty - a simple search. With habitual movements we “google” the information in the search bar. Lacks? Go to the advanced search mode. And again, visibility leaves us. Many searchable attributes are fine, but try to distinguish the sender from person or source or even source person. So also logical operations are performed in a not very obvious order. Complicated. But smart search is good - it allows you to find similar files among all communications - just a couple of buttons, and what a space for creativity.
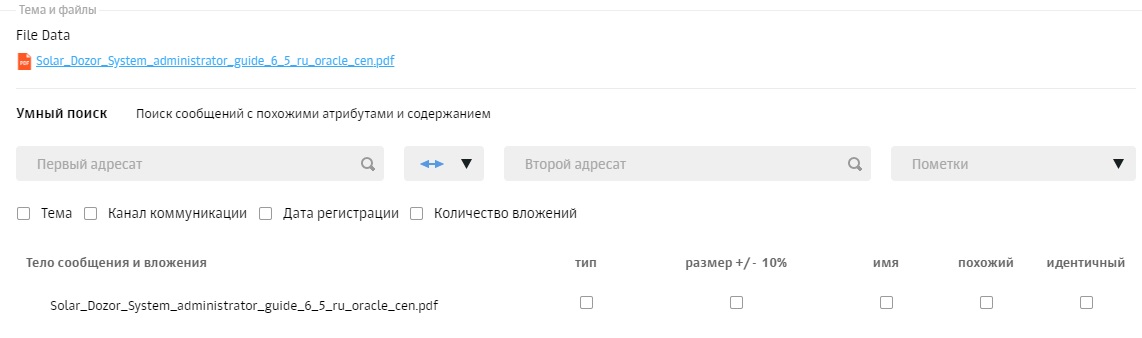
6. Smart search
Dossier. Beauty again. All information on the person so also all the statistics on violations (again, the magic of information objects). The graph of links in the set, however, neither beauty nor power is different.
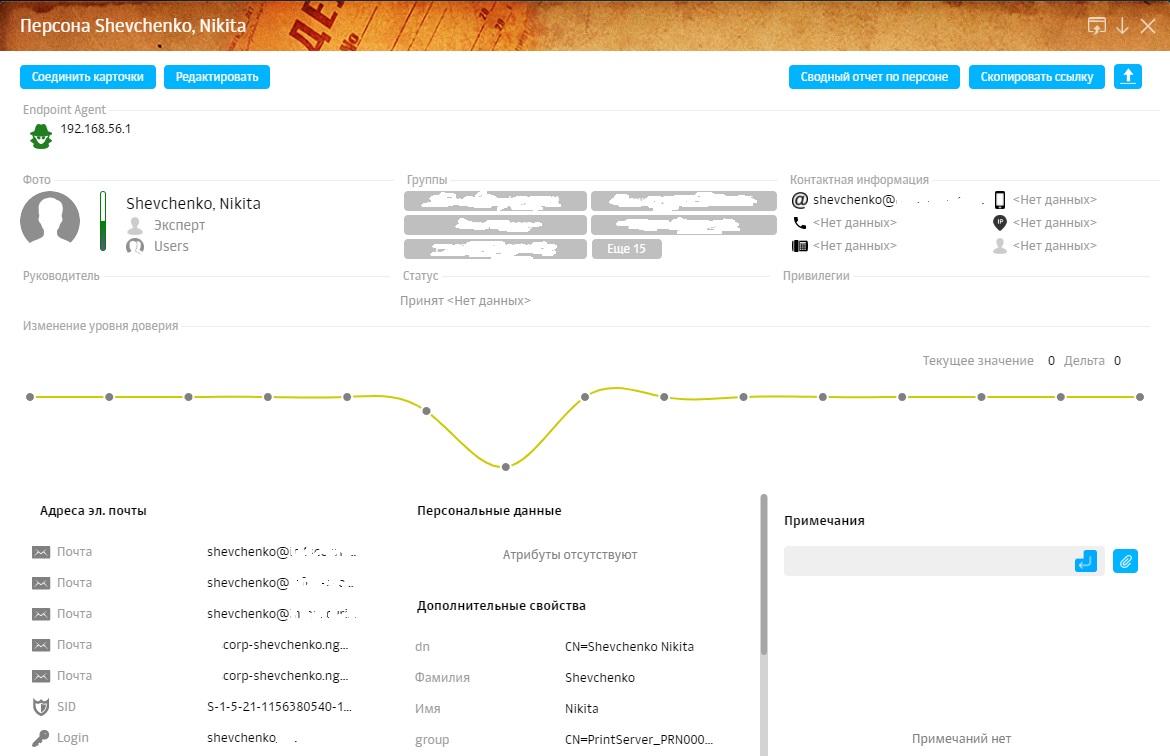

7. Example dossier
Reports. The choice, of course, is not rich. But the “Heat Map Communications” is a very useful thing. Few people will be able to tell at a glance in which departments what information is being processed. And it is often difficult to even determine where any communication channels are used. This is where the heat map will help. All activity of the selected group of employees will be divided into categories, and then we draw conclusions: which actions are normal, and which ones - anomaly.

8. Heatmap
Useful at the start of the setup, useful in further work. The remaining reports are more likely to be able to transfer to colleagues / management everything that we ourselves see in various sections of the system.
Eventually.
There, behind the stars, dark and scary. Perhaps sometime beauty will get there. Or maybe it is unrealistic - to make the complex very simple. But for now, deep into the system, we recommend sending there only specially trained people with a supply of vital manuals.

9. Setup Group
But one of the most friendly systems is waiting for those remaining on the surface.
Nikolay Postnov, Head of Configuration Direction, DLP Block, Infosecurity a Softline Company.

As in the previous article , the issues of technical requirements, stability and completeness of control will be left out of the brackets. Zoo software, the scale and tasks of all are different, and DLP - a piece of fine mental organization. As a result, about what vendor on the square or shout, those who “fell”, “braked”, “could not” will come running first. [ And it just so happened that we are just ready to help - “lift”, “speed up” and “pull”. But that's another story. ]
Let's return to the fact that, like any information system, Dozor tries to balance between power and simplicity. Yes, so that both components unscrew the maximum. But is it possible?
Meets us simplicity - dashboard. Everything is beautiful, clear, in pictures. The dashboard of the head - in general a fairy tale - trends on violations, TOP violators, assessment of the load on the team. But what is behind this, where does all this content come from?

1. Desktop (dashboard)

2. Desktop manager
At the heart of everything is the principle of operating information objects. And here it is, the moment where the functional displaces visibility. We have quite a big team and after the first acquaintance with the system we spent a lot of time, slides and felt-tip pens to understand what was going on here. In short and simplifying, the system using a policy consisting of rules that operate with information objects, specified criteria with the ability to use templates, creates events from messages that can become incidents.

3. At what level are you now?
A little scary, right? The good news is that it is not necessary to understand this to work with the system. At least the whole team. Find / hire / rent the person who sets it all up. For everyone else, let magic fly the plane.

4. Scheme for identifying critical information
The most important thing is that the system generates “events” from the information flow — notifications that something is probably wrong. And then again, beauty. The event has a beautiful card, which briefly describes who did what and in what way. For simplicity, the cards are ranked by severity and type of action (again magic). It remains to carefully look at her and check whether the spell worked correctly.

5. Events in the system
In one click we give the wrong to our magician to "finish it", and fix the correct one as an incident. Fixed? We shout to the next room: “Colleagues, take to work!”. But no, the system asks to designate the person in charge. Assign - the most responsible receives a notification. As a result, each event has a status, and each incident - responsible. Lost nothing. The system took into account the statuses and considers those very trends. Beauty.
What else is this magic capable of? Interrupt data transfer if they are classified as an information object. Issue warnings of a potential violation (on the same principle). Suspend mail to quarantine (and immediately notify about it on the dashboard). Modify letters, removing critical objects. Distribute violators to special control groups.
With the main routine sorted out. Next - look into the past - search. And once again we are greeted by beauty - a simple search. With habitual movements we “google” the information in the search bar. Lacks? Go to the advanced search mode. And again, visibility leaves us. Many searchable attributes are fine, but try to distinguish the sender from person or source or even source person. So also logical operations are performed in a not very obvious order. Complicated. But smart search is good - it allows you to find similar files among all communications - just a couple of buttons, and what a space for creativity.

6. Smart search
Dossier. Beauty again. All information on the person so also all the statistics on violations (again, the magic of information objects). The graph of links in the set, however, neither beauty nor power is different.


7. Example dossier
Reports. The choice, of course, is not rich. But the “Heat Map Communications” is a very useful thing. Few people will be able to tell at a glance in which departments what information is being processed. And it is often difficult to even determine where any communication channels are used. This is where the heat map will help. All activity of the selected group of employees will be divided into categories, and then we draw conclusions: which actions are normal, and which ones - anomaly.

8. Heatmap
Useful at the start of the setup, useful in further work. The remaining reports are more likely to be able to transfer to colleagues / management everything that we ourselves see in various sections of the system.
Eventually.
There, behind the stars, dark and scary. Perhaps sometime beauty will get there. Or maybe it is unrealistic - to make the complex very simple. But for now, deep into the system, we recommend sending there only specially trained people with a supply of vital manuals.

9. Setup Group
But one of the most friendly systems is waiting for those remaining on the surface.
Nikolay Postnov, Head of Configuration Direction, DLP Block, Infosecurity a Softline Company.
