ATM Attacks: Past, Present, and Future
 In a post about the Internet of things, I, almost with a dash bare, referred to such ATMs as well - according to the criteria of battery life and the presence of a permanent Internet connection. In general, everything is true, but if we turn from words to deeds - that is, to the real specifics of protecting ATMs from hacking, then many uncomfortable details immediately arise. A modern ATM is a full-fledged computer, sharpened for one specific task, but suitable for running any code, including malicious code. The ATM is laden and comes in contact with many sensors and specialized devices through which the ATM can be cracked. And you can not hack it by taking control of a device for dispensing cash or a keyboard for entering a PIN code.
In a post about the Internet of things, I, almost with a dash bare, referred to such ATMs as well - according to the criteria of battery life and the presence of a permanent Internet connection. In general, everything is true, but if we turn from words to deeds - that is, to the real specifics of protecting ATMs from hacking, then many uncomfortable details immediately arise. A modern ATM is a full-fledged computer, sharpened for one specific task, but suitable for running any code, including malicious code. The ATM is laden and comes in contact with many sensors and specialized devices through which the ATM can be cracked. And you can not hack it by taking control of a device for dispensing cash or a keyboard for entering a PIN code.There are many scenarios when something can go wrong with an ATM, and most of them are based not on a theoretical analysis of potential vulnerabilities, but on the practice of analyzing real attacks. The banking sector as a whole is much more protected than other industries, but cybercriminals have more attention to it: real money is at stake. Nevertheless, it would be nice to somehow systematize the weaknesses of the banking infrastructure, which was recently done by the specialists of the Laboratory Olga Kochetova and Alexey Osipov.
As is the case with the Lurk campaign investigation history , this text is a free retelling of the original sources. I send them for details: this is a review article on Securelist in Russian, a study“Future scenarios of attacks on communication systems interacting with ATMs” in English, a brief squeeze from there - only a description of attacks and methods of counteraction, as well as earlier publications: a description of the Skimer malware and a targeted attack on Tyupkin ATMs .
Do you remember how it all started
Attacks on ATMs are not a completely new topic. The first version of the Skimer malware appeared in 2008-2009. The attack is aimed directly at the ATMs: in one of the current versions (Skimer exists and is still developing) after infection of the ATM, it can be controlled by inserting a prepared card with a “key” on the magnetic strip into the ATM.
His napping!
According to its name, Skimer can activate the collection of data from cards inserted into the ATM, but it can also be used to directly steal cash - the corresponding command is provided in the control menu. Skimer integrates into the legitimate SpiService.exe process, as a result of which it gets full access to XFS - a universal client-server architecture for financial applications for Windows-systems.
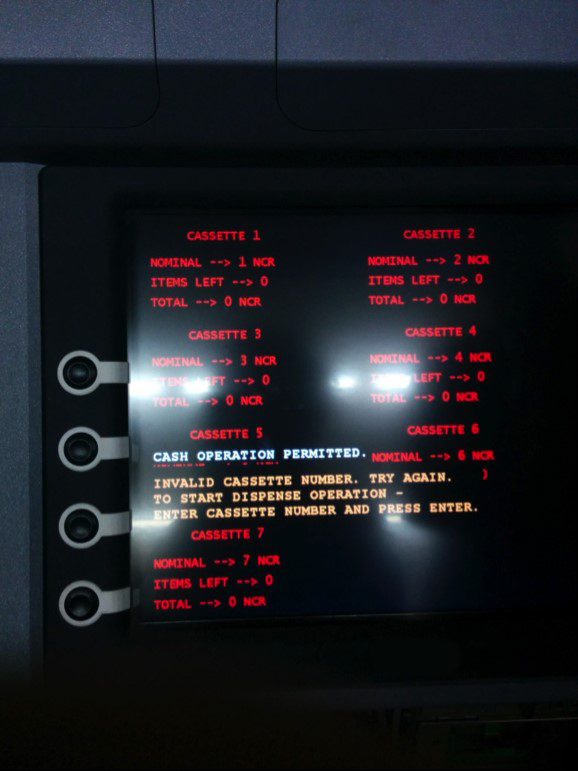
Unlike Skimer, the Tyupkin attack, researched in the Lab in 2014, does not use prepared maps. Instead, it provides for the activation of malicious code at a certain time of the day, and even at that time it is possible to seize control of an ATM only after entering a dynamic authorization code. The consequences of a successful attack, however, are about the same:
Carbanak and company
Actually, the most interesting in these two examples is the infection process, which sometimes has to be restored from surveillance camera records. In the case of Tyupkin, malware was installed from a CD (!), That is, there was physical access to the insides of the ATM. This is an obvious attack vector with no less obvious flaws. But he is not the only one.
In the Carbanak campaign, detailswhich the Laboratory’s experts discovered in February last year, ATMs are used last, silently giving the cache on command from the center, without any manipulation on the spot. The infrastructure of the victims was compromised, due to which the main damage was caused, as they say, by bank transfer. When losses are measured in the hundreds of millions of dollars, cash ceases to play a significant role.
The trend was developed this year as well: in February we talked about three new attacks, two of which were aimed at cashless theft of funds. Only one campaign (Metel) provided for the withdrawal of funds through ATMs, but no one hacked the devices themselves. Technically, the transaction (withdrawing money from the account) was legitimate, but after it the card balance rolled back to its previous value. The modern version of the unchangeable nickel was exploited, as was the case with other attacks, at night, preferably on the weekend.

Cybercriminals will attack the root infrastructure of financial institutions as long as they have such an opportunity, that is, while it will be vulnerable. As history showswith robbery through the SWIFT interbank transfer system, even critical elements of the financial infrastructure are not always properly protected (doesn’t it turn out that ATM protection is sometimes better?). I want to believe that this is not for long. Given that cybercrime does not think about ATMs, they are the ones who claim the dubious privilege of the long-term headache of the financial industry.
Which way to be afraid ?
In their analysis of the future vectors of attacks on ATMs, our experts are not limited to direct theft of cash. To this understandable goal, we add the theft of customer data for the subsequent withdrawal of funds in larger volumes with lower chances to light up on the surveillance camera. But that is not all. If you look closely, then in the entire IT “bundle” of the ATM network you will not be able to find a place that could not be attacked.
An interesting example is the biometric identification of customers - a relatively new technology that allows you to either replace or supplement the standard means of authorization - by PIN, using NFC and so on. The theft of biometric data is theoretically possible through appropriately doped skimers (in the event that biometry comes once again on the rake previously traveled with card readers), through an attack such as Man-in-the-middle (when the ATM starts sending data to someone else’s processing server), or through an attack on the infrastructure of a financial organization.
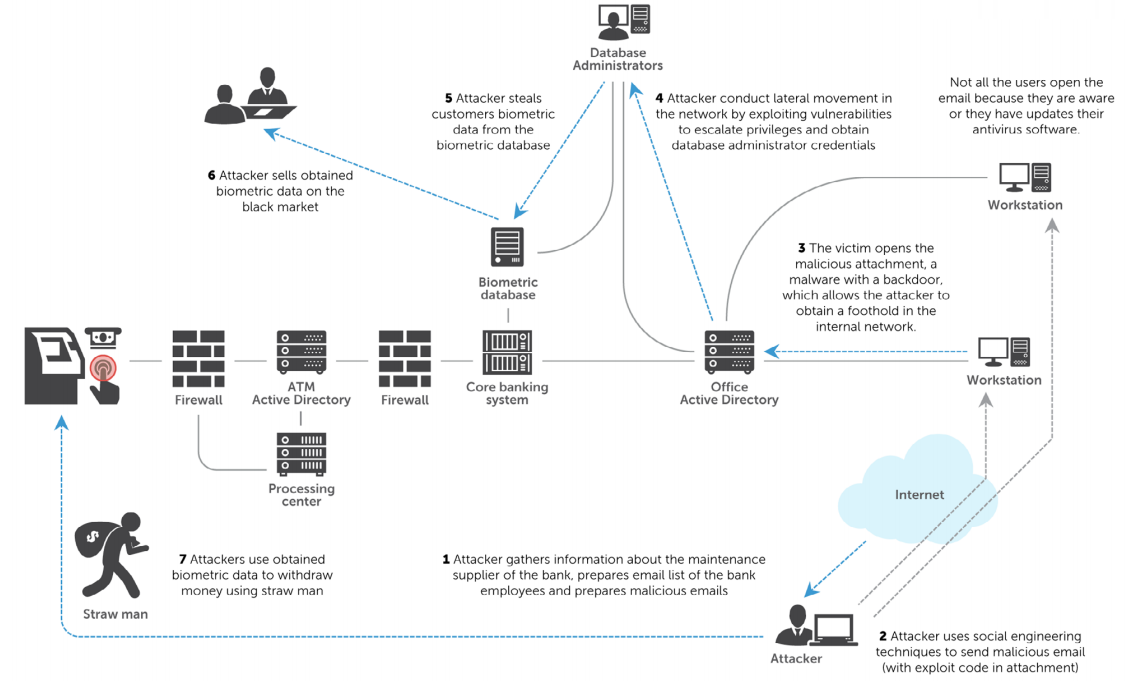
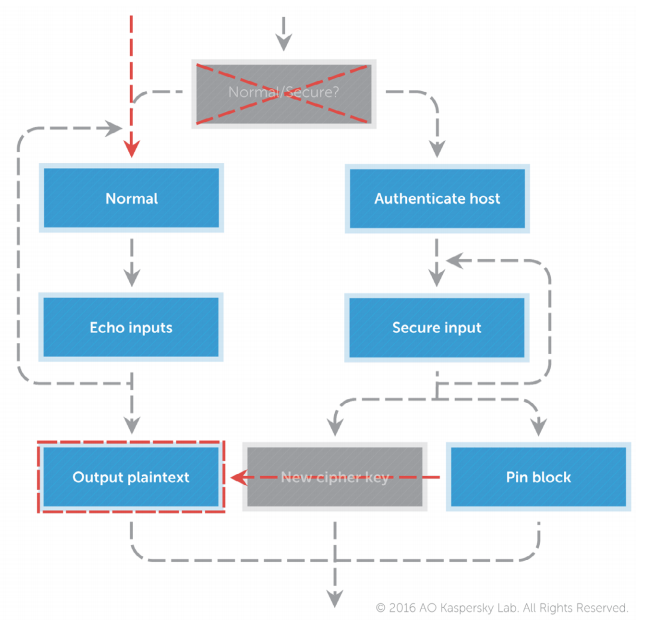
Further use of biometrics to steal funds is still in question, and is not described in detail. But there is an important nuance: if cybercriminals learn to do this, we will get an analogue of the situation with cloned credit cards, but without the possibility of “re-issuance” (fingerprints, voices, etc.). It is not a fact that fingerprint simulators will have to be invented: in a separate chapter of the study, attack scenarios on PIN pads are given, during which data can be intercepted, or can be replaced, with forced encryption disabled. Is it possible to implement this for a biometric sensor? Why not.
What to do?
The report does not address the topic of obsolete hardware in ATMs - although this presents a certain problem in terms of security, solutions even for ancient devices exist. In general, an integrated approach to threat scenarios involves an equally diverse list of measures to prevent them. At least in three areas: network, software and hardware (plus it is advisable not to forget about the training for staff). For all three, there is an obvious need for secure data transfer at all stages and authenticity checks - otherwise it becomes possible that a “foreign” control module is simply connected to the cash dispenser. Separately, the program part offers strict control over the launch of unauthorized code: for ATMs, unlike ordinary computers, this is relatively easy to implement. Finally,

Guess the axis according to Adobe Reader
Although some of the attack scenarios shown in the report (so far) are theoretical, together with the “practical” they add up to an interesting picture. Financial institutions have to deal with both specific threats (attack on SWIFT, Carbanak - hacking with knowledge of internal processes), and common ones (phishing, exploitation of vulnerabilities, configuration errors, and so on). We add here traditional skimers, physical hacking of ATMs, difficulties with updating software and hardware (my own proof is in the photo above). On the one hand, all this makes one gigantic vulnerability. On the other hand, there are a lot of resources for protection, albeit monetary, at least expert. So in the future, the financial sector can bring us both new examples of high-profile cyber-hacking and truly innovative protection models.
Disclaimer: This column is based on real events, but still reflects only the private opinion of its author. It may coincide with the position of Kaspersky Lab, or it may not coincide. That's how lucky.
