Bypass VMware Detection by Programs in VMWare
- Tutorial
Virus software developers and simply developers who do not want their program to be reversed, check the virtual machine at the startup or installation stage, and if it is detected, they refuse to work, or even completely self-destruct. Under the cat, a method is described how you can try to solve this problem.
I used VMWare Fusion for Mac, but it works just as well in Workstation for Win.
1) To work, you need a newly installed system, I did not find how to make changes to an existing one.
Prepare a virtual disk, indicate the system as you usually do, and in the settings for the installed machine, I have this item called Isolation, turn off any data exchange with the host OS.
2) Next, you need to find the VMX configuration file created at the stage of creating the machine in VMWare, and add the lines to the end:
These options prevent programs from detecting virtual environments through sophisticated checks such as tracking memory address space and counters.
Important! If at the installation setup stage there is an option like “Express install”, “Quick install” - turn them off. Also, do not install VMWare Tools in the installed system, as some software also includes the availability of this package.
3) We save the file, specify to download the ISO with the installer of the system, install the OS as usual.
4) Despite the fact that the vast majority of programs that do not like the virtual environment do not go beyond the checks that we cut off in step 2, some particularly persistent ones go further and try to search, for example, everything that looks like the name of virtual controllers drives.
To defeat them in Windows, we go to the registry editor in the HKLM \ SYSTEM \ CurrentControlSet \ Services \ Disk \ Enum branch. As you can see, there is a clear reference to the fact that the disk is virtual.

We need to change it by removing VMware, Virtual, Ven, etc. from the parameter, and save it like that.
It also makes sense to replace everything that changes in the registry by searching for VMware / Virtual with Intel or IBM, and not just disk variables.
After that, try to run your stubborn object of experiments - in 70 percent of the cases, the steps described will help you pass the tests for a virtual environment.
Important! The value in HKLM \ SYSTEM \ CurrentControlSet \ Services \ Disk \ Enum is overwritten after each reboot, so it must be changed after each new system startup.
You can check how much you have secured yourself against detection, as well as familiarize yourself with other means of detecting sandboxes and virtual machines that are popular with developers, using Pafish .
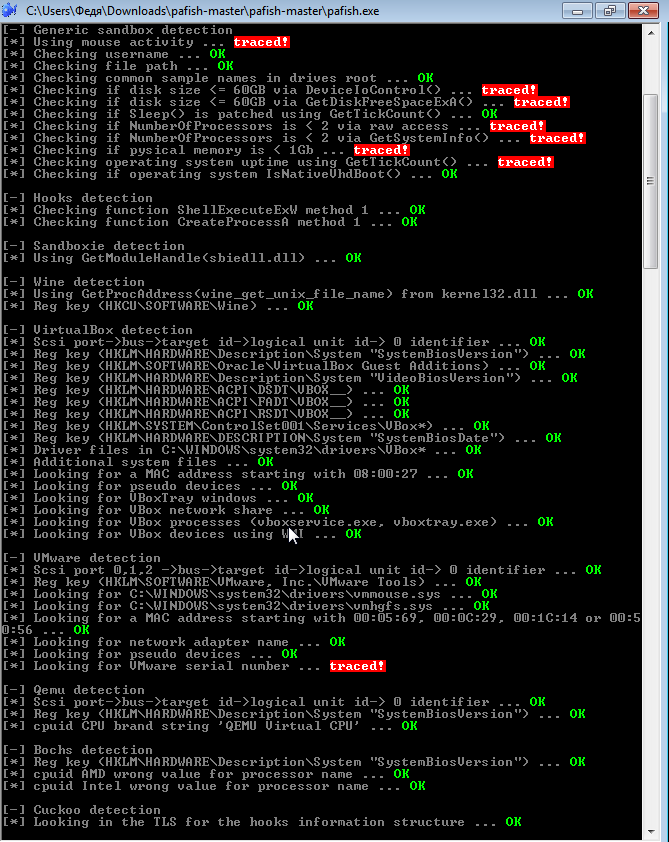
Despite the fact that there are places where you can give yourself away, the proposed method makes you outwit most software that does not want to work in a virtual environment, in this case, in VMWare.
As you can see, secrecy can also be improved by allocating more system resources to the virtual machine. As for memory, it’s worth choosing values that are multiples of 1024.
Thanks to everyone who mastered the article and helped to supplement it with sensible comments!
I used VMWare Fusion for Mac, but it works just as well in Workstation for Win.
1) To work, you need a newly installed system, I did not find how to make changes to an existing one.
Prepare a virtual disk, indicate the system as you usually do, and in the settings for the installed machine, I have this item called Isolation, turn off any data exchange with the host OS.
2) Next, you need to find the VMX configuration file created at the stage of creating the machine in VMWare, and add the lines to the end:
isolation.tools.getPtrLocation.disable = "TRUE"
isolation.tools.setPtrLocation.disable = "TRUE"
isolation.tools.setVersion.disable = "TRUE"
isolation.tools.getVersion.disable = "TRUE"
monitor_control.disable_directexec = "TRUE »
Monitor_control.disable_chksimd =" TRUE "
monitor_control.disable_ntreloc =" TRUE "
monitor_control.disable_selfmod =" TRUE "
monitor_control.disable_reloc =" TRUE "
monitor_control.disable_btinout =" TRUE "
monitor_control.disable_btmspace =
TRUE
monitor_control.disable_btseg = "TRUE"
These options prevent programs from detecting virtual environments through sophisticated checks such as tracking memory address space and counters.
Important! If at the installation setup stage there is an option like “Express install”, “Quick install” - turn them off. Also, do not install VMWare Tools in the installed system, as some software also includes the availability of this package.
3) We save the file, specify to download the ISO with the installer of the system, install the OS as usual.
4) Despite the fact that the vast majority of programs that do not like the virtual environment do not go beyond the checks that we cut off in step 2, some particularly persistent ones go further and try to search, for example, everything that looks like the name of virtual controllers drives.
To defeat them in Windows, we go to the registry editor in the HKLM \ SYSTEM \ CurrentControlSet \ Services \ Disk \ Enum branch. As you can see, there is a clear reference to the fact that the disk is virtual.

We need to change it by removing VMware, Virtual, Ven, etc. from the parameter, and save it like that.
It also makes sense to replace everything that changes in the registry by searching for VMware / Virtual with Intel or IBM, and not just disk variables.
After that, try to run your stubborn object of experiments - in 70 percent of the cases, the steps described will help you pass the tests for a virtual environment.
Important! The value in HKLM \ SYSTEM \ CurrentControlSet \ Services \ Disk \ Enum is overwritten after each reboot, so it must be changed after each new system startup.
@Denisoid UPD :
Naturally, this is not an exhaustive guide, some software may also try to determine the virtual system using the following methods:
1) MAC address range checks (it is simply replaced in the settings of the virtual network adapter before starting the virtual machine)
2) Through WinAPI, by polling the OS configuration and other system information (FirmwareTable)
3) Low-level tricks.
You can check how much you have secured yourself against detection, as well as familiarize yourself with other means of detecting sandboxes and virtual machines that are popular with developers, using Pafish .

Despite the fact that there are places where you can give yourself away, the proposed method makes you outwit most software that does not want to work in a virtual environment, in this case, in VMWare.
As you can see, secrecy can also be improved by allocating more system resources to the virtual machine. As for memory, it’s worth choosing values that are multiples of 1024.
Thanks to everyone who mastered the article and helped to supplement it with sensible comments!
