"Two unfiltered" or easy way to shoot a leg
Already several times in the reports on incidents of routing, we talked about the possible consequences of the absence of BGP announcements filters at the interfaces with clients. Such an incorrect configuration most of the time will work perfectly fine - until one day it becomes guilty of a network anomaly of a regional or global scale. And the day before yesterday, 25.11.2018, it happened again - this time in Russia.
At 13.00 UTC (16:00 Moscow time) a small Russian operator Krek Ltd ( AS57494) started announcing prefixes between their providers, as a result of redirecting a significant part of Rostelecom’s traffic to its network. The anomaly affected more than 40 thousand prefixes - of course, the Krek network could not withstand such a load. As a result, from 10 to 20% of users in the territory of the Russian Federation lost access to thousands of services, including such popular ones as Amazon, Youtube, Vkontakte and the online cinema IVI.RU.
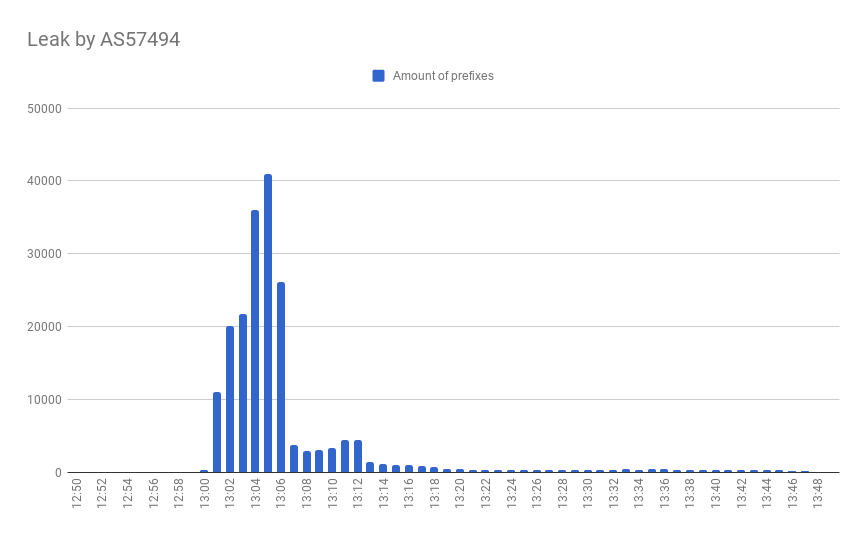
With more than 5,000 prefixes, the incident has spread beyond the borders of the Russian Internet segment, dragging traffic from other regions into this black hole.
This route leak is the result of two interconnected errors - an error in setting up BGP in the Krek network and the absence of filtering at the junctions in the Rostelecom network. Both operators paid a high price for their own mistakes, but this is unlikely to fully satisfy the owners of other services who have lost a significant portion of users.
It is widely believed that the operator has no way to return traffic from such an anomaly - someone else’s router is out of your control. Of course, you can start writing letters to the “guilty” parties - this may speed up the recovery process, but it still will not return traffic to your network instantly.
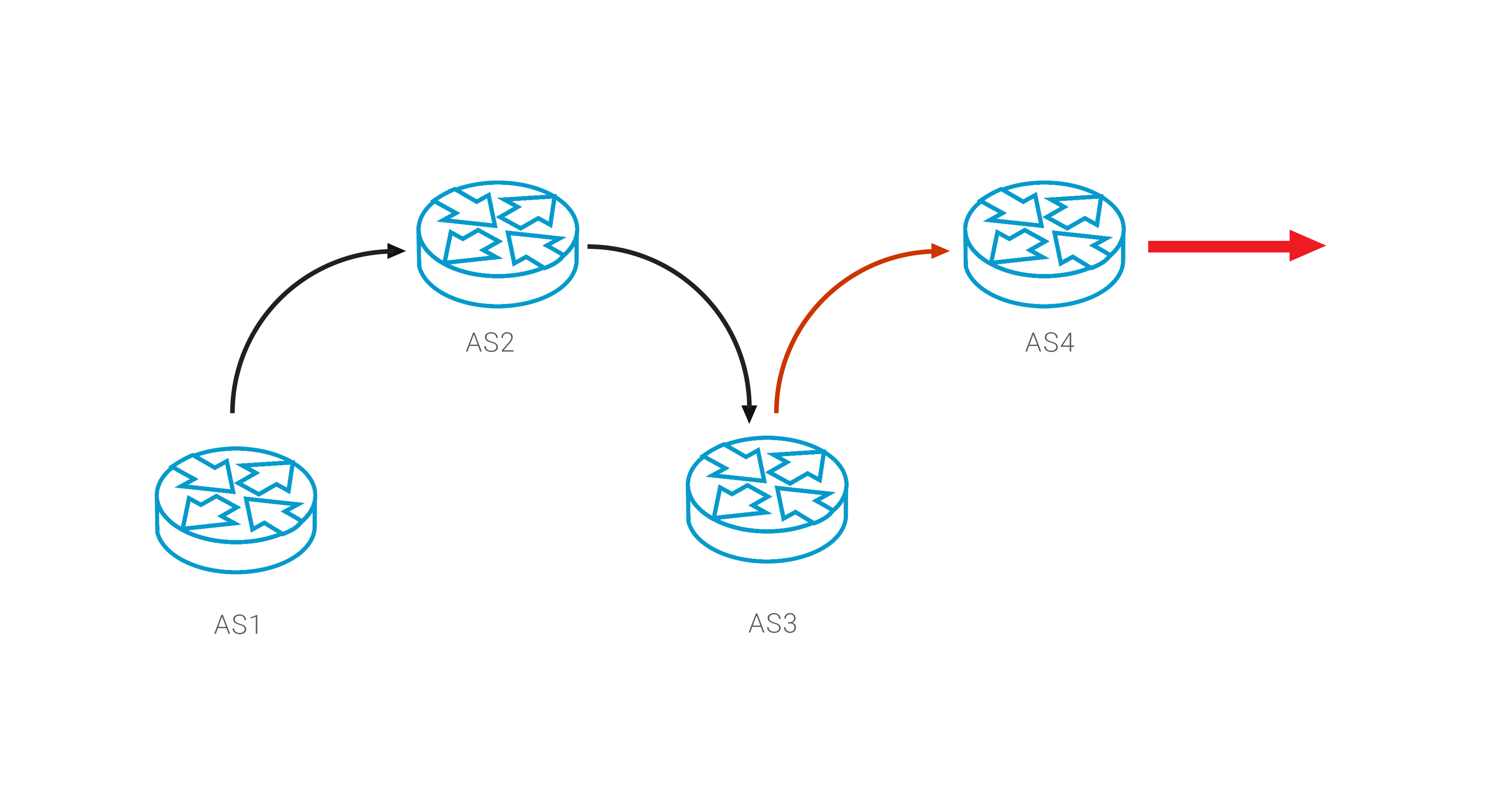
But there is another way to return the correct connectivity by exploiting the BGP loop detection mechanism: the network must automatically reset the route if AS Path includes its own AS number. Therefore, if you know who the source of the anomaly is, you can add it to the beginning of your path, thus forcing it to reset this route.
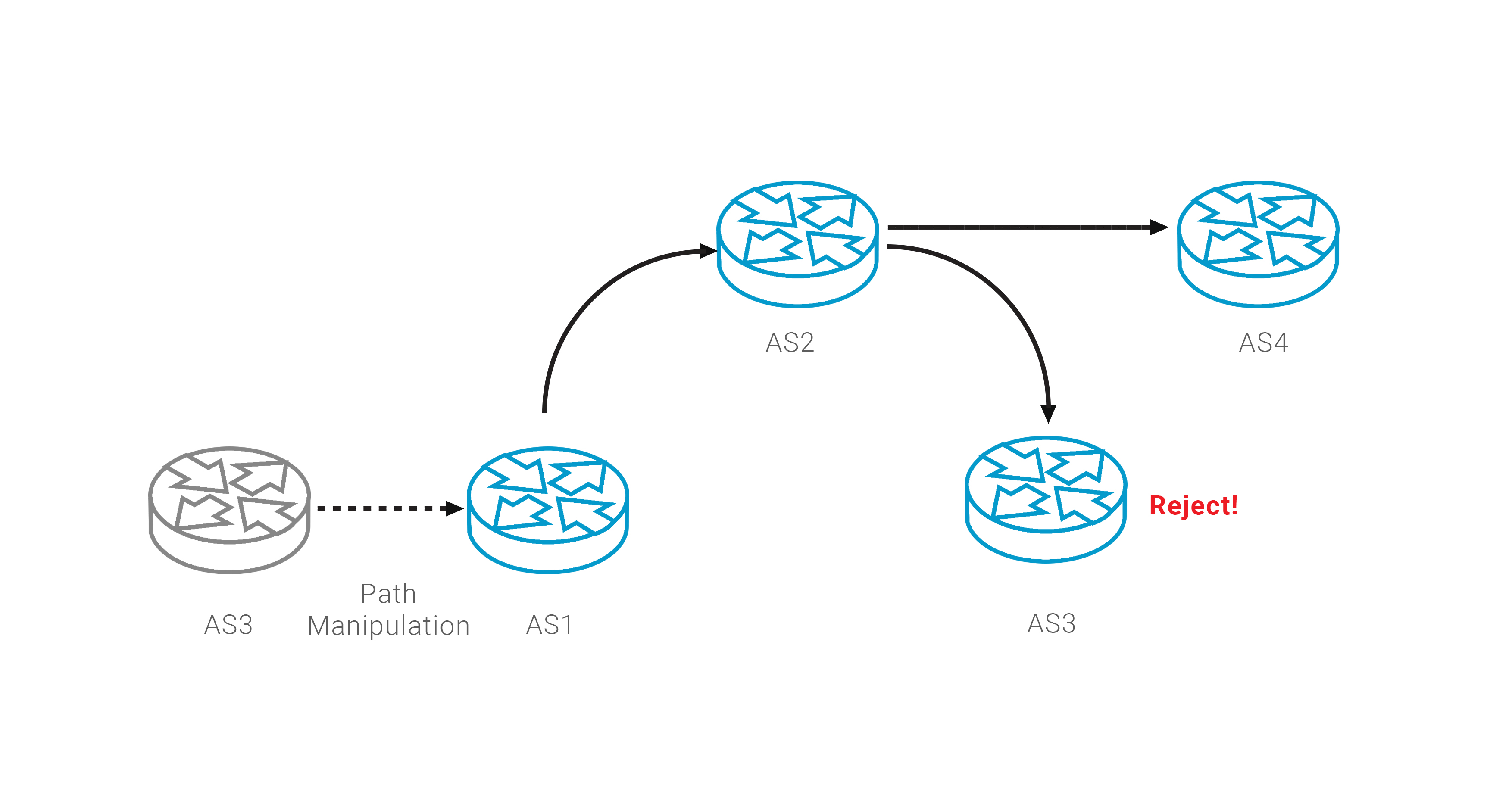
Such a manipulation of AS Path can complement the monitoring of network announcements, providing a guaranteed method to actively deal with incidents such as route leak. But when using such a policy, you should be careful, always checking the validity of the result regarding the ROA validation procedure.
At 13.00 UTC (16:00 Moscow time) a small Russian operator Krek Ltd ( AS57494) started announcing prefixes between their providers, as a result of redirecting a significant part of Rostelecom’s traffic to its network. The anomaly affected more than 40 thousand prefixes - of course, the Krek network could not withstand such a load. As a result, from 10 to 20% of users in the territory of the Russian Federation lost access to thousands of services, including such popular ones as Amazon, Youtube, Vkontakte and the online cinema IVI.RU.

With more than 5,000 prefixes, the incident has spread beyond the borders of the Russian Internet segment, dragging traffic from other regions into this black hole.
This route leak is the result of two interconnected errors - an error in setting up BGP in the Krek network and the absence of filtering at the junctions in the Rostelecom network. Both operators paid a high price for their own mistakes, but this is unlikely to fully satisfy the owners of other services who have lost a significant portion of users.
Return traffic at any cost
It is widely believed that the operator has no way to return traffic from such an anomaly - someone else’s router is out of your control. Of course, you can start writing letters to the “guilty” parties - this may speed up the recovery process, but it still will not return traffic to your network instantly.

But there is another way to return the correct connectivity by exploiting the BGP loop detection mechanism: the network must automatically reset the route if AS Path includes its own AS number. Therefore, if you know who the source of the anomaly is, you can add it to the beginning of your path, thus forcing it to reset this route.

Such a manipulation of AS Path can complement the monitoring of network announcements, providing a guaranteed method to actively deal with incidents such as route leak. But when using such a policy, you should be careful, always checking the validity of the result regarding the ROA validation procedure.
