Conference DEFCON 16. How can I get hold of you? Let me list the ways. Part 1
- Transfer
I am always amazed at the number of people present here, especially considering who I am compared to Phil Zimmerman, so thank you for bothering my ego. I am a Renderer, and if at least three of you do not know me, I will say that I have spoken here at DefCon for 10 years. I love this place, these guys, this is our family, and this is the only place where I feel fine.
My presentation today is called “How can I get you? Let me list the ways. ” This topic was born at the SECTOR conference in Toronto. You know that your workspace is becoming more mobile and wireless. You see it everywhere - in airports, in hotels, here in Vegas. People are constantly typing something on the screens of smartphones, talking and this is the usual picture for our time, every company has something like this.
Mobile users are away from the vigilant eye of BOFH, the computer network operator (and from punishment), so if they do something stupid that violates your security, you can't get to them. They may be on the other side of the earth, but they can harm your networks, so you need to pay attention to this issue in order to protect your company and yourself.
Most of us were forced to come here from afar, I do not think there are many locals among us, so you often find yourself in such a situation. This is not an exhaustive list anyway, but I will try to fully cover the topic. There is nothing new in terms of wireless information, or zero-day problems, or something like that, but I will try to convey to you thoughts that will make you think about how to organize your mobile workspace.
So this is Bob. Bob is engaged in the international sale of widgets. Bob travels around the world. Bob is your worst IT nightmare.

He considers himself a technically savvy, advanced user, he knows enough to get access to porn sites. He is so advanced that if you delete all the icons from his desktop, he will be sure that you have deleted all his programs. I am sure that all of you have come across such people.
Bob is the worst enemy of international widgets and at the same time Bob is the worst scenario development scenario, because by its ability to cause damage to security because of its stupidity, it is much more dangerous than any criminal.
So let's "fuck" Bob. We don’t want to touch him, but simply take up his wireless connections, which he uses to travel around the world, and thus seize power over him.
Bored hackers spend a lot of time at international airports, flying from one hacker conference, for example, in Norway, to the Sector conference in Toronto. They always see people like Bob at airports, and out of boredom they get accustomed to all these laptops and Bluetooth devices that look so tempting. That is why we will start with Wi-Fi.
Bob has a laptop with tons of confidential information from his company, which he connects to the network via access points at the airport, at the railway station, at the hotel, at the Starbucks snack bar. You know these guys who constantly connect to the Internet on business trips to learn CNN news, stock quotes or check their email. Our Bob connects to everything that only finds on the global Internet.
You know that connection points in public places do not encrypt plaintext. This text is easy to read and, in most cases, it is also easy to incorporate malicious content into the text, such as images, scripts, DNS queries, etc.
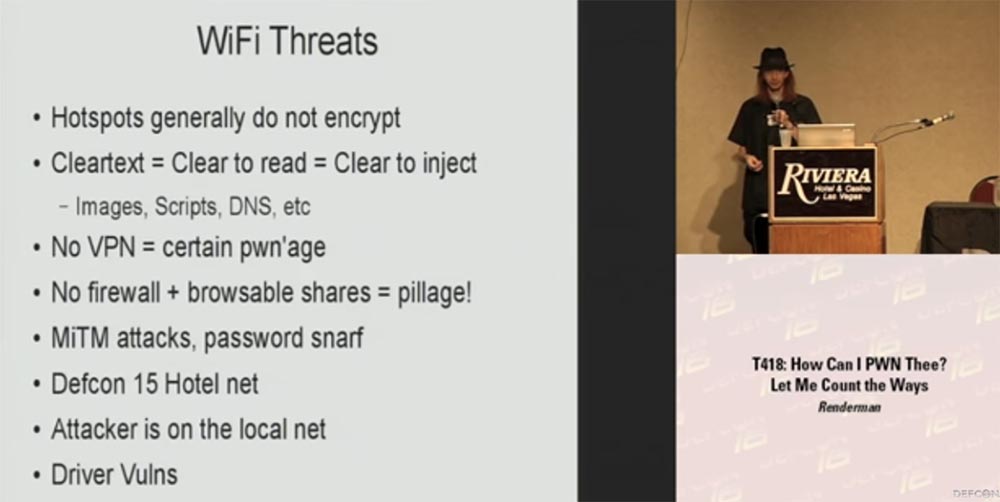
If you are not using a VPN or some kind of encryption layer between your device and the access point, you are caught. You may suffer from the leakage of any information sent, including sent emails, you may enter malicious information into your data. No firewall and sent information can be viewed - assume that you have already been robbed! Tell me, who of you have access points at home? Great, and at the same time you know that you are connecting to your local network, and you are connecting to any computer within your LAN network. But if you connect to an access point in a hotel, there are no networks here, and if you do not have a firewall, you absorb all the crap from other people's computers connected to the same network. If you do not use encryption,
Last year, this hotel had about 20 access points, but as soon as DefCon began, their number increased to 150. This is a gambling city, and I don’t know what it was done for - to reduce the chance of connecting to a fake access point and protect yourself , or you just wanted to reduce the number of barriers to free communication. But you do not even need to connect to the Internet, in which, God knows how many filters, to become vulnerable - I could, sitting nearby, just send a "magic" package using your smartphone or tablet software, which would give me root access to your device.
I was in Norway at a security conference in February, by the way, it was the most terrible flight, which took 48 hours. Let's see what kind of safety knowledge we have, and what people use over the years, believing with all our hearts that this should be so. This was my first trip beyond the North American continent. In Norway, I conducted an experiment on the use of the Airpwn utility, which serves to transmit and intercept packets in wireless networks. In my case, I used this great little Airpwn tool to inject “alternative” images to check how observant people are on other continents.
Let's say you go to the Google homepage and get an HTTP request for the main image, and when the remote server receives a response, it returns this image to you. If I’m in the room, I can respond as an access point before the Google request returns, so that the client will receive my images much faster and the rest of the packages from this server will simply be discarded. That way, I can replace the Google logo with my own image.
It was first shown on the 10th or 11th DefCon, where people replaced images on the fly with a Goatse picture, on the conference website there are some good pictures and videos about it.
At this conference there are several hundred people who use 3 types of wireless networks: open, encrypted WPN and WPA. In Norway, I started with an open network. The next slide shows the first image, nothing special - this is a ten-foot kayak and a 12-foot shark, I don’t know how observant you are to read the analogy of today's topic in it.

So, I throw in this image and watch the reaction of people. They open up some new site on their device, and all the pictures on all screens are the same, as if someone has a shark fetish or something like that. Some confusion arose in the hall, but no one understood what was happening.
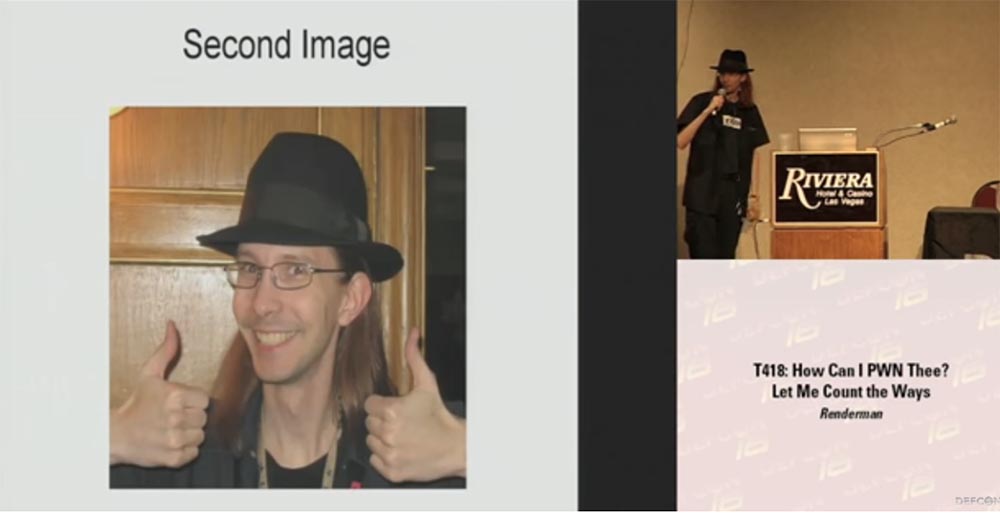
Then I decide to raise the stakes, because when I'm bored, I'm tired and a little drunk, then I become a creative person. Therefore, I inject a second picture with my own photo into their devices, hoping that someone will understand what is happening. And here they finally reach. I still didn’t get it in the face, but several people ran up to me, who had a picture of my physiognomy on the screen instead of the corporate mail logo, and asked what I did with their laptop and what they did to me that I hacked them?
I answered - come to my presentation and I will explain everything to you. It was just very interesting. Imagine that we have a room with traveling salesmen, and you know that they are going to show you their belongings, go to the company's website, and there is such a bummer! In general, I had to thank the staff for the fact that they did not kick me out and didn’t get too angry with me for such a presentation.
The next slide shows the possible threats to Wi-Fi connections. I think that most people encounter them at airports and other public places with free Internet access points.
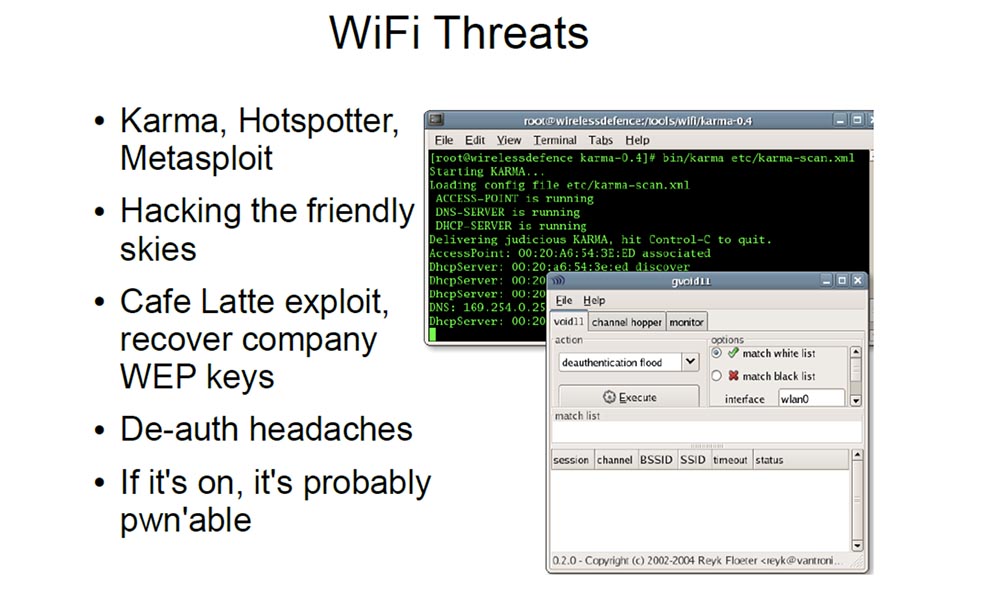
These are things like Karma, Hotspotter or Metasploit that take requests to the access point from client devices and say, “oh, it's me!”, And can turn your laptop into a universal access point that responds to any request to connect to the network independently on what is the SSID. A few years ago, Nomad at the Shmoocon conference gave a very interesting lecture entitled “Breaking the Friendly Skies”. He basically found a way to make his device a beacon, which found the requests of any networks and switched them to himself. He created a special mode of decentralized wireless ad-hoc network. This is an unencrypted network that intercepts packets that serve as some kind of authentication, and in which client devices are connected on the fly, forming their own wireless network.
So on all these flights over long distances, you can be connected to business class guys with all their expensive laptops and see everything they will type and view while in economy class. You can view their corporate information, directories in their computers and find something interesting for themselves.
I don’t know if you’ve seen how Nomad looks like, this is such an ordinary guy in sloppy clothes, and now imagine that he comes up to such a tough businessman and says to him: “Hi, Bob, how are you? How is Julian, an accountant, did you receive this note, which says about a new project? ”And this businessman looks at him crazed and thinks:“ Who the hell are you, and how do you know all this? ”
The Café Latte exploit that was created last year can connect to your company network. If you are just sitting in a cafe, I can send the packet to your laptop, restore the WEP encryption key, and easily connect to your company's network, even if you are not connected to it.
So if I know that these “international widgets” that Bob is trading in are in my hometown, then I can attack them and make their lives miserable. If I know that this businessman is going to have breakfast in this cafe, I can attack him, because he certainly does not have any systems capable of detecting an invasion of his laptop. Therefore, I can safely extract the keys from there and go on to attack his company. I know that the network can be hacked in 60 seconds.
Therefore, to protect against attacks via Wi-Fi, you need to follow these rules:
TOR at one stroke can solve many problems. If you sit at the airport and use the TOR browser, it encrypts the connection between you and the access point. It protects your connection from viewing data and malicious injections.
Roger was with me at that conference in Norway, when I conducted my experiment with pictures, he heard that something was happening, but did not see it until he turned off his “Thor”.
Now let's talk about Bob's phone. Bob lives in his cell phone. I’m sure you’ve probably seen in your office those guys who don’t break away from their phones.
Bob loves his Bluetooth headset. I have such a headset, I use it in the car, it is convenient. But I hate these fanciful people who have something constantly flashing blue in their ears. Tell me how you can manage to answer a phone call in two seconds?
Bob uses the phone for the SMS One Time Pad with a one-time key encryption message. I am not familiar with this in North America, but I know that in South Africa, when you perform a banking transaction, you receive an SMS on the phone - a message with a one-time key to confirm it. This is a very sensitive system, and theoretically an attacker, having the number of your bank card, cannot do anything with it without receiving such an SMS message.
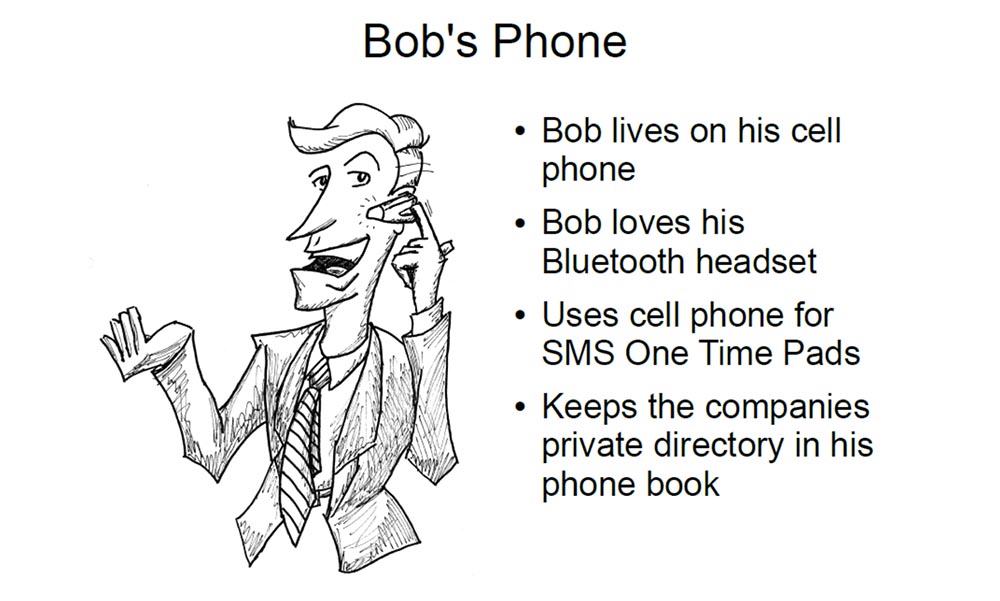
Bob keeps private contacts of the company in his phone book. Anyone using Bluetooth can, if not connect to these numbers, then at least view them and initiate a connection attempt. Most mobile devices have a PIN code, but tell me, who among you changed the PIN code on your Bluetooth phone? Well, why did you raise your hands now? (laughter in the hall).
So, there are the following threats to the Bluetooth connection.
If Bob's phone has a default PIN code, anyone can connect to it. If you have paired with another device via Bluetooth, then you get access to the entire device, and not just, say, contact cards. You can read and write SMS, browse the phone book, notes, images.
The scandal with the mayor of Detroit erupted after hackers infiltrated his phone in this way. They found there several hundreds of SMS messages sent during working hours - his correspondence with his mistress, and all these messages were published in the newspaper. His lawyer later stated that the hackers had inserted all these messages into his phone! However, this could easily be refuted due to time stamps and dates on the messages, because not a single hacker would have faked every message so carefully to make it believable.
You can remotely use AT commands to transfer files, some models have this property. You can connect to them using the RF17 communication channel and execute 80 commands, similar to the commands of old-fashioned modems.
I do not know how in North America, but in Europe there is the possibility of calls to paid numbers, such as our 900 numbers, and you can connect to someone else’s phone and make him dial that number. So if I get Bob to dial such a number, and then he comes at the expense, he will simply have to pay him, but imagine what he would have to explain to the company why he used a corporate phone during a 9-hour conversation with some kind of madam
Now I will show you a video that shows the dangers you face when using a Bluetooth headset.
Voiceover: “Experts have discovered a security flaw present in some of the most popular Bluetooth headsets, which allows unauthorized people to hack into your phone and take control of it. Our volunteers are going to demonstrate on hidden cameras how vulnerable your phone can be to these silent attacks. This is bluetooth fraud. An attacker can connect to your phone and read its contents, such as SMS messages, phone book contacts, and even make calls from it.
How does hacking work via Bluetooth? Our volunteers will demonstrate this - simply turn on Bluetooth on two phones - Jesse and Paul. Now, using his PDA, Alex finds the Bluetooth signal, taking advantage of the fact that Jesse’s phone is not secure enough, and forces him to make a call to Paul’s phone. This is what is called "blue-jacking".
The Bluetooth function in your phone is a very useful modern technology, but it allows an attacker to connect to your phone so that you don’t even know about it, and your phone doesn’t show that you are connected to something.
Now we see that Alex has set up his PDA to search for Bluetooth signals. He detects such a signal and makes a call using Mark's phone, which is in his pocket. Mark does not even know that Alex makes a call to the paid number 0909xxxxxxxxx worth one and a half pounds per minute. This premium line was created by the crooks themselves. Alex steals money straight from your pocket, completely unnoticed, and Mark will lose 75 pounds during his journey from Manchester to Liverpool.
If Alex spends some more time here, it will work fine. In an hour, he manages to “catch” 20 phones, each of which makes a call to a paid line with an average duration of 15. The result is grandiose - our dodgers stole 500 pounds and proved that the latest technology can be used to steal money.
The easiest and best way to protect yourself from this scam is to simply turn off Bluetooth on your phone if you are not using it for specific operations. If you do not turn off Bluetooth when you don’t need it, then you endanger yourself that someone will penetrate your phone and use it for their own purposes.
It’s a pity that you guys can’t see it from here, but every time I show this video or talk about it, several people in the hall take their phone out of their pockets and start messing with it, apparently turning off Bluetooth.
So, consider the threat of Bluetooth. Bob’s headset uses the default pincode. Headsets do not have a keyboard, so you will not be able to change the pin code, which usually looks very simple, like 0 0 0 0 or 1 2 3 4. There are indices of various manufacturers from which you can find out the default pin code. You can intervene in the connection between the headset and the phone and listen to other people's conversations or enter audio recordings into someone else's conversation, for example, drown it with the noise of a car.
You know that during meetings, it is usually asked to turn off phone calls by placing the phone on vibration. But your Bluetooth headset continues to work, blinking its blue light, because even if you turned off your phone altogether, it goes into signal search mode. So I can connect to a working headset in the conference room and listen through it all that they are talking about.
I really like the idea of injecting audio, because it allows people to do all kinds of nasty things and just fool them. This may make a person think that he is crazy.
This slide shows a scene from the movie “The Real Genius”, where they put audio through the brackets into his head, making him think that God is talking to him. Therefore, I hate headsets.
24:00
Conference DEFCON 16. How can I get hold of you? Let me list the ways. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

My presentation today is called “How can I get you? Let me list the ways. ” This topic was born at the SECTOR conference in Toronto. You know that your workspace is becoming more mobile and wireless. You see it everywhere - in airports, in hotels, here in Vegas. People are constantly typing something on the screens of smartphones, talking and this is the usual picture for our time, every company has something like this.
Mobile users are away from the vigilant eye of BOFH, the computer network operator (and from punishment), so if they do something stupid that violates your security, you can't get to them. They may be on the other side of the earth, but they can harm your networks, so you need to pay attention to this issue in order to protect your company and yourself.
Most of us were forced to come here from afar, I do not think there are many locals among us, so you often find yourself in such a situation. This is not an exhaustive list anyway, but I will try to fully cover the topic. There is nothing new in terms of wireless information, or zero-day problems, or something like that, but I will try to convey to you thoughts that will make you think about how to organize your mobile workspace.
So this is Bob. Bob is engaged in the international sale of widgets. Bob travels around the world. Bob is your worst IT nightmare.

He considers himself a technically savvy, advanced user, he knows enough to get access to porn sites. He is so advanced that if you delete all the icons from his desktop, he will be sure that you have deleted all his programs. I am sure that all of you have come across such people.
Bob is the worst enemy of international widgets and at the same time Bob is the worst scenario development scenario, because by its ability to cause damage to security because of its stupidity, it is much more dangerous than any criminal.
So let's "fuck" Bob. We don’t want to touch him, but simply take up his wireless connections, which he uses to travel around the world, and thus seize power over him.
Bored hackers spend a lot of time at international airports, flying from one hacker conference, for example, in Norway, to the Sector conference in Toronto. They always see people like Bob at airports, and out of boredom they get accustomed to all these laptops and Bluetooth devices that look so tempting. That is why we will start with Wi-Fi.
Bob has a laptop with tons of confidential information from his company, which he connects to the network via access points at the airport, at the railway station, at the hotel, at the Starbucks snack bar. You know these guys who constantly connect to the Internet on business trips to learn CNN news, stock quotes or check their email. Our Bob connects to everything that only finds on the global Internet.
You know that connection points in public places do not encrypt plaintext. This text is easy to read and, in most cases, it is also easy to incorporate malicious content into the text, such as images, scripts, DNS queries, etc.

If you are not using a VPN or some kind of encryption layer between your device and the access point, you are caught. You may suffer from the leakage of any information sent, including sent emails, you may enter malicious information into your data. No firewall and sent information can be viewed - assume that you have already been robbed! Tell me, who of you have access points at home? Great, and at the same time you know that you are connecting to your local network, and you are connecting to any computer within your LAN network. But if you connect to an access point in a hotel, there are no networks here, and if you do not have a firewall, you absorb all the crap from other people's computers connected to the same network. If you do not use encryption,
Last year, this hotel had about 20 access points, but as soon as DefCon began, their number increased to 150. This is a gambling city, and I don’t know what it was done for - to reduce the chance of connecting to a fake access point and protect yourself , or you just wanted to reduce the number of barriers to free communication. But you do not even need to connect to the Internet, in which, God knows how many filters, to become vulnerable - I could, sitting nearby, just send a "magic" package using your smartphone or tablet software, which would give me root access to your device.
I was in Norway at a security conference in February, by the way, it was the most terrible flight, which took 48 hours. Let's see what kind of safety knowledge we have, and what people use over the years, believing with all our hearts that this should be so. This was my first trip beyond the North American continent. In Norway, I conducted an experiment on the use of the Airpwn utility, which serves to transmit and intercept packets in wireless networks. In my case, I used this great little Airpwn tool to inject “alternative” images to check how observant people are on other continents.
Let's say you go to the Google homepage and get an HTTP request for the main image, and when the remote server receives a response, it returns this image to you. If I’m in the room, I can respond as an access point before the Google request returns, so that the client will receive my images much faster and the rest of the packages from this server will simply be discarded. That way, I can replace the Google logo with my own image.
It was first shown on the 10th or 11th DefCon, where people replaced images on the fly with a Goatse picture, on the conference website there are some good pictures and videos about it.
At this conference there are several hundred people who use 3 types of wireless networks: open, encrypted WPN and WPA. In Norway, I started with an open network. The next slide shows the first image, nothing special - this is a ten-foot kayak and a 12-foot shark, I don’t know how observant you are to read the analogy of today's topic in it.

So, I throw in this image and watch the reaction of people. They open up some new site on their device, and all the pictures on all screens are the same, as if someone has a shark fetish or something like that. Some confusion arose in the hall, but no one understood what was happening.
Then I decide to raise the stakes, because when I'm bored, I'm tired and a little drunk, then I become a creative person. Therefore, I inject a second picture with my own photo into their devices, hoping that someone will understand what is happening. And here they finally reach. I still didn’t get it in the face, but several people ran up to me, who had a picture of my physiognomy on the screen instead of the corporate mail logo, and asked what I did with their laptop and what they did to me that I hacked them?

I answered - come to my presentation and I will explain everything to you. It was just very interesting. Imagine that we have a room with traveling salesmen, and you know that they are going to show you their belongings, go to the company's website, and there is such a bummer! In general, I had to thank the staff for the fact that they did not kick me out and didn’t get too angry with me for such a presentation.
The next slide shows the possible threats to Wi-Fi connections. I think that most people encounter them at airports and other public places with free Internet access points.

These are things like Karma, Hotspotter or Metasploit that take requests to the access point from client devices and say, “oh, it's me!”, And can turn your laptop into a universal access point that responds to any request to connect to the network independently on what is the SSID. A few years ago, Nomad at the Shmoocon conference gave a very interesting lecture entitled “Breaking the Friendly Skies”. He basically found a way to make his device a beacon, which found the requests of any networks and switched them to himself. He created a special mode of decentralized wireless ad-hoc network. This is an unencrypted network that intercepts packets that serve as some kind of authentication, and in which client devices are connected on the fly, forming their own wireless network.
So on all these flights over long distances, you can be connected to business class guys with all their expensive laptops and see everything they will type and view while in economy class. You can view their corporate information, directories in their computers and find something interesting for themselves.
I don’t know if you’ve seen how Nomad looks like, this is such an ordinary guy in sloppy clothes, and now imagine that he comes up to such a tough businessman and says to him: “Hi, Bob, how are you? How is Julian, an accountant, did you receive this note, which says about a new project? ”And this businessman looks at him crazed and thinks:“ Who the hell are you, and how do you know all this? ”
The Café Latte exploit that was created last year can connect to your company network. If you are just sitting in a cafe, I can send the packet to your laptop, restore the WEP encryption key, and easily connect to your company's network, even if you are not connected to it.
So if I know that these “international widgets” that Bob is trading in are in my hometown, then I can attack them and make their lives miserable. If I know that this businessman is going to have breakfast in this cafe, I can attack him, because he certainly does not have any systems capable of detecting an invasion of his laptop. Therefore, I can safely extract the keys from there and go on to attack his company. I know that the network can be hacked in 60 seconds.
Therefore, to protect against attacks via Wi-Fi, you need to follow these rules:
- turn off Wi-Fi when you are not using the network;
- When connecting to the network, use VPN for all connections, for this there are many good free products;
- always assume that you have already been attacked. Do not think that there is a solid happy wireless world around you. Remember that there may be some bored hacker near you in the airport lounge;
- do not trust your customer networks because there are people like Bob there. He enters the Internet without any protection, checks his mail, stock quotes and so on. You’ve all heard of people who go online and pounce on everything they see: “oh, look, this is a new host! Oh look, polka! Oh, this is a guy who sells something! Look, open distribution! ”;
- turn on the firewall;
- be careful;
TOR at one stroke can solve many problems. If you sit at the airport and use the TOR browser, it encrypts the connection between you and the access point. It protects your connection from viewing data and malicious injections.
Roger was with me at that conference in Norway, when I conducted my experiment with pictures, he heard that something was happening, but did not see it until he turned off his “Thor”.
Now let's talk about Bob's phone. Bob lives in his cell phone. I’m sure you’ve probably seen in your office those guys who don’t break away from their phones.
Bob loves his Bluetooth headset. I have such a headset, I use it in the car, it is convenient. But I hate these fanciful people who have something constantly flashing blue in their ears. Tell me how you can manage to answer a phone call in two seconds?
Bob uses the phone for the SMS One Time Pad with a one-time key encryption message. I am not familiar with this in North America, but I know that in South Africa, when you perform a banking transaction, you receive an SMS on the phone - a message with a one-time key to confirm it. This is a very sensitive system, and theoretically an attacker, having the number of your bank card, cannot do anything with it without receiving such an SMS message.

Bob keeps private contacts of the company in his phone book. Anyone using Bluetooth can, if not connect to these numbers, then at least view them and initiate a connection attempt. Most mobile devices have a PIN code, but tell me, who among you changed the PIN code on your Bluetooth phone? Well, why did you raise your hands now? (laughter in the hall).
So, there are the following threats to the Bluetooth connection.
If Bob's phone has a default PIN code, anyone can connect to it. If you have paired with another device via Bluetooth, then you get access to the entire device, and not just, say, contact cards. You can read and write SMS, browse the phone book, notes, images.
The scandal with the mayor of Detroit erupted after hackers infiltrated his phone in this way. They found there several hundreds of SMS messages sent during working hours - his correspondence with his mistress, and all these messages were published in the newspaper. His lawyer later stated that the hackers had inserted all these messages into his phone! However, this could easily be refuted due to time stamps and dates on the messages, because not a single hacker would have faked every message so carefully to make it believable.
You can remotely use AT commands to transfer files, some models have this property. You can connect to them using the RF17 communication channel and execute 80 commands, similar to the commands of old-fashioned modems.
I do not know how in North America, but in Europe there is the possibility of calls to paid numbers, such as our 900 numbers, and you can connect to someone else’s phone and make him dial that number. So if I get Bob to dial such a number, and then he comes at the expense, he will simply have to pay him, but imagine what he would have to explain to the company why he used a corporate phone during a 9-hour conversation with some kind of madam
Now I will show you a video that shows the dangers you face when using a Bluetooth headset.
Voiceover: “Experts have discovered a security flaw present in some of the most popular Bluetooth headsets, which allows unauthorized people to hack into your phone and take control of it. Our volunteers are going to demonstrate on hidden cameras how vulnerable your phone can be to these silent attacks. This is bluetooth fraud. An attacker can connect to your phone and read its contents, such as SMS messages, phone book contacts, and even make calls from it.
How does hacking work via Bluetooth? Our volunteers will demonstrate this - simply turn on Bluetooth on two phones - Jesse and Paul. Now, using his PDA, Alex finds the Bluetooth signal, taking advantage of the fact that Jesse’s phone is not secure enough, and forces him to make a call to Paul’s phone. This is what is called "blue-jacking".
The Bluetooth function in your phone is a very useful modern technology, but it allows an attacker to connect to your phone so that you don’t even know about it, and your phone doesn’t show that you are connected to something.

Now we see that Alex has set up his PDA to search for Bluetooth signals. He detects such a signal and makes a call using Mark's phone, which is in his pocket. Mark does not even know that Alex makes a call to the paid number 0909xxxxxxxxx worth one and a half pounds per minute. This premium line was created by the crooks themselves. Alex steals money straight from your pocket, completely unnoticed, and Mark will lose 75 pounds during his journey from Manchester to Liverpool.
If Alex spends some more time here, it will work fine. In an hour, he manages to “catch” 20 phones, each of which makes a call to a paid line with an average duration of 15. The result is grandiose - our dodgers stole 500 pounds and proved that the latest technology can be used to steal money.
The easiest and best way to protect yourself from this scam is to simply turn off Bluetooth on your phone if you are not using it for specific operations. If you do not turn off Bluetooth when you don’t need it, then you endanger yourself that someone will penetrate your phone and use it for their own purposes.
It’s a pity that you guys can’t see it from here, but every time I show this video or talk about it, several people in the hall take their phone out of their pockets and start messing with it, apparently turning off Bluetooth.
So, consider the threat of Bluetooth. Bob’s headset uses the default pincode. Headsets do not have a keyboard, so you will not be able to change the pin code, which usually looks very simple, like 0 0 0 0 or 1 2 3 4. There are indices of various manufacturers from which you can find out the default pin code. You can intervene in the connection between the headset and the phone and listen to other people's conversations or enter audio recordings into someone else's conversation, for example, drown it with the noise of a car.
You know that during meetings, it is usually asked to turn off phone calls by placing the phone on vibration. But your Bluetooth headset continues to work, blinking its blue light, because even if you turned off your phone altogether, it goes into signal search mode. So I can connect to a working headset in the conference room and listen through it all that they are talking about.
I really like the idea of injecting audio, because it allows people to do all kinds of nasty things and just fool them. This may make a person think that he is crazy.

This slide shows a scene from the movie “The Real Genius”, where they put audio through the brackets into his head, making him think that God is talking to him. Therefore, I hate headsets.
24:00
Conference DEFCON 16. How can I get hold of you? Let me list the ways. Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until December for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
