Veramine - New Security Product from Former MSRC Specialists
A team of renowned security professionals who previously worked at the Microsoft Security Response Center and are involved in the development of EMET have unveiled information about their new Windows product called Veramine . It is a cloud-based security solution and specializes in investigating system anomalies in order to detect various types of attacks and malicious actions, including pass-the-hash attacks, exploiting LPE exploits, introducing malicious code into processes, etc. .

Veramine specializes in studying the behavior of the target system using a client that sends information about events in the system to the server, after which the server part builds the logic of the system and tries to detect anomalies there based on the rules used. The user can see the actions and possible anomalies in the system through the web interface when connecting to his account on the server.
The paid version of Veramine differs from the free presence of more rules and methods for detecting malicious activity.
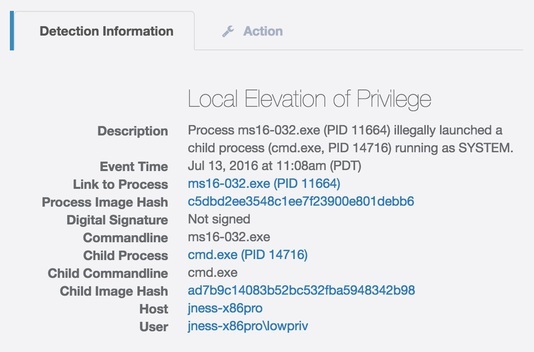
Fig. Detection of LPE exploit by behavior.
The Veramine client part collects comprehensive information about the actions and operations that occur in the system, and then sends them to a remote server, where they are analyzed. From the information received, the system generates a warning for the user, and also helps him to get information about the following actions.
Veramine is positioned as a product that does not consume a lot of system resources and CPU time.
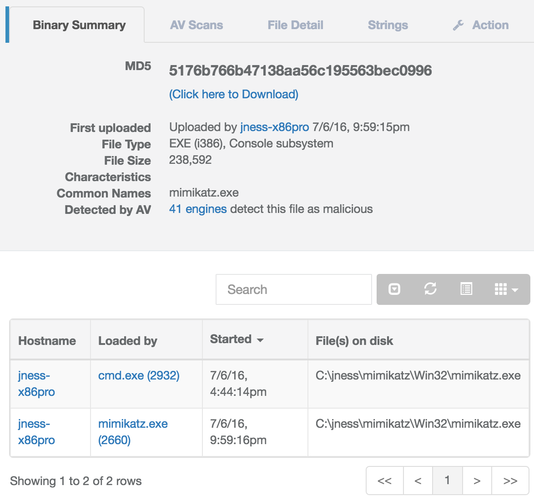
Fig. A message from Veramine about a well-known tool for pass-the-hash attacks of mimikatz.
The tool collects information about the following events in the system:
The Veramine client part consists of a driver that specializes in collecting system events, and a user-mode application that receives information collected by the driver and transfers it to the server. The client part works with the server through one outgoing TCP / IP connection to port number 443. All information is transmitted to the server as a continuous stream over a secure TLS channel.
Veramine specializes in detecting the following types of attacks.
The tool does not require any signature updates for its operation.
FAQ: veramine.com/faq.html
To get a free version of the product, go to the website: veramine.com

Veramine specializes in studying the behavior of the target system using a client that sends information about events in the system to the server, after which the server part builds the logic of the system and tries to detect anomalies there based on the rules used. The user can see the actions and possible anomalies in the system through the web interface when connecting to his account on the server.
The paid version of Veramine differs from the free presence of more rules and methods for detecting malicious activity.

Fig. Detection of LPE exploit by behavior.
The Veramine client part collects comprehensive information about the actions and operations that occur in the system, and then sends them to a remote server, where they are analyzed. From the information received, the system generates a warning for the user, and also helps him to get information about the following actions.
- The system starts the process, the command line of which coincides with a specific line.
- The process running in the system establishes outgoing network connections to a specific domain or IP address.
- A process running on the system loads an executable file with a specific MD5 hash into memory.
- The system starts executable processes without the built-in DEP & ASLR support.
- The system runs a file without a digital signature, but with elevated privileges.
- The system operates a process that sends more than 10MB of network traffic.
- The system runs a process that writes data to specific locations in the system registry.
- For a certain period of time, the system starts processes from the account of a compromised user.
- The powershell process has started executing files without a digital signature in the last 24 hours.
Veramine is positioned as a product that does not consume a lot of system resources and CPU time.
Continuous monitoring without compromising overall system performance. The Veramine sensor is aggressively optimized to minimize system overhead. After an initial enumeration period, the sensor consumes <1% CPU.

Fig. A message from Veramine about a well-known tool for pass-the-hash attacks of mimikatz.
The tool collects information about the following events in the system:
- process activity;
- network connection activity;
- operations with logins;
- operations with the system registry;
- operations with deleted files;
- SMB protocol operations
- changes in the configuration of services;
- Changes in the status of process privileges
- password dumping operations;
The Veramine client part consists of a driver that specializes in collecting system events, and a user-mode application that receives information collected by the driver and transfers it to the server. The client part works with the server through one outgoing TCP / IP connection to port number 443. All information is transmitted to the server as a continuous stream over a secure TLS channel.
Veramine specializes in detecting the following types of attacks.
- Exploiting LPE vulnerabilities to obtain maximum SYSTEM privileges in the system.
- Dumping passwords and account data, for example, using the mimikatz tool.
- Unusual process operations and remote thread creation, for example, the migrate attack technique known from metasploit.
- User downloads malicious files from the Internet or mail and launches them for execution.
The tool does not require any signature updates for its operation.
... the Veramine detection system requires no signature updates. Detection is performed against a set of known-malicious behavior, not specific attributes of known malicious software files. For this reason, the Veramine sensor happily coexists alongside existing traditional anti-malware products. The anti-malware product may detect known malicious software that does not meet Veramine's detection criteria and the Veramine system will detect malicious behavior exhibited by any software, regardless of whether it is included in the anti-malware product's signature database.
FAQ: veramine.com/faq.html
To get a free version of the product, go to the website: veramine.com
