Destroy SSD in 7 seconds: tactical protection of information from unauthorized access
"Any value is controlled only by the one who is able to destroy it"
- Dune, Frank Herbert
In the second year of university, my classmate got a job as an assistant administrator. A month later, in the canteen, he (I and three other classmates) boasted that he wrote a software that allowed him to download files from the Internet through a corporate account (I remind you that on the dialup in those days one mp3 download took an hour). Another classmate after the brewery said this already in his company of friends, and those without his knowledge decided to take a nap. Databases with phone numbers, addresses, traffic police and others have long walked around, a small town. Call:
- Eugene, good afternoon, this is Sergeant Ivanov, department of the Federal Service for the Investigation of Information Crimes. Do you have an illegal use of your official position when you can come to us to testify?
The guy did not appear at the university for about a week, and he thrashed his hard disk, disks and RAM into crumbs.
Surely everyone who reads these lines wondered how and with what to crumble their hard drive if they come to it (the effect of the elusive Joe). For some, this remained in the form of a mental plan, while for others, their hands reached the armament with technical means (for example, a hard drive, a disk was previously removed from the system, and a favorite Bulgarian was nearby.)
Protection against unauthorized access is not only soft, but also hardcore. There are all kinds of situations, and information has to be protected at the cost of its life. “So don’t you get anyone!” Or “Ultima ratio regum” (the last argument of kings).
Today - a report from the laboratory on the operational destruction of information. (Thanks to the security expert Oleg Pozdnyakov from Detector Systems for the right of access.)

Gilfoyl is a schoolboy, compared to how they protect critical information in Russia.
I already wrote about how to smear the magnetic field of HDD ( Killer hard drives. Coercive head shot ). But SSD has more armor. SSD is tenacious. Here the SSD was fed petabytes , he did not choke, but he himself can be fed the shredder, as they do in Europe and America. Our engineers came up with a more elegant solution. But not at once. First there was
When they
Several photos and videos and test versions of destroyers, as well as standards for protecting information from unauthorized access.
Theory
Guidance document “Protection against unauthorized access to information”. Terms and definitions .
American National Standard DoD 5220.22-M
В его основе лежит один из самых старых алгоритмов гарантированного уничтожения информации. DoD 5220.22-M был принят в 1995 году для использования в армии США. Кстати, именно отсюда и взялась в названии стандарта аббревиатура DoD — Department of Defence (Министерство обороны).
Стандарт DoD 5220.22-M предполагает совершение трех проходов записи поверх удаляемой информации и одного цикла верификации. В первом из них сохраняются случайным образом выбранные символы в каждый байт каждого сектора. Второй проход — запись инвертированных данных. То есть вместо всех нулей записываются единицы и наоборот. Ну и, наконец, третий цикл — это еще одна запись случайной последовательности символов.
Такой подход является неплохой защитой от людей, не обладающих специальными средствами. Тем не менее во многих случаях его применения будет явно недостаточно. Это признает и армия США, штаб которой запрещает использование DoD 5220.22-M для удаления информации с грифом «Совершенно секретно».
pcsupport.about.com/od/termsd/g/dod-5220-22-M.htm
Стандарт DoD 5220.22-M предполагает совершение трех проходов записи поверх удаляемой информации и одного цикла верификации. В первом из них сохраняются случайным образом выбранные символы в каждый байт каждого сектора. Второй проход — запись инвертированных данных. То есть вместо всех нулей записываются единицы и наоборот. Ну и, наконец, третий цикл — это еще одна запись случайной последовательности символов.
Такой подход является неплохой защитой от людей, не обладающих специальными средствами. Тем не менее во многих случаях его применения будет явно недостаточно. Это признает и армия США, штаб которой запрещает использование DoD 5220.22-M для удаления информации с грифом «Совершенно секретно».
pcsupport.about.com/od/termsd/g/dod-5220-22-M.htm
German national standard VSITR
Этот стандарт был разработан в 1999 году организацией Bundesamt fuer Sicherheit in der Information-stechnik, исполняющей в Германии многие обязанности нашего бывшего ФАПСИ. По сравнению с американским DoD 5220.22-M он более надежен. Достигается это за счет осуществления семи циклов записи поверх уничтожаемой информации. Правда, никакой оригинальности в нем нет. Первый цикл — запись всех логических нулей (0x00), второй — единиц (0xFF). Следующие четыре прохода повторяют первые два. А на седьмом, последнем «круге», происходит запись значения 0xAA.
Естественно, такой алгоритм гарантированного уничтожения информации выполняется дольше американского DoD 5220.22-M. И хотя он по надежности лучше, тем не менее не гарантирует абсолютную невозможность восстановления данных.
Естественно, такой алгоритм гарантированного уничтожения информации выполняется дольше американского DoD 5220.22-M. И хотя он по надежности лучше, тем не менее не гарантирует абсолютную невозможность восстановления данных.
Russian national standard GOST R50739-95
Этот стандарт, как это видно из его названия, был разработан в 1995 году. В его основе лежит самый «мягкий» алгоритм, который, хоть и защищает от восстановления данных с помощью обычных программ, но не обеспечивает абсолютно никакой защиты от специальных средств. Стандарт предусматривает два варианта уничтожения данных. Первый из них — для компьютерных систем с 6-го по 4-й класс защиты. Он предусматривает запись логических нулей в каждый байт каждого сектора. Второй вариант используется для компьютерных систем с 3-го по 1-й класс защиты. В этом случае вместо нулей записываются случайно выбранные символы.
ГОСТ P 50739-95 Средства вычислительной техники. Защита от несанкционированного доступа к информации. Общие технические требования
ГОСТ P 50739-95 Средства вычислительной техники. Защита от несанкционированного доступа к информации. Общие технические требования
Hardware data corruption
According to the Pentagon, software does not guarantee absolutely reliable data deletion. Therefore, the provision of NTSC-TG-025 determines that when deleting Secret or Topsecret category information, it is necessary to use powerful devices to demagnetize and heat the hard drive to temperatures above 700 ° C.
NSA
NSA / CSS Storage Device Declassification Manual (NSA / CSS SDDM)
And this is what they do in Europe:

Russia, 2016.
Laboratory for the destruction of information. Test samples of SSD destroyers.Hotter
The first hypothesis is to burn.

The hypothesis was put forward that instead of the oven and microwave, which are “heated” in a few minutes, the termite will cope in a few seconds. They made several test samples, even showed them at the exhibition.

Self-igniting SSD drives. Click, and the termite inside fuses everything into glass. But not everything turned out to be so simple in practice.

"Drops of molten silicon." The burning temperature of the termite is 1300 degrees.

Two cups of termite, please. With myself.

Termite stuffed drive.

Tests by termite.
At the test site:
Digging in what's left:
The termite version was rejected due to the risk of uncontrolled consequences of accidental operation - too much noise, light and sound effects. As well as the risk of damage to neighboring equipment.
Solid flame
There were still ideas to use solid flame , and there were also links to the SHS laboratory ( self-propagating high-temperature synthesis ).
Here is how it looks. Handsomely.
Although if you make the basis of the boards from such a material or case for drives. But so far this has remained at the idea level.
Louder
DISCLAIMER. For explosions, they used the usual New Year's firecrackers, which are sold in any fireworks store.

Tested on a regular flash drive, tightly screwed into caprolon.



Experts found the damage to the chip insufficient . Plus the risk of unauthorized operation, for example, in an airplane.
Sun socket (outdated technology)
Marketers came up with the idea of how you can fool unreliable equipment to simpletons. Here, they say, we’ll connect 220 volts directly, and we’ll burn everything in a second. But no. The wiring burns out, but the chip remains intact. Nevertheless, similar solutions still come across in the market. (Again, “Raskat”?)
In the laboratory we tried a similar solution, tested it and found it absolutely unreliable.

But since electricity is the most affordable, quiet and odorless, we decided to use it, but with a qualitatively different method. Thus, the most optimal solution at the moment was born - Impulse-SSD .
Lightning chain

Here is a demonstration of the operation of the Impulse-SSD exterminator , voltage 20,000 volts.
The device is intended for emergency erasure of information from a solid-state single-board SSD carrier form factor 2.5 ”.

Appearance - a regular five-inch slot, with a hole for a standard SSD drive.
The ultimate task of the device’s operation is to perform irreplaceable and complete erasure of the information recorded on the NAND-flash chip in the minimum time.
The performance of the disk after erasing is irretrievably lost and the disk must be replaced.
When the device is activated (data erasing), a specific electric field is generated in the device’s camera, which leads to the destruction of the structure of NAND-flash memory microcircuits.
Erase time up to 2 seconds.
A side effect is the permissible partial cracking of the housing of the microcircuit.
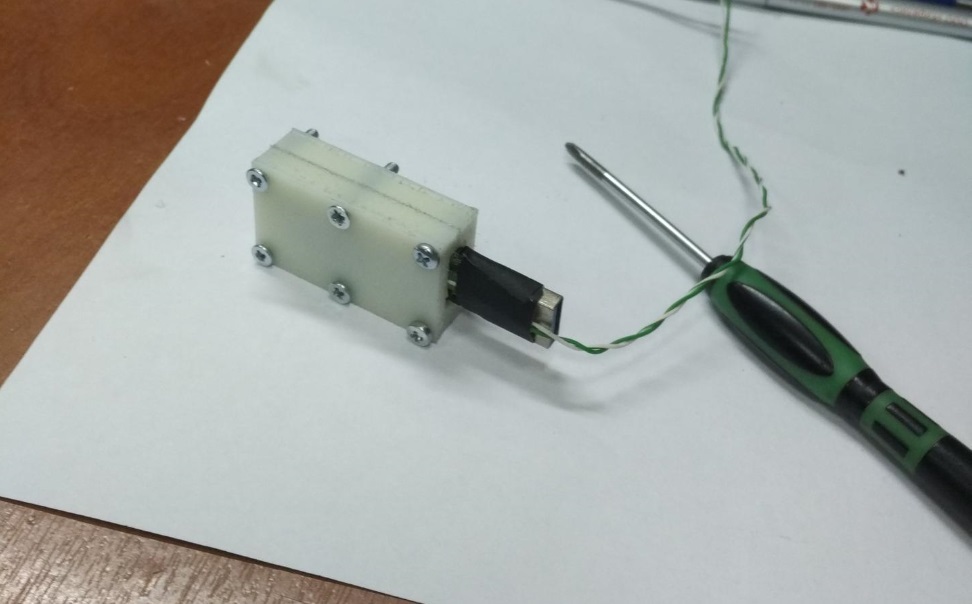
An ordinary SSD must be stripped from the aluminum case so that it does not shield our lightning.
The SSD disk is placed in the device’s camera, connected to the server (disk controller) using an interface cable - extension cable. The disk interface does not matter. At the same time, the speed and functionality of the disks are completely preserved. Before placement in the device, the external case must be removed from the disk, that is, the disk board itself without a protective casing is placed in the device. This operation can be performed by mid-level IT personnel familiar with the instructions.

A knot of "red buttons" to destroy information.
Peripheral devices allow remote (including wireless) control of the device, organization of protection of the perimeter of the computer case, premises.
Local device activation - wired buttons up to 300m.
Remote activation - a radio channel (range 40, 1000m), a GSM controller with the additional possibility of receiving feedback on activation and the status of the device.

Blocks of the radio channel of short and medium range.
Perimeter protection - mechanical, reed switches, security control - proximity keys.
I was not allowed to climb inside the device, only “motors” showed me.

These simple motors provide a sweep over the entire area of the SSD drive.
Protection from the fool and the cleaning lady
When all hard drives can be destroyed with the click of a button, it is worth considering protection "from a fool." Our engineers proposed a solution - a kind of "click pattern" (like a tricky knock at the door: pam-papababampam-pam-pam). But once the "fool" managed to circumvent the defense against himself and he decided to compete with a colleague. Drive destruction activation has occurred. At first they wanted to put the blame on the spontaneous operation of the device, but there are logs. When the logs were raised, there was a clear actuation of the radio start and our hero, bypassing the defense, confessed.
Conclusion
“Our company is increasingly turning to us for solid-state destruction systems. SSD media, apparently becoming cheaper, are more often used in the assembly of workstations and servers. I have been an expert in the information security market for 5 (10 years), during this time I have double-checked several dozens of exterminator options and boldly declare that Ipuls-SSD maximizes the destruction of carriers from all existing options. It does not use wire soldering, pyrotechnics and other, to put it mildly, quack methods of information destruction. ”
- Oleg Pozdnyakov
“Never trust a computer that you cannot throw out the window.”
- Steve Wozniak
When all measures to ensure the protection of the perimeter have failed, the kings ’last argument remains. It is important that it works guaranteed (especially in situations with power outages and jamming the radio) and precisely when they are ordered (and not arbitrarily). It follows from this that it is worth checking the reliability of the destruction system several times in the “training alert” mode and not trusting “marketing assurances”.
PS
Again I want to remind about the "Genius":
PPS
It somehow happened that my classmate forgot to say that they pinned him. He only found out after a year. But this year he lived as a saint, even passed the tests on time.
Only registered users can participate in the survey. Please come in.
