Easter Egg in Mr Robot S02E01
- Transfer
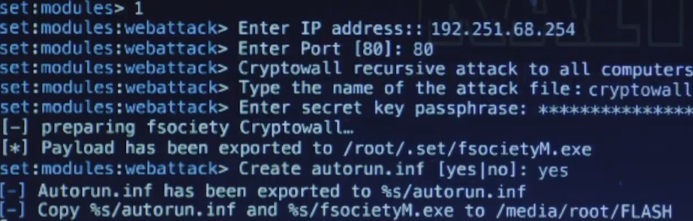
At the end of the first episode of the second season, Mr Robot has a scene where Darlene generates a ransomware trojan using a modified SET (Social Engineer Toolkit) framework. My fingers just itched to try the IP address 192.251.68.254, where it seems like the Trojan’s management server is located. Not surprisingly, WHOIS pointed to the owner of NBC-UNIVERSAL. Let's see how deep the rabbit hole is.
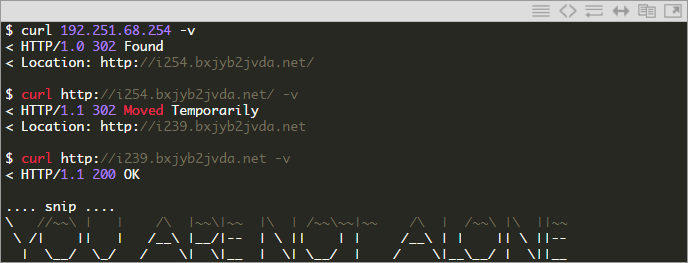
The last page http://i239.bxjyb2jvda.net/ displays the message “YOUR PERSONAL FILES ARE ENCRYPTED” and starts the countdown. You can wait 24 hours or just check the javascript , which controls the countdown timer, where you will find the base64 encoded string. After decoding comes out:
PGRpdiBjbGFzcz0ib3ZlciI+PGRpdj4iSSBzaW5jZXJlbHkg
YmVsaWV2ZSB0aGF0IGJhbmtpbmcgZXN0YWJsaXNobWVudHM
gYXJlIG1vcmUgZGFuZ2Vyb3VzIHRoYW4gc3RhbmRpbmcgYXJta
WVzLCBhbmQgdGhhdCB0aGUgcHJpbmNpcGxlIG9mIHNwZW5k
aW5nIG1vbmV5IHRvIGJlIHBhaWQgYnkgcG9zdGVyaXR5LCB1bm
RlciB0aGUgbmFtZSBvZiBmdW5kaW5nLCBpcyBidXQgc3dpbmRs
aW5nIGZ1dHVyaXR5IG9uIGEgbGFyZ2Ugc2NhbGUuIjwvZGl2Pjx
kaXYgY2xhc3M9ImF1dGhvciI+LSBUaG9tYXMgSmVmZmVyc29u
PC9zcGFuPjwvZGl2PjwvZGl2Pg==I sincerely believe that banking institutions are more dangerous for freedom than regular armies, and that the principle of spending money at the expense of descendants, called "financing", is nothing but a scam at the expense of the future on a large scale.
- Thomas Jefferson
By the way, having studied the SSL certificate of the NBC-UNIVERSAL web server, I found a ton of other domains that are related to Mr Server. Specified in the Subject Alternative Names field. At the beginning of the first episode of the second season, you will also notice how Elliot logs in to bkuw300ps345672-cs30.serverfarm.evil-corp-usa.com via SSH. As for the puzzle on https://fsoc.sh : If you look at this page, you will notice that the cursor blinks at different intervals.
DNS Name=www.racksure.com
DNS Name=racksure.com
DNS Name=*.serverfarm.evil-corp-usa.com
DNS Name=www.e-corp-usa.com
DNS Name=iammrrobot.com
DNS Name=www.conficturaindustries.com
DNS Name=www.iammrrobot.com
DNS Name=*.seeso.com
DNS Name=*.evil-corp-usa.com
DNS Name=e-corp-usa.com
DNS Name=*.bxjyb2jvda.net
DNS Name=whoismrrobot.com
DNS Name=seeso.com
DNS Name=fsoc.sh
DNS Name=www.fsoc.sh
DNS Name=conficturaindustries.com
DNS Name=whereismrrobot.com
DNS Name=www.whoismrrobot.com
DNS Name=www.whereismrrobot.com
DNS Name=evil-corp-usa.com
DNS Name=www.seeso.comIt’s really easy to understand that this is Morse code, but I’m extremely poor at solving such puzzles manually. Therefore, I decided to apply a more technical way.
https://www.fsoc.sh/assets/main.js
addHandlers: function() {
var t = this;
this.$(".eye__form").on("submit", this.handleSubmit), this.textView.on("typingEnded", function() {
t.appendEye(), t.startCursor("MzkzMzUzNTM5NTMzMzk1Mzc5OTUzNzMzMzM1MzUzOTM1Mw==")
})
},
startCursor: function(t) {
var e = this;
e.$(".eye__cursor").css("opacity", 0).removeClass("typing"), setTimeout(function() {
e.handleBlinkTime(window.atob(t), 0)
}, 500)
},
handleBlinkTime: function(t, e) {
var n = 300,
r = t.charAt(e),
i = 0,
o = n;
switch (r) {
case "9":
i = 3 * n;
break;
case "3":
i = n;
break;
case "5":
o = 3 * n;
break;
case "7":
o = 7 * n
}
var u = this;
i && u.$(".eye__cursor").css("opacity", 1), setTimeout(function() {
u.$(".eye__cursor").css("opacity", 0), setTimeout(function() {
t.length > e + 1 ? u.handleBlinkTime(t, e + 1) : setTimeout(function() {
u.handleBlinkTime(t, 0)
}, 4e3)
}, o)
}, i)Actually, the flicker speed of the cursor controls
t.startCursor("MzkzMzUzNTM5NTMzMzk1Mzc5OTUzNzMzMzM1MzUzOTM1Mw=="), and if verified in ASCII, it turns out 3933535395333953799537333353539353. 3 this is the point "."
5 separates the letters ""
7 represents the separator "/" in the Morse code
and 9 is a dash "-"
3933535395333953799537333353539353
.-…. .- ...- ./-- ./... .- .. == LEAVE ME HERE
It should be added that in the second season the series retained the extreme realism of computer scenes. Each hacking and operation is performed in the correct sequence and using the correct tools. In the first season, we saw the Kali Linux operating system, using the bashdoor (shellshock) vulnerability to get the / etc / passwd file, hacking the automobile CAN bus using candump utility, scanning surrounding the device with the active Bluetooth utility btscanner from the Kali Linux kit, using the bluesniff sniffer for MiTM attacks followed by launching the Meterpreter shell.
In the first series of the second season, all the technical details - the SET framework, ransomware, IRC logs, the BitchX client and more - are also shown quite reliably.
Remark: In one of the frames, a QR code flashes, which points to one of the domains in the list above: http://www.conficturaindustries.com .

The code is poorly recognized from the frame, here is a clear copy :

Apparently, the future Mr Robot series will also not be left without Easter eggs.
Technical advisers Mr Robot from the hacker community: @KorAdana , @ ryankaz42 , @AndreOnCyber , @MOBLAgentP , @IntelTechniques , @marcwrogers .
