Security agency and "new" technologies
The story of how not to do authorization, especially in areas important for life and property, such as, for example, managing an alarm through the application from the phone.

Small preface
It all started with the fact that I built a house, and a house without a security alarm can exist in our realities, of course, but nothing can be left there in the slightest degree (the sad cases of the neighbors confirm this). While the decoration was being made inside and outside, the keying and disarming of the key did not cause any inconvenience.
The house has a garage, the gate opens with a remote control and, accordingly, a car is put in there. If the house is guarded, the opening from the remote control will trigger a “alarm” at the gate and after 2-3 minutes the arrival of serious guys. To avoid this, you must first remove the guard (open the vestibule, attach the key, close the vestibule, get into the car again) and then open the gate. And somehow this procedure is a bit annoying, especially in winter, and indeed all the "magic" is somehow lost.
Of course, you can slyly do it so that the opening of the gate removes the alarm, but I haven’t gotten to that yet.
But I heard that our security agency has a miracle application "Mobile Phoenix Keyboard". The application is not exactly theirs, but they work with it. With it, you can control the alarm from your phone, which already more or less brings back the joy of using it all.
And now the story itself
To connect the security management from the application, you need to come to the office of the security agency, find the necessary engineer, pay 400 rubles for the “tune-up” to the cashier, and you will be given an account, which is driven into the settings on the phone and voila, you can steer the guards push notifications and not know grief.
Everything would be fine, but when you register, you are given a login in the form of three letters, for example abb (initials), and the password is made from the last four digits of the phone number (as the engineer said - not to forget), that is, for example 0808. A little taken aback by what he heard, I asked if the password could be set differently, they said that it was possible, but only numbers. Well, ok, I asked myself the right password and retired to test how everything works.
In my head, meanwhile, the idea had already matured - but would you try ...
We take an iPhone, connect it to Mac, run:, we rvictl -s iPhone_UDIDcling to the new interface through Wireshark and see how it works and what it sends to our application. You can take other devices / tools, but I have such.
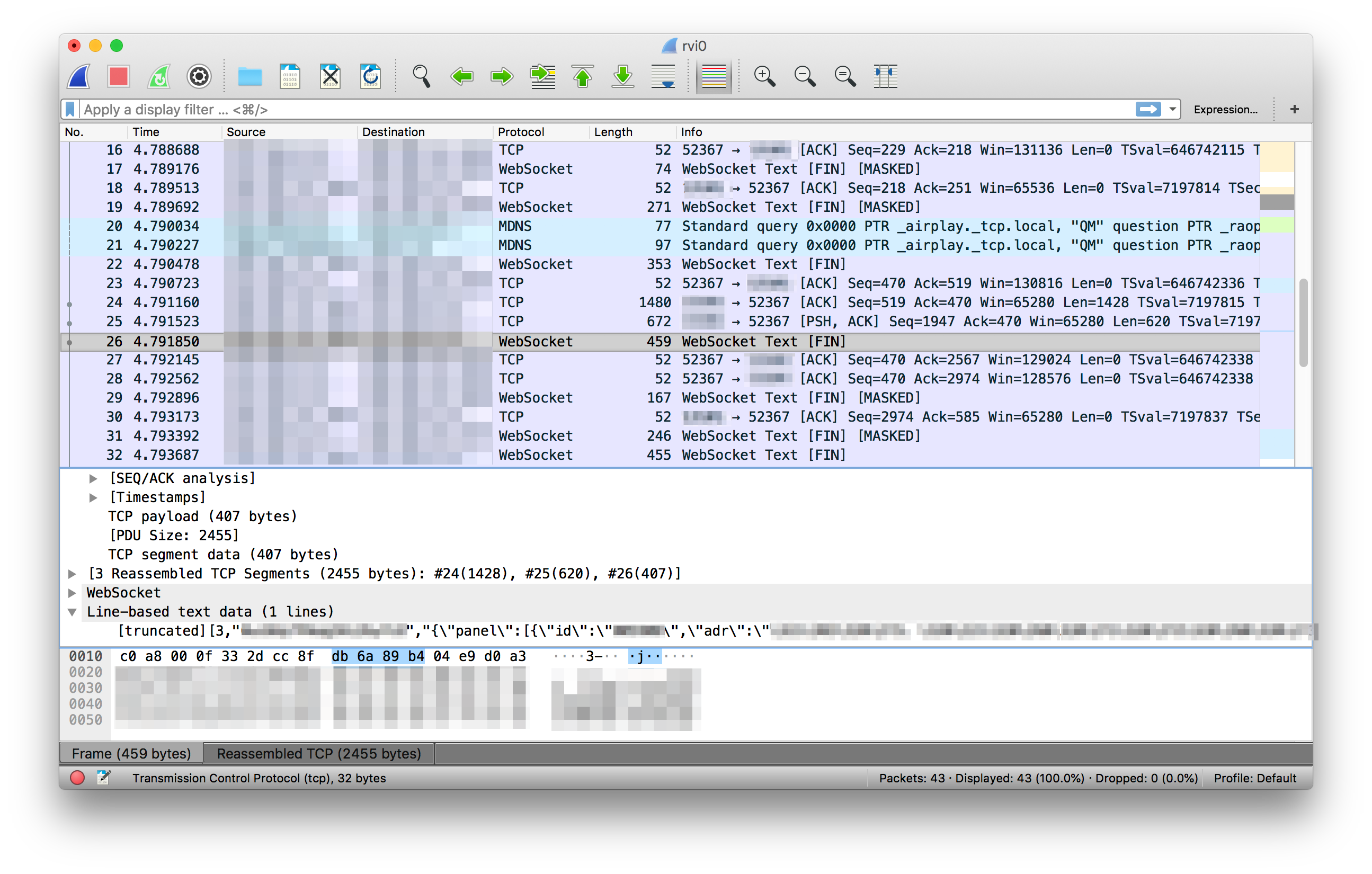
It works, it turns out, through the wamp protocol - this is essentially almost the same web socket. Naturally, nothing is encrypted and you can see exactly how requests are sent and actually repeat them.
Now we are trying to reproduce the received requests. All this for the speed of tests, you can put an extension for chrome like "Web Socket Client" and try there.
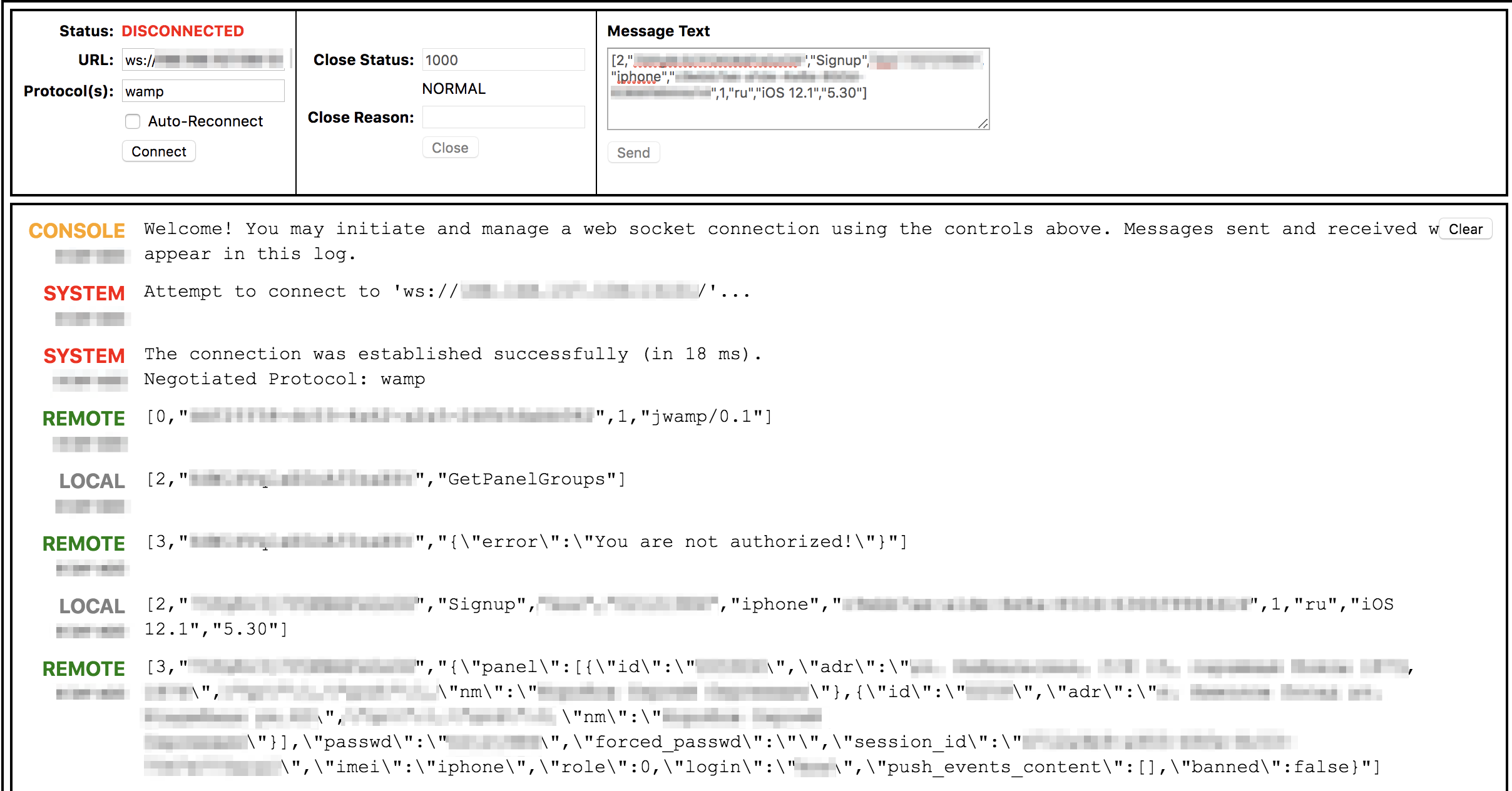
After making sure that everything works exactly as expected, we quickly write the client, for example, to node.
Note that the API responds to us with different messages when the user is not found at all and when the password is incorrect. This will speed up the process.
Our client will be pretty dumb, but nonetheless effective. The client enumerates all logins consisting of 3 letters. If the login exists, it starts brute force password search; if not, proceed to the next one. The password is moved in the range from 0000 to 9999.
We start all this and wait. The logins moved pretty quickly (10 minutes), it turned out about 150 pieces (the service is not so much used). The password for each login is approximately 8 minutes. There are no restrictions on checking in the API. And you can hammer multithreaded.
Passwords were selected in 100% of cases. If the password is successfully selected, the API spits out such information as: the owner’s full name, addresses (there may be many objects), some tokens (apparently for sending them to push), session id, and so on.
By authorizing, you can respectively disarm the entire object. Objects themselves came across rather distant from the city. If this information fell into the hands of the “bad guys,” the autopsy, as it were, of a protected object, would have passed without any problems, and then it could have been safely guarded and no one would have noticed anything.
Realizing that I myself am a client of this office - it became a bit uncomfortable.
Pleases one, apparently some kind of monitoring the company has or may have accidentally noticed, but after a while the application stopped accepting passwords and suggested contacting the office.
As a result, logins changed everything and made normal passwords. The protocol, however, was as unencrypted, and remained, but at least something.
What is this all about? Maybe after that someone will want to make their system a bit safer, and someone who uses the same service with similar passwords will look at it from the other side and ask for action. Such simple actions will slightly increase the level of security.
I deliberately do not give names here and as much as possible depersonalized all the data, so that those who recognize themselves can draw conclusions :)
PS This article is for informational purposes only, the problems described here are no longer relevant at the time of publication - the company took action.
