As a vulnerability in REG.RU allowed to get registration data of any domain
Today I want to talk about how back in 2012 I found a vulnerability in the domain registration system of the company REG.RU. Very often I see stories in which the authors talk about vulnerabilities while mentioning that the company did not pay enough attention to the found bug for a long time or did not fix it at all. In my case, everything was exactly the opposite, and the vulnerability was eliminated very quickly.

In September 2012, REG.RU started registering domains in the ru.com zone and sent all its customers letters offering for free for the first year a domain in the new zone with the name of an already registered domain in the zones ru , RF , su , com , net .
Getting a free domain turned out to be quite simple: you had to follow the link from the letter, enter the activation code for the domain, and the domain was registered for free for a year.

Before registering a domain, the system offered to familiarize itself with the contact details of the “original” domain for which the gift domain will be registered, but this data was open only for viewing without editing so the meaning of their display was not clear. However, this was the first bug: the registration of a new domain was available by the link of the form
REG.RU specialists made it so that any contacts were not shown completely, but only the first 7 characters of each field were displayed, which theoretically should not fully disclose information about the domain owner, however, for example, my first and last name turned out to be less than 7 characters long and they shown completely. Well, plus to everything, if you show the first 7 characters of the name, you can often guess which characters to add, a simple example is “Vladimi”.
This bug was corrected fairly quickly, and now the system showed only the first 4 characters, which was much better, although a person with the name “Han Solo” would not be very pleased.
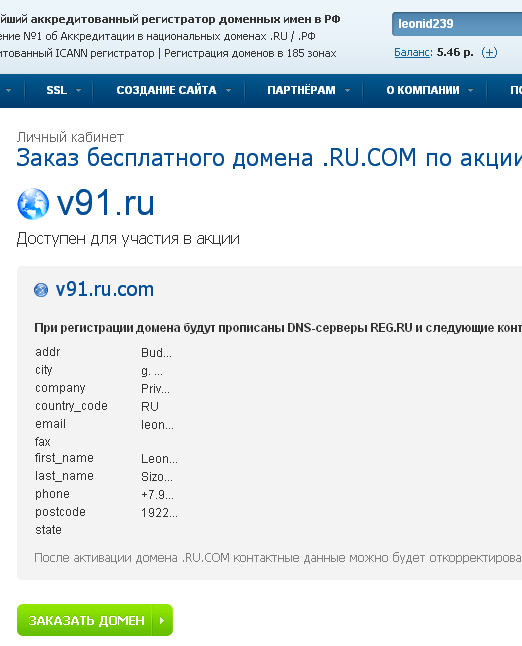
The next bug is the ability to register a domain without entering an activation code. So that all domain owners did not run at once to register free domains, REG.RU decided to send letters not immediately, but within a couple of days, so the load was distributed evenly. From a technical point of view, it was like this: in the database in the table with domains, a new column “Authorization code” was created with a null value, and from time to time users were sent letters with the simultaneous filling of this field with the generated code. A simple search could go through the link of the form
There was nothing wrong with registering such a domain, but after registering, you could see the full contact details (name, address and telephone number) of the owner of the “original” domain without hidden symbols. It was easy to fix this bug by simply adding a check for a non-empty authorization code during registration, which the REG.RU specialists also promptly fixed.
After a while, I found another bug, but it required a bit more action than just busting the service ID. To simplify the registration procedure for gift domains, REG.RU made it possible to register a domain without entering an authorization code from a letter, if the e-mail account in the reg.ru system coincided with the e-mail address specified as a contact in the original domain. For the user, it was quite convenient, but in terms of security, everything was not so good.
In 2012, there was no law on the protection of personal data in the current edition, and in many domains in the zone ruYou could see the contact e-mail address through Whois. At the time of finding this bug, the e-mail address was already hidden, but through the services of viewing the history of the Whois, the e-mail could be viewed, and, most likely, it was relevant. After that, it was necessary to try to register in the REG.RU system with this e-mail address and after that without an authorization code get a free domain, which in turn opened access to the contact information of the original domain.
To be brief, the procedure is as follows:
Errors that were made by REG.RU could potentially lead to the leakage of a large amount of personal data of domain owners, but all the bugs were fixed very quickly. From the moment of writing the first letter (and I wrote it personally to the executive director of REG.RU) less than two days passed before fixing all the vulnerabilities, which, in my opinion, is quite a short time for a company of this size and with deadlines for fixing vulnerabilities in other corporations.

In September 2012, REG.RU started registering domains in the ru.com zone and sent all its customers letters offering for free for the first year a domain in the new zone with the name of an already registered domain in the zones ru , RF , su , com , net .
Getting a free domain turned out to be quite simple: you had to follow the link from the letter, enter the activation code for the domain, and the domain was registered for free for a year.

Before registering a domain, the system offered to familiarize itself with the contact details of the “original” domain for which the gift domain will be registered, but this data was open only for viewing without editing so the meaning of their display was not clear. However, this was the first bug: the registration of a new domain was available by the link of the form
https://www.reg.ru/domain/new/get_free_ru_com?service_id=XXXX, and the service ID could simply be sorted out when it saw who the domain was registered to.REG.RU specialists made it so that any contacts were not shown completely, but only the first 7 characters of each field were displayed, which theoretically should not fully disclose information about the domain owner, however, for example, my first and last name turned out to be less than 7 characters long and they shown completely. Well, plus to everything, if you show the first 7 characters of the name, you can often guess which characters to add, a simple example is “Vladimi”.
This bug was corrected fairly quickly, and now the system showed only the first 4 characters, which was much better, although a person with the name “Han Solo” would not be very pleased.

The next bug is the ability to register a domain without entering an activation code. So that all domain owners did not run at once to register free domains, REG.RU decided to send letters not immediately, but within a couple of days, so the load was distributed evenly. From a technical point of view, it was like this: in the database in the table with domains, a new column “Authorization code” was created with a null value, and from time to time users were sent letters with the simultaneous filling of this field with the generated code. A simple search could go through the link of the form
https://www.reg.ru/domain/new/get_free_ru_com?service_id=XXXX, increasing the service ID to the value when the system had not yet managed to issue an authorization code to such a domain and register a domain with an empty code.There was nothing wrong with registering such a domain, but after registering, you could see the full contact details (name, address and telephone number) of the owner of the “original” domain without hidden symbols. It was easy to fix this bug by simply adding a check for a non-empty authorization code during registration, which the REG.RU specialists also promptly fixed.
After a while, I found another bug, but it required a bit more action than just busting the service ID. To simplify the registration procedure for gift domains, REG.RU made it possible to register a domain without entering an authorization code from a letter, if the e-mail account in the reg.ru system coincided with the e-mail address specified as a contact in the original domain. For the user, it was quite convenient, but in terms of security, everything was not so good.
In 2012, there was no law on the protection of personal data in the current edition, and in many domains in the zone ruYou could see the contact e-mail address through Whois. At the time of finding this bug, the e-mail address was already hidden, but through the services of viewing the history of the Whois, the e-mail could be viewed, and, most likely, it was relevant. After that, it was necessary to try to register in the REG.RU system with this e-mail address and after that without an authorization code get a free domain, which in turn opened access to the contact information of the original domain.
To be brief, the procedure is as follows:
- Go to the page of the form
https://www.reg.ru/domain/new/get_free_ru_com?service_id=XXXXand look at the domain name with this ID, for example, habr.ru.com . - Viewing through the service Whois History find e-mail address for the domain habr.ru .
- Using this e-mail address, we create an account in the REG.RU system (no confirmation of the ownership of the e-mail address was then required).
- Without entering the confirmation code register the domain habr.ru.com and see the full contact details of the owner habr.ru .
Errors that were made by REG.RU could potentially lead to the leakage of a large amount of personal data of domain owners, but all the bugs were fixed very quickly. From the moment of writing the first letter (and I wrote it personally to the executive director of REG.RU) less than two days passed before fixing all the vulnerabilities, which, in my opinion, is quite a short time for a company of this size and with deadlines for fixing vulnerabilities in other corporations.
Go to VPS.today - a site for searching virtual servers. 1400 tariffs from 120 hosters, convenient interface and a large number of criteria for finding the best virtual server.