Two-headed monster in the world of viruses: GozNym

Employees of IBM X-Force Research discovered a new trojan, which is a hybrid of the well-known malware Nymaim and Gozi ISFB. It turned out that the Nymaim developers combined the source code of this virus with part of the Gozi ISFB code. The result was a hybrid that was actively used in attacks on a network of 24 banks in the USA and Canada. With this malware, millions of dollars have been stolen. The hybrid viral product is called GozNym.
According to information security experts, this hybrid took the best from the two viruses mentioned above: from Nyamaim the malware inherited the ability to hide its presence from antiviruses, from Gozi - the ability to penetrate users' PCs. GozNym is unofficially called the "two-headed monster."
Targeting: Financial Organizations in North America
The developers of the new virus sent it to organizations in North America - in the United States and Canada. Currently, there are 22 known virus-affected banks, credit institutions, and popular e-commerce platforms. Also listed are two financial companies from Canada.

Source code - where is it from?
How was the hybrid created? It has already been mentioned above that this virus consists of parts of two other malware. The source code of the first, Gozi ISFB, was repeatedly laid out on the Web. This happened for the first time in 2010. The second time - in 2015, when the sources of a modified version of this software were posted on the Internet.
As for Nymaim, its developers are the only possible source of source code. Most likely, it was the Nymaim team who took part of the Gozi ISFB code, combined it with their product, and received Frankenstein in the world of viruses.
From Nymaim to GozNym,
Nymaim operates in two stages. Initially, this malware penetrates computers using exploit kits, and after entering the PC, it performs the second stage - launching two executable files that complete the infection of the victim’s machine.
The original virus, Nymaim, uses encryption, anti-VM, anti-debugging and obfuscation of the program code execution sequence, i.e. obfuscation of control flow. Until now, this virus has been used primarily as a dropper.. Droppers (Dropper) - a family of malicious programs (usually a Trojan) designed for unauthorized and hidden from the user installing on the computer victims of other malicious programs contained in the body of the dropper or downloaded over the network. This type of malware usually without any messages (or with false messages about an error in the archive, incorrect version of the operating system, etc.) downloads files from the network and saves files on the victim’s disk with their subsequent execution.
Nymaim, as you know, was created by a team of developers who have been managing this malware for several years. At the moment, traces of the presence of the dropper are found on the PC of users in Europe, North America, South America.
Of course, far from all of the cybercriminals' operations using Nymaim are documented. However, there is evidence of 2.5 million infections using the Blackhole Exploit Kit (BHEK) only at the end of 2013.

IBM researchers note that Nymaim has started using the Gozi ISFB module, the web injection injection DLL since 2015. The final version of the hybrid, which is a full integration of two malware, was discovered only in April 2016. In its hybrid incarnation, Nymaim is executed first, and then the Gozi ISFB executable module is launched.
Some technical information
Before merging into a single whole, the Nymaim malware used the Gozi ISFB DLL to inject the victim into the browser and conduct web injections. The size of the DLL was about 150 KB and was a valid Portable Executable (PE) file.
New versions of Nymaim began to use not the DLL, but the Gozi ISFB code itself. Instead of a 150 KB file, Nymaim now injects 40 KB of buffer into the browser. This buffer has all the features of a Gozi ISFB. But there are differences: now this is no longer a valid PE file, its structure is different and is a shell code. This uses an Import Address Table (IAT) and no PE headers.

Old version of Nymaim where Gozi ISFB DLL is used.

New buffer and new jmp_nymaim_code hybrid function (below)
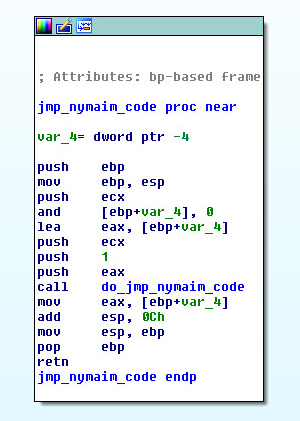
This piece of code is always executed when Gozi ISFB is required by Nymaim for the operation. In this case, the function prepares the required parameters, the type of operation, the size of the allocated memory, etc. for Nymaim. Then Nymaim takes over and returns the result for Gozi ISFB.
The MD5 hash in this case is 2A9093307E667CDB71884ECC1B480245.
How to protect yourself?
This is not so simple. The malware described above is unique and can create big problems for both an individual and the whole company. In order to avoid such a development of events, it is worth following the usual rules for working with information in organizations.
True, this does not always help, especially if the company has a lot of employees working with computer equipment with access to the Network.
In this case, we also recommend using our security tools: IBM Security Trusteer Pinpoint Malware Detection and IBM Security Trusteer Rapport . These services ensure the timely detection of infected devices on the network, the destruction of malware if the system is already infected, plus they prevent the process using various protection methods.
