Cyber Counterintelligence. How Palantir Can Catch Snowden
Together with Edison, we continue to investigate the capabilities of the Palantir system.
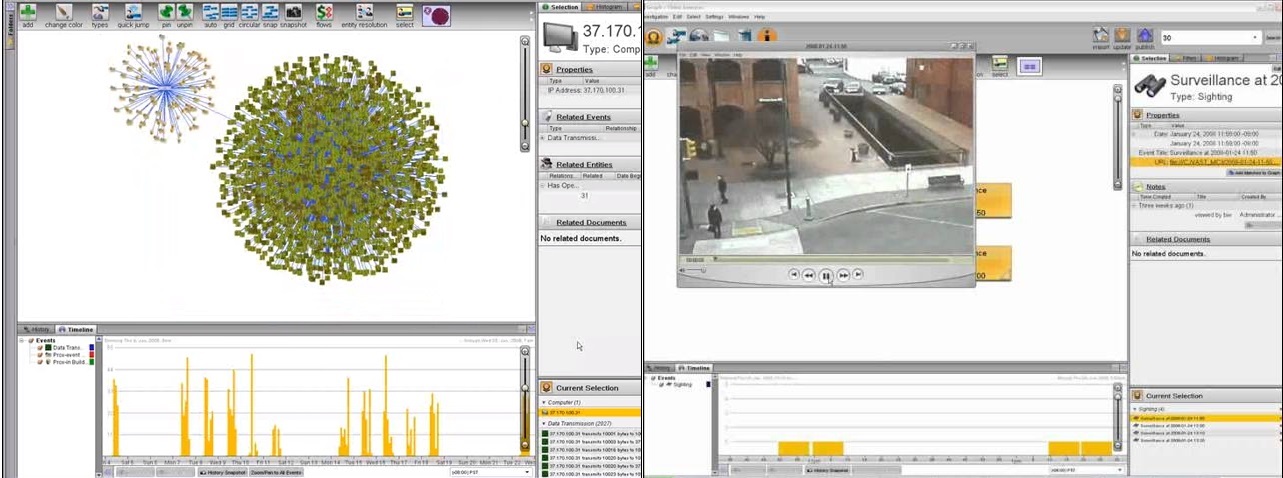
Palantir system allows you to catch "Snowdens", as long as they have not become global heroes and were just spies, which at any moment it could bean ice pick anything.
Despite the fact that the leadership of Palantir, as it can, is fighting for freedom and logging every single action in the system, such systems pose a huge danger to future “snowboards”. Forewarned is forearmed.
Consider the case when, thanks to the Palantir platform, a special investigation was carried out to calculate an unreliable embassy employee who was leaking information to a third-party organization.
The investigation analyzed network traffic, router information, contact card and employee badges, events, social media data, and video surveillance data. Thanks to static, temporal analysis, geodata analysis, and visual analysis, the mole was uncovered.
Thirtieth destroy.
(Special thanks to Alexei Vorsin, Russian expert on the Palantir system, for helping prepare this article)
0:00 In this video we used data from access card usage logs, IP logs and a list of personnel identification numbers.
0:07 On the Palantir platform, we can combine, and combine all this data into one investigation, to identify a suspicious exchange of information and associate it with a possible suspect.
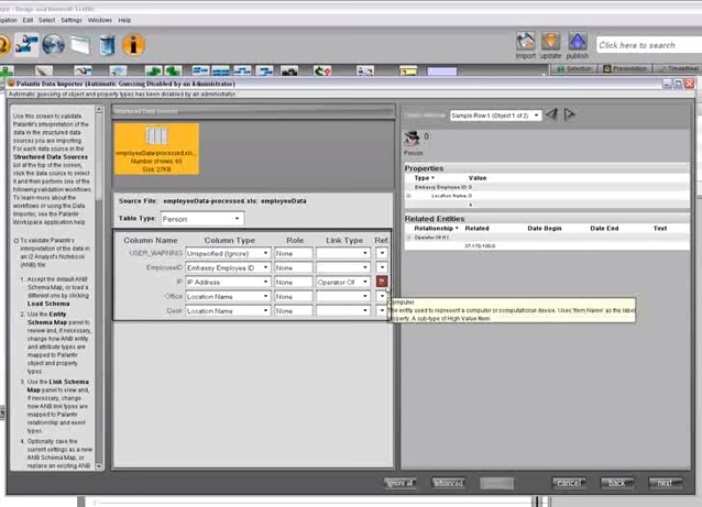
0:20 First, we import the data.

0:25 Palantir Import Wizard (Palantir Import Wizard) allows the user to lay out the data, building a structure dynamically, depending on the source.
0:30 The Import Wizard automatically imports data, creates objects and assigns properties to them, links objects according to specified conditions, and deletes the resulting duplicates identified based on custom restrictions.
0:43 We will begin our investigation with all the events associated with access cards to the secret area (classified space - the territory is not completely clear or information is meant) and displayed on the graph.
0:49 Each of these events contains the time of gaining access and the time of terminating access, but we also see several incomplete events when someone skipped behind a colleague (piggybacking, one of the values is to ride on someone's back) while using that card.

0:57 We see an interesting pattern: Three times a week, a Thirty worker gains access to a secret area.

1:03 Using 30 employee’s office neighbors as a starting point, we will track down possible episodes of unauthorized use of computers through the study of data transfer events related to access to sensitive data.

1:13 Partially coincident events indicate unauthorized access to data due to computers not belonging to the secret area

1:21 Our search revealed unauthorized data transfer to the IP address 100.59.151.133.

1:30 “Search around” (Palantir tool), applied to a suspicious IP, showed 18 cases of data transfer to 12 different computers of the embassy.
1:37 We auto-arranged (autoarrange, apparently also a tool) graph, and colored objects by type, for the sake of clarity.

1:43 On the histogram, we see that all these 18 cases use port 8080 and the entire amount of data transferred came from the organization.

1:50 On the assistant “timewheel”, we see that the data was transmitted for four weeks, every Tuesday and Wednesday, and one transmission a day at the beginning, up to three per day at the end.
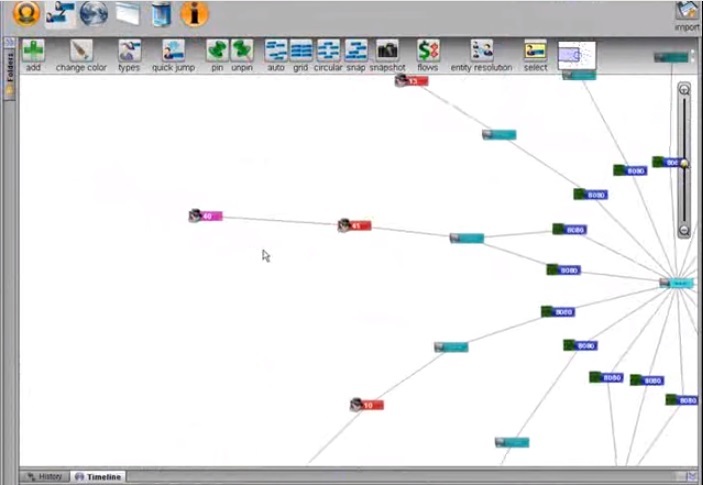
2:01 We added authorized users and their office neighbors to the graph using "search around."

2:07 Now, choosing these employees individually, we will find all the events related to them related to gaining access or transmitting information, and then, by timeline, we will track when the transfer of data to a suspicious IP was authorized.
2:21 We see an unauthorized transfer while a 40 employee had access to a secret area.

2:29 Repeating this procedure for the rest of the employees, we found 14 cases when the corresponding employee had access to the secret area during data transfer, 13 cases when they probably were not in the office, and 6 when they were seen away from their workplace.

2:43 Only employee 30 was present while employee 31's computer was transmitting data, suggesting that the thirtieth saw the suspect or is himself.
2:51 To confirm suspicions about the Thirtieth, we can conduct an additional test by creating several time filters corresponding to the time of suspicious data transmission. Using these filters, we investigate possible intersections with time when the suspect had access to the secret area.

3:09 The suspect had to have access to the computer all eighteen times when the data was being transferred.

3:11 On the graph are all the events related to access to the secret area. We can add our filters to see all intersecting events.

3:22 “Search Around” gave us all the event-related employees that we may perceive as suspects.

3:29 Finally, the filter among the embassy staff gives us two potential suspects, one of them, of course, Thirtieth.

3:39 Our workflow confirmed the suspicion: Thirtieth is a malicious insider. A temporary analysis of IP logs and access logs, not only gave us the opportunity to identify unauthorized use of computers, but also to associate this with a specific individual.

0:00 Social network analysis and spatial analysis - written on the screen.
We got intelligence data suggesting that the embassy employee, driven by malicious intent, uses social networks to contact the criminal organization and transmit data.
0:10 Our data: a list of 6000 users of some kind (Flickr? Or an invented Flitter network?) Social networks and a list of links between their accounts.
[0:15 Palantir Import Wizard) allows the user to lay out data by building a structure dynamically, depending on the source.
0:23 The Import Wizard automatically imports data, creates objects and assigns properties to them, associates the objects according to specified conditions and deletes the resulting duplicates identified on the basis of custom restrictions.] This entire piece is repeated in the first video.
0:41 There is information that our suspect has more than 40 contacts on Flickr. We can conduct a quick search of 6000 accounts to select all containing from 42 to 48 contacts.

1:01 We also know that this embassy worker is associated with three accomplices, each with 30 to 40 contacts.
1:09 Using search around, we will find these characters and add them to the graph.
1:16 This search around revealed 5 accounts that have three contacts matching the description.
1:28 Having selected one of these accounts, we will examine its social network.
1:34 Let's start with Lafouge and get all of his potential accomplices back using the saved request in search around.
1:44 Now we’ll find out whether they communicate with the leader through a common intermediary, or whether everyone has their own intermediary. To do this, we will find all users who are associated with accomplices, and who have no more than six contacts, as intelligence has reported that the intermediary has only one or two contacts, except for accomplices.
2:06 We see an obvious common intermediary, right in the center of the graph. Nevertheless, to make sure that there is only one intermediary in this network, we will look for contacts of potential partners among contacts of accomplices.

2:23 The leader has hundreds of contacts, many of them international. The search revealed that in our case, a common intermediary is used to bring all contacts together, to a leader named Cornell.
2:36 I think we discovered our network. Of course, the result is still crude, as we must confirm that the leader is not directly connected with the embassy employee or accomplices.

2:47 Our search shows that this potential leader is associated with an accomplice; this information allows us to remove Lafuzh from the list of suspects.

2:55 Now, let's apply the same logic to the four remaining suspects.
3:02 In the end, we got 3 networks that almost completely coincided with the description given by the intelligence.
3:09 One of these networks, built around Shafter, details of his network can be seen using spatial analysis. For this analysis, we added the coordinates of the city specified in the profile by users of the social network to Palantir.

3:23 Location data does not fully match the intelligence provided.

3:30 And the embassy employee and his accomplices live in Prunov, an intermediary in Kenwich, and a leader in Kuvnic. The only possible explanation for this is that for some reason, accomplices should be within the reach of an embassy employee.

3:45 The mediator may not be physically connected to the network, for greater security, and the leader can live near the border to control the transfer of data outside of Flavia.
3:57 The location of the leader may also indicate that the criminal organization has connections in the neighboring state of Trium.
Analysis of outdoor surveillance records.
0:00 We have ten hours of recordings from surveillance cameras recording the meeting of our suspects.
0:09 Dates and times of recordings: Wednesday, January 24, from 10:00 to 15:00 and Saturday, January 26, from 8:00 to 13:00.

0:18 We also know that the camcorder is located within walking distance of the embassy.
0:24 For our investigation, we imported the metadata for the video as additional events in Palantir, and each is associated with a ten-minute passage.

0:36 Based on our suspicion of Thirtieth, we will look for passages corresponding to the time when he was outside the embassy.

0:45 To do this, we will create temporary filters for the time when Thirtieth was to leave the embassy.
0:55 We found four such events on Wednesday, and, unfortunately, not a single one on Saturday, since Thirtieth was not at the embassy that day.

1:10 By watching the video, we can create events associated with each suspicious moment that we discover.

1:18 We previously watched the video for Wednesday, and did not find anything interesting.
1:23 The Saturday video, however, contains an interesting point: the two meet and exchange portfolios.

1:31 We created the corresponding meeting event, which includes a description, a screenshot, and other metadata.

1:48 Here we see a completed dossier about the event: time, duration, comments, related media files.

1:55 Having created this event, we integrate it into the investigation.

2:00 If we confirm that one of the participants of the meeting is the Thirtieth, we will be able to connect him and the meeting.
2:17 Finally, we can publish this new data by making it available to other Palantir users.

2:26 With Palantir’s advanced analysis capabilities, we were able to relate disparate data sources to each other and performed a temporary, statistical, social, spatial analysis, as well as interdependence analysis in one unified analytical environment.
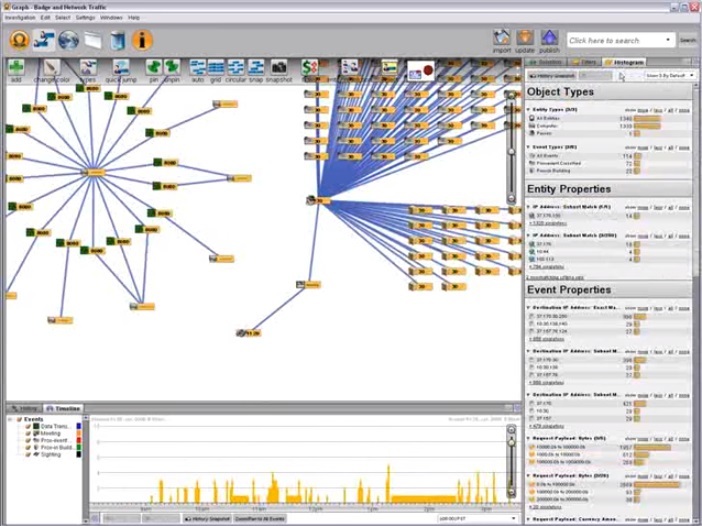
2:40 Our investigation on the Palantir platform not only quickly revealed the use of embassy computers to seize information, but also the employee responsible for this, as well as allowed us to map his social connections.
More about Palantir:

Palantir system allows you to catch "Snowdens", as long as they have not become global heroes and were just spies, which at any moment it could be
Despite the fact that the leadership of Palantir, as it can, is fighting for freedom and logging every single action in the system, such systems pose a huge danger to future “snowboards”. Forewarned is forearmed.
Consider the case when, thanks to the Palantir platform, a special investigation was carried out to calculate an unreliable embassy employee who was leaking information to a third-party organization.
The investigation analyzed network traffic, router information, contact card and employee badges, events, social media data, and video surveillance data. Thanks to static, temporal analysis, geodata analysis, and visual analysis, the mole was uncovered.
Thirtieth destroy.
(Special thanks to Alexei Vorsin, Russian expert on the Palantir system, for helping prepare this article)
Part 1
0:00 In this video we used data from access card usage logs, IP logs and a list of personnel identification numbers.
0:07 On the Palantir platform, we can combine, and combine all this data into one investigation, to identify a suspicious exchange of information and associate it with a possible suspect.
0:20 First, we import the data.

0:25 Palantir Import Wizard (Palantir Import Wizard) allows the user to lay out the data, building a structure dynamically, depending on the source.
0:30 The Import Wizard automatically imports data, creates objects and assigns properties to them, links objects according to specified conditions, and deletes the resulting duplicates identified based on custom restrictions.

0:43 We will begin our investigation with all the events associated with access cards to the secret area (classified space - the territory is not completely clear or information is meant) and displayed on the graph.
0:49 Each of these events contains the time of gaining access and the time of terminating access, but we also see several incomplete events when someone skipped behind a colleague (piggybacking, one of the values is to ride on someone's back) while using that card.

0:57 We see an interesting pattern: Three times a week, a Thirty worker gains access to a secret area.

1:03 Using 30 employee’s office neighbors as a starting point, we will track down possible episodes of unauthorized use of computers through the study of data transfer events related to access to sensitive data.

1:13 Partially coincident events indicate unauthorized access to data due to computers not belonging to the secret area

1:21 Our search revealed unauthorized data transfer to the IP address 100.59.151.133.

1:30 “Search around” (Palantir tool), applied to a suspicious IP, showed 18 cases of data transfer to 12 different computers of the embassy.
1:37 We auto-arranged (autoarrange, apparently also a tool) graph, and colored objects by type, for the sake of clarity.

1:43 On the histogram, we see that all these 18 cases use port 8080 and the entire amount of data transferred came from the organization.

1:50 On the assistant “timewheel”, we see that the data was transmitted for four weeks, every Tuesday and Wednesday, and one transmission a day at the beginning, up to three per day at the end.

2:01 We added authorized users and their office neighbors to the graph using "search around."

2:07 Now, choosing these employees individually, we will find all the events related to them related to gaining access or transmitting information, and then, by timeline, we will track when the transfer of data to a suspicious IP was authorized.
2:21 We see an unauthorized transfer while a 40 employee had access to a secret area.

2:29 Repeating this procedure for the rest of the employees, we found 14 cases when the corresponding employee had access to the secret area during data transfer, 13 cases when they probably were not in the office, and 6 when they were seen away from their workplace.

2:43 Only employee 30 was present while employee 31's computer was transmitting data, suggesting that the thirtieth saw the suspect or is himself.
2:51 To confirm suspicions about the Thirtieth, we can conduct an additional test by creating several time filters corresponding to the time of suspicious data transmission. Using these filters, we investigate possible intersections with time when the suspect had access to the secret area.

3:09 The suspect had to have access to the computer all eighteen times when the data was being transferred.

3:11 On the graph are all the events related to access to the secret area. We can add our filters to see all intersecting events.

3:22 “Search Around” gave us all the event-related employees that we may perceive as suspects.

3:29 Finally, the filter among the embassy staff gives us two potential suspects, one of them, of course, Thirtieth.

3:39 Our workflow confirmed the suspicion: Thirtieth is a malicious insider. A temporary analysis of IP logs and access logs, not only gave us the opportunity to identify unauthorized use of computers, but also to associate this with a specific individual.

Part 2
0:00 Social network analysis and spatial analysis - written on the screen.
We got intelligence data suggesting that the embassy employee, driven by malicious intent, uses social networks to contact the criminal organization and transmit data.
0:10 Our data: a list of 6000 users of some kind (Flickr? Or an invented Flitter network?) Social networks and a list of links between their accounts.
[0:15 Palantir Import Wizard) allows the user to lay out data by building a structure dynamically, depending on the source.
0:23 The Import Wizard automatically imports data, creates objects and assigns properties to them, associates the objects according to specified conditions and deletes the resulting duplicates identified on the basis of custom restrictions.] This entire piece is repeated in the first video.
0:41 There is information that our suspect has more than 40 contacts on Flickr. We can conduct a quick search of 6000 accounts to select all containing from 42 to 48 contacts.

1:01 We also know that this embassy worker is associated with three accomplices, each with 30 to 40 contacts.
1:09 Using search around, we will find these characters and add them to the graph.
1:16 This search around revealed 5 accounts that have three contacts matching the description.
1:28 Having selected one of these accounts, we will examine its social network.
1:34 Let's start with Lafouge and get all of his potential accomplices back using the saved request in search around.
1:44 Now we’ll find out whether they communicate with the leader through a common intermediary, or whether everyone has their own intermediary. To do this, we will find all users who are associated with accomplices, and who have no more than six contacts, as intelligence has reported that the intermediary has only one or two contacts, except for accomplices.
2:06 We see an obvious common intermediary, right in the center of the graph. Nevertheless, to make sure that there is only one intermediary in this network, we will look for contacts of potential partners among contacts of accomplices.

2:23 The leader has hundreds of contacts, many of them international. The search revealed that in our case, a common intermediary is used to bring all contacts together, to a leader named Cornell.
2:36 I think we discovered our network. Of course, the result is still crude, as we must confirm that the leader is not directly connected with the embassy employee or accomplices.

2:47 Our search shows that this potential leader is associated with an accomplice; this information allows us to remove Lafuzh from the list of suspects.

2:55 Now, let's apply the same logic to the four remaining suspects.
3:02 In the end, we got 3 networks that almost completely coincided with the description given by the intelligence.
3:09 One of these networks, built around Shafter, details of his network can be seen using spatial analysis. For this analysis, we added the coordinates of the city specified in the profile by users of the social network to Palantir.

3:23 Location data does not fully match the intelligence provided.

3:30 And the embassy employee and his accomplices live in Prunov, an intermediary in Kenwich, and a leader in Kuvnic. The only possible explanation for this is that for some reason, accomplices should be within the reach of an embassy employee.

3:45 The mediator may not be physically connected to the network, for greater security, and the leader can live near the border to control the transfer of data outside of Flavia.
3:57 The location of the leader may also indicate that the criminal organization has connections in the neighboring state of Trium.
Part 3
Analysis of outdoor surveillance records.
0:00 We have ten hours of recordings from surveillance cameras recording the meeting of our suspects.
0:09 Dates and times of recordings: Wednesday, January 24, from 10:00 to 15:00 and Saturday, January 26, from 8:00 to 13:00.

0:18 We also know that the camcorder is located within walking distance of the embassy.
0:24 For our investigation, we imported the metadata for the video as additional events in Palantir, and each is associated with a ten-minute passage.

0:36 Based on our suspicion of Thirtieth, we will look for passages corresponding to the time when he was outside the embassy.

0:45 To do this, we will create temporary filters for the time when Thirtieth was to leave the embassy.
0:55 We found four such events on Wednesday, and, unfortunately, not a single one on Saturday, since Thirtieth was not at the embassy that day.

1:10 By watching the video, we can create events associated with each suspicious moment that we discover.

1:18 We previously watched the video for Wednesday, and did not find anything interesting.
1:23 The Saturday video, however, contains an interesting point: the two meet and exchange portfolios.

1:31 We created the corresponding meeting event, which includes a description, a screenshot, and other metadata.

1:48 Here we see a completed dossier about the event: time, duration, comments, related media files.

1:55 Having created this event, we integrate it into the investigation.

2:00 If we confirm that one of the participants of the meeting is the Thirtieth, we will be able to connect him and the meeting.
2:17 Finally, we can publish this new data by making it available to other Palantir users.

2:26 With Palantir’s advanced analysis capabilities, we were able to relate disparate data sources to each other and performed a temporary, statistical, social, spatial analysis, as well as interdependence analysis in one unified analytical environment.

2:40 Our investigation on the Palantir platform not only quickly revealed the use of embassy computers to seize information, but also the employee responsible for this, as well as allowed us to map his social connections.
More about Palantir:
