Directed Phishing - A Modern Security Threat

The spread of targeted phishing attacks is related to their effectiveness and the weak ability of traditional security solutions to resist them. While a regular phishing attack is being sent out massively, spear phishing attacks are carried out against specific subjects.
Spear phishing
Currently, the percentage of targeted phishing attacks, organized by sending e-mails in which a specific organization or group of people can be identified, is growing. Target users receive carefully designed phishing messages that force a person to enter confidential personal information - such as login and password, which give access to corporate networks or databases with the most important information. In addition to requesting credentials, targeted phishing emails can also contain malware.
Directed phishing has become the most common type of targeted attack for one simple reason: this technique really works, misleading even those users who are serious about security issues. It creates for hackers a strong point for penetrating the corporate network. According to a Check Point study conducted among more than 10 thousand organizations around the world, 84% of them downloaded at least one infected document over the past 12 months. This is because an attacker just needs to get an idea of the company or its specific employees on the Internet, and then write a letter that will prompt even the most vigilant employee to open a malicious attachment and thereby initiate a hacker attack.
Attack targets
To determine the list of targets, attackers can use several ways:
- get a list of employees from the site (the level of information trust is very high);
- Get a list of employees using sociotechnical techniques - call or mail (the level of information trust is very high);
- get the name from the metadata of documents posted on the site (the level of trust in information is high);
- linkedin (information confidence level - medium);
- parse social networks (the level of information trust is low).
The higher the level of trust in information, the higher the likelihood that this subject is directly connected with the organization of interest.
After preliminary collection of the list of probable employees of the organization, data is collected on their field of activity, areas of responsibility and horizontal connections. An entry point is also searched for to attack selected subjects. After analyzing the information received, you can make an attack scenario.
Attack Psychology
A targeted phishing attack always contains sophisticated sociotechnical methods and techniques for manipulating the human mind.
From the point of view of psychology, an attack by methods of social engineering always bypasses the analytical tools of the mind. It acts mainly at the level of the emotional sphere, habitually suppressed by most people engaged in mental work. That is why social engineering techniques are often successful even if the attacker's intelligence is noticeably lower than that of the victim.
High IQ prevents little deception, since SI methods strike patterns of behavior, deep fears and adaptive reflexes developed under the pressure of microsocium. In order for the developed block of critical perception of the victim not to interfere with the attack, they simply overload it with a data stream, switching to the analysis of secondary information, or use the urgency factor to disable it altogether and force it to act thoughtlessly. All this is like an attack on key nodes of a neural network.
One of the basic techniques of social engineering is the creation of a shortage of time, an event that the victim must react to immediately. Urgent decisions are difficult to make precisely because they have to act in conditions of a lack of reliable information. In such situations, there is no time to consult and check all the data reported to the attacker, so the victim begins to act, guided by strong feelings: the desire to help, the desire to gain recognition or to get rid of an unexpected problem as soon as possible. It is also often possible to play on the thirst for easy money, the fear of losing money, work, work results or reputation.
The victim can be told in the forehead that the situation is urgent, or allow her to come to this conclusion on her own. The second is more effective, since for a person it will be their own thought, which is beyond doubt. It is on her that he will rely in his minimal arguments, more and more imbued with confidence in the legend he has heard.
Example
Object of attack organization LLC "Camomile". From the company’s website, information was received about the head of the company, secretary and system administrator. With the help of a phone call, the name and email of the chief accountant were clarified. The full details of the company were obtained from the database OGRN / USRLE.
The main accountant and secretary were selected as the objects of attack, under which the following attack scenarios were used (vector - email):
Chief accountant:
- From: neutral address, such as %surname%%birthyear%@mail.ru
- Subject line: FWD reconciliation report
- Text of the letter: Good afternoon, full name. According to the preliminary agreement I will send a reconciliation report.
- Application: Act of reconciliation LLC Romashka.xls
Secretary:
- From: info@msk.arbitr.ru (fake address)
- Subject of the letter: Debt collection action
- The Moscow Arbitration Court filed a statement of claim No. 23401-16 for debt collection from Romashka LLC, a register of companies: ХХХХХХХХХХХХХХ, TIN: ХХХХХХХХХХХХХ, Legal address :, certificate of registration: ХХХХХХ based on the statement of claim by the counterparty for debt collection for services rendered .
- Claim:
- In accordance with Art. 395 of the Civil Code of the Russian Federation for the use of other people's money as a result of their unlawful retention, evasion of their return, other delay in payment thereof or unjustified receipt or savings at the expense of another person, interest on the amount of these funds is payable.
- Application: court decision 23401-16.docx
The so-called attacking means office backdoor . At the time of the attack, the system administrator can be “occupied” by an attack on the network perimeter, a DoS / DDoS attack on the site, etc.
Staff training
Many companies conduct trainings to raise staff awareness of social and technical attacks.
Technical protection measures against phishing, such as filtering and analysis of mail / web traffic, limiting the software environment, and preventing the launch of attachments, are very effective, but they cannot resist new threats and, more importantly, they cannot resist the human stupidity of
Periodic briefings and newsletters are an important component of staff training, but, as practice shows, their effectiveness is much lower than training employees on their own mistakes, given the factor of involvement in the process.
The simplest system that allows testing and training personnel to identify phishing attacks is as follows:
- Preparation of the script and letter templates;
- Phishing emails to users;
- Redirecting reacted users to a specialized warning page;
- Statistical accounting of attack efficiency.

Screenshot of the “notification” page generated by the sptoolkit framework. The project is currently frozen.
To facilitate this kind of “exercise”, you can use the specialized gophish framework. There are other utilities to facilitate the task of the social engineer, for example setoolkit, but they have redundant functionality and are intended more for an active attack. There are also several online services, but they are mainly English-speaking and are not suitable for use among the Russian-speaking purposes of a phishing company.
Gopgish is a multi-platform framework with a user-friendly web interface and simple deployment. This framework is developed on Golang and most likely will not work on shared hosting, keep this in mind.
Using it, you can create a phishing company for a specific group of users:
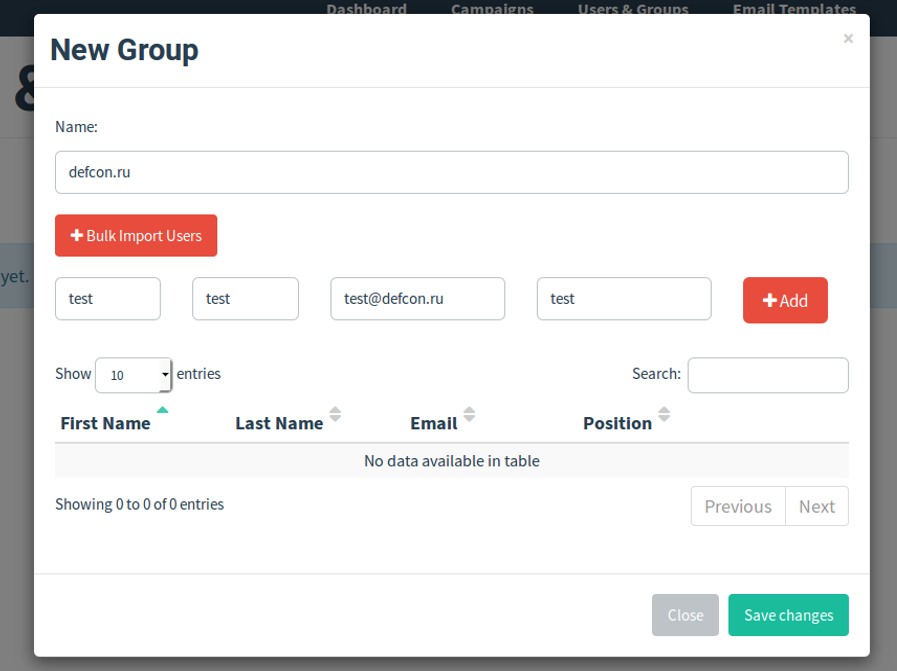
For mailing, you can apply a variety of templates. To evaluate the effectiveness of mailing, a tracking system is used:

On the phishing page, you can "collect" user-entered data:


After the company, you can evaluate its effectiveness:

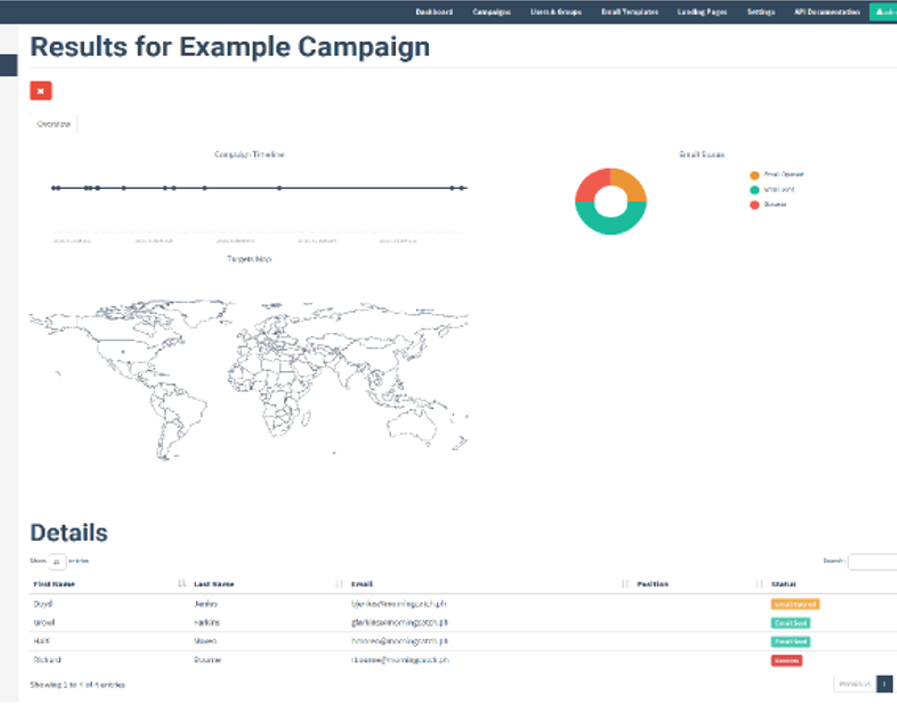
Precautionary measures
As protection measures, it is necessary to establish control over mail attachments and links, conduct trainings with personnel about the presence of new threats, observe safety measures and notify technical personnel of all suspicious cases.
