Ixia launches intelligent network packet broker - Vision ONE
Ixia, a provider of network testing, monitoring and protection solutions, has launched Vision ONE, a high-performance, intelligent network packet broker.
Vision ONE has 48 1 / 10GbE SFP + ports and 4 40GbE QSFP + ports.
Further description under the cut.
Vision ONE acts as the first step to security by providing reliable in-line connectivity for connecting security tools such as IPS, DLP and firewalls. It simultaneously connects monitoring tools, intrusion detection systems (IDS) and data recording / storage systems.

In this solution, Ixia has concentrated the most advanced features of transparency and traffic control, including the capabilities of the Ixia ATI (Application and Threat Intelligence) processor. Among them are SSL traffic decryption and in-depth packet analysis (DPI), which goes far beyond just checking for regular expression matching and provides accurate identification of application traffic. Vision ONE also performs various functions of packet processing (for example, deduplication, trimming, timestamps ...) and load balancing on the inline IB devices that are turned on (firewalls, IPS, etc.). This device can work with both inline and out-of-band devices at the same time.

The solution is quickly deployed and quickly included in the workflow thanks to an intuitive graphical user interface. This allows the company's IT staff to focus on improving security without wasting time on configuration.

A bit more about the Vision ONE

Advanced Packet Processing (AFM) features:
Deduplication - only one copy of the packet is sent to the analyzer

Where do duplicate packets come from?
Multiple tapes aggregate into the same analyzer.
One SPAN port usually generates repeated packets.
Removing headers- Detects and removes tunneling protocols from the header, for analysis by tools that do not support these protocols.


Examples of use:
• Translation: Deletes protocol headers that the analyzer does not understand and gives the packet in a supported format.
- MPLS, VNTag, FabricPath, etc.
• vTap Termination: Terminates traffic from Phantom vTap
• ERSPAN termination: Terminates traffic from remote offices / branches
Packet Trimming - truncates packets to a certain size and optionally inserts a “trailer” to get the original packet size before sending it to the analyzer.

Examples of use
• Analyzer efficiency: Reducing the size of the packet to send to the analyzer.
- Remove SSL-encrypted payloads before analysis
- Remove payloads for analyzers that study only headers
• Security: If the payload package is not needed for analysis, this function can be used to protect against the disclosure of confidential information, such as personal information (Personally Identifiable Information - PII) as required by many mandates such as PCI.
Masking data x - Allows you to hide certain data, while maintaining the overall frame size, so that personal information (Personally Identifiable Information - PII) is not transmitted to the analyzer.

Examples of using
• Protection of PII: Enterprises often have recommendations / obligations that oblige them not to store, transfer or otherwise disclose PII to internal or external users. Examples of such mandates are PCI (Payment Card Industry) or HIPAA in the US healthcare industry. Violations often lead to multi-million fines.
Timestamps (Packet Timestamping) - Adds a section containing a timestamp to each packet for a detailed study of the delay by analyzers.
Vision ONE uses PTP or NTP to obtain a reference time.

Examples of use
• Delay: The analyzer can determine the delay between any tapes in the network by comparing timestamps in the same packet from different places in the network.
Burst Protection- Adds an additional buffer to 1G interfaces to provide protection against events such as microburst and avoids data loss.
Examples of use
• Aggregation: When traffic is aggregated from different parts of the network into one 1G analyzer, a short-term excess of 1Gbps traffic is possible.
• Speed translation: When filtering 1G of data from a 10G link / interface, this functionality can protect the analyzer with 1G performance from short-term “burst”.
Ixia ATI (Application and Threat Intelligence) - accurate intelligent processing of application traffic based on in-depth packet analysis (DPI) and decryption of SSL traffic.
(applications and their activity, geolocation, device OS, browser, etc.)

Filtering applications


RegEx search and data masking

Flexible


ATIP traffic processing - understanding SSL
• Passive decryption - does not affect application performance
• Easy setup - only import certificates / keys
• All popular ciphers:
3DES, RC4, AES, SHA1 / 521/384/256/224 , MD5.
• SSL / TLS decryption support:
- SSL / TLS versions: SSL3.0, TLS1.0, TLS1.1 and TLS1.2.
- Exchange of asymmetric keys: RSA and ECDH.
- Symmetric keys: AES, 3DES and RC4.
- Hash algorithms: SHA and MD5.
- The maximum number of concurrent sessions: more than 1,000,000.
- Private key storage: in encrypted form with the attribute write only.
• Report encryption details - Netflow

Work with inline devices
• Supports parallel (for load balancing) and serial connection of inline devices, as well as any combination of these types of connections.
• To identify failed inline-devices in order to automatically overcome failures, single-stage and multi-stage transmission of heartbeat packets are used.
• Two modes of overcoming a failure:
- Redistribution of sessions from a failed inline-device to all active inline-devices.
- Switching all active sessions from a failed inline device to a backup inline device.
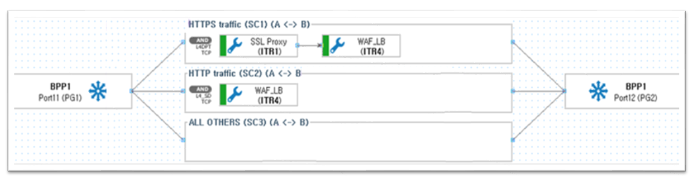
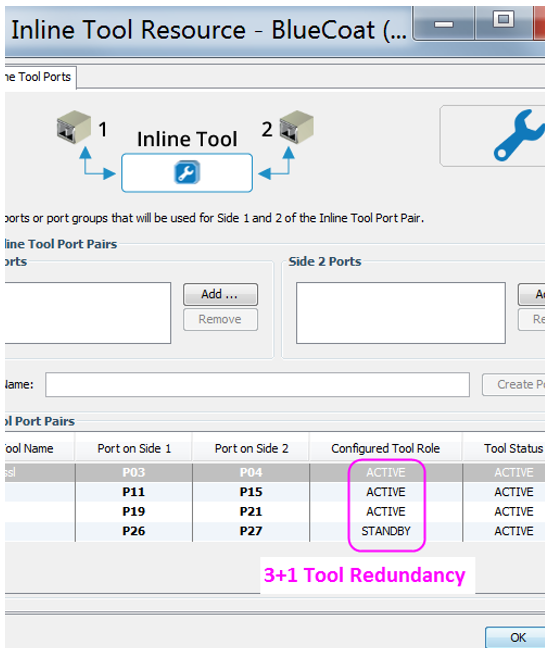
Fast Failure Detection - Heartbeats
Failure Detection
• Heartbeats between bypass switch and NPB
• Heartbeats between NPB and device
• Lack of heartbeats indicates failure
Key features
• Preset heartbeats for testing different devices
• Customizable heartbeats for difficult situations
• Support for single-stage (blue) or multistage (red) heartbeats


As a result, we have a scalable, high-performance device with a wide a set of functions and working on line-rate.

For questions about IXIA solutions, contact: dcs@muk.ua.
IXIA solutions distribution in Ukraine , Belarus , CIS countries .
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service

In this solution, Ixia has concentrated the most advanced features of transparency and traffic control, including the capabilities of the Ixia ATI (Application and Threat Intelligence) processor. Among them are SSL traffic decryption and in-depth packet analysis (DPI), which goes far beyond just checking for regular expression matching and provides accurate identification of application traffic. Vision ONE also performs various functions of packet processing (for example, deduplication, trimming, timestamps ...) and load balancing on the inline IB devices that are turned on (firewalls, IPS, etc.). This device can work with both inline and out-of-band devices at the same time.

The solution is quickly deployed and quickly included in the workflow thanks to an intuitive graphical user interface. This allows the company's IT staff to focus on improving security without wasting time on configuration.

A bit more about the Vision ONE

Advanced Packet Processing (AFM) features:
Deduplication - only one copy of the packet is sent to the analyzer

Where do duplicate packets come from?
Multiple tapes aggregate into the same analyzer.
One SPAN port usually generates repeated packets.
Removing headers- Detects and removes tunneling protocols from the header, for analysis by tools that do not support these protocols.


Examples of use:
• Translation: Deletes protocol headers that the analyzer does not understand and gives the packet in a supported format.
- MPLS, VNTag, FabricPath, etc.
• vTap Termination: Terminates traffic from Phantom vTap
• ERSPAN termination: Terminates traffic from remote offices / branches
Packet Trimming - truncates packets to a certain size and optionally inserts a “trailer” to get the original packet size before sending it to the analyzer.

Examples of use
• Analyzer efficiency: Reducing the size of the packet to send to the analyzer.
- Remove SSL-encrypted payloads before analysis
- Remove payloads for analyzers that study only headers
• Security: If the payload package is not needed for analysis, this function can be used to protect against the disclosure of confidential information, such as personal information (Personally Identifiable Information - PII) as required by many mandates such as PCI.
Masking data x - Allows you to hide certain data, while maintaining the overall frame size, so that personal information (Personally Identifiable Information - PII) is not transmitted to the analyzer.

Examples of using
• Protection of PII: Enterprises often have recommendations / obligations that oblige them not to store, transfer or otherwise disclose PII to internal or external users. Examples of such mandates are PCI (Payment Card Industry) or HIPAA in the US healthcare industry. Violations often lead to multi-million fines.
Timestamps (Packet Timestamping) - Adds a section containing a timestamp to each packet for a detailed study of the delay by analyzers.
Vision ONE uses PTP or NTP to obtain a reference time.

Examples of use
• Delay: The analyzer can determine the delay between any tapes in the network by comparing timestamps in the same packet from different places in the network.
Burst Protection- Adds an additional buffer to 1G interfaces to provide protection against events such as microburst and avoids data loss.

Examples of use
• Aggregation: When traffic is aggregated from different parts of the network into one 1G analyzer, a short-term excess of 1Gbps traffic is possible.
• Speed translation: When filtering 1G of data from a 10G link / interface, this functionality can protect the analyzer with 1G performance from short-term “burst”.
Ixia ATI (Application and Threat Intelligence) - accurate intelligent processing of application traffic based on in-depth packet analysis (DPI) and decryption of SSL traffic.
(applications and their activity, geolocation, device OS, browser, etc.)

Filtering applications


RegEx search and data masking

Flexible


ATIP traffic processing - understanding SSL
• Passive decryption - does not affect application performance
• Easy setup - only import certificates / keys
• All popular ciphers:
3DES, RC4, AES, SHA1 / 521/384/256/224 , MD5.
• SSL / TLS decryption support:
- SSL / TLS versions: SSL3.0, TLS1.0, TLS1.1 and TLS1.2.
- Exchange of asymmetric keys: RSA and ECDH.
- Symmetric keys: AES, 3DES and RC4.
- Hash algorithms: SHA and MD5.
- The maximum number of concurrent sessions: more than 1,000,000.
- Private key storage: in encrypted form with the attribute write only.
• Report encryption details - Netflow

Work with inline devices
• Supports parallel (for load balancing) and serial connection of inline devices, as well as any combination of these types of connections.
• To identify failed inline-devices in order to automatically overcome failures, single-stage and multi-stage transmission of heartbeat packets are used.
• Two modes of overcoming a failure:
- Redistribution of sessions from a failed inline-device to all active inline-devices.
- Switching all active sessions from a failed inline device to a backup inline device.


Fast Failure Detection - Heartbeats
Failure Detection
• Heartbeats between bypass switch and NPB
• Heartbeats between NPB and device
• Lack of heartbeats indicates failure
Key features
• Preset heartbeats for testing different devices
• Customizable heartbeats for difficult situations
• Support for single-stage (blue) or multistage (red) heartbeats


As a result, we have a scalable, high-performance device with a wide a set of functions and working on line-rate.

For questions about IXIA solutions, contact: dcs@muk.ua.
IXIA solutions distribution in Ukraine , Belarus , CIS countries .
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
