Telegram on MacOS [presumably] also locally stores correspondence in an accessible form

Illustration bleepingcomputer.com
Never had such a thing, and here it is again ...
Researcher from the United States Nathaniel Sachi discovered that Telegram does not protect the user's copy of the user's correspondence with encryption:
Telegram stores your messages in an unencrypted SQLite database. At least I did not have to make an effort to find the key this time. Although [posts] are quite difficult to view (probably, you need to write some kind of auxiliary script in python?) - this is very similar to the problem with Signal
UPD Information is presented in the form in which it was in the original source and twitter of the researcher.
UPD 2 Received an exposing comment from Pavel Durov
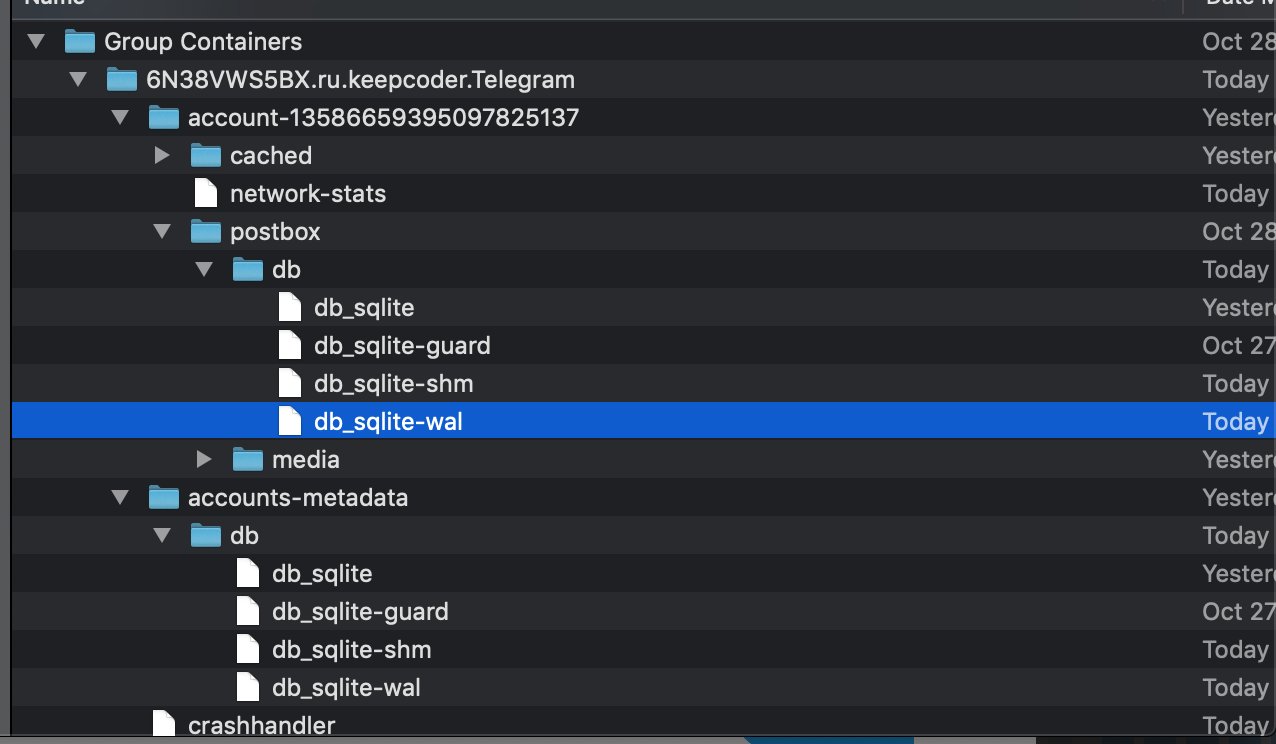
Nathaniel Sachi also checked the “secret chat” function in the Telegram for macOS application ( there is no secret chat in the Windows version, thanks to mwizard , however, Telegram Desktop is mentioned in the original source ). It turned out that messages from the secret chat are in the clear form in the same database as regular messages. Those. although data transfer for secret chats is reasonably well protected, a local copy of messages from such chats is stored locally without any protection from the application itself.
Telegram supports setting a local pincode to prevent unauthorized access to a running application, but this feature does not imply any additional protection for the local SQLite database with message history (as the researcher says).
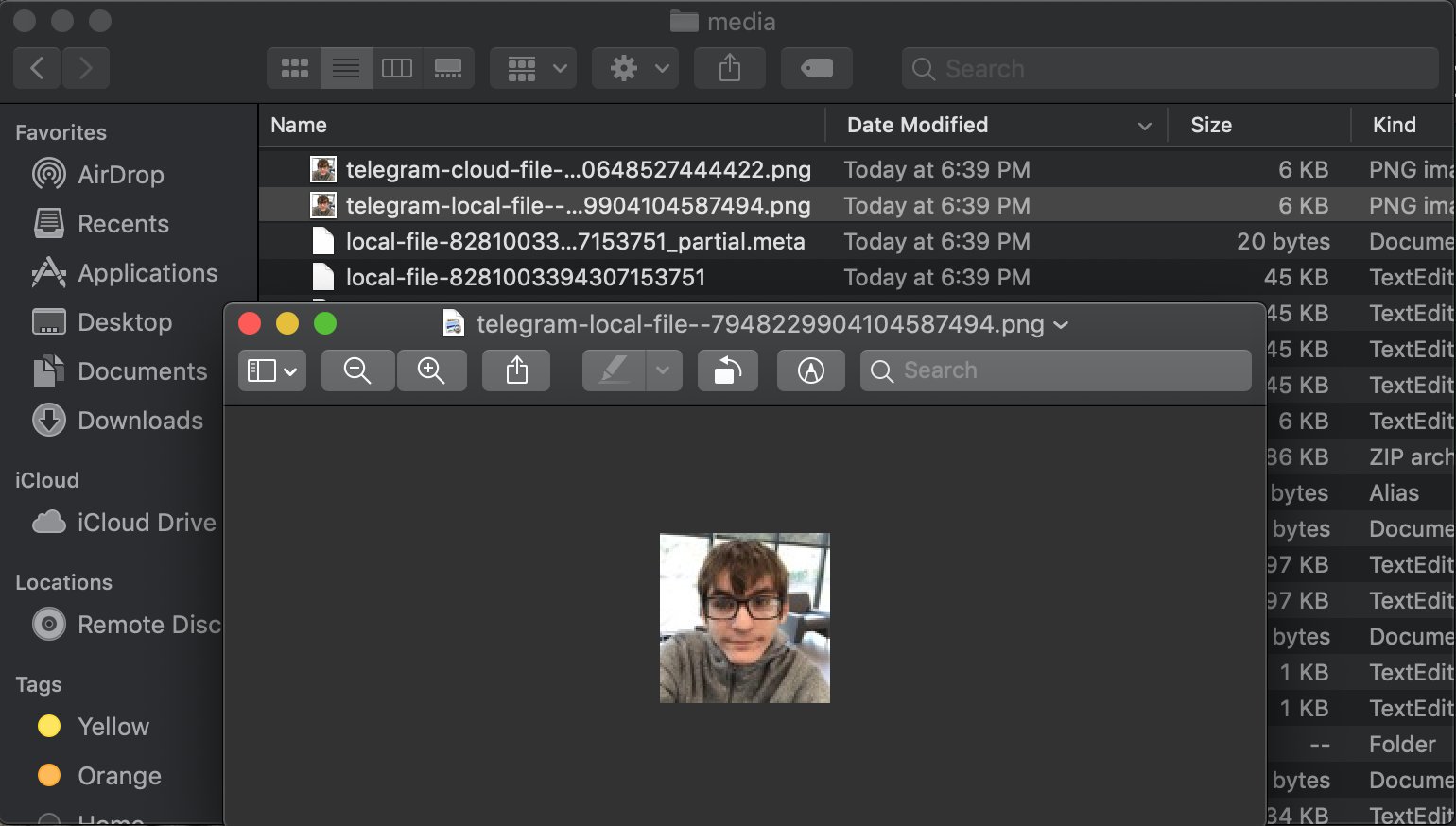
Sent media files in correspondence are also not particularly hidden, but only obfustsiruyutsya. Nathaniel Sachi only needed to change the file extension to view the photos from his chat.
Let me remind you that a few days ago, a hacker, Matthew Syush, revealed a similar problem with the lack of protection of the local message history database in the Signal application.
Updated!
Pavel Durov does not deny the situation, but believes that the problem is not a problem at all: