Protection at all stages of cyberattacks
HPE solutions allow you to build an integrated defense system against cyber attacks, including those carried out using fundamentally new methods of penetrating corporate systems.

Cyberattacks are becoming more widespread and sophisticated. One of the key reasons for the massive scale of cyberattacks is their affordability. For example, in a report published in October 2015 on the 2015 Cost of Cyber Crime Study: Global study conducted by Ponemon Institute with sponsorship from HPE, the average cost of a cyber crime in Russia is estimated at only 100-150 rubles, in dollars in terms of calculation, it decreased from $ 3.33 in 2014 to $ 2.37 in 2015.
One of the main problems of the insufficient effectiveness of protection against cyber attacks is often that in most cases the protection against attacks is fragmented, and not all risks are adequately taken into account. Experience shows that approximately 80% of the budgets allocated for the purchase of information security funds are spent on the acquisition and implementation of prevention tools to protect against penetration into the network. To do this, firewalls, IPS systems, various gateway solutions are installed. After penetration, the remaining 20% of the money spent on information security tools is necessary to protect against the actions of attackers. The key objective of the IS service is to provide a holistic, integrated uniform defense against attack at all its stages, avoiding failures in defense.
Hewlett Packard Enterprise offers internationally proven solutions to build such multi-level protection against cyberattacks and very effectively minimize the damage they cause. In addition to extremely effective products, HPE also has methodologies for protecting against hacker attacks. Creating on their basis a comprehensive protection of user information systems is a key task of HPE partners.
The HPE solution portfolio is built around the stages of an attack by an attacker. The first stage is the collection of information about the victim: which IP addresses are used in the organization, which services are hosted, which means of protection are used, etc. The second stage of the attack is penetration, which can be carried out using only technological means, and using methods social engineering, for example, making phone calls to users or sending them phishing messages. The third stage of the attack: an attacker entered the organization’s network and is looking for data (for example, accounting or client databases) that he could use to his advantage; for this, he is trying to penetrate individual protected network segments. Fourth stage: an attacker entered a protected segment, installed malware on computers or network devices and is trying to get at its disposal the data it needs (by the way, if they are encrypted - and HPE has the appropriate tools for this - it is far from easy to get them). The last, fifth stage - sending data to remote computers controlled by a hacker for the purpose of their further use (for example, selling to competitors or making it public in order to undermine the victim's reputation).
HPE has a Security Research unit that analyzes threats and trends in information security. Every year, HPE Security Research issues information security reports, which lists the most relevant and key trends in four areas:
For each of these areas, the portfolio of Hewlett Packard Enterprise Security, a division developing information security solutions, has its own products that solve the corresponding groups of problems. In total, the HPE portfolio includes about four dozen information security products.
The HPE ArcSight family of solutions contains technologies that perform the following tasks:
The ArcSight family includes over a dozen different products. It has been used in Russia since 2007. ArcSight users are about half of the top 100 Russian banks, almost all major telecommunications companies, and about 15 of the top two dozen leading event monitoring and incident management centers (Security Operation Center, SOC). ArcSight is also used in many Russian situational centers.
In our country, there are more than 200 certified ArcSight specialists (uncertified, probably ten times more). In addition, there is a certified training center and an ecosystem of HPE partners implementing ArcSight. For example, Solar Security uses the ArcSight family of products to provide information security services to its customers.
Another important reason for the popularity of this family of information technology technologies is that, working with ArcSight, IT and information security specialists will be able to significantly improve their professional level, as the ArcSight family of products incorporates the experience of a huge number of customer organizations and their expert experience.
In addition to ArcSight, Hewlett Packard Enterprise Security offers the market a powerful family of solutions for comprehensive protection of applications at the stage of developing source codes, their static analysis, as well as for dynamic analysis of the integrity of protection systems of already compiled applications (HPE Fortify), as well as a set of intrusion prevention tools (Intrusion Prevention System, IPS) and network threat protection - HPE TippingPoint, as well as various encryption tools.
In this article, we will focus on three products from the ArcSight family - Enterprise Security Manager (ESM), DNS Malware Analytics (DMA) and User Behavior Analytics (UBA).
The functionality of the HPE ArcSight ESM goes far beyond traditional security information and event management (SIEM) systems, and, as experience in using this product in Russia shows, it can be used to solve many different practical problems. For example, it can be used to monitor financial transactions in banking systems, business scenarios in ERP systems, integrate it into a single enterprise management console, etc. Often, ArcSight ESM is used in risk management tasks, including ensuring compliance with regulatory requirements .
However, ESM is most often used in systems aimed at identifying and repelling hacker attacks, as well as at preventing consequences from them. Many cases of failures are known due to such malicious actions. Many of them could be prevented or suppressed before causing noticeable damage by, firstly, checking the installed software for malicious codes and / or vulnerabilities and, secondly, by continuously monitoring the behavior of software products in information systems. It is no secret that a considerable period of time can pass from the penetration of a hacker into the system before the onset of serious malicious actions. So, according to the Ponemon Institute (see Fig. 3), from penetration to the suppression of malicious code, an average of about a month and a half passes, from the beginning of the activity of malicious insiders to its suppression - about two months. During this time, it is possible to track with the help of ESM the deviation in the behavior of the programs and notify the system administrator.
ESM provides not only the collection of information security events, but also many other types of processing, including the analysis of correlations of these events. ESM can also be considered as a platform for automating security tasks, not only informational, but also physical: ESM can be used to monitor IT events that are not directly related to information security and to collect information about traditional threats and tools that oppose them . Nothing prevents, for example, monitoring, KPI information security settings - the corresponding logic can be incorporated into the product. When collecting information from anti-virus systems, it does not matter how many types are deployed in an enterprise. Nothing prevents you from monitoring the situation in a heterogeneous environment of antivirus products,
In addition, ESM can be used to protect against fraud by analyzing information from business applications, for example, ERP-systems. If the detection logic can be formalized, then in this case it will probably be possible to lay it in the ESM.
To store and process very large amounts of data in ESM, the HPE Vertica DBMS platform can be used, significantly accelerating the execution of search queries formulated by security analysts. The integration of ArcSight and Vertica can be used not only to monitor information security events, but also, for example, to track events in business processes that store data in Vertica, in particular, to prevent fraudulent activities. For the integration of systems there is a special connector.
In September, at the annual HPE Protect conference, a new converged hardware-software solution was announced - HPE ArcSight DMA, designed to monitor network traffic and analyze the DNS domain name system requests encountered in it. It quickly and accurately detects servers infected with malicious code, network and user devices, including workstations and mobile gadgets, analyzing DNS traffic in order to detect real-time “bad” packets moving between servers, network equipment and devices connected to networks. This gives enterprises the ability to quickly defend themselves against new, previously unknown threats - this is important because they pose the greatest risk to business applications, systems and data. Using DMA, users can identify threats,
At the heart of DMA - an idea that, at first glance, seems to lie on the surface - was expressed by one of the HP Labs security experts: DNS is used in almost all attacks on computer networks (in particular, to ensure connectivity, transfer commands or tunneling data transmitted by attackers), and if you teach a computer system to recognize DNS queries, it will be able to identify those that may be related to hacker attacks.
An experimental model of such a system was created at HP Labs and deployed at HP SOC, a California-based information security incident management center that collects and analyzes information about information security events from the devices of 365,000 HP and HPE employees. Over the course of more than a year of running-in, the system was trained and, after reaching the required level of maturity, was launched into the market as an independent product - DMA. Templates and analysis bases come from HPE.
The customer of the product receives a web interface at its disposal, which displays a visualized picture of network activity and particularly identifies components with suspicious activity. In fact, it implements the concept of a “red button”, which makes it possible to detect hacker attacks without making almost any effort on the part of the user - they are required to repel and suppress attacks, but not to track their start.
A very important property is the scalability of the product. About 20 billion DNS queries are processed daily at HPE SOC - this is traffic comparable to the traffic of large telecommunication companies, which indicates unusually high scalability.
When working with traditional SIEM systems, information security experts usually act as follows: they take the signs of a known incident, lay them in the form of logic of correlation rules, and then follow these rules to monitor data flows. If signs of an incident are detected, then an alert or notification of the duty administrator is triggered, after which the incident processing begins - manually or automatically. This approach (from particular to general) is not always possible to apply, especially in cases where signs of malicious activity cannot be identified in advance.
The approach laid down in HPE ArcSight UBA implies a movement in the opposite direction: user accounts are built on the accounts and audit events that contain patterns of their typical behavior, and then, during the monitoring of events, atypical user behavior is revealed when they work with applications and data.
The UBA product released in April 2015 allows you to analyze any events related to user activity: access to databases, file directories, work with removable media, operations in corporate information systems (billing, payments, document management, work with personal data), etc. In addition to Moreover, UBA based on ready-made mathematical models for profiling activity on the basis of the received events allows grouping of the same type of events (peer group analysis), revealing anomalies (anomaly detection), determining profiles of user experience (baseline profiling), to determine the frequency of occurrence of the event (event rarity). Applying the results of mathematical models to information security tasks, UBA allows identifying insiders, exercising control over privileged users,
Importantly, UBA allows you to complement security events with information about the user, his work environment, job responsibilities, and other attributes. Even if the event contains only an IP address, using UBA, you can determine the real username associated with this event. Thus, by means of UBA it is possible to create a “universal” user card in which all its current attributes (dates of hiring and dismissal, position, division, region, etc.) and accounts in corporate systems will be automatically supported.
Based on this information, various IS incidents can be detected, for example, to detect the activity of one of their users, significantly different from the activity of its colleagues. For example, a bank operator opens an average of 20 clients per day. However, one of the operators opened the documents of 200 clients. Such atypical user behavior is a good reason to think about what is happening. Why did this particular operator need 10 times more documents than others? Maybe his boss got him some atypical job? Or was this operator assigned the burden of a sick boss? Or, in preparation for the dismissal, did the operator begin to copy information about the bank's customers onto his carriers (or take photographs on his phone)? The final conclusion can be made by conducting an internal investigation.
Another example: the amount of transactions conducted on one of the products of a bank or telecom operator exceeds the normally observed values for the calculated time periods (hour of the day, day of the week, day of the month, month, weekend, etc.) - this is an occasion to think whether this activity is hidden hacker or insider scammer.
In both cases, it’s important that UBA uses atypical user behavior, or you can identify and then examine what it is.
Of course, monitoring tools with which it was possible to track the behavior of users and programs and, evaluating the dynamics, to identify the atypical behavior of some of them, could have been done before. The advantage of UBA is that with this tool it has become much easier. For example, trying to implement the functions of analyzing user behavior in traditional SIEM tools, I had to study many regulations and job descriptions, but they often did not give a complete or reliable picture of user behavior, because, firstly, not everywhere employees strictly adhere to job descriptions, and - secondly, the regulations, as a rule, are not too deeply detailed, and the arrangement of priorities and emphasis in the regulations is usually not possible to see (in particular, it is impossible to determine what should the main activity of the employee in the organization look like from the point of view of the information systems with which he works). Using UBA, you can build user behavior profiles by classifying them by position and job group, include any events related to user behavior that are reflected in the company's information systems in the list of monitored parameters, and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. Using UBA, you can build user behavior profiles by classifying them by position and job group, include any events related to user behavior that are reflected in the company's information systems in the list of monitored parameters, and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. Using UBA, you can build user behavior profiles by classifying them by position and job group, include any events related to user behavior that are reflected in the company's information systems in the list of monitored parameters, and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts.
However, as a rule, the biggest losses are associated with the actions of insider attackers, and the higher the position of the insider, the more damage he can inflict through his actions. Now HPE, together with developers of leading ERP, CRM, SCM systems, is developing insider protection systems, reducing the risks of abuse of their official position, corruption, fraud, economic espionage, etc. In addition, HPE willingly shares with its partners the experience of building insider protection systems in organizations of various industries and sectors.
HPE ArcSight ESM, DMA UBA products can significantly minimize the risks that companies, their partners and customers could suffer, significantly increasing the security of enterprise systems and data. Most importantly, they help prevent damage from previously unknown threats and risks by identifying suspicious activities in a timely manner and helping to find gaps in IT systems. All of these products have emerged in response to recent challenges in the field of information security, helping HPE customers ensure a calm, safe operation of their business.
Types of attacks detected in 252 companies:
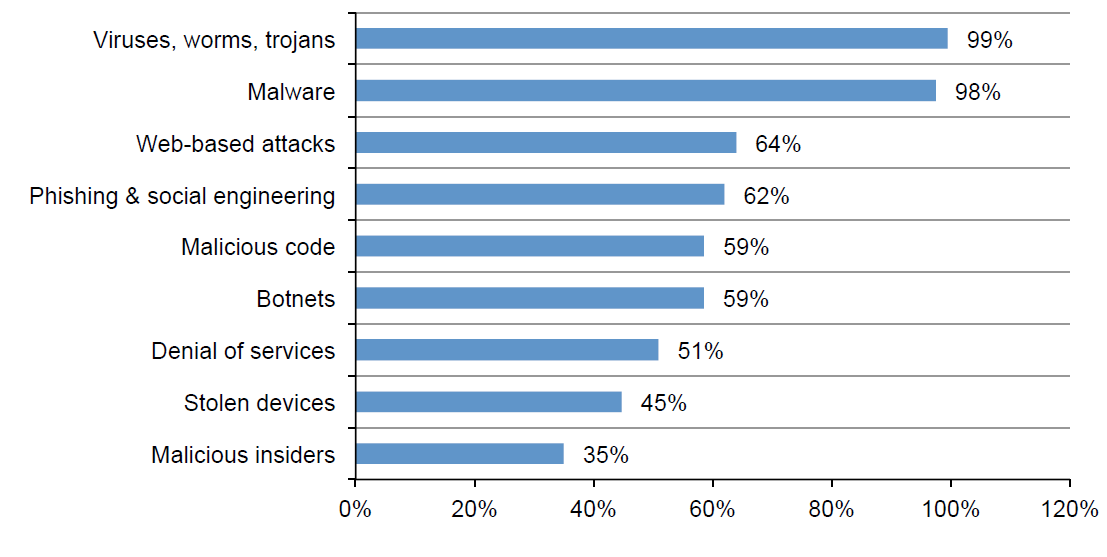
Source: Ponemon Institute, “2015 Cost of Cyber Crime Study: Global”, October 2015
Average cost of damage caused during a year as a result of exposure to cyber attacks:
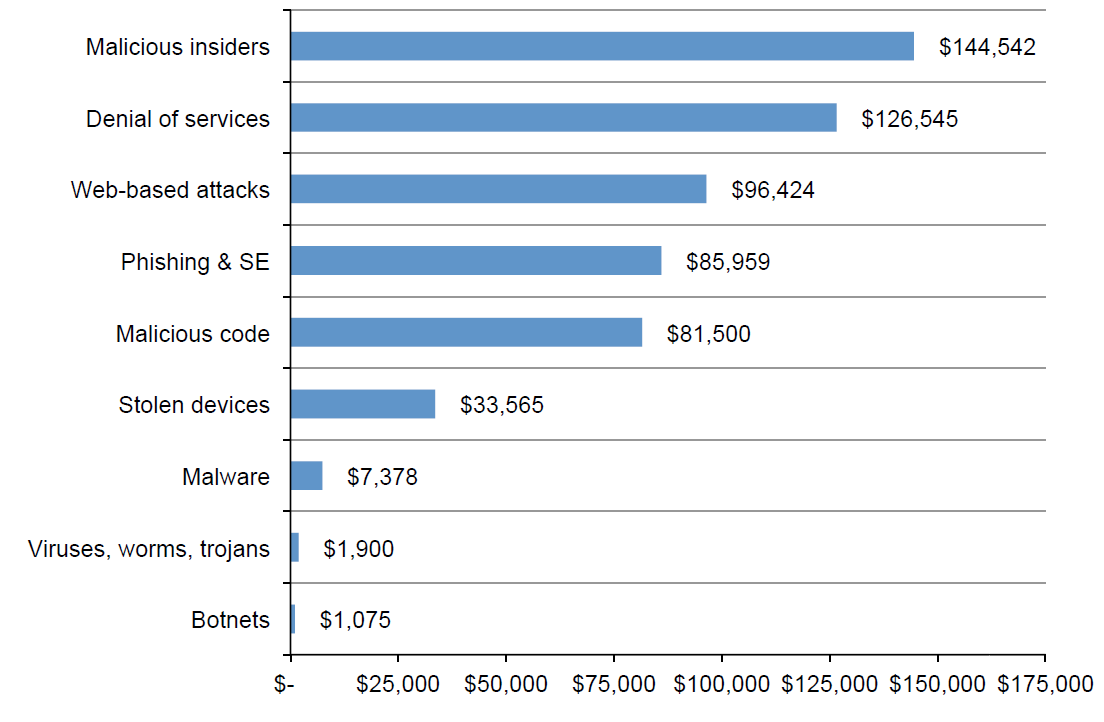
Source: Ponemon Institute, “2015 Cost of Cyber Crime Study: Global,” October 2015
Average duration of attacks before they are suppressed (in days):

Source: Ponemon Institute, “2015 Cost of Cyber Crime Study: Global,” October 2015

Cyberattacks are becoming more widespread and sophisticated. One of the key reasons for the massive scale of cyberattacks is their affordability. For example, in a report published in October 2015 on the 2015 Cost of Cyber Crime Study: Global study conducted by Ponemon Institute with sponsorship from HPE, the average cost of a cyber crime in Russia is estimated at only 100-150 rubles, in dollars in terms of calculation, it decreased from $ 3.33 in 2014 to $ 2.37 in 2015.
One of the main problems of the insufficient effectiveness of protection against cyber attacks is often that in most cases the protection against attacks is fragmented, and not all risks are adequately taken into account. Experience shows that approximately 80% of the budgets allocated for the purchase of information security funds are spent on the acquisition and implementation of prevention tools to protect against penetration into the network. To do this, firewalls, IPS systems, various gateway solutions are installed. After penetration, the remaining 20% of the money spent on information security tools is necessary to protect against the actions of attackers. The key objective of the IS service is to provide a holistic, integrated uniform defense against attack at all its stages, avoiding failures in defense.
Hewlett Packard Enterprise offers internationally proven solutions to build such multi-level protection against cyberattacks and very effectively minimize the damage they cause. In addition to extremely effective products, HPE also has methodologies for protecting against hacker attacks. Creating on their basis a comprehensive protection of user information systems is a key task of HPE partners.
The HPE solution portfolio is built around the stages of an attack by an attacker. The first stage is the collection of information about the victim: which IP addresses are used in the organization, which services are hosted, which means of protection are used, etc. The second stage of the attack is penetration, which can be carried out using only technological means, and using methods social engineering, for example, making phone calls to users or sending them phishing messages. The third stage of the attack: an attacker entered the organization’s network and is looking for data (for example, accounting or client databases) that he could use to his advantage; for this, he is trying to penetrate individual protected network segments. Fourth stage: an attacker entered a protected segment, installed malware on computers or network devices and is trying to get at its disposal the data it needs (by the way, if they are encrypted - and HPE has the appropriate tools for this - it is far from easy to get them). The last, fifth stage - sending data to remote computers controlled by a hacker for the purpose of their further use (for example, selling to competitors or making it public in order to undermine the victim's reputation).
HPE has a Security Research unit that analyzes threats and trends in information security. Every year, HPE Security Research issues information security reports, which lists the most relevant and key trends in four areas:
- incident monitoring and response (including user behavioral analysis);
- analysis of software source codes;
- network security;
- encryption.
For each of these areas, the portfolio of Hewlett Packard Enterprise Security, a division developing information security solutions, has its own products that solve the corresponding groups of problems. In total, the HPE portfolio includes about four dozen information security products.
The HPE ArcSight family of solutions contains technologies that perform the following tasks:
- collection, consolidation and correlation of events about emerging information security incidents - HPE ArcSight Enterprise Security Manager / Express / Logger;
- integration with more than 350 event sources, as well as a convenient SDK for connecting any other systems - HPE ArcSight Smart / FlexConnectors;
- investigation and timely detection of threats using a large number of standard correlation rules and Compliance Insight Packages;
- behavioral analysis of any types of events - HPE ArcSight ThreatDetector; analysis of user behavior - HPE ArcSight User Behavior Analytics to monitor the activity of internal intruders;
- HPE ArcSight Reputation Security Monitor subscription to alerts about current information security threats to prevent intrusions into corporate networks and the detection of sensitive data leaks;
- centralized management of deployed HPE ArcSight infrastructure - HPE ArcSight Management Center;
- Fighting human and time resources during incident investigations - HPE ArcSight Risk Insight.
The ArcSight family includes over a dozen different products. It has been used in Russia since 2007. ArcSight users are about half of the top 100 Russian banks, almost all major telecommunications companies, and about 15 of the top two dozen leading event monitoring and incident management centers (Security Operation Center, SOC). ArcSight is also used in many Russian situational centers.
In our country, there are more than 200 certified ArcSight specialists (uncertified, probably ten times more). In addition, there is a certified training center and an ecosystem of HPE partners implementing ArcSight. For example, Solar Security uses the ArcSight family of products to provide information security services to its customers.
Another important reason for the popularity of this family of information technology technologies is that, working with ArcSight, IT and information security specialists will be able to significantly improve their professional level, as the ArcSight family of products incorporates the experience of a huge number of customer organizations and their expert experience.
In addition to ArcSight, Hewlett Packard Enterprise Security offers the market a powerful family of solutions for comprehensive protection of applications at the stage of developing source codes, their static analysis, as well as for dynamic analysis of the integrity of protection systems of already compiled applications (HPE Fortify), as well as a set of intrusion prevention tools (Intrusion Prevention System, IPS) and network threat protection - HPE TippingPoint, as well as various encryption tools.
In this article, we will focus on three products from the ArcSight family - Enterprise Security Manager (ESM), DNS Malware Analytics (DMA) and User Behavior Analytics (UBA).
HPE ArcSight Enterprise Security Manager
The functionality of the HPE ArcSight ESM goes far beyond traditional security information and event management (SIEM) systems, and, as experience in using this product in Russia shows, it can be used to solve many different practical problems. For example, it can be used to monitor financial transactions in banking systems, business scenarios in ERP systems, integrate it into a single enterprise management console, etc. Often, ArcSight ESM is used in risk management tasks, including ensuring compliance with regulatory requirements .
However, ESM is most often used in systems aimed at identifying and repelling hacker attacks, as well as at preventing consequences from them. Many cases of failures are known due to such malicious actions. Many of them could be prevented or suppressed before causing noticeable damage by, firstly, checking the installed software for malicious codes and / or vulnerabilities and, secondly, by continuously monitoring the behavior of software products in information systems. It is no secret that a considerable period of time can pass from the penetration of a hacker into the system before the onset of serious malicious actions. So, according to the Ponemon Institute (see Fig. 3), from penetration to the suppression of malicious code, an average of about a month and a half passes, from the beginning of the activity of malicious insiders to its suppression - about two months. During this time, it is possible to track with the help of ESM the deviation in the behavior of the programs and notify the system administrator.
ESM provides not only the collection of information security events, but also many other types of processing, including the analysis of correlations of these events. ESM can also be considered as a platform for automating security tasks, not only informational, but also physical: ESM can be used to monitor IT events that are not directly related to information security and to collect information about traditional threats and tools that oppose them . Nothing prevents, for example, monitoring, KPI information security settings - the corresponding logic can be incorporated into the product. When collecting information from anti-virus systems, it does not matter how many types are deployed in an enterprise. Nothing prevents you from monitoring the situation in a heterogeneous environment of antivirus products,
In addition, ESM can be used to protect against fraud by analyzing information from business applications, for example, ERP-systems. If the detection logic can be formalized, then in this case it will probably be possible to lay it in the ESM.
To store and process very large amounts of data in ESM, the HPE Vertica DBMS platform can be used, significantly accelerating the execution of search queries formulated by security analysts. The integration of ArcSight and Vertica can be used not only to monitor information security events, but also, for example, to track events in business processes that store data in Vertica, in particular, to prevent fraudulent activities. For the integration of systems there is a special connector.
HPE ArcSight DNS Malware Analytics
In September, at the annual HPE Protect conference, a new converged hardware-software solution was announced - HPE ArcSight DMA, designed to monitor network traffic and analyze the DNS domain name system requests encountered in it. It quickly and accurately detects servers infected with malicious code, network and user devices, including workstations and mobile gadgets, analyzing DNS traffic in order to detect real-time “bad” packets moving between servers, network equipment and devices connected to networks. This gives enterprises the ability to quickly defend themselves against new, previously unknown threats - this is important because they pose the greatest risk to business applications, systems and data. Using DMA, users can identify threats,
At the heart of DMA - an idea that, at first glance, seems to lie on the surface - was expressed by one of the HP Labs security experts: DNS is used in almost all attacks on computer networks (in particular, to ensure connectivity, transfer commands or tunneling data transmitted by attackers), and if you teach a computer system to recognize DNS queries, it will be able to identify those that may be related to hacker attacks.
An experimental model of such a system was created at HP Labs and deployed at HP SOC, a California-based information security incident management center that collects and analyzes information about information security events from the devices of 365,000 HP and HPE employees. Over the course of more than a year of running-in, the system was trained and, after reaching the required level of maturity, was launched into the market as an independent product - DMA. Templates and analysis bases come from HPE.
The customer of the product receives a web interface at its disposal, which displays a visualized picture of network activity and particularly identifies components with suspicious activity. In fact, it implements the concept of a “red button”, which makes it possible to detect hacker attacks without making almost any effort on the part of the user - they are required to repel and suppress attacks, but not to track their start.
A very important property is the scalability of the product. About 20 billion DNS queries are processed daily at HPE SOC - this is traffic comparable to the traffic of large telecommunication companies, which indicates unusually high scalability.
HPE ArcSight User Behavior Analytics
When working with traditional SIEM systems, information security experts usually act as follows: they take the signs of a known incident, lay them in the form of logic of correlation rules, and then follow these rules to monitor data flows. If signs of an incident are detected, then an alert or notification of the duty administrator is triggered, after which the incident processing begins - manually or automatically. This approach (from particular to general) is not always possible to apply, especially in cases where signs of malicious activity cannot be identified in advance.
The approach laid down in HPE ArcSight UBA implies a movement in the opposite direction: user accounts are built on the accounts and audit events that contain patterns of their typical behavior, and then, during the monitoring of events, atypical user behavior is revealed when they work with applications and data.
The UBA product released in April 2015 allows you to analyze any events related to user activity: access to databases, file directories, work with removable media, operations in corporate information systems (billing, payments, document management, work with personal data), etc. In addition to Moreover, UBA based on ready-made mathematical models for profiling activity on the basis of the received events allows grouping of the same type of events (peer group analysis), revealing anomalies (anomaly detection), determining profiles of user experience (baseline profiling), to determine the frequency of occurrence of the event (event rarity). Applying the results of mathematical models to information security tasks, UBA allows identifying insiders, exercising control over privileged users,
Importantly, UBA allows you to complement security events with information about the user, his work environment, job responsibilities, and other attributes. Even if the event contains only an IP address, using UBA, you can determine the real username associated with this event. Thus, by means of UBA it is possible to create a “universal” user card in which all its current attributes (dates of hiring and dismissal, position, division, region, etc.) and accounts in corporate systems will be automatically supported.
Based on this information, various IS incidents can be detected, for example, to detect the activity of one of their users, significantly different from the activity of its colleagues. For example, a bank operator opens an average of 20 clients per day. However, one of the operators opened the documents of 200 clients. Such atypical user behavior is a good reason to think about what is happening. Why did this particular operator need 10 times more documents than others? Maybe his boss got him some atypical job? Or was this operator assigned the burden of a sick boss? Or, in preparation for the dismissal, did the operator begin to copy information about the bank's customers onto his carriers (or take photographs on his phone)? The final conclusion can be made by conducting an internal investigation.
Another example: the amount of transactions conducted on one of the products of a bank or telecom operator exceeds the normally observed values for the calculated time periods (hour of the day, day of the week, day of the month, month, weekend, etc.) - this is an occasion to think whether this activity is hidden hacker or insider scammer.
In both cases, it’s important that UBA uses atypical user behavior, or you can identify and then examine what it is.
Of course, monitoring tools with which it was possible to track the behavior of users and programs and, evaluating the dynamics, to identify the atypical behavior of some of them, could have been done before. The advantage of UBA is that with this tool it has become much easier. For example, trying to implement the functions of analyzing user behavior in traditional SIEM tools, I had to study many regulations and job descriptions, but they often did not give a complete or reliable picture of user behavior, because, firstly, not everywhere employees strictly adhere to job descriptions, and - secondly, the regulations, as a rule, are not too deeply detailed, and the arrangement of priorities and emphasis in the regulations is usually not possible to see (in particular, it is impossible to determine what should the main activity of the employee in the organization look like from the point of view of the information systems with which he works). Using UBA, you can build user behavior profiles by classifying them by position and job group, include any events related to user behavior that are reflected in the company's information systems in the list of monitored parameters, and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. Using UBA, you can build user behavior profiles by classifying them by position and job group, include any events related to user behavior that are reflected in the company's information systems in the list of monitored parameters, and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. Using UBA, you can build user behavior profiles by classifying them by position and job group, include any events related to user behavior that are reflected in the company's information systems in the list of monitored parameters, and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts. and then track deviations from typical behavior. What is important, in this way it is possible to control not only internal users, but also external ones - for example, to quickly hack hacking systems of remote banking services or to illegally connect telecommunication companies' clients to their accounts.
However, as a rule, the biggest losses are associated with the actions of insider attackers, and the higher the position of the insider, the more damage he can inflict through his actions. Now HPE, together with developers of leading ERP, CRM, SCM systems, is developing insider protection systems, reducing the risks of abuse of their official position, corruption, fraud, economic espionage, etc. In addition, HPE willingly shares with its partners the experience of building insider protection systems in organizations of various industries and sectors.
* * *
HPE ArcSight ESM, DMA UBA products can significantly minimize the risks that companies, their partners and customers could suffer, significantly increasing the security of enterprise systems and data. Most importantly, they help prevent damage from previously unknown threats and risks by identifying suspicious activities in a timely manner and helping to find gaps in IT systems. All of these products have emerged in response to recent challenges in the field of information security, helping HPE customers ensure a calm, safe operation of their business.
Types of attacks detected in 252 companies:

Source: Ponemon Institute, “2015 Cost of Cyber Crime Study: Global”, October 2015
Average cost of damage caused during a year as a result of exposure to cyber attacks:

Source: Ponemon Institute, “2015 Cost of Cyber Crime Study: Global,” October 2015
Average duration of attacks before they are suppressed (in days):

Source: Ponemon Institute, “2015 Cost of Cyber Crime Study: Global,” October 2015
