Security Week 41: Good News
 This is enough in the information security industry, it's drama. The latest means of hacking, grandiose failures in the protection systems of programs and hardware - or the complete absence of these same systems. The daily routine of spam with malicious appendages and phishing, cryptographers and stuff is not as interesting as the most complex cyber attacks, but they have to be dealt with the most.
This is enough in the information security industry, it's drama. The latest means of hacking, grandiose failures in the protection systems of programs and hardware - or the complete absence of these same systems. The daily routine of spam with malicious appendages and phishing, cryptographers and stuff is not as interesting as the most complex cyber attacks, but they have to be dealt with the most.Finding out that the password does not fit your router - it's about how to detect a broken lock in the front door. And yet, although cyber threats should be taken seriously, the real work on security begins at the moment when everyone stopped waving their hands and speaking unprintable words and started doing business. They updated the router, conducted a training on phishing with employees, installed protection from cryptographers. Even at the moment when everything is bad with information security, it makes sense to imagine how it should be good, and not rushing to move towards a beautiful future. Today is a digest of good news: Google fixed Android security, Cisco fixed Webex, Wordpress fixed Wordpress.
Let's start with the simple news : as reported by The Verge , Google has supplemented the contractual obligations of smartphone manufacturers based on the Android operating system with a separate item about security. Starting from January 31, 2019, all new phones, sold in more than one hundred thousand copies, should receive security patches regularly within two years after release. Accordingly, manufacturers of more or less popular phones will be required to prepare and distribute these patches.

The practice of delivering patches that close security issues was introduced in 2015 — first for Google’s own phones, and later other manufacturers pulled up. Three years ago, Google began to move away from the traditional scheme of preparing updates for smartphones, when priority was given to new features, and security holes were tackled “as lucky”. In the version of Android 8.0 Oreo was introduced Project Treble, designed to improve the situation with the fragmentation of the code base. If before that vendors were in no hurry to roll patches, fearing conflicts with their own code, now functionality and security have been completely (or something) separated. Closing vulnerabilities made easy.

Not everyone took advantage of these benefits. First, active devices based on the eighth (or higher) version of Android are still in the minority. Secondly, not all vendors regularly send out monthly security patches, as Security Research Labs found out in April. It is time for organizational measures. Of course, the ideal way to improve security is to develop technology so that it works more or less by itself. But this is not always the case, so now vendors will be required to support devices for at least two years. Another good news about Android: the fight against malicious applications on Google Play continues. Nearly three dozen applications with relatively useful functionality and an addition in the form of SMS interception have been removed from the official Google store .
More good news. Cisco fixed a dangerous bug in the Webex newsgroup system. Webex usually requires the installation of client software, which intercepts requests from the browser and ensures that the video stream, the contents of the desktop speaker and other things are transmitted to the user's computer. The client works constantly, even when you are not using a conference call, and it has already become clear more than oncethat he can add a couple of extra attack vectors to the system. Back in September, a vulnerability was discovered and closed in which the WebExService.exe process was used for privilege escalation (if you already had access to the system at the rank of a regular user). And last week, a researcher known as SkullSecurity found a similar bug. He studied how WebExService launches the client update process, and was able to redirect this functionality to launch any process with system privileges, and even with the theoretical possibility of remote operation. I recommend reading the original research , there is described in detail the process of
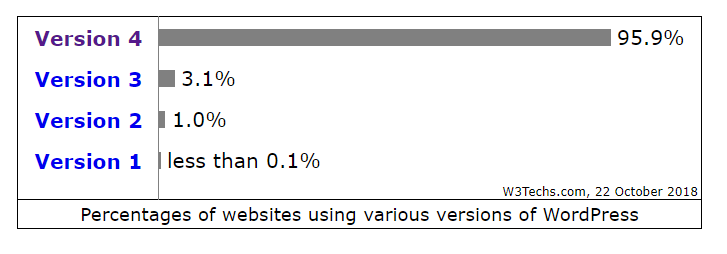
Finally, the good news about Wordpress: 96% of the sites on this engine use a modern version of the software. Just last week, we looked at Wordpress version statistics and came up with similar conclusions. Or did not come. 96% of Wordpress sites actually use version 4.x, but the most current version 4.9 is used by a little more than 70%, and this release, for a minute, is already a year. At the DerbyCon conference, Wordpress developers decided, apparently, to also focus on the positive and told how they achieved (in any case) a very good indicator. The automatic update system of the engine also helped (far from all implementations working normally - it depends on the admin user), and the security notifications in the Google Search Console, and the Tide rating .

Tide is an automated test suite that evaluates plug-in security. It is assumed that the Tide rating will eventually be displayed next to the plug-in user rating (as in the screenshot), which will motivate developers to code more reliably . So far, the rating has not been demonstrated, the system is in development, and, judging by the notes on the project website, release 1.0 is coming. Automated tests by definition can not find all the vulnerabilities, but their task is not in this. Quickly assessing the code for well-known security problems is a good start. Moreover, the real cases of hacking sites on Wordpress most often occur through vulnerable extensions. In addition, Wordpress will now alert users if their site uses a no longer supportedPHP version 5.6. Useful feature for customers of companies that provide "Wordpress out of the box." And topical: according to the site W3Techs, at the time of publication, the fifth version of PHP was used by more than 60% of sites.

All good!
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
