Security analysis of corporate wireless network
Today, wireless Wi-Fi networks are used almost everywhere: thanks to the ease of use of the network, high user mobility and low installation cost, this technology is increasingly becoming an indispensable part of not only home but also corporate networks. At the same time, like any data transfer technology, Wi-Fi with unsafe use carries certain threats. An attacker, using incorrect settings of the access point or the user's negligence, can intercept this user's personal data, carry out an attack on his device or penetrate the company's internal network.
As part of the study, an analysis of the security of the guest network of our company, USSC-Guest, was conducted. Testing was conducted on the model of an external intruder, that is, without having direct access to the selected network, so the main purpose of a possible attacker was to get a password to connect to it.It should be noted that knowledge of the password will allow the offender to intercept and decrypt data transmitted over the network, as well as provide the ability to create a fake access point with the same name and connection method.
The initial scan of the wireless broadcast showed that the WPA2 algorithm with WPS technology turned off is used to encrypt the transmitted data in the network under study. At the time of writing, WPA2 is the most secure algorithm for protecting wireless networks and does not contain vulnerabilities that allow an attacker to identify the password in a reasonable time. The attack called “KRACK”, which became known in 2017, does not have an open practical implementation. Two technical attack scenarios remain available to the attacker: intercepting packets related to client authentication (handshake, handshake) with further dictionary search through the dictionary, and creating a fake access point with a parallel denial of service attack on the real access point.
In order to intercept packets associated with client authentication in a wireless air, you must first switch the network adapter to the “monitor” state - a state in which the adapter receives all packets passing on its frequency in the visible range. After that, the attacker becomes available detailed information about the visible access points and active clients:

Figure 1. The result of scanning the wireless air
You can see that from the office in which the testing was conducted, two access points were found with the name "USSC-Guest". For the attack, an access point with a MAC address of 00: 3A: 99: 89: D2: 01 was chosen as the most frequently used in the available range:
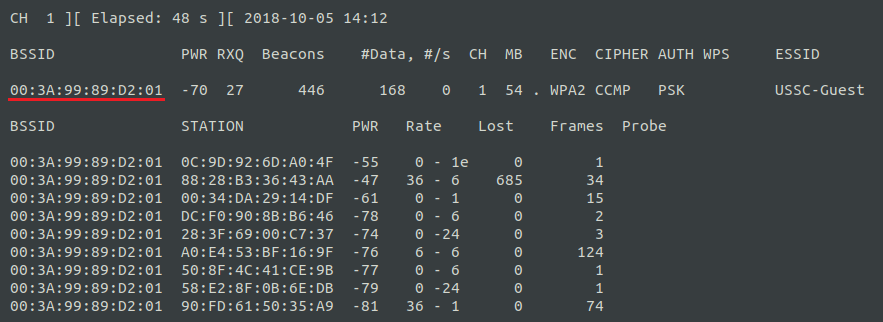
Figure 2. MAC addresses of users of the selected access point
Some time after the start of the network scan, a new client connection was fixed, thanks to which we managed to intercept the necessary authentication packets. This is evidenced by the line "WPA handshake: 00: 3A: 99: 89: D2: 01":

Figure 3. The result of intercepting authentication packets
Next, an attempt was made to find a password using the most popular dictionaries ("rockyou", "top-wpa-passwords" and a set of numerical passwords). As a result of the brute-force attack, the dictionary could not figure out the connection password. In this case, the attacker is likely to abandon the definition of a password by a full brute force, because this method will take him, at best, a few years.
The implementation of this scenario consisted of two stages:
For users, it looked as if the USSC-Guest guest network, to which they were already connected, disappeared from the list of available networks, and instead of it appeared exactly the same, but without authentication:
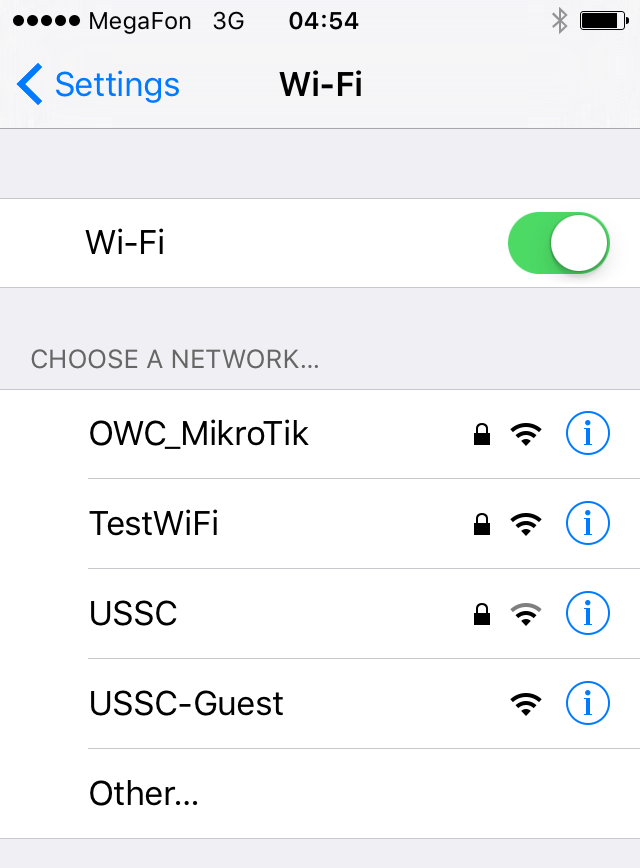
Figure 4. The result of the denial of service attack on the access point under investigation.
When connecting to a false access point, the user was still asked to enter the WPA2 password. So, for example, it looked for iOS users:

Figure 5. A suggestion to enter a password after connecting to a false access point
Due to the fact that the false access point was completely controlled by the attacker, all data sent over the wireless network could be intercepted and analyzed by it. So, for example, the password that had to be entered into the specified form was sent directly to the server of a possible intruder. It was assumed that the user, connecting to a false access point, will consider this a change in the method of connection and enter the necessary data.
Testing was conducted on a weekday, in the period from 12 to 15 hours. During this time, four different devices were connected to the false access point, but the required password was never entered. Further testing was discontinued due to the fact that the guest network under investigation might have been required to resolve work issues and should have functioned normally. The attacker, in turn, with such an attack could completely paralyze the work of a particular wireless network and after some time obtain the required password.
According to the results of scanning of one of the access points of the USSC-Guest guest network, no problems were detected in the security settings: a strong password WPA2-CCMP algorithm with a strong password is used to encrypt the transmitted data, WPS technology is disabled. Despite the fact that, if necessary, an attacker can stop the wireless network and create a false access point, to implement this attack, the intruder will have to be within the coverage area of the wireless network (for example, one floor below), which greatly reduces his search range and complicates the attack. .
In conclusion, we highlight the main recommendations for the use of wireless Wi-Fi networks:
Author: Dmitry Morozov, Assistant Analyst, Analytical Center, LLC “UTsSB”
As part of the study, an analysis of the security of the guest network of our company, USSC-Guest, was conducted. Testing was conducted on the model of an external intruder, that is, without having direct access to the selected network, so the main purpose of a possible attacker was to get a password to connect to it.It should be noted that knowledge of the password will allow the offender to intercept and decrypt data transmitted over the network, as well as provide the ability to create a fake access point with the same name and connection method.
The initial scan of the wireless broadcast showed that the WPA2 algorithm with WPS technology turned off is used to encrypt the transmitted data in the network under study. At the time of writing, WPA2 is the most secure algorithm for protecting wireless networks and does not contain vulnerabilities that allow an attacker to identify the password in a reasonable time. The attack called “KRACK”, which became known in 2017, does not have an open practical implementation. Two technical attack scenarios remain available to the attacker: intercepting packets related to client authentication (handshake, handshake) with further dictionary search through the dictionary, and creating a fake access point with a parallel denial of service attack on the real access point.
Dictionary brute force attack
In order to intercept packets associated with client authentication in a wireless air, you must first switch the network adapter to the “monitor” state - a state in which the adapter receives all packets passing on its frequency in the visible range. After that, the attacker becomes available detailed information about the visible access points and active clients:

Figure 1. The result of scanning the wireless air
You can see that from the office in which the testing was conducted, two access points were found with the name "USSC-Guest". For the attack, an access point with a MAC address of 00: 3A: 99: 89: D2: 01 was chosen as the most frequently used in the available range:

Figure 2. MAC addresses of users of the selected access point
Some time after the start of the network scan, a new client connection was fixed, thanks to which we managed to intercept the necessary authentication packets. This is evidenced by the line "WPA handshake: 00: 3A: 99: 89: D2: 01":

Figure 3. The result of intercepting authentication packets
Next, an attempt was made to find a password using the most popular dictionaries ("rockyou", "top-wpa-passwords" and a set of numerical passwords). As a result of the brute-force attack, the dictionary could not figure out the connection password. In this case, the attacker is likely to abandon the definition of a password by a full brute force, because this method will take him, at best, a few years.
Creating a fake access point
The implementation of this scenario consisted of two stages:
- creating a false access point with the same name as the attacking access point, but without having to enter a password to connect,
- conducting a denial of service attack on the access point under investigation.
For users, it looked as if the USSC-Guest guest network, to which they were already connected, disappeared from the list of available networks, and instead of it appeared exactly the same, but without authentication:

Figure 4. The result of the denial of service attack on the access point under investigation.
When connecting to a false access point, the user was still asked to enter the WPA2 password. So, for example, it looked for iOS users:

Figure 5. A suggestion to enter a password after connecting to a false access point
Due to the fact that the false access point was completely controlled by the attacker, all data sent over the wireless network could be intercepted and analyzed by it. So, for example, the password that had to be entered into the specified form was sent directly to the server of a possible intruder. It was assumed that the user, connecting to a false access point, will consider this a change in the method of connection and enter the necessary data.
Testing was conducted on a weekday, in the period from 12 to 15 hours. During this time, four different devices were connected to the false access point, but the required password was never entered. Further testing was discontinued due to the fact that the guest network under investigation might have been required to resolve work issues and should have functioned normally. The attacker, in turn, with such an attack could completely paralyze the work of a particular wireless network and after some time obtain the required password.
Conclusion
According to the results of scanning of one of the access points of the USSC-Guest guest network, no problems were detected in the security settings: a strong password WPA2-CCMP algorithm with a strong password is used to encrypt the transmitted data, WPS technology is disabled. Despite the fact that, if necessary, an attacker can stop the wireless network and create a false access point, to implement this attack, the intruder will have to be within the coverage area of the wireless network (for example, one floor below), which greatly reduces his search range and complicates the attack. .
In conclusion, we highlight the main recommendations for the use of wireless Wi-Fi networks:
- To ensure the security of data transmitted over the wireless network, use WPA2-CCMP encryption with a strong password (the password from the numbers alone is not strong),
- If possible, do not connect to open Wi-Fi networks, even if their name seems true to you: they can be monitored or even completely controlled by an intruder. If this is not possible, use a VPN,
- Closed Wi-Fi networks can also be controlled by an attacker. If you are not sure about the security of the connection, use VPN,
- When using wireless networks, always pay attention to the type of connection used by the browser: HTTP or HTTPS. The last connection type, HTTPS, is secure.
Author: Dmitry Morozov, Assistant Analyst, Analytical Center, LLC “UTsSB”
