What is the difference between Snort and Cisco FirePOWER?
Often I hear that there isn’t much point in acquiring Cisco FirePOWER, it’s the same Snort, only in the hardware shell. And after the recent release of Snort on the Cisco ISR 4000 series routers, this question came up again with renewed vigor. Therefore, I would like in this article to briefly go over the key differences between the Snort free redistribution systemand the Cisco family of solutions, united under the umbrella name FirePOWER (not to be confused with Firepower 9300, which is Cisco's new high-performance and modular security platform). This issue has become especially relevant recently, when a number of Russian developers began to use Snort as the basis for their own intrusion detection systems, after being certified by the FSTEC or the FSB.
Snort
Let's start with a brief background. Snort was created by Martin Reshem in 1998 and quickly gained popularity as a free intrusion detection system that allows you to write rules for attack detection on your own and without much effort. Essentially, the Snort signature description language has become the de facto standard for many intrusion detection systems that use it in their engines.
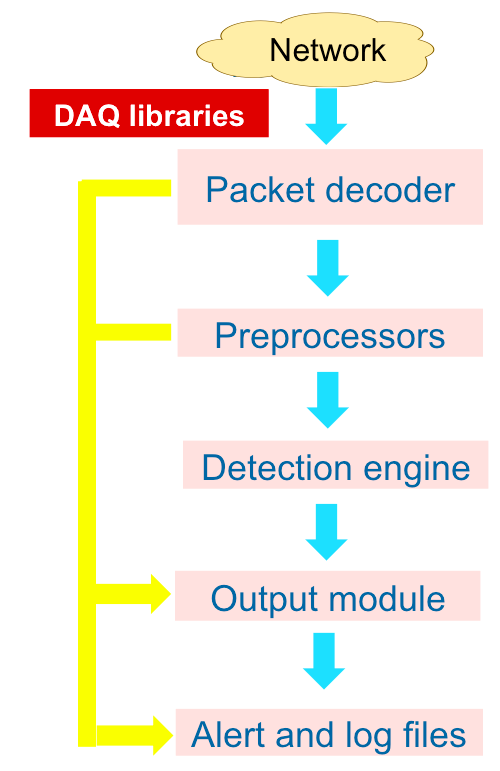
The basis of Snort is an engine consisting of five modules:
Both before and after Snort, attack detection systems appeared, but it was Snort that earned the fame of the de facto standard, which confirms over 4 million downloads of this software from www.snort.org and over 500 thousand registered users in the official community. What caused this love of Snort? Its language is for describing network security policy violations. On the one hand, this language is very simple and the rule for detecting an attack or other violation of security policies can be written in just a couple of minutes (or even faster). On the other hand, filters, complex queries, combining rules, setting thresholds, taking into account time intervals, allow you to write really very complex network event handlers.
At the end of 2014, the alpha version of Snort 3.0 (aka Snort ++) was announced, in which many of the ideas previously dusted “on the shelf” were implemented. In particular, the system design has been redesigned to become more user-oriented. Also, a mechanism for automatically identifying protocols on all ports has appeared, support for parallel processing of packets, and the language for describing rules has become even simpler.
At the end of 2014, another major change was made to Snort, which was included in the release 2.9.7 of the system, without waiting for Snort 3.0 to go into production. We are talking about OpenAppID, that is, the language for recognizing application protocols and implementing what Cisco calls Application Visibility and Control. In essence, we are talking about a mechanism (in the form of a separate preprocessor) for describing signatures for native applications and using them in decision rules (attack signatures). So far, Snort with OpenAppID is ahead of Cisco FirePOWER in this way. Now, to describe your applications in Cisco FirePOWER, you must use either the HEX editor or give a pre-recorded PCAP file with the traffic of the application of interest to the system input. This is not very convenient and requires certain skills. OpenAppID language,
Firepower
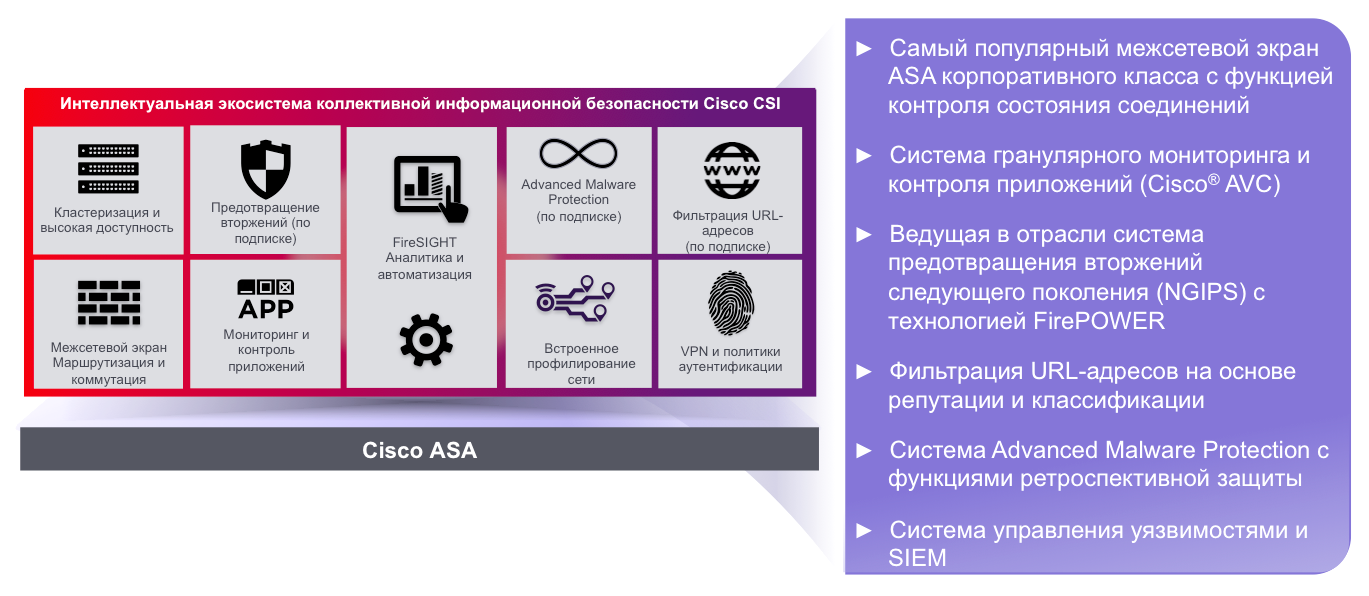
After 3 years, in 2001, Martin Resh founded the commercial company Sourcefire, within the framework of which a commercial version of Snort was created, called 3D Sensor, FirePOWER, etc. at different times. The main goal of Martin Resh was to offer customers a turnkey and automated solution, not requiring a lot of effort to configure and implement. The second goal was to create a high-performance solution capable of detecting attacks at high speeds of tens of gigabits per second. This was the first generation of Sourcefire devices. Then the second series of devices appeared, in which the application identification function appeared (it appeared in Snort only last year), the FireAMP malicious code detection mechanism, firewall and a number of other functions. In the third generation, a full-fledged next-generation ITU (NGFW) has appeared.
Currently, this platform is presented in the form of 6 implementation options:
How is the commercial software of these six platforms different from Snort, which can be downloaded freely from the Internet?
What are the differences?
I’ll try to highlight the key features present in FirePOWER technologies:
We could stop at this, completing the comparison of protective sensors built on the basis of Snort and FirePOWER. But this is not all that is needed for a complete protection system, especially in the corporate environment. Let's see what management functions, including and centralized, are offered along with Snort or FirePOWER.
Snort itself has no control system. However, the output module allows you to send the results of work to external systems, which developers did not fail to take advantage of, who offered the market several different systems for managing, generating reports, analyzing and visualizing Snort security events. Among them, ACID (has not been updated for a very long time), BASE , Snorby , Sguil , Aanval(commercial solution). I worked with ACID a very, very long time ago when I wrote the book “Attack Detection”. In addition, like BASE, ACID does not have advanced analytical capabilities for working with data. I did not work with Aanval, and commercial third-party management systems for the free Snort are not exactly what you need (although in some cases it is possible). But as for Snorby and Sguil, I can say that the second is more popular. Let's try to compare it with the “native” FirePOWER sensor management system - FireSIGHT Management Center (formerly called Defense Center).
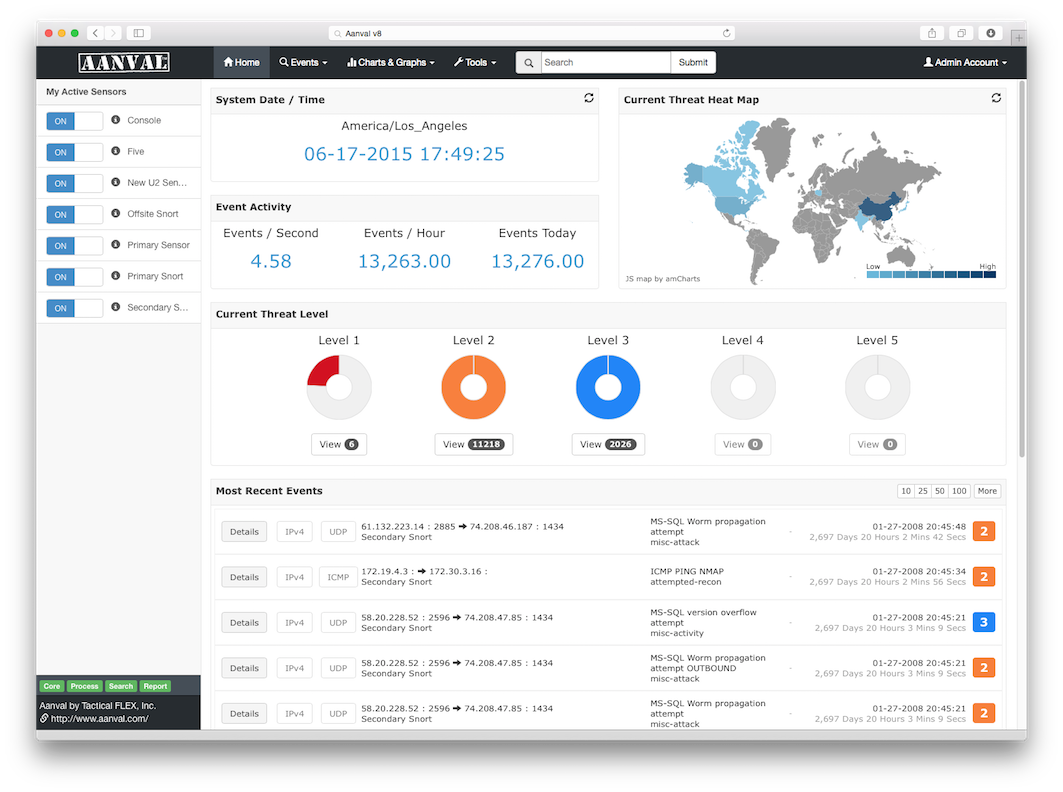
What is Sguil? In essence, this is an event aggregation system from Snort, which allows you to visualize what the Snort output module outputs to the outside - an alarm, the contents of the packet, and other related information. Further, Sguil allows you to run other tools through it for a more detailed investigation of recorded events. These tools may include:
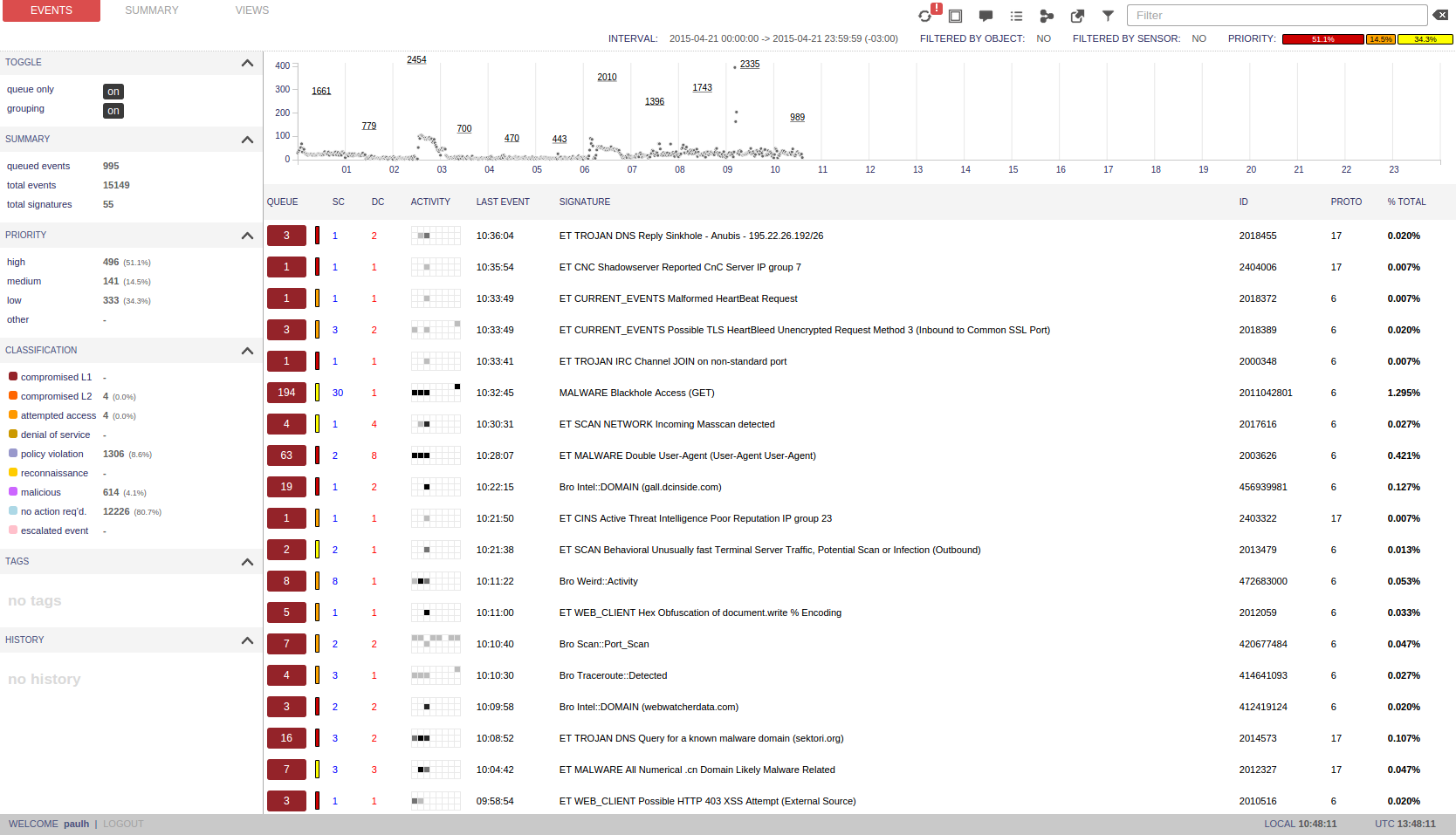
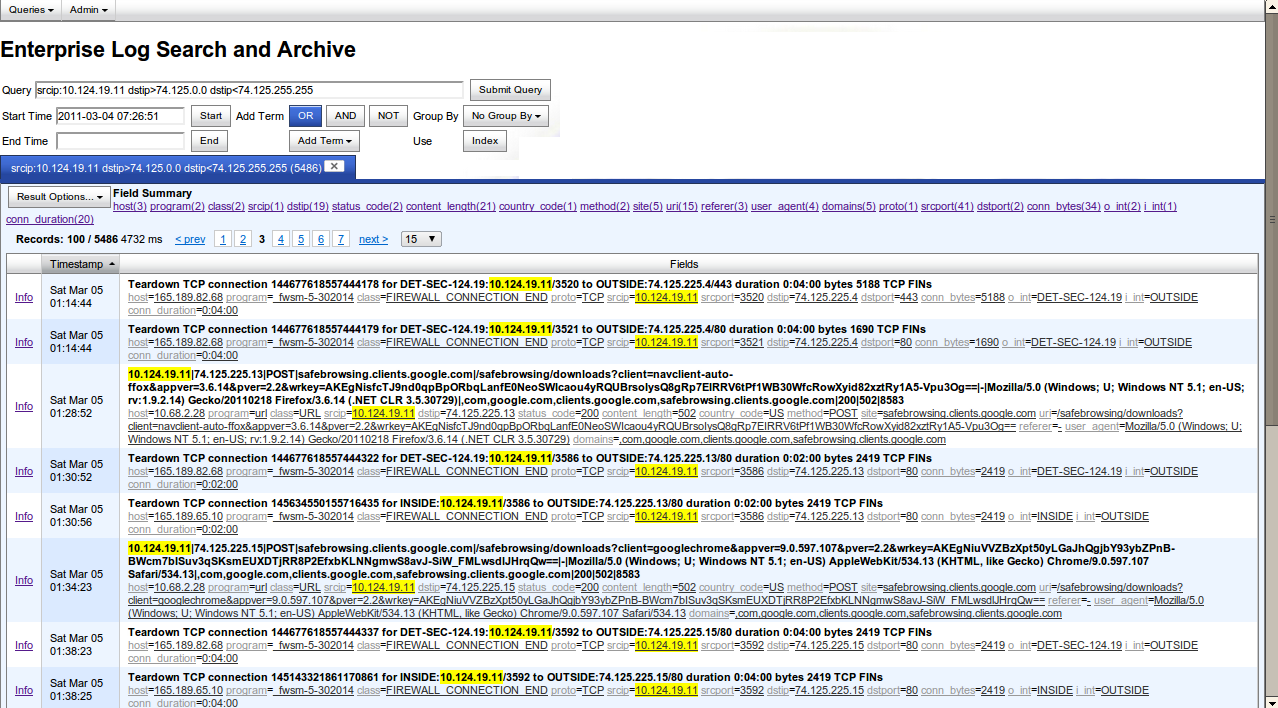
In principle, if you have the qualifications and time, from a bunch of Sguil and other monitoring tools (for example, included in the Security Onion), you can create a good event management system that Snort gives us. But only ... Managing rules, configuring sensors, monitoring their status, updating, backing up the event database, role-based access control, hierarchical management system, reporting ... All this remains inaccessible to Sguil users.
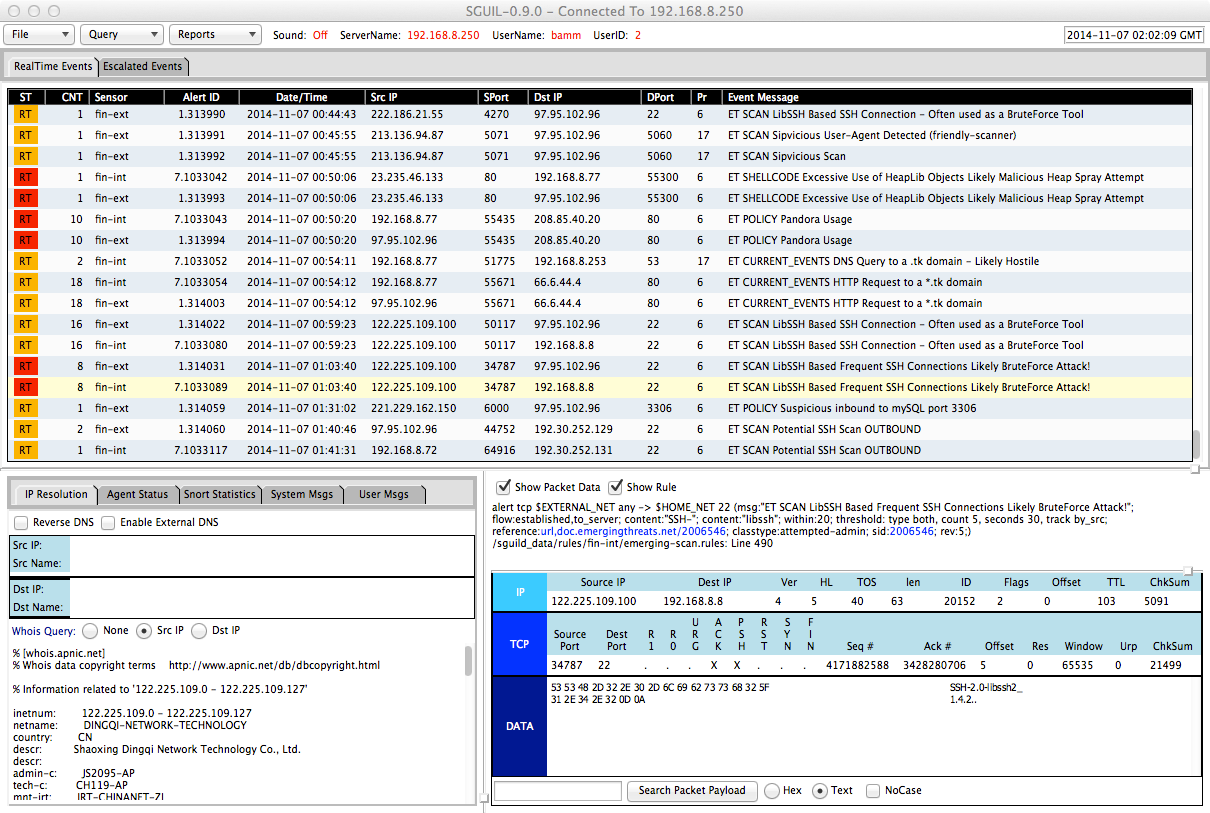
The “native” FireSIGHT Management Center does not have these shortcomings. Among its functions:
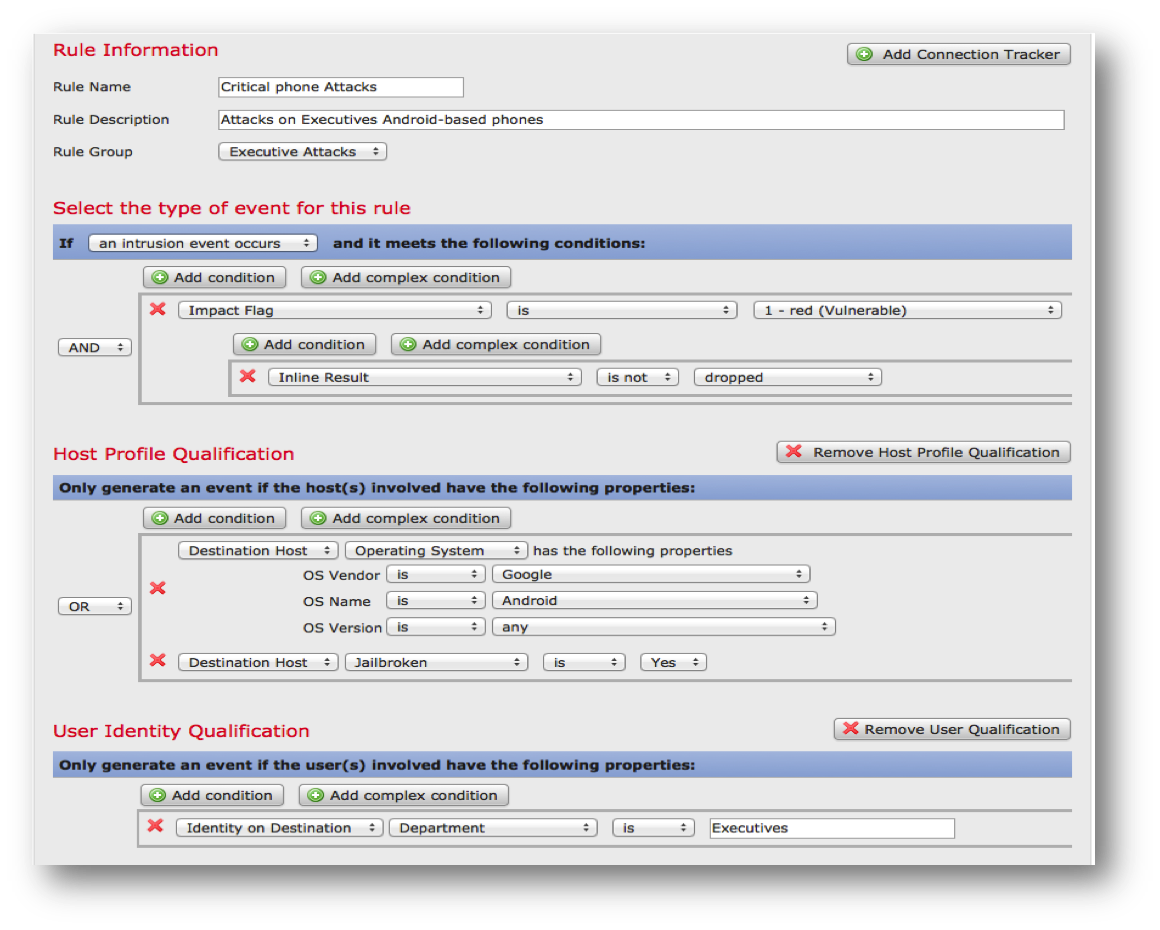
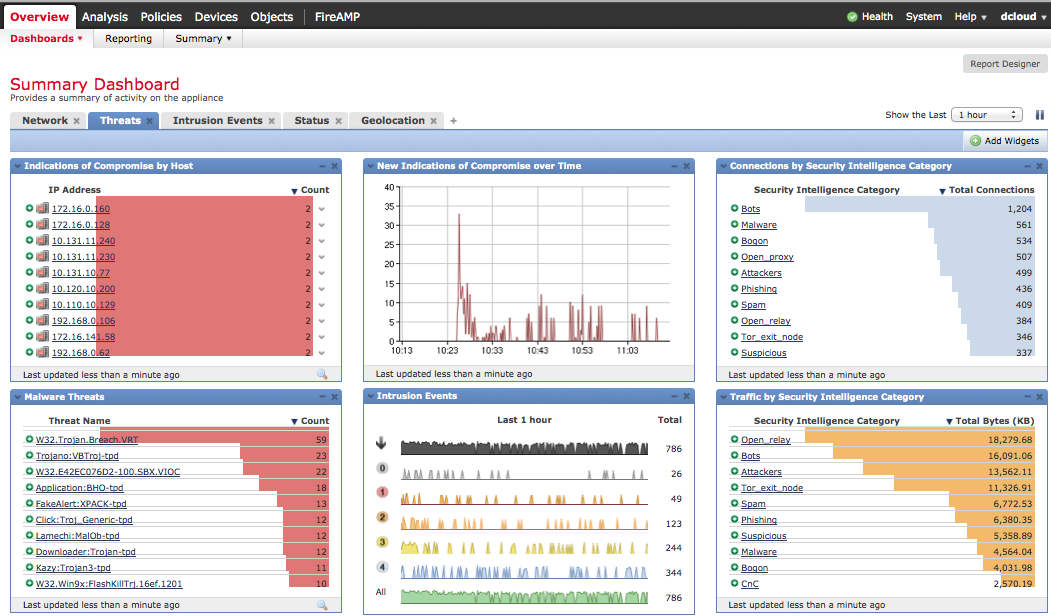
In essence, FireSIGHT is a means of automating routine tasks that used to be so precious in responding to incidents. For example, Snort and FirePOWER have a HAT (Host Attribute Table) - an XML file that associates the operating systems used on it with each IP address, as well as service-port associations. In Snort, this file is created manually, which on a large network can present some difficulties. In FirePOWER, this file is created automatically by RNA and does not require manual work. And there are many such examples.
SGUIL has two advantages over the “native” FireSIGHT Management Center. Firstly, it is free. And secondly, it displays data from sensors in real time; FireSIGHT has a maximum data refresh rate of once per minute. But FireSIGHT allows you to integrate FirePOWER sensors with various external security systems used in the corporate segment - security scanners, firewalls, routers and switches, packet capture systems, security event visualization systems, SIEM, etc. This is done through special APIs that are also missing from the same Snort (although with the help of various scripts you can try to integrate it with a number of the same free protection tools).
Summary
As a conclusion, I would not want to draw any conclusions except one. Statements that FirePOWER technologies, previously owned by Sourcefire and later acquired by Cisco, and the free Snort attack detection system that once underpinned Sourcefire's solutions, are not the same thing. Well, that is, not at all the same thing. Yes, Snort remains the de facto standard for attack detection systems, but Cisco FirePOWER is much more than just IDS. Here you have an application level firewall, URL filtering, malicious code neutralization, built-in correlation of events, incident investigation, integration with security scanners, and many other functions that automate security routine tasks.
Snort
Let's start with a brief background. Snort was created by Martin Reshem in 1998 and quickly gained popularity as a free intrusion detection system that allows you to write rules for attack detection on your own and without much effort. Essentially, the Snort signature description language has become the de facto standard for many intrusion detection systems that use it in their engines.
The basis of Snort is an engine consisting of five modules:
- Packet sniffer. As the name implies, this module is responsible for capturing data transmitted over the network for subsequent transmission to the decoder. He does this using the DAQ (Data AcQuisition) library. This sniffer can work “in break”, in passive mode or read network data from a previously prepared file.
- Packet decoder. This module is responsible for parsing the headers of captured packets, parsing them, searching for anomalies and deviations from the RFC, analyzing TCP flags, excluding individual protocols from further analysis, and other similar work. This decoder focuses on the TCP / IP stack.
- Preprocessors. If the decoder analyzed traffic at the 2nd and 3rd levels of the reference model, then the preprocessors are designed for more detailed analysis and normalization of protocols at the 3rd, 4th and 7th levels. Among the most popular preprocessors are frag3 (working with fragmented traffic), stream5 (reconstructing TCP streams), http_inspect_ (normalizing HTTP traffic), DCE / RPC2, sfPortscan (used to detect port scans) and various decoders for Telnet, FTP protocols , SMTP, SIP, SSL, SSH, IMAP, etc. Some Russian developers write their preprocessors (for example, for industrial protocols) and add to their own intrusion detection systems (IDS), built on the basis of Snort.
- Attack Detection Engine This engine consists of two parts. The rule designer collects many different decision rules (attack signatures) into a single set, optimized for subsequent use by the inspection subsystem of captured and processed traffic in search of various violations.
- Output module. Upon detection of an attack, Snort can issue (record or display) the corresponding message in various formats - file, syslog, ASCII, PCAP, Unified2 (binary format for faster and easier processing).

Both before and after Snort, attack detection systems appeared, but it was Snort that earned the fame of the de facto standard, which confirms over 4 million downloads of this software from www.snort.org and over 500 thousand registered users in the official community. What caused this love of Snort? Its language is for describing network security policy violations. On the one hand, this language is very simple and the rule for detecting an attack or other violation of security policies can be written in just a couple of minutes (or even faster). On the other hand, filters, complex queries, combining rules, setting thresholds, taking into account time intervals, allow you to write really very complex network event handlers.
At the end of 2014, the alpha version of Snort 3.0 (aka Snort ++) was announced, in which many of the ideas previously dusted “on the shelf” were implemented. In particular, the system design has been redesigned to become more user-oriented. Also, a mechanism for automatically identifying protocols on all ports has appeared, support for parallel processing of packets, and the language for describing rules has become even simpler.
At the end of 2014, another major change was made to Snort, which was included in the release 2.9.7 of the system, without waiting for Snort 3.0 to go into production. We are talking about OpenAppID, that is, the language for recognizing application protocols and implementing what Cisco calls Application Visibility and Control. In essence, we are talking about a mechanism (in the form of a separate preprocessor) for describing signatures for native applications and using them in decision rules (attack signatures). So far, Snort with OpenAppID is ahead of Cisco FirePOWER in this way. Now, to describe your applications in Cisco FirePOWER, you must use either the HEX editor or give a pre-recorded PCAP file with the traffic of the application of interest to the system input. This is not very convenient and requires certain skills. OpenAppID language,
Firepower
After 3 years, in 2001, Martin Resh founded the commercial company Sourcefire, within the framework of which a commercial version of Snort was created, called 3D Sensor, FirePOWER, etc. at different times. The main goal of Martin Resh was to offer customers a turnkey and automated solution, not requiring a lot of effort to configure and implement. The second goal was to create a high-performance solution capable of detecting attacks at high speeds of tens of gigabits per second. This was the first generation of Sourcefire devices. Then the second series of devices appeared, in which the application identification function appeared (it appeared in Snort only last year), the FireAMP malicious code detection mechanism, firewall and a number of other functions. In the third generation, a full-fledged next-generation ITU (NGFW) has appeared.

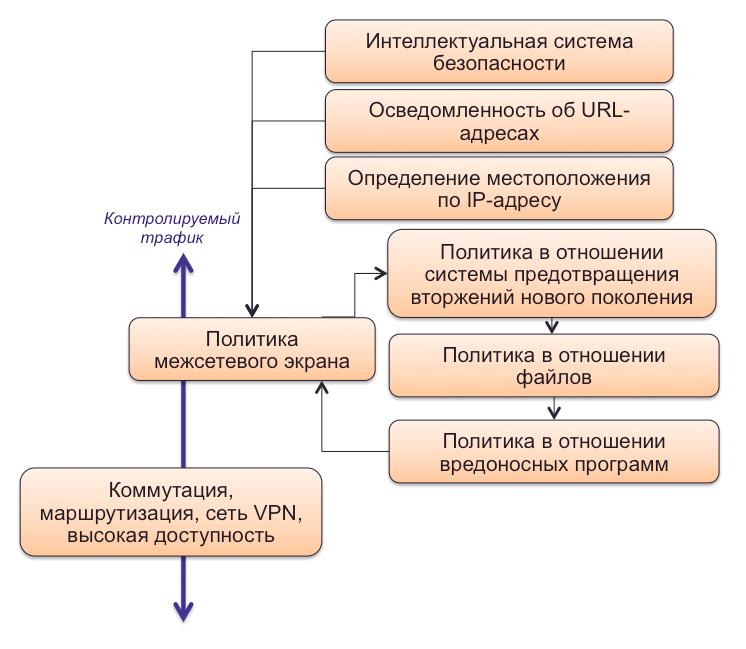
Currently, this platform is presented in the form of 6 implementation options:
- Separate high-performance Cisco FirePOWER Appliance devices . In fact, these are the same devices that Sourcefire released.
- The Cisco ASA with FirePOWER Services firewall , which in addition to the functionality of the traditional ITU and VPN (Site-to-Site and Remote Access) has received the capabilities of the next-generation ITU (NGFW), intrusion prevention system (NGIPS), content filtering system, malicious code neutralization system and a number of other functions.
- Router Cisco FirePOWER Threat Defense for ISR , allowing you to run all of the above features on the basis of the router.
- Virtual versions of all the mentioned features, launched on the basis of VMware.
- The new Firepower 9300 hardware platform , capable of performing many network security tasks (from ITU and VPN to combating malicious code and DDoS reflection) at speeds of hundreds of gigabits
- Cisco Firewalls and Intrusion Detection Systems Cisco ISA 3000 and Cisco ISA 4000.
How is the commercial software of these six platforms different from Snort, which can be downloaded freely from the Internet?
What are the differences?
I’ll try to highlight the key features present in FirePOWER technologies:
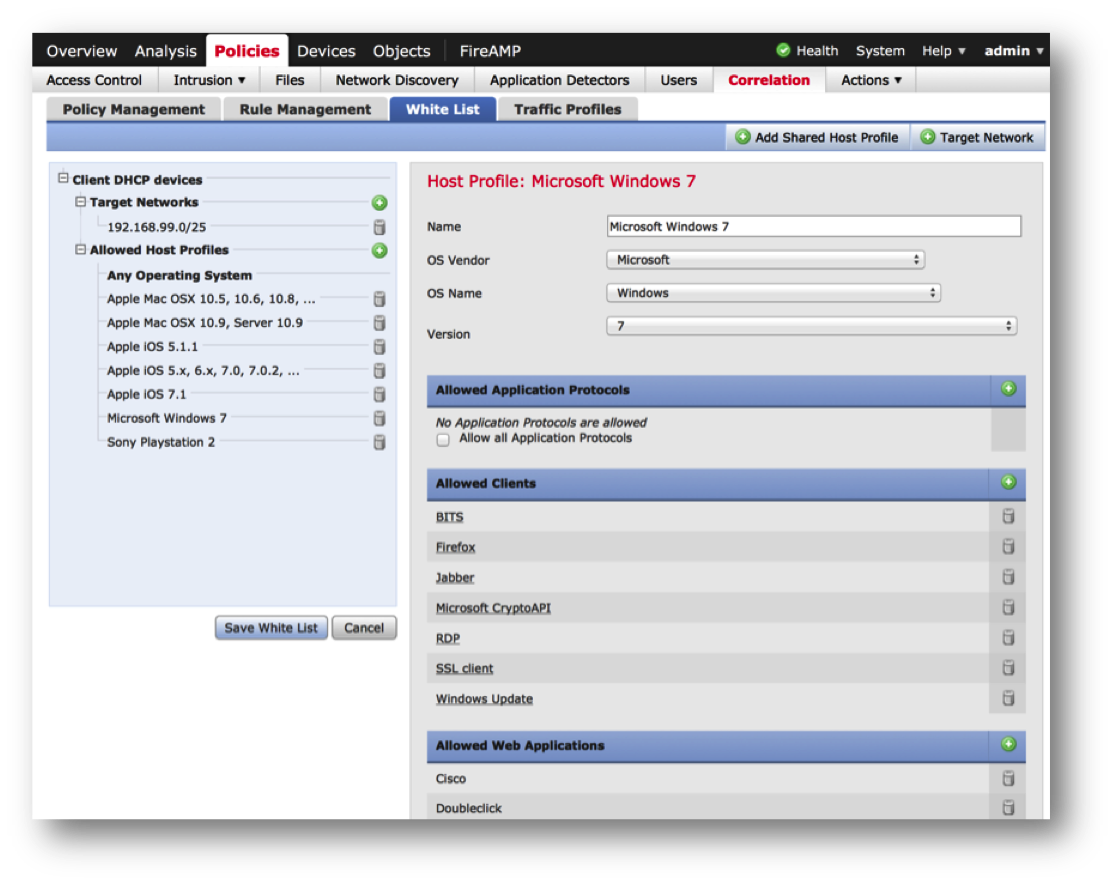
- One of the major changes that appeared in 2007 was RNA (Real-Time Network Awareness) technology, which allows you to build an active profile of everything that happens in a controlled network, build a network map, identify hosts, protocols and applications by passive traffic analysis. Later this information is compared with data on attacks and other violations of security policies.

- Similar to RNA is RUA (Real-Time User Awareness) technology, which associates user data with network activity. It is always useful to see that the attack is carried out against the user “Ivanov II,” and not against the impersonal host with the IP address 192.168.1.34.
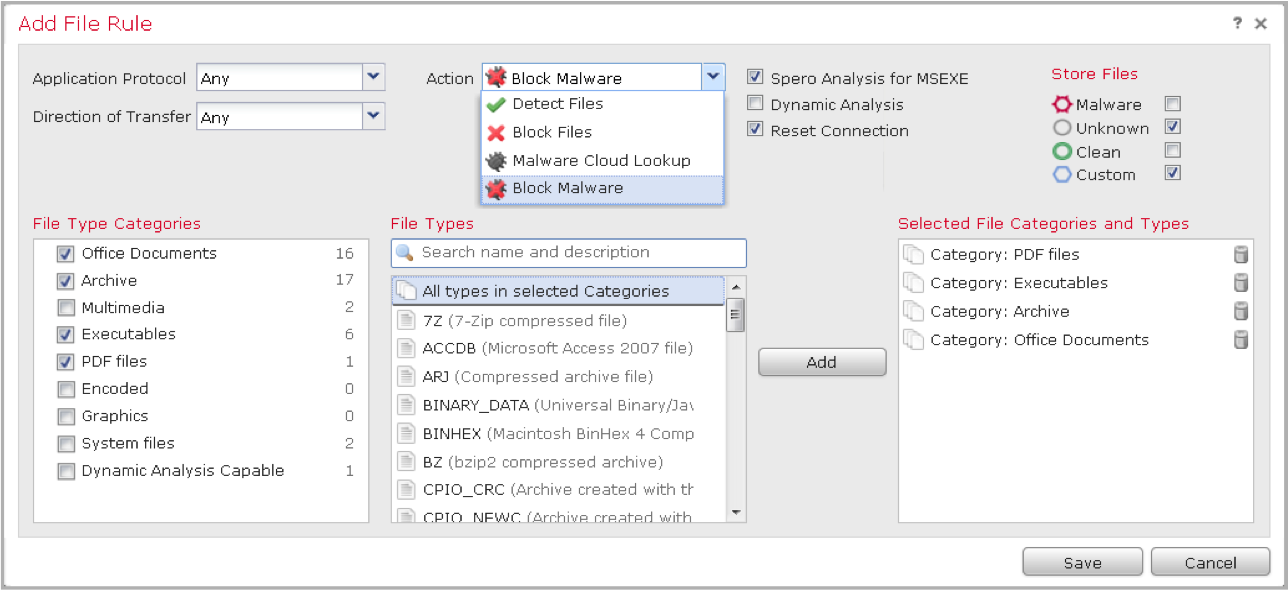
- In 2007, Sourcefire bought the rights to ClamAV, a free antivirus that was integrated with an intrusion prevention system to analyze not network packets and connections, but files transferred over the network. Later, after the acquisition of Immunet in 2011, this solution developed into the AMP for Networks system, which allows identifying malicious code using seven different algorithms, as well as performing retrospective analysis (post-facto analysis) of files that have already entered the network. By the way, identification and blocking of files by their types appeared in Snort, starting with version 2.9.7.

- Martin Resch is skeptical of the idea of firewalling, believing that attackers just use the ports open on ITU to encapsulate their unauthorized actions. Therefore, instead of the traditional firewall, Sourcefire solutions implemented an application-level firewall, which is also the next generation firewall (NGFW), which allows controlling violations in the use of applications, encapsulating prohibited traffic in them, etc. By the way, precisely for this reason, NGFW is almost impossible to certify according to Russian requirements for ITU - NGFW simply do not have such functionality; this is not their task.
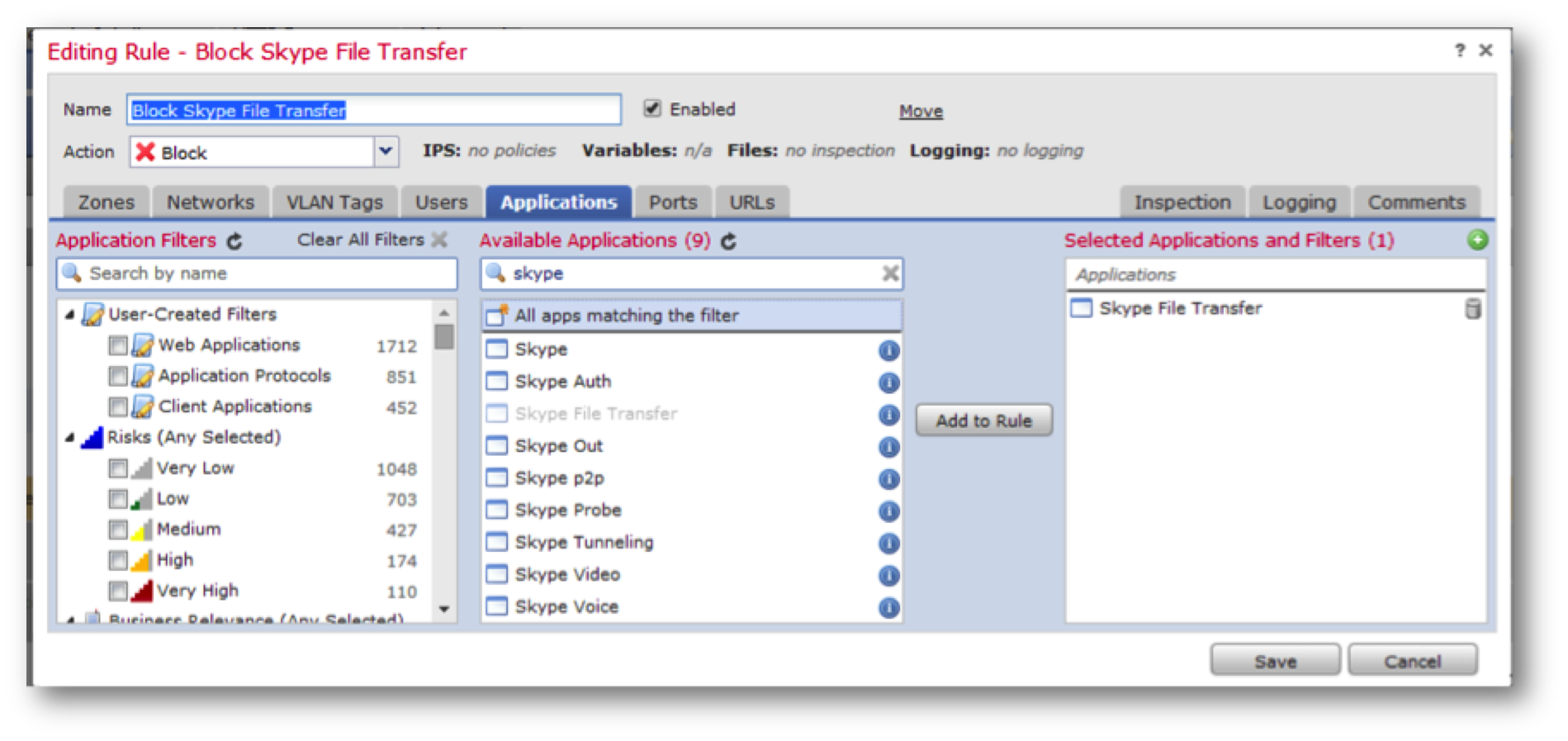
- To implement the NGFW function, you must be able to identify applications running on the network. This is done using AppID technology, which essentially became the basis for the development of the previously mentioned OpenAppID technology. In addition to predefined application detectors, it is possible to describe your own applications (this is described above).

- But the implementation of the firewall functions in FirePOWER was still worth it. In particular, in any of the six platforms using FirePOWER technologies, when creating security policies, you can use zones, VLAN, IP, ports, as well as users and groups in ITU rules.

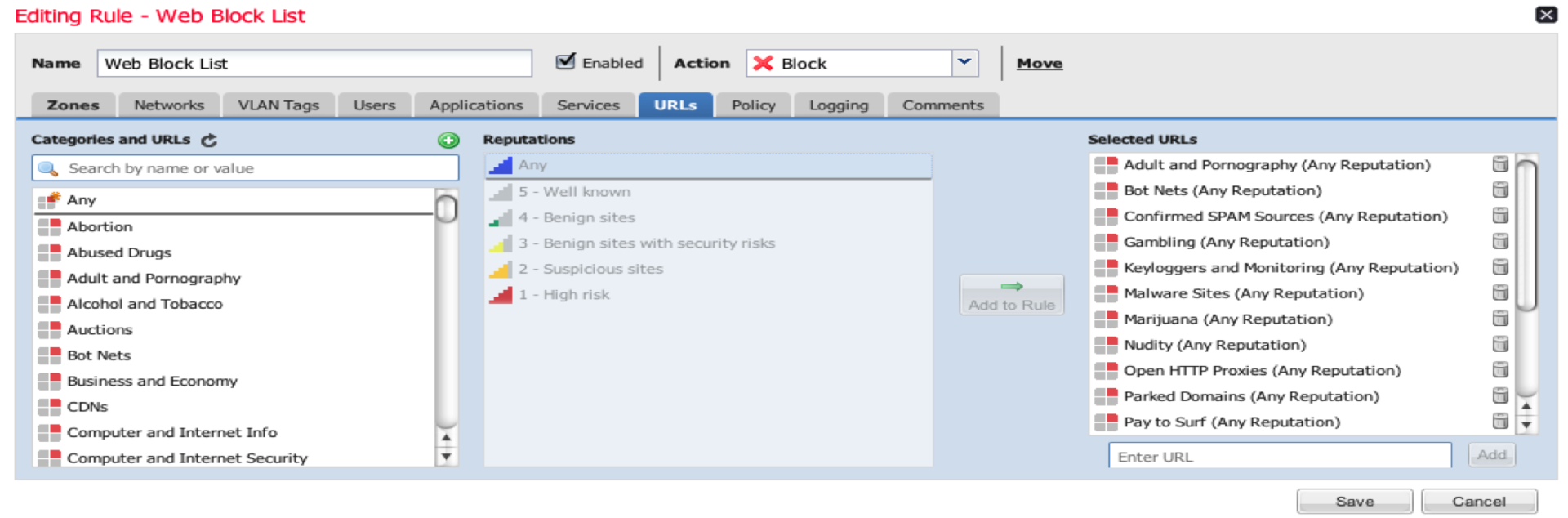
- In addition to blocking traffic by IP address, FirePOWER also implemented URL filtering technology. In the case of using SSL, it can be decrypted with subsequent inspection. Currently, SSL inspection is available only in the FirePOWER Appliance, but by the end of 2015 it will be implemented on other platforms.

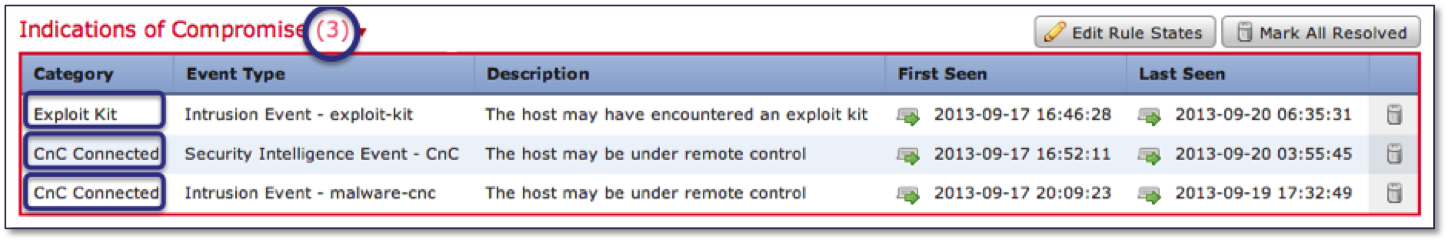
- Having on board a single sensor not only an intrusion detection system, but also a firewall, a system for combating malicious code, a URL filtering system and a number of other protective technologies, it was logical to combine their capabilities in the identification of compromise indicators (IOC), which was done in one version of FirePOWER.

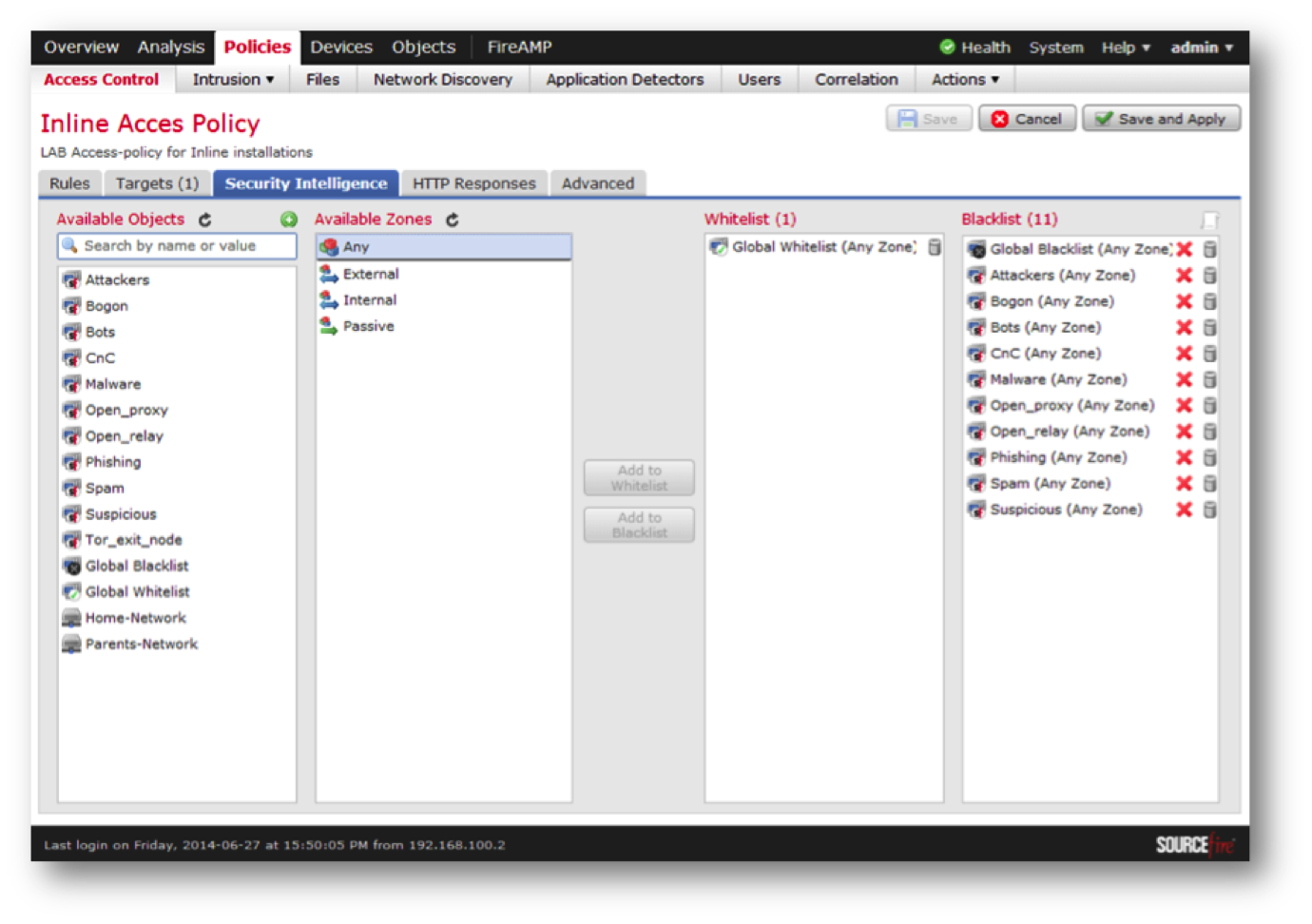
- To reduce the load on the sensors, they implemented the so-called Security intelligence function, which consists in maintaining black and white lists of IP addresses. This allows you to not process trusted traffic and block the initially malicious traffic. This is done at the decoder level, which ultimately improves the performance of the entire system. Another built-in feature is geolocation support, which allows geo-referencing of addresses recorded in network packets and sessions.
- FirePOWER has a built-in function for detecting protected content by checksums (it appeared in Snort 2.9.7), which can be used as a lightweight version of a DLP system.
- In terms of network capabilities, FirePOWER implements NAT and routing support, which Snort does not have, as well as stacking devices to improve performance (only for the FirePOWER Appliance) and clustering (only for Cisco ASA with FirePOWER Services) - up to 16 devices. In the case of clustering, the aggregate performance in the ITU mode will be 640 Gbit / s, and in the IPS mode - 160 Gbit / s.
- The commercial software code has been optimized (instead of GCC. Intel C is used), and the FirePOWER Appliance also uses special network cards that allow balancing the load and processing of TCP flows between several cores on one device. With their help, several devices are stacked. Support for multi-core processors should be implemented in Snort 3.0.
We could stop at this, completing the comparison of protective sensors built on the basis of Snort and FirePOWER. But this is not all that is needed for a complete protection system, especially in the corporate environment. Let's see what management functions, including and centralized, are offered along with Snort or FirePOWER.
Snort itself has no control system. However, the output module allows you to send the results of work to external systems, which developers did not fail to take advantage of, who offered the market several different systems for managing, generating reports, analyzing and visualizing Snort security events. Among them, ACID (has not been updated for a very long time), BASE , Snorby , Sguil , Aanval(commercial solution). I worked with ACID a very, very long time ago when I wrote the book “Attack Detection”. In addition, like BASE, ACID does not have advanced analytical capabilities for working with data. I did not work with Aanval, and commercial third-party management systems for the free Snort are not exactly what you need (although in some cases it is possible). But as for Snorby and Sguil, I can say that the second is more popular. Let's try to compare it with the “native” FirePOWER sensor management system - FireSIGHT Management Center (formerly called Defense Center).

What is Sguil? In essence, this is an event aggregation system from Snort, which allows you to visualize what the Snort output module outputs to the outside - an alarm, the contents of the packet, and other related information. Further, Sguil allows you to run other tools through it for a more detailed investigation of recorded events. These tools may include:
- Squert , a web application for organizing queries and displaying data stored in a Squil database.

- ELSA , a centralized log management system, a kind of lightweight SIEM.

- NetworkMiner , a network investigation tool based on a snapshot pcap file.
- WireShark, which needs no introduction.
In principle, if you have the qualifications and time, from a bunch of Sguil and other monitoring tools (for example, included in the Security Onion), you can create a good event management system that Snort gives us. But only ... Managing rules, configuring sensors, monitoring their status, updating, backing up the event database, role-based access control, hierarchical management system, reporting ... All this remains inaccessible to Sguil users.

The “native” FireSIGHT Management Center does not have these shortcomings. Among its functions:
- Centralized management and configuration of multiple FirePOWER sensors.
- Updating sensors without the need to recompile the code (still, do not forget to specify the correct parameters).
- Correlation of events not only from several IDS sensors, but also from different types of protection tools and technologies - ITU, AMP, RNA, RUA, etc.

- Creating security policies.
- Investigation of incidents.
- Manage profiles for each node (addresses, OS, applications, protocols, users).
- Integration with AD and centralized, hierarchical user management.
- Monitoring the status of remote sensors.
- Customizable dashboard to display various information.
- Report Generation.
- Backup database.
- Etc.

In essence, FireSIGHT is a means of automating routine tasks that used to be so precious in responding to incidents. For example, Snort and FirePOWER have a HAT (Host Attribute Table) - an XML file that associates the operating systems used on it with each IP address, as well as service-port associations. In Snort, this file is created manually, which on a large network can present some difficulties. In FirePOWER, this file is created automatically by RNA and does not require manual work. And there are many such examples.
SGUIL has two advantages over the “native” FireSIGHT Management Center. Firstly, it is free. And secondly, it displays data from sensors in real time; FireSIGHT has a maximum data refresh rate of once per minute. But FireSIGHT allows you to integrate FirePOWER sensors with various external security systems used in the corporate segment - security scanners, firewalls, routers and switches, packet capture systems, security event visualization systems, SIEM, etc. This is done through special APIs that are also missing from the same Snort (although with the help of various scripts you can try to integrate it with a number of the same free protection tools).
Summary
As a conclusion, I would not want to draw any conclusions except one. Statements that FirePOWER technologies, previously owned by Sourcefire and later acquired by Cisco, and the free Snort attack detection system that once underpinned Sourcefire's solutions, are not the same thing. Well, that is, not at all the same thing. Yes, Snort remains the de facto standard for attack detection systems, but Cisco FirePOWER is much more than just IDS. Here you have an application level firewall, URL filtering, malicious code neutralization, built-in correlation of events, incident investigation, integration with security scanners, and many other functions that automate security routine tasks.

