Security Week 40: vulnerabilities in CMS Drupal and not only
 Last week, the developers of CMS Drupal closed ( news , more on their website ) just two critical vulnerabilities. Both issues affect Drupal versions 7.x and 8.x. The most serious vulnerability was found in the built-in e-mail sending system (DefaultMailSystem :: mail ()). You can use it in such a way that when processing a message it becomes possible to execute arbitrary code. As usual, this is due to the lack of proper verification of a number of variables.
Last week, the developers of CMS Drupal closed ( news , more on their website ) just two critical vulnerabilities. Both issues affect Drupal versions 7.x and 8.x. The most serious vulnerability was found in the built-in e-mail sending system (DefaultMailSystem :: mail ()). You can use it in such a way that when processing a message it becomes possible to execute arbitrary code. As usual, this is due to the lack of proper verification of a number of variables.The second vulnerability was found in the Contextual Links module - it allows modifying elements of web pages without switching to the control panel. Failure to verify the parameters passed during the execution of such a request may also lead to the execution of the code. However, unlike the first vulnerability, this one is exploited only if the attacker already has the rights to edit the site.
Such news usually does not get into the digest: well, found, well, closed, well done! But at least once a year you should look at the most popular content management systems and understand in perspective how things are going with security. Is there a fragmentation of CMS versions, similar, for example, to the fragmentation of the Android platform? Is everything so bad with security, as, for example, in the industry of those IoT devices, which are not even IoT devices, but routers and cameras? Let's get a look.
First you need to understand where to look. Enough detailed information about the use of a CMS gives Web Technology Surveys . The authors of the resource regularly scan the 10 million most visited sites on the Internet (according to the Alexa rating service) and analyze the content management systems used. The general results of the study can be viewed on this page , here is the graph from there:
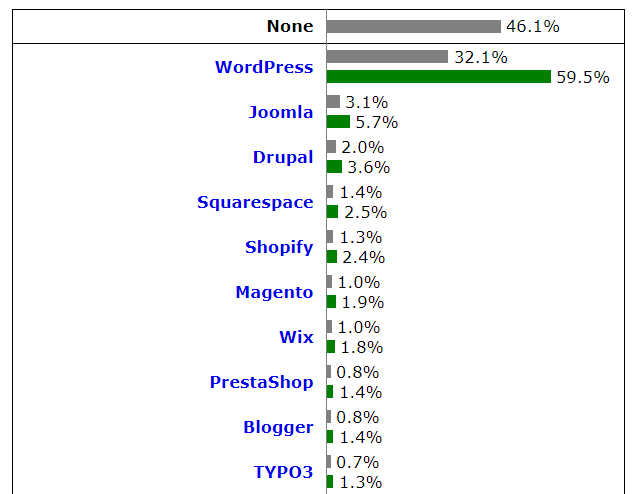
Well, firstly, it was not possible to get information about CMS for 46.1% of sites; more precisely, none of the systems that this service can reliably identify are used there. Among those sites where CMS has been defined, the undisputed leader is Wordpress, a sort of Android CMS market. Joomla and Drupal occupy the second and third places with a significant lag, and then in Top10 there are mainly services offering the creation of a ready-made website on their own platform - for those who need to be simpler and faster. Combined, Joomla, Drupal and Wordpress are installed on 68.8% of sites with a well-known CMS, or 37.2% of all sites out of the 10 million studied.
There is already a fragmentation at the level of the choice of CMS: Wordpress is the clear leader, but even it is installed on only a third of online resources, and half of the sites generally work incomprehensibly on what. Perhaps, there is a gloomy admin that is still old-school uploading static HTML via FTP. It is difficult to draw conclusions from this diversity: on the one hand, fragmentation complicates life for an attacker, on the other - no one really knows how the security situation is in about half of the Internet. In cryptography, self-written encryption algorithms have long been equated to a sharply sharpened rake. Should web management be different?
Let's look at the distribution of versions for the three most popular CMS. Here is the distribution for wordpress. w3techs update their reports daily, so the information is expected to be the latest.
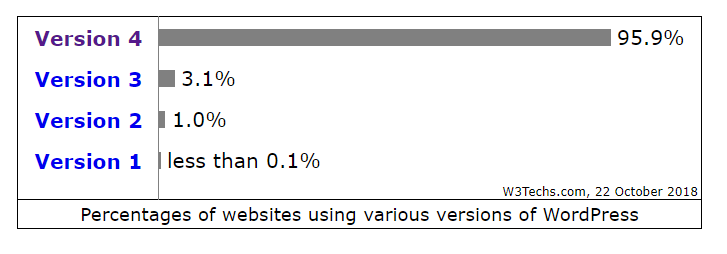
Somehow boring even. Let's look at the details of the current version 4.x:
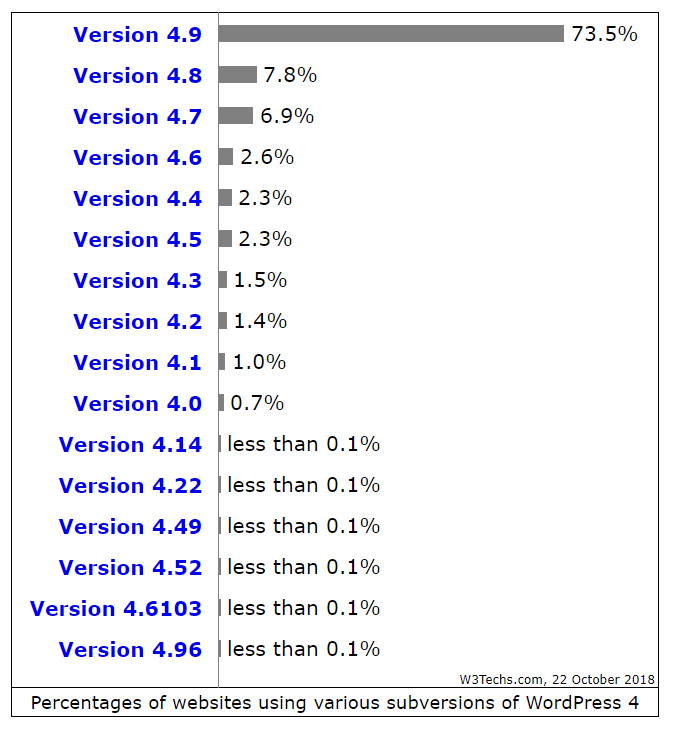
Slightly more than 70% of Wordpress websites use (as of the publication date) the most up-to-date version (without regular updates of the main release). This, of course, is a more pleasant distribution than Android, where the current version 8.x is used by 19.2% of devices, but not as much as we would like.
And there is something to fear? Let's look at the history of versions of Wordpress. Version 4.9 was released on November 15, 2017, that is, WordPress 4.8 and earlier versions have been outdated for almost a year. Since the release of version 4.9, at least four CMS updates have been sent to fix vulnerabilities. How serious the risk of each of them is is a subject for more detailed research, although there have been no critical bugs over the past year. However, Julyrelease 4.9.7 closes the vulnerability, under certain conditions, which allows deleting files outside the Uploads folder.
Let's see how the hero of the last week is doing - CMS Drupal.

So it goes. The latest version of Drupal 8.x is used by 11.8% of sites that generally use Drupal. The most popular is the previous (note for the sake of justice - supported) release 7.x. Specification on specific releases within the framework of the main branch of w3techs does not, so suppose that everyone has already been updated (this, of course, is a bold assumption). In any case, almost 10% of Drupal sites use unsupported versions 4.x – 6.x.
The situation for CMS Joomla is as follows:

The current version of Joomla 3.8.13 was released recently - October 9th. You can see what percentage of sites updated to the latest version in such a short time.
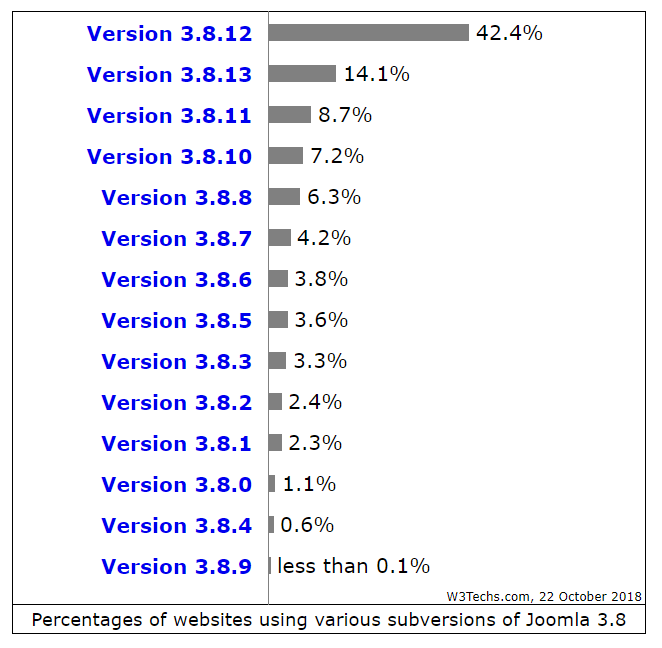
14.1% of all users of the branch 3.8. Or 5.8% of all Joomla users are those who managed to update the site to the latest version in 13 days. What are the consequences if you do not update the CMS on time? Switch back to Wordpress examples, as this is the most popular and most cracked web content management system. So (all of a sudden), reports about the practical hijacking of sites for malicious activity mostly mention not the main Wordpress code, but its plugins.
Here, for example, last year's news about plugins actually attacked, including, for example, the Flickr Gallery plugin. In December 2017, Wordpress blocked three more plugins - all of them were sold by the creators, and the new owners introduced backdoors into them. Here is another analysis.Plugin uses that were abandoned by developers a long time ago have critical vulnerabilities and are still used on hundreds of sites.
And it's not just plugins. Repeatedly, a brute force password is mentioned as a working method for attacking Wordpress sites (for example, here and here ). And this problem is also beyond the capabilities of Wordpress developers. Making it difficult for bruteforce and not to use simple passwords is the task of the administrator and site users, not the developers.
What happens when a site is successfully hacked? Above, I refer to the news about the installation of miners, although most often on sites appear classic malicious scripts. An indicative case occurred in the summer of this year: in July it was hackedCoinDash marketplace, and right during fundraising within the framework of ICO. How exactly hacked the site - not reported, it could not necessarily be a vulnerability in Wordpress. But the result is obvious: in the first phase of collecting funds from privileged participants on the site, they simply changed the wallet number to transfer funds, as a result of which $ 7.7 million in cryptocurrency equivalent went to the attackers. There is an interesting discussion on Reddit about this : would it not be safer to make a static page in critical cases? Oh, not sure what is safer.
According to the results of this mini-study, a clear question arises: is it necessary to update the CMS code, if critical vulnerabilities are not always, hacking sites are often done through plug-ins, or even brute-force passwords? As in the case of routers , a set of measures brings real benefits: updating the CMS, revising the list of installed plug-ins and regularly updating the really needed ones, changing the admin URL, strong passwords, multifactor authentication, and just user auditing. Website security (and anything else) is a process, not a result.
To add to the to-do list a regular check of the CMS version is not that difficult. If your site is managed by a third-party organization, it will not be superfluous to separately discuss the issue of regular updates. If you have once “set up a site”, and since then it “just works” without any support, you have problems. As we have seen today, even such a simple measure for enhancing the security of a website, such as updating the code, is used by no means all.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
