Check your sites for TLS Logjam vulnerability
A couple of months ago, a vulnerability called Logjam was discovered in the TLS protocol. Studies have shown that a large number of servers are subject to this vulnerability, because, using secure connections, they use the typical and most common simple encryption keys of 512 bits in size. Previously, this length could be enough to protect the client’s connection to the server. To date, research has been conducted to calculate the most common keys. Host-tracker offers functionality that allows you to instantly check this vulnerability.
Three ways to carry out a Logjam attack have been identified. One way is due to the settings of the web server, which by default uses 512-bit DH keys. To crack such keys, you just need to “listen” to the traffic of this server, and then do the decryption. Two other methods involve a man-in-the-middle attack. The first case involves the use of a special TLS connection acceleration mechanism, TLS False Start; in the second case, this mechanism is not required. However, both cases involve forcing the server to lower the cryptographic strength of keys to 512-bit.
Most servers and clients, when establishing a secure connection, use the Diffie-Hellman (DH) encryption mechanism. By requesting a connection, the client can reduce the encryption strength to the level of export ciphers using 512-bit DH keys. This is possible if the server supports a set of export ciphers. Accordingly, connecting between the client and the server, the attacker is able to intercept traffic and, on behalf of the client, request a decrease in the strength of the cipher. Researchers also report that with productive machines, 768-bit keys can be easily calculated, and special services can decrypt 1024-bit keys as well.
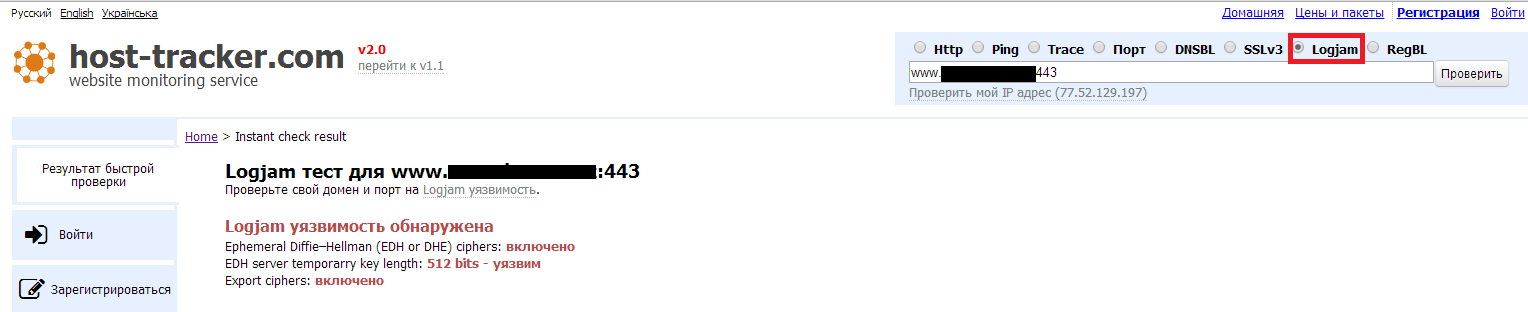
HostTracker offers the function of checking Logjam server vulnerabilities. This functionality is very simple and available as an option of the quick check service. To use it, just select the checkbox in the Logjam option, and enter the address of the server to be checked in the text box. After some time, the Logjam check will produce a result based on the check of the cipher suites used by the server.

If the server supports export ciphers, EDH ciphers, a 512-bit temporary DH key, then the Logjam service will detect these settings and indicate them as vulnerabilities. These settings should be fixed on the server. Researchers even suggested instructions for properly configuring SSL settings for different servers. So, for the Apache server, it is suggested to set the value “On” in the SSLHonorCipherOrder parameter - this directive sets the priority for the use of ciphers set by the server. Also, in the SSLCipherSuite directive, export cipher suites should be disabled, and the SSLv2 and SSLv3 protocols should be prohibited with the SSLProtocol directive.

Logjam in action
Three ways to carry out a Logjam attack have been identified. One way is due to the settings of the web server, which by default uses 512-bit DH keys. To crack such keys, you just need to “listen” to the traffic of this server, and then do the decryption. Two other methods involve a man-in-the-middle attack. The first case involves the use of a special TLS connection acceleration mechanism, TLS False Start; in the second case, this mechanism is not required. However, both cases involve forcing the server to lower the cryptographic strength of keys to 512-bit.
Most servers and clients, when establishing a secure connection, use the Diffie-Hellman (DH) encryption mechanism. By requesting a connection, the client can reduce the encryption strength to the level of export ciphers using 512-bit DH keys. This is possible if the server supports a set of export ciphers. Accordingly, connecting between the client and the server, the attacker is able to intercept traffic and, on behalf of the client, request a decrease in the strength of the cipher. Researchers also report that with productive machines, 768-bit keys can be easily calculated, and special services can decrypt 1024-bit keys as well.
Logjam quick check
HostTracker offers the function of checking Logjam server vulnerabilities. This functionality is very simple and available as an option of the quick check service. To use it, just select the checkbox in the Logjam option, and enter the address of the server to be checked in the text box. After some time, the Logjam check will produce a result based on the check of the cipher suites used by the server.
If the server supports export ciphers, EDH ciphers, a 512-bit temporary DH key, then the Logjam service will detect these settings and indicate them as vulnerabilities. These settings should be fixed on the server. Researchers even suggested instructions for properly configuring SSL settings for different servers. So, for the Apache server, it is suggested to set the value “On” in the SSLHonorCipherOrder parameter - this directive sets the priority for the use of ciphers set by the server. Also, in the SSLCipherSuite directive, export cipher suites should be disabled, and the SSLv2 and SSLv3 protocols should be prohibited with the SSLProtocol directive.
