Spam campaign “Love you” redirected to Japan
Studying the fresh wave of spam in Russia , we noticed another attack. Since mid-January 2019, the famous “Love you” campaign has been refined and redirected to Japan, where it is used to distribute the GandCrab 5.1 encoder.

According to telemetry, the latest version of “Love you” was launched on January 28, 2019, its activity was approximately twice as high as the initial one (see the chart below). As in mid-January, a set of malicious payloads is distributed with some updates using spam. So, we have seen attempts to download a cryptominer, software for changing system settings, a malicious bootloader, the Phorpiex worm, and the GandCrab version 5.1 encoder.

Figure 1. Detection of malicious JavaScript attachments distributed in the “Love you” campaign and its latest wave .
As of January 29, 2019, the overwhelming majority of detections are in Japan (95%), tens of thousands of malicious emails are detected every hour. On the same day, JS / Danger.ScriptAttachment (according to the ESET classification - malicious JavaScript distributed via email attachments) was the fourth-largest threat in the world and # 1 threat in Japan (see below).
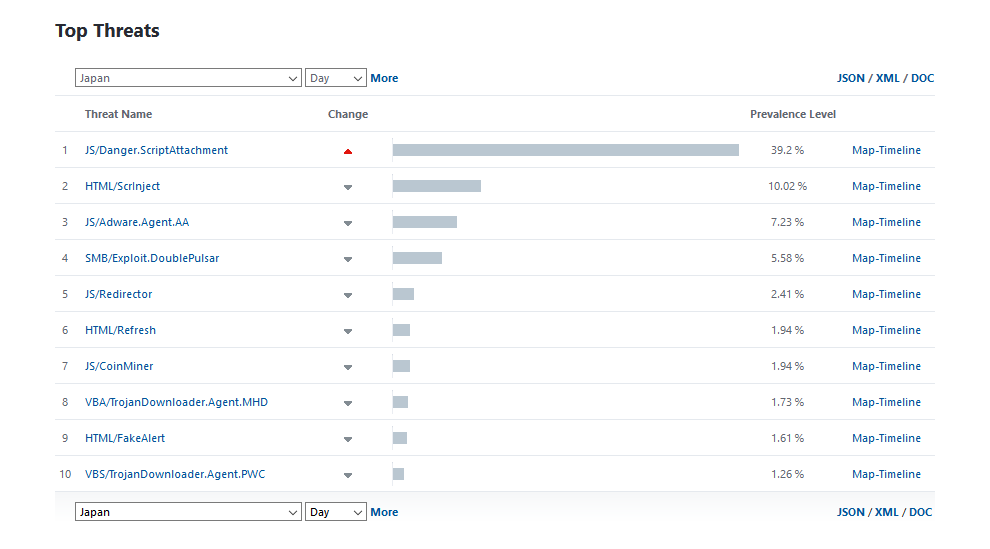
Figure 2. JS / Danger.Script Attachment was the # 1 threat in Japan as of January 29
In the last campaign, the attackers changed the texts of the mailings, moving from “Love You” in the subject line to headings related to Japan. Many smiles remain in the subject and body of the letter.
Topics of the letters that we saw during the analysis:
- Yui Aragaki;)
- Kyary Pamyu Pamyu;)
- Kyoko Fukada;)
- Yuriko Yoshitaka;)
- Sheena Ringo;)
- Misia;)
(Japanese stars of show business)
Studied malicious attachments These are ZIP archives disguised as images with PIC0- [9-digit-number] 2019-jpg.zip format names. The figure below shows examples of such letters.
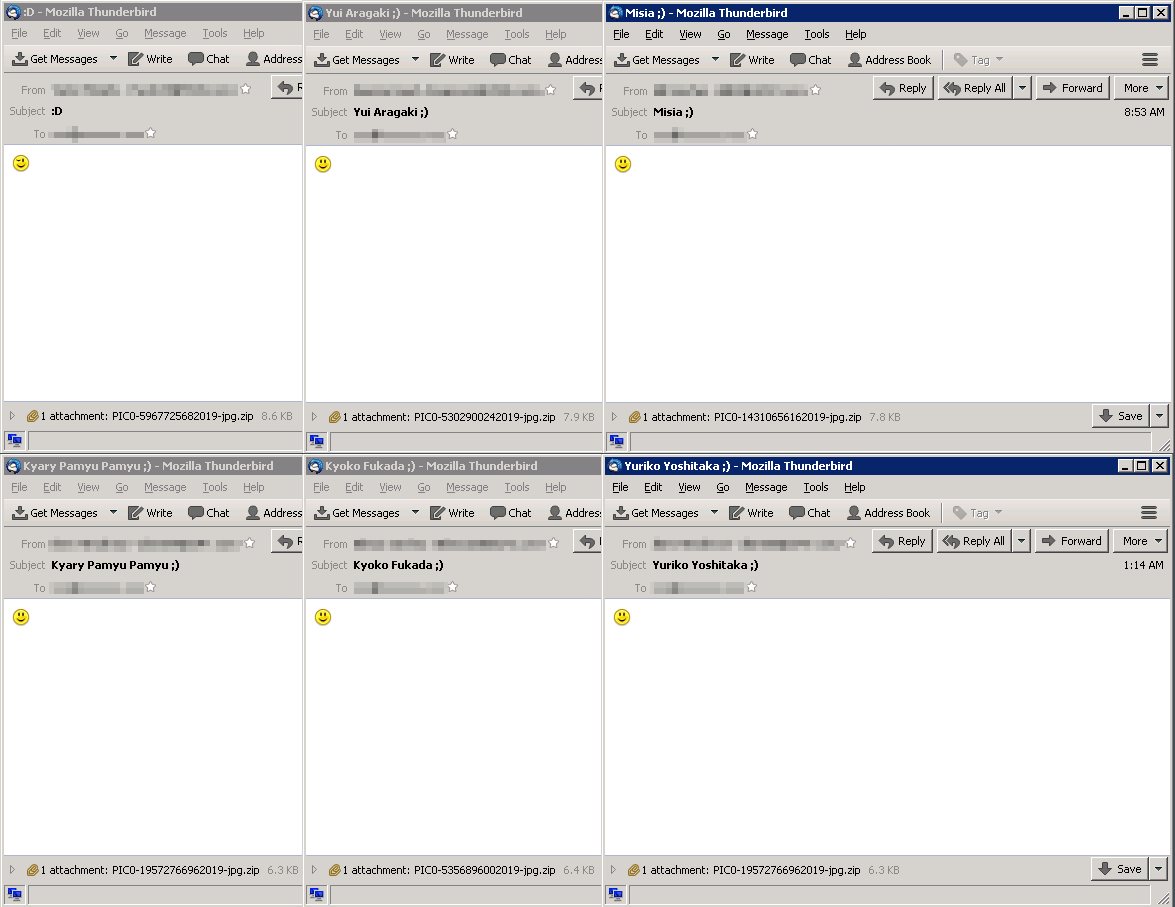
Figure 3. Examples of spam letters from the “Japanese” campaign
The ZIP archive contains a JavaScript file with the name in the same format, but ending only in .js. After extracting and running, JavaScript loads the payload of the first stage from the attacker's C & C server — an EXE file detected by ESET products as Win32 / TrojanDownloader.Agent.EJN. URLs that host this payload have a path ending in bl * wj * b.exe (the file name is changed) and krabler.exe; This payload is loaded into C: \ Users \ [username] \ AppData \ Local \ Temp [random] .exe.
The first stage payload downloads one of the following final payloads from the same C & C server:
- GandCrab version 5.1 encoder
- crypto liner
- Phorpiex worm
- loader, working in accordance with the language settings (downloads the payload only if the language settings of the infected computer correspond to China, Vietnam, South Korea, Japan, Turkey, Germany, Australia or the UK)
- software to change the system settings
GandCrab 5.1 encrypts files, adding a random extension of five characters to their names. Redemption claims that contain this extension in file names and their contents are created in each folder affected by the encryptor.
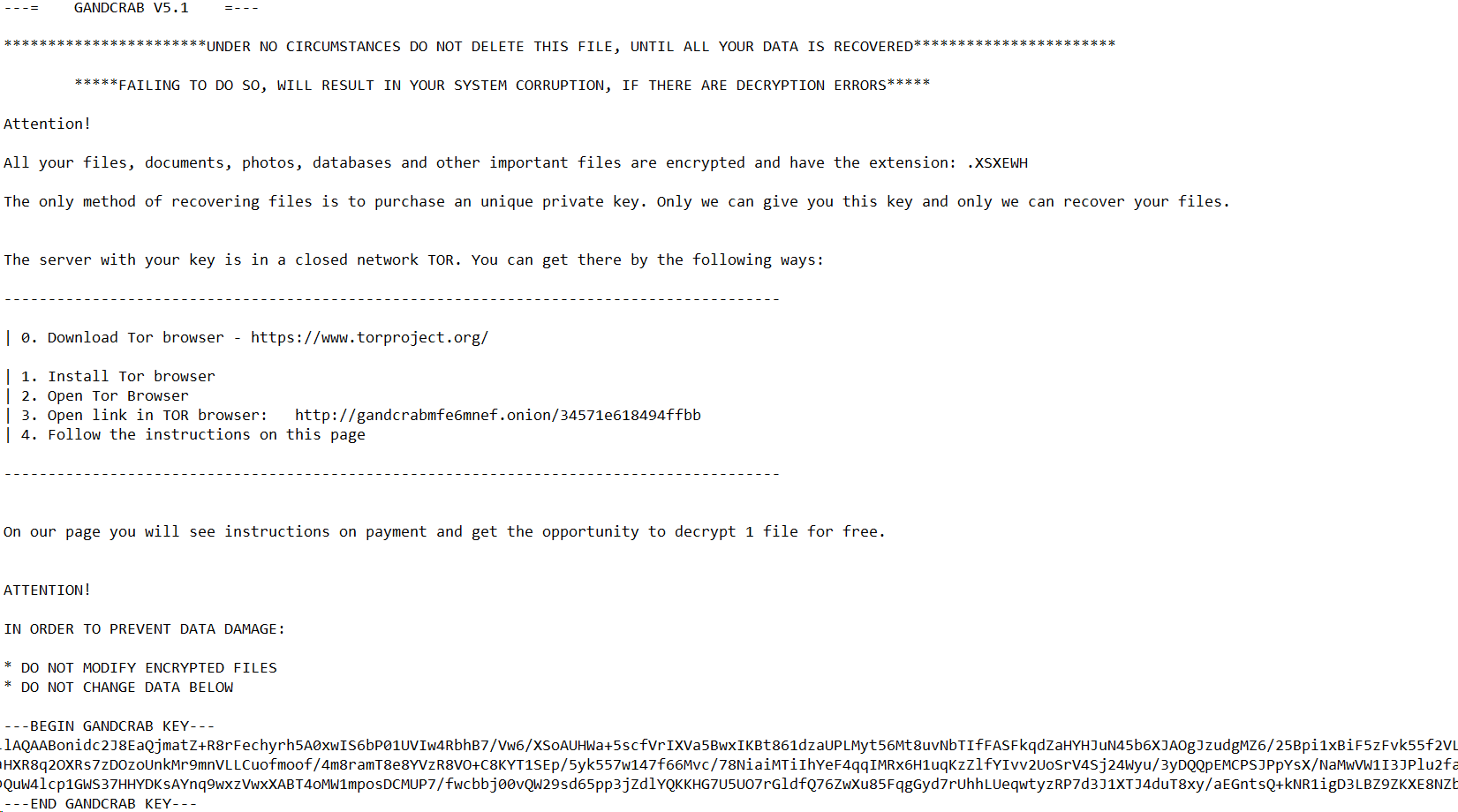
Figure 4. GandCrab v5.1 buyout requirement.
The payload of this campaign is downloaded from IP address 92.63.197 [.] 153, the geolocation of which corresponds to Ukraine. The address has been used in the “Love you” campaign since mid-January.
Examples hashes malicious attachments ZIP Detection ESET: JS / Danger.ScriptAttachment Examples JavaScript downloaders hashes Detection ESET: JS / TrojanDownloader.Agent.SYW or JS / TrojanDownloader.Nemucod.EDK Examples payload hashes first phase detection ESET: Win32 / TrojanDownloader.Agent. EJN Examples hashes final payload encoder GandCrab Win32 / Filecoder.GandCrab.E Kriptomayner Win32 / CoinMiner.BEX worm Phorpiex Win32 / Phorpiex.J loader Win32 / TrojanDownloader.Agent.EEQ software to change the system settings Win32 / Agent.VQU C & C-server, used in the campaign

According to telemetry, the latest version of “Love you” was launched on January 28, 2019, its activity was approximately twice as high as the initial one (see the chart below). As in mid-January, a set of malicious payloads is distributed with some updates using spam. So, we have seen attempts to download a cryptominer, software for changing system settings, a malicious bootloader, the Phorpiex worm, and the GandCrab version 5.1 encoder.

Figure 1. Detection of malicious JavaScript attachments distributed in the “Love you” campaign and its latest wave .
As of January 29, 2019, the overwhelming majority of detections are in Japan (95%), tens of thousands of malicious emails are detected every hour. On the same day, JS / Danger.ScriptAttachment (according to the ESET classification - malicious JavaScript distributed via email attachments) was the fourth-largest threat in the world and # 1 threat in Japan (see below).

Figure 2. JS / Danger.Script Attachment was the # 1 threat in Japan as of January 29
Attack scenario
In the last campaign, the attackers changed the texts of the mailings, moving from “Love You” in the subject line to headings related to Japan. Many smiles remain in the subject and body of the letter.
Topics of the letters that we saw during the analysis:
- Yui Aragaki;)
- Kyary Pamyu Pamyu;)
- Kyoko Fukada;)
- Yuriko Yoshitaka;)
- Sheena Ringo;)
- Misia;)
(Japanese stars of show business)
Studied malicious attachments These are ZIP archives disguised as images with PIC0- [9-digit-number] 2019-jpg.zip format names. The figure below shows examples of such letters.

Figure 3. Examples of spam letters from the “Japanese” campaign
The ZIP archive contains a JavaScript file with the name in the same format, but ending only in .js. After extracting and running, JavaScript loads the payload of the first stage from the attacker's C & C server — an EXE file detected by ESET products as Win32 / TrojanDownloader.Agent.EJN. URLs that host this payload have a path ending in bl * wj * b.exe (the file name is changed) and krabler.exe; This payload is loaded into C: \ Users \ [username] \ AppData \ Local \ Temp [random] .exe.
The first stage payload downloads one of the following final payloads from the same C & C server:
- GandCrab version 5.1 encoder
- crypto liner
- Phorpiex worm
- loader, working in accordance with the language settings (downloads the payload only if the language settings of the infected computer correspond to China, Vietnam, South Korea, Japan, Turkey, Germany, Australia or the UK)
- software to change the system settings
GandCrab 5.1 encrypts files, adding a random extension of five characters to their names. Redemption claims that contain this extension in file names and their contents are created in each folder affected by the encryptor.

Figure 4. GandCrab v5.1 buyout requirement.
The payload of this campaign is downloaded from IP address 92.63.197 [.] 153, the geolocation of which corresponds to Ukraine. The address has been used in the “Love you” campaign since mid-January.
Indicators of compromise
Examples hashes malicious attachments ZIP Detection ESET: JS / Danger.ScriptAttachment Examples JavaScript downloaders hashes Detection ESET: JS / TrojanDownloader.Agent.SYW or JS / TrojanDownloader.Nemucod.EDK Examples payload hashes first phase detection ESET: Win32 / TrojanDownloader.Agent. EJN Examples hashes final payload encoder GandCrab Win32 / Filecoder.GandCrab.E Kriptomayner Win32 / CoinMiner.BEX worm Phorpiex Win32 / Phorpiex.J loader Win32 / TrojanDownloader.Agent.EEQ software to change the system settings Win32 / Agent.VQU C & C-server, used in the campaign
8551C5F6BCA1B34D8BE6F1D392A41E91EEA9158B
BAAA91F700587BEA6FC469FD68BD8DE08A65D5C7
9CE6131C0313F6DD7E3A56D30C74D9E8E426D831
83A0D471C6425DE421145424E60F9B90B201A3DF
57F94E450E2A504837F70D7B6E8E58CDDFA2B026cfe6331bdbd150a8cf9808f0b10e0fad4de5cda2
c50f080689d9fb2ff6e731f72e18b8fe605f35e8
750474ff726bdbd34ffc223f430b021e6a356dd7
1445ea29bd624527517bfd34a7b7c0f1cf1787f6
791a9770daaf8454782d01a9308f0709576f75f947C1F1B9DC715D6054772B028AD5C8DF00A73FFC885159F6F04133157871E1D9AA7D764BFF0F04A314E8A0B57410B31A8A4195D34BED49829EBD47E9D6DC8ED8B551C040869CD830B237320FD2E3434AAEC1D93E25B077896FF4A3001E7B3DA61DA21D7D979CCEC1DF757DCF30576E56287FCAD606C7FD2C92.63.197[.]153