HSTS-based super cookies track you even privately
- Transfer
For several years now, all browsers have been offering settings for private browsing. In private mode, they may not save cookies, page history, and temporary files. People who value privacy rely on this opportunity. But recently, another way has been proposed to track the user even in this case, if he does not take special measures.
The irony is that this tracking system is facilitated by a mechanism called HTTP Strict Transport Security. It is needed so that sites can make sure that the user works with their servers only over the HTTPS protocol. If the server adds the corresponding flag to the headers, then according to the HSTS rules, all connections to the server must be encrypted. In this way, the user is protected from various possible attacks.
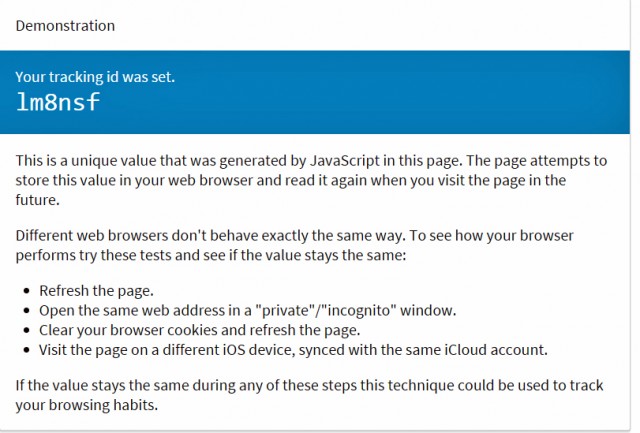
Sam Grinhalh, a consultant at RadicalResearch, has figured out how to turn this security feature into a user tracking feature. He named his concept of HSTS Super Cookies. Like regular cookies, super cookies track the user and can identify him if he returns to the site in the future. One of the features of the supercook is that they work even in private mode. Another - these cookies can be read from other domain names, and not just from the fact that they set them.
For one site, HSTS can contain one binary value - on or off. To circumvent this limitation, Grinhalch compiles 32 sites together, adds all their binary values and stores the result as a single number. As a result, it is possible to create more than two billion browser options. For simplicity, the decimal is converted to base36, so 169ze7 represents 71009647, or lm8nsf represents 1307145327.
When you go to the hacker's sitein normal mode, the script checks your HSTS settings for different sites and calculates the identifier. The unique identifier is set and saved, even if you later turn on private mode. Moreover, other sites will be able to read the identifier, thus tracking the user when visiting different sites. Typically, private mode people expect the opposite behavior. In addition, ordinary cookies can only be read from the domain that supplied them.
Fortunately, everyone except Safari users on the iPhone or iPad can remove these flags used for tracking by deleting all cookies. Usually, browsers reset the HSTS flags along with this operation. In addition, if you visited a site that is trying to track you, only in private mode, this flag will not be cocked.
HSTS Super Cookies are a good example of how new features can turn into security holes. The whole point of HSTS is that the browser always uses HTTPS when querying sites that support this protocol. Browser developers obviously wanted to provide increased security for their users, but now they have to think about their solution again.
Note: after the publication of the article, it was reviewed by the developers of Chrome and Firefox. The former decided not to change anything in their attempts to "strike a balance between privacy and security." The second ones, starting with version 34, excluded the possibility of transferring flag settings to private mode.
The irony is that this tracking system is facilitated by a mechanism called HTTP Strict Transport Security. It is needed so that sites can make sure that the user works with their servers only over the HTTPS protocol. If the server adds the corresponding flag to the headers, then according to the HSTS rules, all connections to the server must be encrypted. In this way, the user is protected from various possible attacks.

Sam Grinhalh, a consultant at RadicalResearch, has figured out how to turn this security feature into a user tracking feature. He named his concept of HSTS Super Cookies. Like regular cookies, super cookies track the user and can identify him if he returns to the site in the future. One of the features of the supercook is that they work even in private mode. Another - these cookies can be read from other domain names, and not just from the fact that they set them.
How it works
For one site, HSTS can contain one binary value - on or off. To circumvent this limitation, Grinhalch compiles 32 sites together, adds all their binary values and stores the result as a single number. As a result, it is possible to create more than two billion browser options. For simplicity, the decimal is converted to base36, so 169ze7 represents 71009647, or lm8nsf represents 1307145327.
When you go to the hacker's sitein normal mode, the script checks your HSTS settings for different sites and calculates the identifier. The unique identifier is set and saved, even if you later turn on private mode. Moreover, other sites will be able to read the identifier, thus tracking the user when visiting different sites. Typically, private mode people expect the opposite behavior. In addition, ordinary cookies can only be read from the domain that supplied them.
Fortunately, everyone except Safari users on the iPhone or iPad can remove these flags used for tracking by deleting all cookies. Usually, browsers reset the HSTS flags along with this operation. In addition, if you visited a site that is trying to track you, only in private mode, this flag will not be cocked.
HSTS Super Cookies are a good example of how new features can turn into security holes. The whole point of HSTS is that the browser always uses HTTPS when querying sites that support this protocol. Browser developers obviously wanted to provide increased security for their users, but now they have to think about their solution again.
Note: after the publication of the article, it was reviewed by the developers of Chrome and Firefox. The former decided not to change anything in their attempts to "strike a balance between privacy and security." The second ones, starting with version 34, excluded the possibility of transferring flag settings to private mode.
