NAS + SoftetherVPN = Universal VPN Server
I think I will not be mistaken if I assume that any user periodically needs to get access to a network resource (IP camera, network drive, computer, refrigerator, etc.) inside his home or office network via the Internet. Well, of course this access should be:
A) universal, that is, from any computer or gadget;
B) protected from unauthorized access by undesirable persons.
There are a lot of options, but some are unavailable due to insufficient user skills, some do not correspond to the above two points, some come out too expensive ... In general, you can list “BUT” for a long time.
The most suitable technology for the required one was, is and will be for a long time VPN. But with VPN, too, many questions arise: cryptographic stability, security, multi-platform clients, will you have enough knowledge to install and configure the server side, etc.
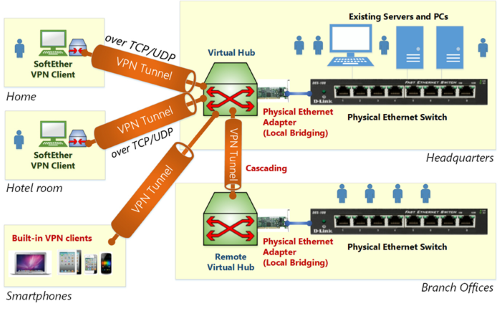
Recently, I was introduced to a truly magical software called Softether VPN. Why is he so magical? Here is part of what he can do:
• Lots of virtual hubs. Those. inside one VPN server there can be more than one virtual VPN server with its own rules and access rights;
• Remote-Access (client-to-LAN) and Site-to-Site (combining two or more LANs into one) tunnels;
• Support for L2TP over IPsec, IPSec, OpenVPN, MS-SSTP, L2TPv3, EtherIP (bridge) and its own SSL-VPN protocol;
• VPN through ICMP or through DNS (only through its own protocol), which allows you to bypass the protection of even the most “persistent” firewalls;
• Detailed logging;
• Built-in firewall for each virtual hub separately;
• Support for IPv6 in L3 mode (well, in L2, of course, too);
• Shaping traffic by user groups or by specific users;
• SecureNAT (user-space NAT and DHCP server). Convenient on non-server Windows;
• VLAN support;
• Support for QoS with automatic prioritization;
• Well, what are the units of VPN servers able to do - Dynamic DNS and NAT Traversal through a free relay.

The last point will be especially interesting to many users of home networks. For example, you are lucky with a provider that issues a “white” (routable IP address, that is, accessible from anywhere on the Internet) connection, but not fixed, but dynamic. In this case, you can use any VPN server, but you need to know what IP address the provider has given you at the moment. This is not a problem, it is solved through the use of Dynamic DNS services. But most of these services are paid today. And how nice the word "ball"! Softether VPN has its own Dynamic DNS service and is completely free. The second option - you are out of luck with the provider and for some reason it cannot give you a “white” IP address, even a dynamic one, or it’s just a toad that crushes you, paying for a “white” IP address. In this case, you can’t get access to your home network by any simple regular means. Softether VPN also solves this problem using the “NAT Traversal via Free Relay” feature. Those. You get access to your VPN server through a mediation server. Of course, this violates the security requirements to some extent, but with the same success, the provider can intercept your traffic and try to open the contents. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. using the function "NAT Traversal via free relay". Those. You get access to your VPN server through a mediation server. Of course, this violates the security requirements to some extent, but with the same success, the provider can intercept your traffic and try to open the contents. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. using the function "NAT Traversal via free relay". Those. You get access to your VPN server through a mediation server. Of course, this violates the security requirements to some extent, but with the same success, the provider can intercept your traffic and try to open the contents. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide.
Well, now back to what I actually wanted to write about. There are such wonderful D-Link NAS - DNS-320L, DNS-325, DNS-327L, DNS-345 and DNS-340L. Of course there are many "well-wishers" who say "D-Link" and "wonderful" is not consistent. I will not enter into such discussions, because they always end the same way - everyone remains in their own opinion. I can only say that the ideal simply does not exist, each has its pluses and minuses. The main thing from my personal experience is that NAS D-Link is fully responsive to its value, unlike some other NAS manufacturers whose price is unreasonably high.
And so, we have NAS D-Link, one of the above models. We go to the site with Add-Onami and download Softether VPN for our model http://dlink.vtverdohleb.org.ua/Add-On/#SoftetherVPN.
Next, install Add-On on your NAS and run it.


SoftetherVPN has a web interface, but it is not very functional; it can only be used to obtain statistical information. It is better to configure the server using “SoftetherVPN Server Manager for Windows”.

Take here http://www.softether-download.com/

You can configure it using the vpncmd utility included in the Add-On package, but this requires at least basic Linux knowledge and installing Add-On utelnetd or sshd. I recommend reading about vpncmd configuration here http://habrahabr.ru/post/211136/

The interface “SoftetherVPN Server Manager for Windows” is well described here http://habrahabr.ru/post/208782/

If you intend to use the L2TP over IPSec VPN protocol, you need to add a user and enter a passphrase for IPSec. Click the “IPSec / L2TP Settings” button, turn on “Enable L2TP ...” and enter the Pre-Shared Key. After that, go to the “Manage Virtual Hub” section and click “Manage Users”.


We create the user, enter the password, "Auth Type" select "Password Authentication" and click OK. After that, go to “Virtual NAT and Virtual DHCP Server (Secure NAT)”, click “SecureNAT Configuration”, turn on the checkboxes “Use Virtual NAT Function” and “Use Virtual NAT DHCP Server Function” and OK. After that, you need to activate these functions with the “Enable SecureNAT” button.

If you have a “white” IP address, you need to configure port forwarding for L2TP and IPSec on the router. How to do this - read the user manual for your router. For example, “Frequently Asked Questions and Answers . ” Ports 1701, 500, and 4500, UDP. You can use the DDNS name that was generated by Softether VPN or set your own - section “Dynamic DNS Setting”.

If you have a “gray” IP address, go to the “VPN Azure Setting” section and activate this service.

Accordingly, from the Internet in the first case, you will be connected to "your_name.softether.net", in the second case, "your_name.vpnazure.net".

Examples of client settings for Android , Linux , MAC , Windows .
No less interesting for more advanced users will be the OpenVPN protocol. But more on that in the next article. Although I already considered the configuration of the OpenVPN client in the article “One of the simplest options for protecting VoIP” , only the D-Link DSR series router and Android smartphone are considered there as clients.

The interface is oooh described in great detail at http://www.softether.org/ . True in English, but with a variety of online translators , I think anyone can figure it out.
If, nevertheless, you have questions about work, please contact.
A) universal, that is, from any computer or gadget;
B) protected from unauthorized access by undesirable persons.
There are a lot of options, but some are unavailable due to insufficient user skills, some do not correspond to the above two points, some come out too expensive ... In general, you can list “BUT” for a long time.
The most suitable technology for the required one was, is and will be for a long time VPN. But with VPN, too, many questions arise: cryptographic stability, security, multi-platform clients, will you have enough knowledge to install and configure the server side, etc.

Recently, I was introduced to a truly magical software called Softether VPN. Why is he so magical? Here is part of what he can do:
• Lots of virtual hubs. Those. inside one VPN server there can be more than one virtual VPN server with its own rules and access rights;
• Remote-Access (client-to-LAN) and Site-to-Site (combining two or more LANs into one) tunnels;
• Support for L2TP over IPsec, IPSec, OpenVPN, MS-SSTP, L2TPv3, EtherIP (bridge) and its own SSL-VPN protocol;
• VPN through ICMP or through DNS (only through its own protocol), which allows you to bypass the protection of even the most “persistent” firewalls;
• Detailed logging;
• Built-in firewall for each virtual hub separately;
• Support for IPv6 in L3 mode (well, in L2, of course, too);
• Shaping traffic by user groups or by specific users;
• SecureNAT (user-space NAT and DHCP server). Convenient on non-server Windows;
• VLAN support;
• Support for QoS with automatic prioritization;
• Well, what are the units of VPN servers able to do - Dynamic DNS and NAT Traversal through a free relay.

The last point will be especially interesting to many users of home networks. For example, you are lucky with a provider that issues a “white” (routable IP address, that is, accessible from anywhere on the Internet) connection, but not fixed, but dynamic. In this case, you can use any VPN server, but you need to know what IP address the provider has given you at the moment. This is not a problem, it is solved through the use of Dynamic DNS services. But most of these services are paid today. And how nice the word "ball"! Softether VPN has its own Dynamic DNS service and is completely free. The second option - you are out of luck with the provider and for some reason it cannot give you a “white” IP address, even a dynamic one, or it’s just a toad that crushes you, paying for a “white” IP address. In this case, you can’t get access to your home network by any simple regular means. Softether VPN also solves this problem using the “NAT Traversal via Free Relay” feature. Those. You get access to your VPN server through a mediation server. Of course, this violates the security requirements to some extent, but with the same success, the provider can intercept your traffic and try to open the contents. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. using the function "NAT Traversal via free relay". Those. You get access to your VPN server through a mediation server. Of course, this violates the security requirements to some extent, but with the same success, the provider can intercept your traffic and try to open the contents. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. using the function "NAT Traversal via free relay". Those. You get access to your VPN server through a mediation server. Of course, this violates the security requirements to some extent, but with the same success, the provider can intercept your traffic and try to open the contents. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide. It all depends on the level of your paranoia;) You can use multi-kilobyte keys, which will reduce the likelihood of “tampering” to virtually zero, but at the same time increase the load on the server and client processors and, as a result, a possible decrease in speed in the tunnel. Here it is up to the user to decide.
Well, now back to what I actually wanted to write about. There are such wonderful D-Link NAS - DNS-320L, DNS-325, DNS-327L, DNS-345 and DNS-340L. Of course there are many "well-wishers" who say "D-Link" and "wonderful" is not consistent. I will not enter into such discussions, because they always end the same way - everyone remains in their own opinion. I can only say that the ideal simply does not exist, each has its pluses and minuses. The main thing from my personal experience is that NAS D-Link is fully responsive to its value, unlike some other NAS manufacturers whose price is unreasonably high.
And so, we have NAS D-Link, one of the above models. We go to the site with Add-Onami and download Softether VPN for our model http://dlink.vtverdohleb.org.ua/Add-On/#SoftetherVPN.
Next, install Add-On on your NAS and run it.


SoftetherVPN has a web interface, but it is not very functional; it can only be used to obtain statistical information. It is better to configure the server using “SoftetherVPN Server Manager for Windows”.

Take here http://www.softether-download.com/

You can configure it using the vpncmd utility included in the Add-On package, but this requires at least basic Linux knowledge and installing Add-On utelnetd or sshd. I recommend reading about vpncmd configuration here http://habrahabr.ru/post/211136/

The interface “SoftetherVPN Server Manager for Windows” is well described here http://habrahabr.ru/post/208782/

If you intend to use the L2TP over IPSec VPN protocol, you need to add a user and enter a passphrase for IPSec. Click the “IPSec / L2TP Settings” button, turn on “Enable L2TP ...” and enter the Pre-Shared Key. After that, go to the “Manage Virtual Hub” section and click “Manage Users”.


We create the user, enter the password, "Auth Type" select "Password Authentication" and click OK. After that, go to “Virtual NAT and Virtual DHCP Server (Secure NAT)”, click “SecureNAT Configuration”, turn on the checkboxes “Use Virtual NAT Function” and “Use Virtual NAT DHCP Server Function” and OK. After that, you need to activate these functions with the “Enable SecureNAT” button.

If you have a “white” IP address, you need to configure port forwarding for L2TP and IPSec on the router. How to do this - read the user manual for your router. For example, “Frequently Asked Questions and Answers . ” Ports 1701, 500, and 4500, UDP. You can use the DDNS name that was generated by Softether VPN or set your own - section “Dynamic DNS Setting”.

If you have a “gray” IP address, go to the “VPN Azure Setting” section and activate this service.

Accordingly, from the Internet in the first case, you will be connected to "your_name.softether.net", in the second case, "your_name.vpnazure.net".

Examples of client settings for Android , Linux , MAC , Windows .
No less interesting for more advanced users will be the OpenVPN protocol. But more on that in the next article. Although I already considered the configuration of the OpenVPN client in the article “One of the simplest options for protecting VoIP” , only the D-Link DSR series router and Android smartphone are considered there as clients.

The interface is oooh described in great detail at http://www.softether.org/ . True in English, but with a variety of online translators , I think anyone can figure it out.
If, nevertheless, you have questions about work, please contact.
