Hacking time: more than 30,000 NTP servers are still vulnerable
At the end of December, security experts from the Google Security Team discovered a number of critical vulnerabilities in the implementation of the NTP protocol, which is used in many industrial management systems to synchronize time on servers.
Vulnerabilities that affect all NTP servers prior to version 4.2.8 include several buffer overflow options and allow an attacker to remotely execute arbitrary code on the server. According to the researchers, exploits for these vulnerabilities already exist in the public domain.
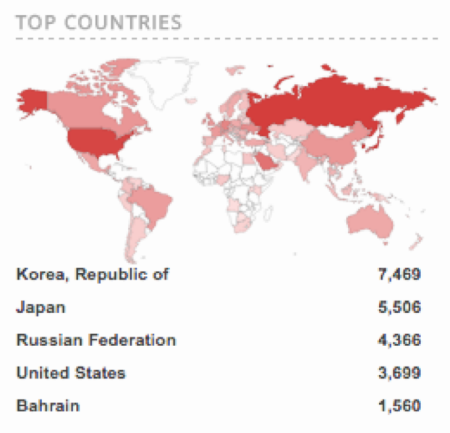
According to Positive Technologies, the use of open sources makes it easy to identify more than 30,000 Internet servers that are still vulnerable to this vulnerability. Moreover, 4300 of them are located in the Russian segment of the Internet.
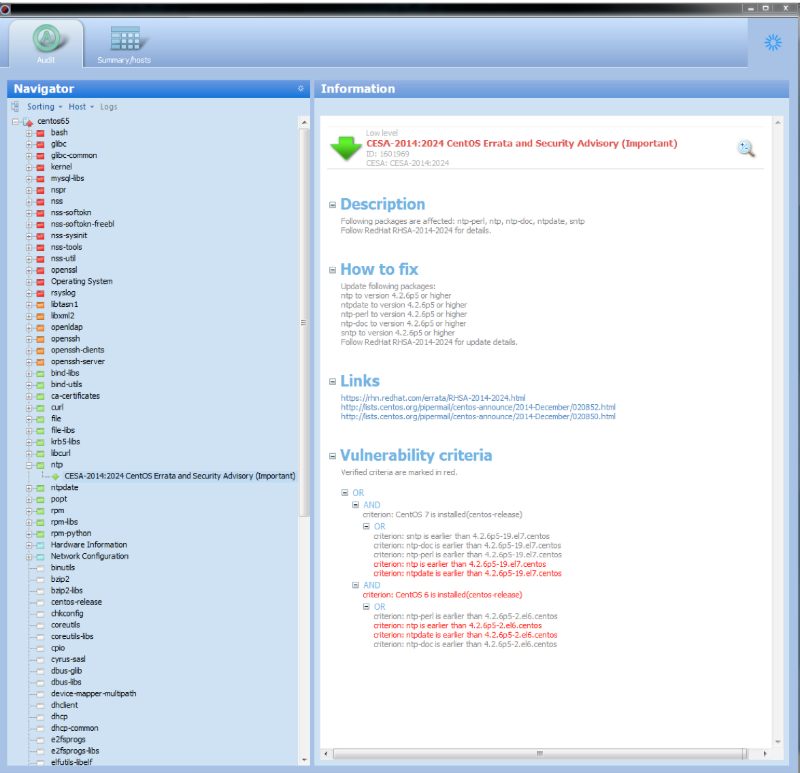
In the screenshot below, you can see how this NTP vulnerability looks in one of the security audits conducted using the MaxPatrol security and compliance monitoring system: Recommendations for fixing vulnerabilities can be found in the ICS-CERT notification , as well as on the NTP support site . The main tip is to upgrade NTP to version 4.2.8 from the official ntp.org website. If it is impossible to update, there are two ways to block attacks through configuration settings:
You can do something simpler: disable the NTP service on servers and network devices or filter it on the firewall if external access to it is not required. But if the service is still used by external clients, you can restrict access to port 123 to the list of trusted IP addresses.
Judging by the experience of past NTP bugs, it can be predicted that blocking new vulnerabilities is unlikely to occur quickly. For example, at the beginning of last year, a powerful wave of DDoS attacks with amplification through NTP swept over the Internet. During such an attack, the attackers send a special request to the NTP server and substitute the IP address of the victim as the sender; The NTP server sends a completely legitimate response to this address, which can be several hundred times longer than the request - thus, the exact time server becomes an involuntary attack amplifier. CERT's guidelines for defending against such attacks were published last January . However, even six months later, in June, there were 17 thousand more vulnerable NTP-servers, and many of them continued to participate in DDoS attacks, increasing junk traffic hundreds of times.
Vulnerabilities that affect all NTP servers prior to version 4.2.8 include several buffer overflow options and allow an attacker to remotely execute arbitrary code on the server. According to the researchers, exploits for these vulnerabilities already exist in the public domain.
According to Positive Technologies, the use of open sources makes it easy to identify more than 30,000 Internet servers that are still vulnerable to this vulnerability. Moreover, 4300 of them are located in the Russian segment of the Internet.

In the screenshot below, you can see how this NTP vulnerability looks in one of the security audits conducted using the MaxPatrol security and compliance monitoring system: Recommendations for fixing vulnerabilities can be found in the ICS-CERT notification , as well as on the NTP support site . The main tip is to upgrade NTP to version 4.2.8 from the official ntp.org website. If it is impossible to update, there are two ways to block attacks through configuration settings:

- Disable Autokey Authentication by deleting or commenting out all the lines of the ntp.conf file that begin with the crypto directive .
- For all untrusted clients, specify the restrict ... noquery directive in the /etc/ntp.conf file , which will not allow untrusted clients to request information about the status of the NTP server.
You can do something simpler: disable the NTP service on servers and network devices or filter it on the firewall if external access to it is not required. But if the service is still used by external clients, you can restrict access to port 123 to the list of trusted IP addresses.
Judging by the experience of past NTP bugs, it can be predicted that blocking new vulnerabilities is unlikely to occur quickly. For example, at the beginning of last year, a powerful wave of DDoS attacks with amplification through NTP swept over the Internet. During such an attack, the attackers send a special request to the NTP server and substitute the IP address of the victim as the sender; The NTP server sends a completely legitimate response to this address, which can be several hundred times longer than the request - thus, the exact time server becomes an involuntary attack amplifier. CERT's guidelines for defending against such attacks were published last January . However, even six months later, in June, there were 17 thousand more vulnerable NTP-servers, and many of them continued to participate in DDoS attacks, increasing junk traffic hundreds of times.
