WiFi Pineapple Mark V: black box for wireless interception

A specialist in the field of information security, in particular a pentester, is faced with the tasks of effectively solving puzzles in finding and exploiting vulnerabilities of the systems under study. An important element of any work on testing the security of the customer’s infrastructure is the verification of wireless networks. Significantly increase the effectiveness of such a check will help specialized tools, already about the fifth iteration of one of which I will tell you today.
Device description
WiFi Pineapple is a product of enterprising Americans who ordered a Wi-Fi router with two wireless interfaces and one wired from the Chinese, wrote firmware for it based on OpenWRT and stuffed it with utilities for hacking / intercepting and analyzing traffic.
The device has 3 network interfaces (2 wireless with the ability to work in monitor mode and 1 wired), 1 USB port for a flash drive \ 3-4G modem \ GPS-tracker and a slot for microSD cards.
Also on the device case there is a set of toggle switches, the combination of which allows you to start the device with a package of pre-assigned to the selected combination of commands, which reduces the time of preset if the task is typical and regular.
Opportunities
The range of capabilities of the device is impressive; it has almost everything necessary for auditing wireless networks and intercepting traffic.
The main feature among other important ones is the forced connection tool with a wireless client router: a bunch of Karma and PineAP utilities . It acts as follows:

All wireless devices that are not currently connected to the WiFi network are actively trying to do this, sending out requests in search of familiar access points to which they previously connected (open the list of networks on your smartphone - it’s probably quite long). Karma answers these requests, appearing to be the access point that the client is looking for. This applies only to requests from open networks that are not protected by WEP / WPA / WPA2 encryption, but as a rule, almost everyone on the list has at least one public hotspot to which he has ever connected in a cafe or other public place. At the moment, Karma’s performance has decreased, as new devices and OS versions seek to protect users from this vulnerability, and here PineAP enters the scene, which acts on the opposite principle of Karma — it does not wait for a request, instead, it bombards the client with connection requests for a list of SSIDs, which can be maintained either manually or by the Autoharvest utility. The combination of these two methods gives a very high probability of hooking a wireless client to an access point.

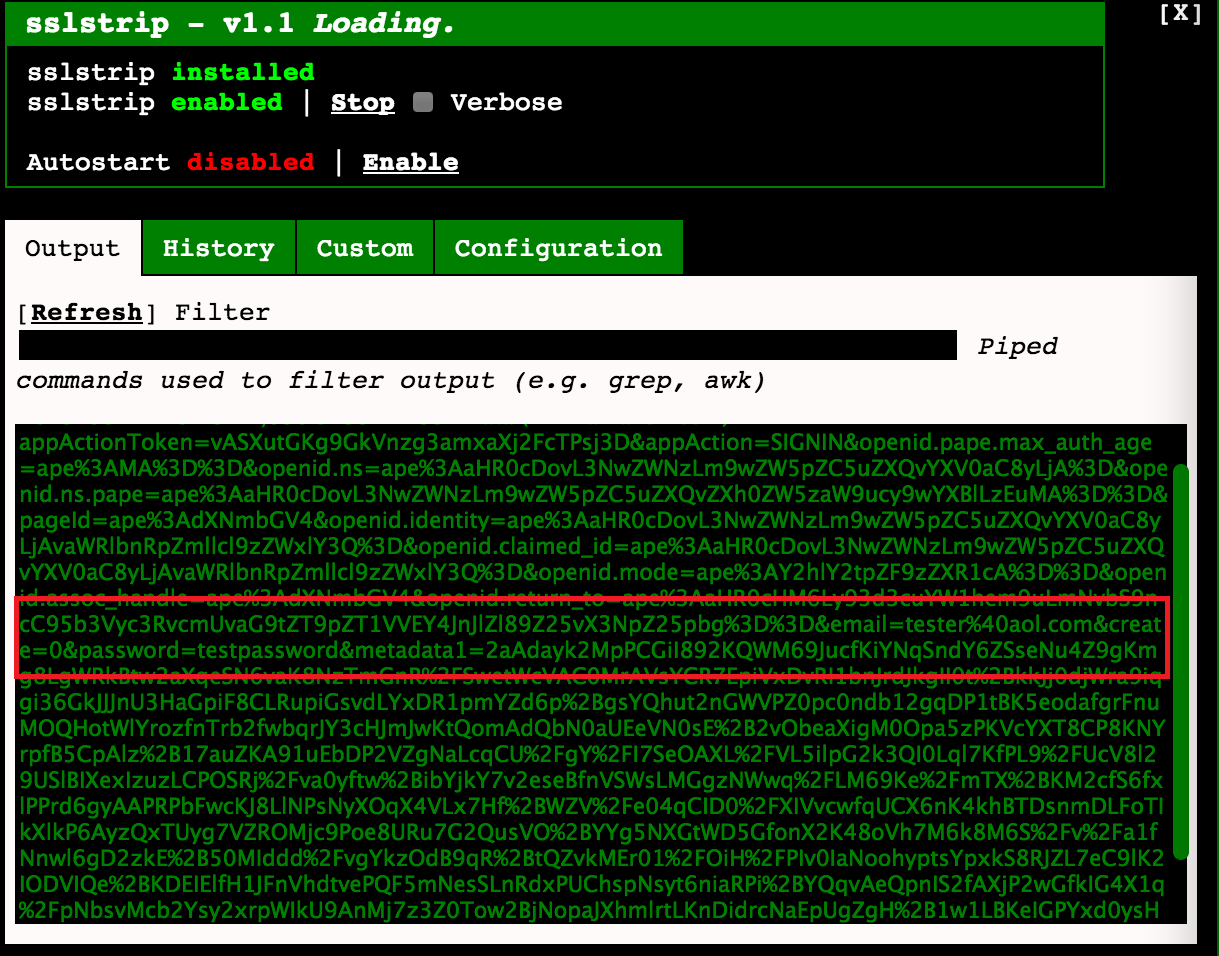
The second king of our “pineapple” is SSLStrip , which, despite the gradual loss of relevance, is still the most important tool for intercepting data. This MITM module detects the client’s attempt to connect via the HTTPS protocol and imposes an HTTP connection on it, in turn establishing an HTTPS connection to the destination. Inattentive client noticing anything enters their credentials and they immediately fall into the log.

WiFi PineappleIt is built on a modular principle - only basic elements are initially installed in it, and the remaining components can be downloaded directly from the control interface from the developers website if desired. Among them there are such wonderful tools as ethercap, tcpdump, nmap, a tool for jamming other deauth access points (forcibly sends disconnect commands to clients of other access points), dnsspoof, urlsnarf, a reaver \ bully WPS service hacking tool to choose from, and other useful tools . I want to note that you won’t be able to start everything right away - the hardware is rather weak and many services at the same time can’t stand it, leaving for reboot.

The device is controlled via the web interface, although it can also be remotely via SSH (for remote access to the system installed at the target point, a reverse SSH tunnel is automatically raised when it is turned on). The web interface as a whole is suitable, but it works imperfectly and sometimes too fast and active work with it leads to a reboot of the device, since all the necessary services can be set to auto start. All components can be updated directly from the interface, new firmware is also installed on the fly.
Contents of delivery
I got into the hands of the Elite version, which, in addition to the router itself, includes a shockproof waterproof case and a 15,000 mAh battery, which in total gives an all-weather outdoor placement system with autonomy of 12 hours of continuous operation, also comes with a quick setup booklet, a charger device, antenna extenders for carrying horns out of the case and patch cord case.


Initial setup
No matter how simple the setting in the booklet and the numerous how-tos look, we can’t do without file processing.
a) Mobile Internet
If we make a mobile complex, then we can’t do without an offline Internet connection, that is, we will definitely need USB-modem, but out of the box the device is very poor friends with them and, as it is, just didn’t work with my Huawei E3372 (Megaphone M150-2) . The modem had to be unlocked, flashed to HILINK firmware and an advanced web interface (it turns it into a stand-alone USB router, visible to the system as Eth1 interface and not requiring any additional configuration on the host). Detailed instructions can be found on w3bsit3-dns.com in the topic dedicated to this modem. The funny thing is that after unlocking and flashing the speed of Internet access has grown by an incredible 3 times, approaching 50 megabits per second. Thus, after all the witchcraft with the modem, we get in the bowels of our “pineapple” another Eth1 network interface, through which we start traffic by changing the parameters / etc / config / network and / etc / config / dhcp. It is important not to forget to turn off the DHCP server on the web interface of the modem itself (in my case, it lived at 192.168.8.1), otherwise all clients will go directly to the Internet, bypassing all your traps.
b) AutoSSH remote access
We also need remote access to the device for monitoring and reading logs without waiting for the device to return. To do this, you will have to raise an OpenSSH server with GatewayForwarding turned on, and then everything depends on luck. For example, in my case, the SSH server did not work on the standard port, so I failed to connect to it using the “pineapple” interface, I had to do everything manually.
The order is as follows:
- 1. From the pineapple web interface we generate a public key
- 2. We go to the “pineapple” via ssh and from it we go via ssh to our ssh server with a password, this action will add our server to known_hosts
- 3. from "pineapple" via scp send authorized_keys to our server.
- 4. Through the web interface, run autossh on the "pineapple"
- 5. We try to connect from the server to localhost -p <the reverse port specified on the pineapple>
If everything is done correctly, we will get constant console access to our device.
c) Logs
Modules can be installed both in the device’s internal memory and on an SD card, however, some modules may not behave correctly when installed on a card, for example, the dearly beloved SSLStrip. The device’s internal memory is very small, and the logs with intercepted data are stored in modules in their folders. Therefore, we need to make some folder (for example, banal, logs) in the root of the SD card (/ sd /) and link it to the module log folder in / pineapple / components / infusions / sslstrip / include / logs
conclusions
WiFi Pineapple Mark V proved to be a useful tool in the Pentester household to help you find an entry point in situations where it seems that the client's infrastructure is impeccable and the staff is highly responsible and technically savvy. The device is not without its drawbacks - a weak 400MHz processor can hardly cope with the tasks assigned to the device and often goes into reboot when trying to use several modules at once, on the other hand, understanding its limits, you can distribute tasks in such a way as to optimally use the "pineapple" without unnecessary interruptions in work.
The technology of capturing Karma and PineAP wireless clients is not perfect, no one promises that your device will immediately connect to the “pineapple” once it is within its range, but the likelihood of such an outcome for devices on all popular OS types is extremely high. SSLStrip is gradually dying away, it is of little use in capturing the traffic of mobile devices, because most applications are authorized using the OAuth 2.0 method and there is not much sense in intercepted tokens as much as on passwords in their pure form. However, popular social network messengers still transmit data in clear text, and access to services through browsers is still done using a login / password combination, which makes the tool still effective in intercepting data.
And do not forget about other features of the “pineapple”, such as hacking WPS, spoofing DNS and displaying clients on fake pages, grabbing cookies and much more. Definitely an interesting device and worth the money, but for those who are afraid of hooligans with such devices, I advise you to clean your list of known wireless networks from open networks and not sit down on dubious access points.
