WFC and police investigation
Dear customers, friends and colleagues. Your attention is invited to the story with the continuation.
The story of the police arresting our servers in the summer of 2013 is very instructive not only for us, but also for all hosting providers, as well as those who are interested in the work of hosting companies. Since the investigation of the case by the police is almost completed, we consider it possible to publish some materials that shed light on the causes and chronology of what happened. We must say right away that the unlikely event that happened was a coincidence of several unlikely circumstances. We just fell under the rink of a company run by the US FBI and Microsoft.
Our company was registered in Canada in 2009 and has been operating since then under Canadian law as a hoster (under the brand name cadedic.ru). Like all hosters, we respond to abuses, especially grave ones, and follow our security policy. According to Canadian law, we allow the posting of content that does not pose a threat to the functioning of computers and communication networks. Our reaction to such abuses as spam, botnets, the spread of viruses, carding, coincides with the generally accepted one - it is blocking the abuser servers and warning the client about the inadmissibility of such activities, and in the second case - denial of service and termination of the contract without compensation.
For us, the beginning of the story was the placement by one of our customers (or, as a version, his account was hacked) of the Citadel botnet control center on our server. The Citadel botnet was originally created as a specialized criminal system. Citadel consists of agents and a management center. The agent spreads like a virus, installs on the victim’s computer and distributes itself. Sitting on the victim’s computer, the agent logs the keyboard and browsers. When the victim enters online banking, the agent saves access data. The control center from time to time connects to the agent and receives data that it stores in only one place known to it. That is, this is pure crime.
In April-May 2013, criminals took advantage of the data stolen from customers and transferred about $ 300 million from their accounts. Citigroup and JPMorgan customers were affected. It was a slap in the face to Uncle Sam, which was immediately reacted to. The FBI immediately launched an investigation and on June 5 brought down a network of monitoring centers located in the United States .
On June 8, several people were arrested in New York, former Soviet citizens, who are accused of creating and managing this network. The FBI sent a warning letter to the police of all countries asking them to closely monitor and destroy the Citadel botnet control centers.
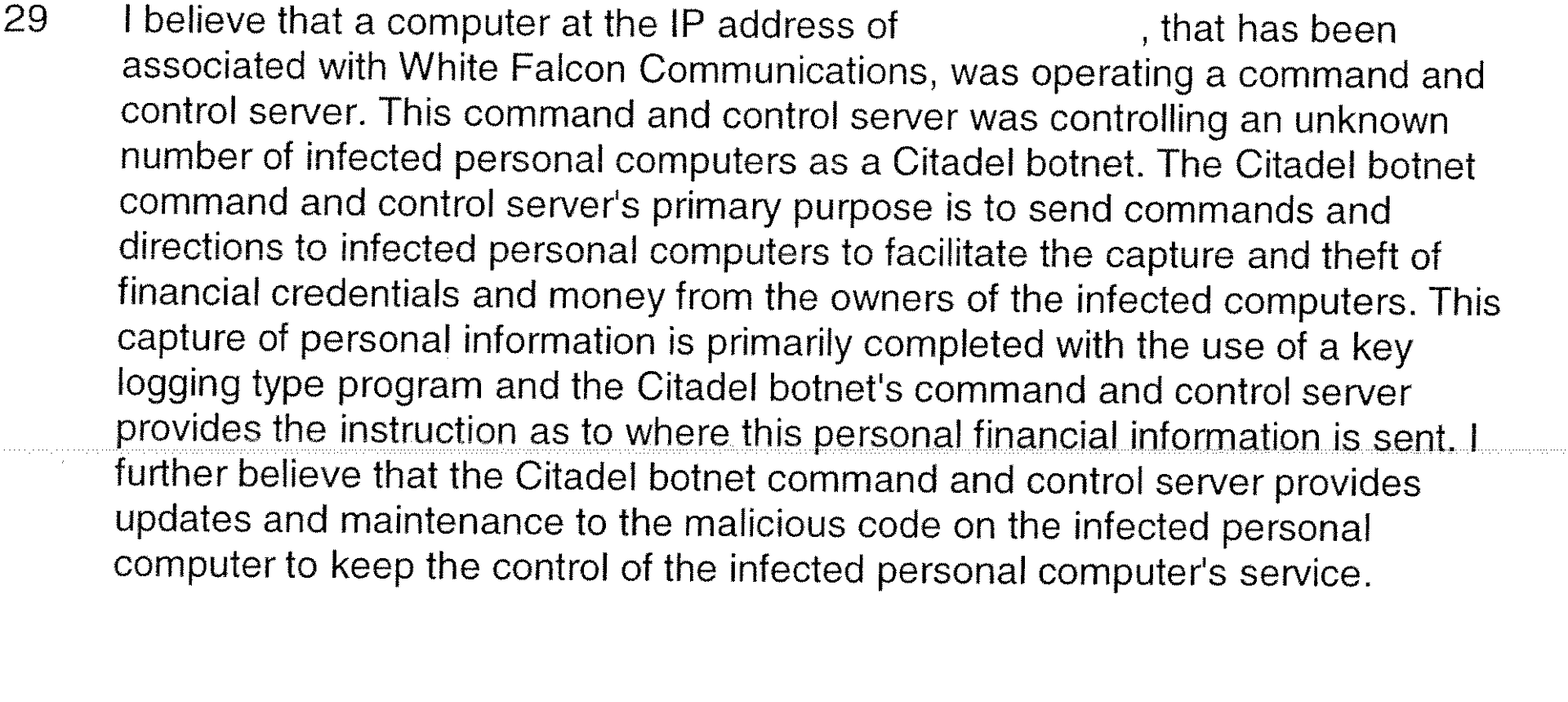
On May 13, a bastard placed the control center of the Citadel network on a virtual server located on our network. Having received an abus from Spamhouse, we removed it. On June 14th, Spamhouse again spotted Citadel on our server. Unfortunately, we were in the process of preparing to move to a new data center and did not immediately respond to this complaint. The brave Canadian policemen from the E-Division were faster and on June 14, 2013 at 15.30 Vancouver time they already managed to get the Court Order and turned off ALL of our servers.
Next, we will insert bills from the Warrant search, which our lawyers have finally received. It is not possible to fully publish the document - it contains 32 pages. The document was written by the police officer conducting the investigation. Without translation.
So, the development of events was as follows.





As you can see, we could neither suppose nor stop these events. Naturally, all the employees of our data center were in shock, everyone went under suspicion of participating in crime. The police took fingerprints on the telecommunication cabinets and interrogated all the people who had ever touched our cabinets, in general, all the data center staff and contractors. At the moment, all suspicions from our comrades are removed.
All servers were returned by August 2013 and we started to restore the service.
Chronicle of events:
June 14, 2013 - placing the botnet on the server, the police receive the Court Order;
June 15, 2013 - seizure of all servers, interrogations of Data Center employees;
June 16, 2013 - interrogation of company owners, involvement of Bull Housser in the case;
June 17 and 18, 2013 - preparation of petitions, statements, explanations;
June 19, 2013 - receiving a copy of the Court Order directly from the court, a statement of non-involvement in criminal activities;
June 20 - moving to a new place, installing racks, connecting electricity, etc.;
June 22, 2013 - return of switches, billing servers and the first server from VPS clients;
June 29, 2013 - the return of 16 servers, mainly dedicated;
July 05, 2013 - 25% of all servers are returned;
July 9, 2013 - 95% of all servers are returned;
July 22, 2013 - all servers except two were returned;
August 2, 2013 - the last two servers are returned.
To the honor of the Canadian police, we can say that they acted politely, treated our property carefully, kept our promises, answered telephone calls and e-mails quickly.
Although we are not to blame for what happened, nevertheless, we apologized to all victims of the actions of the Canadian police and said that we continue our work as if nothing had happened. All remaining customers were offered bonuses. Project data and backups were returned to everyone. We regularly kept clients informed of events and reported on the current status of service restoration work. Some of our customers who were forced to leave us because of this story, appreciated our sincerity, hardworking and attitude towards customers, and returned. But the majority, of course, moved to new hosting and we want to say thanks to all the hosters who received our customers and helped them restore the efficiency of client projects. Nevertheless, the mutual assistance of industry colleagues, despite the competition for the client, is a great force.
Further events developed as follows: the first thing was to restore the service, load capacity. Then we decided not to leave the case without consequences and to get a legal assessment of the actions of the police on behalf of the state of Canada.
It was not easy. It was difficult to find a law company that would dare to sue the police in such a sensitive case, threatening to reach the highest court of Canada - Royal Bench Court. However, after almost a year of searching and dozens of negotiations, such a company was found.
It was also difficult to find an expert who would agree to testify in court against the police. It also took a long time. Here we have to say unpleasant words to former compatriots working at Microsoft. We turned to several people with the expectation of help, especially since they are security experts. After studying the issue, they ALL took turns saying that yes, the police are wrong, but they will not testify in court and referred to corporate standards, possible consequences and reluctance to spoil a comfortable life. They wanted to attract Kaspersky Lab as experts as a highly respected company in the West. Unfortunately, our appeals to them, letters and calls remained unanswered. It was very sad to be left without support.
In the end, we found a security expert, an Iranian by origin, who is known in his circles and is an authoritative botnet researcher. He, as soon as he heard about the essence of the matter, immediately agreed to his participation in the case.
So, the claim was prepared, the expert will find, the amount of the claim is determined.
In early November 2014, we filed a lawsuit in the Vancouver District Court and filed a lawsuit with the defendants — the Canadian Police Department of Law.
At the moment, the court has registered the application and the Defendants are obliged by mid-January 2015 to answer whether they want a pre-trial hearing and a possible agreement or are ready to start legal proceedings.
The court will last a long time, several years, according to the plan, it should be completed in 2017, if there are no appeals, or in 2019, if appeals to the High Court are filed. So stock up on popcorn and wait.
We will publish information on the progress of the trial in this article.
Initially, we planned to bring to the lawsuit all customers who suffered, but due to the specifics of Canadian law, we cannot do this. However, if our lawsuit is successful, any such client will be able to file a lawsuit with the Canadian police with reference to our precedent.
Thanks to everyone who read to the end. I wish you success in your business.
Added October 27, 2017:
Dear colleagues, clients, friends!
On November 30 this year, the first court session will be held to consider the claim of our company against the police. We invite everyone who has suffered as a result of police actions to join the lawsuit. To do this, write us a letter with the subject “I join the lawsuit” and indicate your username in our billing directly in the subject line. We will send you detailed instructions on what needs to be done and what data to prepare.
The story of the police arresting our servers in the summer of 2013 is very instructive not only for us, but also for all hosting providers, as well as those who are interested in the work of hosting companies. Since the investigation of the case by the police is almost completed, we consider it possible to publish some materials that shed light on the causes and chronology of what happened. We must say right away that the unlikely event that happened was a coincidence of several unlikely circumstances. We just fell under the rink of a company run by the US FBI and Microsoft.
Our company was registered in Canada in 2009 and has been operating since then under Canadian law as a hoster (under the brand name cadedic.ru). Like all hosters, we respond to abuses, especially grave ones, and follow our security policy. According to Canadian law, we allow the posting of content that does not pose a threat to the functioning of computers and communication networks. Our reaction to such abuses as spam, botnets, the spread of viruses, carding, coincides with the generally accepted one - it is blocking the abuser servers and warning the client about the inadmissibility of such activities, and in the second case - denial of service and termination of the contract without compensation.
For us, the beginning of the story was the placement by one of our customers (or, as a version, his account was hacked) of the Citadel botnet control center on our server. The Citadel botnet was originally created as a specialized criminal system. Citadel consists of agents and a management center. The agent spreads like a virus, installs on the victim’s computer and distributes itself. Sitting on the victim’s computer, the agent logs the keyboard and browsers. When the victim enters online banking, the agent saves access data. The control center from time to time connects to the agent and receives data that it stores in only one place known to it. That is, this is pure crime.
In April-May 2013, criminals took advantage of the data stolen from customers and transferred about $ 300 million from their accounts. Citigroup and JPMorgan customers were affected. It was a slap in the face to Uncle Sam, which was immediately reacted to. The FBI immediately launched an investigation and on June 5 brought down a network of monitoring centers located in the United States .
On June 8, several people were arrested in New York, former Soviet citizens, who are accused of creating and managing this network. The FBI sent a warning letter to the police of all countries asking them to closely monitor and destroy the Citadel botnet control centers.
On May 13, a bastard placed the control center of the Citadel network on a virtual server located on our network. Having received an abus from Spamhouse, we removed it. On June 14th, Spamhouse again spotted Citadel on our server. Unfortunately, we were in the process of preparing to move to a new data center and did not immediately respond to this complaint. The brave Canadian policemen from the E-Division were faster and on June 14, 2013 at 15.30 Vancouver time they already managed to get the Court Order and turned off ALL of our servers.
Next, we will insert bills from the Warrant search, which our lawyers have finally received. It is not possible to fully publish the document - it contains 32 pages. The document was written by the police officer conducting the investigation. Without translation.
So, the development of events was as follows.






As you can see, we could neither suppose nor stop these events. Naturally, all the employees of our data center were in shock, everyone went under suspicion of participating in crime. The police took fingerprints on the telecommunication cabinets and interrogated all the people who had ever touched our cabinets, in general, all the data center staff and contractors. At the moment, all suspicions from our comrades are removed.
All servers were returned by August 2013 and we started to restore the service.
Chronicle of events:
June 14, 2013 - placing the botnet on the server, the police receive the Court Order;
June 15, 2013 - seizure of all servers, interrogations of Data Center employees;
June 16, 2013 - interrogation of company owners, involvement of Bull Housser in the case;
June 17 and 18, 2013 - preparation of petitions, statements, explanations;
June 19, 2013 - receiving a copy of the Court Order directly from the court, a statement of non-involvement in criminal activities;
June 20 - moving to a new place, installing racks, connecting electricity, etc.;
June 22, 2013 - return of switches, billing servers and the first server from VPS clients;
June 29, 2013 - the return of 16 servers, mainly dedicated;
July 05, 2013 - 25% of all servers are returned;
July 9, 2013 - 95% of all servers are returned;
July 22, 2013 - all servers except two were returned;
August 2, 2013 - the last two servers are returned.
To the honor of the Canadian police, we can say that they acted politely, treated our property carefully, kept our promises, answered telephone calls and e-mails quickly.
Although we are not to blame for what happened, nevertheless, we apologized to all victims of the actions of the Canadian police and said that we continue our work as if nothing had happened. All remaining customers were offered bonuses. Project data and backups were returned to everyone. We regularly kept clients informed of events and reported on the current status of service restoration work. Some of our customers who were forced to leave us because of this story, appreciated our sincerity, hardworking and attitude towards customers, and returned. But the majority, of course, moved to new hosting and we want to say thanks to all the hosters who received our customers and helped them restore the efficiency of client projects. Nevertheless, the mutual assistance of industry colleagues, despite the competition for the client, is a great force.
Further events developed as follows: the first thing was to restore the service, load capacity. Then we decided not to leave the case without consequences and to get a legal assessment of the actions of the police on behalf of the state of Canada.
It was not easy. It was difficult to find a law company that would dare to sue the police in such a sensitive case, threatening to reach the highest court of Canada - Royal Bench Court. However, after almost a year of searching and dozens of negotiations, such a company was found.
It was also difficult to find an expert who would agree to testify in court against the police. It also took a long time. Here we have to say unpleasant words to former compatriots working at Microsoft. We turned to several people with the expectation of help, especially since they are security experts. After studying the issue, they ALL took turns saying that yes, the police are wrong, but they will not testify in court and referred to corporate standards, possible consequences and reluctance to spoil a comfortable life. They wanted to attract Kaspersky Lab as experts as a highly respected company in the West. Unfortunately, our appeals to them, letters and calls remained unanswered. It was very sad to be left without support.
In the end, we found a security expert, an Iranian by origin, who is known in his circles and is an authoritative botnet researcher. He, as soon as he heard about the essence of the matter, immediately agreed to his participation in the case.
So, the claim was prepared, the expert will find, the amount of the claim is determined.
In early November 2014, we filed a lawsuit in the Vancouver District Court and filed a lawsuit with the defendants — the Canadian Police Department of Law.
At the moment, the court has registered the application and the Defendants are obliged by mid-January 2015 to answer whether they want a pre-trial hearing and a possible agreement or are ready to start legal proceedings.
The court will last a long time, several years, according to the plan, it should be completed in 2017, if there are no appeals, or in 2019, if appeals to the High Court are filed. So stock up on popcorn and wait.
We will publish information on the progress of the trial in this article.
Initially, we planned to bring to the lawsuit all customers who suffered, but due to the specifics of Canadian law, we cannot do this. However, if our lawsuit is successful, any such client will be able to file a lawsuit with the Canadian police with reference to our precedent.
Thanks to everyone who read to the end. I wish you success in your business.
Added October 27, 2017:
Dear colleagues, clients, friends!
On November 30 this year, the first court session will be held to consider the claim of our company against the police. We invite everyone who has suffered as a result of police actions to join the lawsuit. To do this, write us a letter with the subject “I join the lawsuit” and indicate your username in our billing directly in the subject line. We will send you detailed instructions on what needs to be done and what data to prepare.
