Access to thousands of personal data of Beeline Wired Internet users was obtained.
Excuse me for the pathos headline, but since such a booze has gone , we will continue. I personally always liked such posts.
So, we will talk about the vulnerability of the well-known Beeline provider in Moscow (and not only). Many remember him under the name Corbina. Without a doubt, this is one of the leading Internet providers with a great and good history. At one time, it was a salvation thanks to high-quality and fast Internet, intranet networks, etc. Currently, the provider’s employees are aware of vulnerabilities and the most critical are already closed. However, I am sure that many will discover a lot of new and interesting things. Moreover, the technique is applicable to almost any provider.

By the will of fate, I ended up in a removable Khrushchev. I had the whistle of a Megaphone. Since I had to stay there for about a week, I was not bothered by the lack of fixed Internet. However, my stay there was delayed. I decided that it didn’t matter, as I was armed with wardriving tools. But I could not bring anything together in a couple of days, except for the open Yota network (facepalm). As you might guess from the name of the post, in the hallway of the apartment I found painfully familiar orange wire. Connected - it was Beeline. It would seem that this is just an orange wire. Nevertheless, it is at least a 100mb channel (optimally) with access to a local network (possibly). In our case, whois said it was a 10.0.0.0/8 subnet. It is clear that not all ip will be available, but better than nothing.
Then nmap enters the fray. I forgot about him in the early 2000s, because Like the era of open ports has passed. However, at the beginning of 2010 I remembered about it again, because all kinds of nosql and other subservices, which were often without authorization, gained wide popularity. nosql saved on everything in the pursuit of productivity, and lots of subservices like zabbiks, jenkins, etc. often turned out to be either open, from the category “yes, who will know that my port is 12345 open”, or full of holes. The same zabbix had a bunch of holes, including sqli without authorization. In short, my goal was routers. 80s ports. Previously, they were often opened to the outside, now providers block the default by default, like the routers themselves. But I was local to them.
He started scanning with nmap, but quickly changed his mind, as he suggested that I wait a couple of days. Zmap was sent to battle . You can read about it, but in short - this is a very fast and narrow alternative to nmap. zmap scanned the same subnet in 2 minutes.
The fact that there were default logins / passwords on the glands, I won’t even consider it a vulnerability. As old as the world. From the category “why should I put a complex password on my router, if it’s local”. Or, more often: "Oh, that's it."
However, a more interesting detail awaited me further. 80% of the routers that I found are dir300 with firmware from Beeline. Without a doubt, this is one of the most reliable and affordable routers that fully copes with its task. When I came across non-standard logins / passwords, I decided to see how and where it goes. Those. opened the inspector in the browser and started sniffing requests. Amazing near! It turned out that the Beeline firmware returned an attempt to log in incorrectly:
However, the firmware for some reason sent several authorization requests at once. At the same time. And when the first simply swore auth: false, the second produced something like:
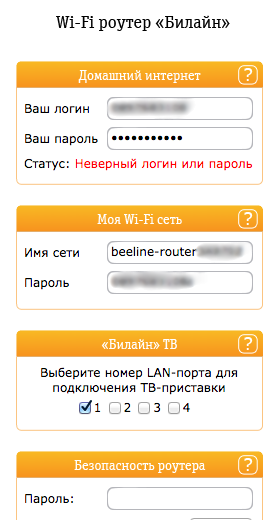
Those. the firmware seemed to say that auth: false, sorry guy. But at the same time I gave away all the settings for the router, including the login / pass from the Beeline personal account and from wifi. In some cases, it was generally funny, the webmord swore at the wrong username / password, but it also showed the username / password, but this was rather the exception, I could see a couple of such routers:
I admit, I did not even suspect that everything would turn out that way. I found all this by accident. And indeed, if the firmware had not sent several requests at once (obviously by mistake of the developers), I would never have thought of checking its availability.
Even having a login / pass from your personal account, we won’t do anything with it. Firstly, as soon as a device is registered under a certain login / password in the Beeline network, no other device can register under this login / password. Secondly, it is a hard fawn.
We scan routers, collect usernames / passwords from wifi. We look at what networks are in reach. Connect to them and sit like partisans. Even networks with a huge password will not stand, because in the router it is stored in open form. Well, so as not to scorch at all. We take a marker and write the login / password from this wifi network somewhere in an inaccessible place at the entrance. Under the stairs of the first floor, for example. Those. even if they come to you, you turn on the fool and say that right there under the stairs you found the username and password and the subscription: “Use everything, free wifi”.
In my case, I did not have the patience to collect all wifi accesses from all routers. The only network that I quickly found and which was in the visibility range of my laptop had good speed, but pings from 30ms to 7s. With AlfaNetworks, I had a stable signal, but these external wifi cards around the world have a reputation as an assistant to the driver, so sitting under them is fawn too.
I continued to collect wifi accesses. There were a lot of them and it bothered me. I wanted a network right now. The simplest and brilliant idea came to mind. Suppose I found a router with an open 80 port at 10.82.2.20. Standard dir300. Or anything else, it doesn’t matter. Turn off DHCP, and write the network settings:
gateway: 10.82.2.20 (the router that you found)
ip: 10.82.2.222 (from the bulldozer in the same subnet)
dns: 8.8.8.8 We
connect the network, and even without intrigue, we have high-quality Internet through a wire, and not through wifi. We go to the router, look - yes indeed, we are connected to it as if in lan.
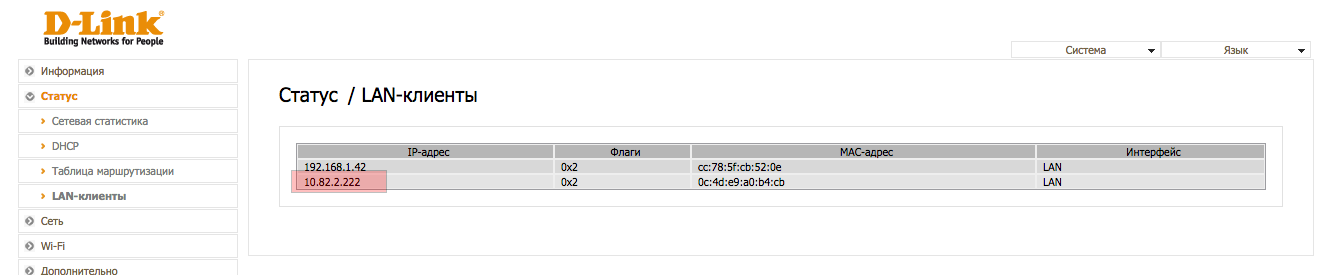
Once again, we read, slowly and delving into each word: As a gateway, we register ANY active IP network and have a connection to it via LAN.
Fine? In my opinion, quite.
I could only check a few routers in my account for a normal tariff to select "who to be today."
Honestly, this is more likely a vulnerability not only (and not only) of Beeline, but of routers. But nonetheless.
Having received moral and aesthetic pleasure, I contacted the representatives of the provider and gave them all the best practices.
At the exit, having only a Beeline wire, without knowing the usernames / passwords, it was possible to get fast Internet for free. Just send 2 bytes.
Some details:
1. 99% of TrendNet routers have a standard username / password. For all the time I found only 1 or 2 routers from TrendNet, to which default accesses did not fit.
2. 0% of Zyxel routers have a standard login / password. Most likely, when setting up, they require you to change this password.
3. 50% of access to the LC do not change. Anyone familiar with the beeline knows that when concluding the contract, the installer makes the password for the personal account either equal to the login, or adds 1 character to the beginning or end of the login.
And here's another thing, on a fantasy level. Again, quite by accident, I came across a live router, registered it as a gateway and myself a local 192.168.0.222. I got the Internet, used it, and then went to the router settings (to 192.168.0.1). I don’t remember why. Maybe check something or something else. Imagine my surprise when the login form of the ADSL router from MTS was opened in front of me. I double-checked the network, looked at checkip.dyndns.com, upgraded the external IP - indeed, this is MTS Internet.
I stuck a Beeline wire, and got the Internet from MTS. I puzzled for a long time, what is the point and how is this possible. Connected to the process of the system administrator from work and specialists from Beeline. The only possible option that I came up with:
1. There is a dude who has both MTS and Beeline Internet, respectively, 2 routers.
2. Both routers are terminated to each other.
3. The Beeline router does not have an Internet and asks it from the MTS router.
4. “Beeline” router is not on the network 192.168.0.0/24
5. MTS router is on the network 192.168.0.0/24
6. Knowing the local IP beeline, inserting it as a gateway, I connect through it to the MTS router and have Internet from him.
Cool? It is noteworthy that on the 1st of the next month the device disappeared. Presumably, the dude turned off the Beeline.
Thanks to Beeline employees for the quick response. In particular, geran_utran and givtone. In fact, one often has to communicate with administrators and developers of a particular service about security and more often stumbles upon: "Yes, we will put you in prison, this is a matter of jurisdiction!" And other inadequate. The guys quickly fixed critical holes and attracted the right people. I was sure that I would have another month or two freebies until the entire Beeline network was reconfigured, but no, everything was decided within a day, as soon as they found the person responsible. Well done, in a word.
So, we will talk about the vulnerability of the well-known Beeline provider in Moscow (and not only). Many remember him under the name Corbina. Without a doubt, this is one of the leading Internet providers with a great and good history. At one time, it was a salvation thanks to high-quality and fast Internet, intranet networks, etc. Currently, the provider’s employees are aware of vulnerabilities and the most critical are already closed. However, I am sure that many will discover a lot of new and interesting things. Moreover, the technique is applicable to almost any provider.

By the will of fate, I ended up in a removable Khrushchev. I had the whistle of a Megaphone. Since I had to stay there for about a week, I was not bothered by the lack of fixed Internet. However, my stay there was delayed. I decided that it didn’t matter, as I was armed with wardriving tools. But I could not bring anything together in a couple of days, except for the open Yota network (facepalm). As you might guess from the name of the post, in the hallway of the apartment I found painfully familiar orange wire. Connected - it was Beeline. It would seem that this is just an orange wire. Nevertheless, it is at least a 100mb channel (optimally) with access to a local network (possibly). In our case, whois said it was a 10.0.0.0/8 subnet. It is clear that not all ip will be available, but better than nothing.
Then nmap enters the fray. I forgot about him in the early 2000s, because Like the era of open ports has passed. However, at the beginning of 2010 I remembered about it again, because all kinds of nosql and other subservices, which were often without authorization, gained wide popularity. nosql saved on everything in the pursuit of productivity, and lots of subservices like zabbiks, jenkins, etc. often turned out to be either open, from the category “yes, who will know that my port is 12345 open”, or full of holes. The same zabbix had a bunch of holes, including sqli without authorization. In short, my goal was routers. 80s ports. Previously, they were often opened to the outside, now providers block the default by default, like the routers themselves. But I was local to them.
He started scanning with nmap, but quickly changed his mind, as he suggested that I wait a couple of days. Zmap was sent to battle . You can read about it, but in short - this is a very fast and narrow alternative to nmap. zmap scanned the same subnet in 2 minutes.
Vulnerability # 1
Without a login / password from Beeline, just by plugging in a wire, I got access to all local resources and devices (routers, cameras, voip glands, etc.)
The fact that there were default logins / passwords on the glands, I won’t even consider it a vulnerability. As old as the world. From the category “why should I put a complex password on my router, if it’s local”. Or, more often: "Oh, that's it."
However, a more interesting detail awaited me further. 80% of the routers that I found are dir300 with firmware from Beeline. Without a doubt, this is one of the most reliable and affordable routers that fully copes with its task. When I came across non-standard logins / passwords, I decided to see how and where it goes. Those. opened the inspector in the browser and started sniffing requests. Amazing near! It turned out that the Beeline firmware returned an attempt to log in incorrectly:
{
auth: false
}
However, the firmware for some reason sent several authorization requests at once. At the same time. And when the first simply swore auth: false, the second produced something like:
{
auth: false,
…
settings: {
ssid: "blablabla",
wpakey: "12345678",
login: 089746254
password: "lovelove123"
…
}
}
Those. the firmware seemed to say that auth: false, sorry guy. But at the same time I gave away all the settings for the router, including the login / pass from the Beeline personal account and from wifi. In some cases, it was generally funny, the webmord swore at the wrong username / password, but it also showed the username / password, but this was rather the exception, I could see a couple of such routers:

Vulnerability # 2
Beeline firmware for routers itself gave all the settings of the router without knowing the login / password.
I admit, I did not even suspect that everything would turn out that way. I found all this by accident. And indeed, if the firmware had not sent several requests at once (obviously by mistake of the developers), I would never have thought of checking its availability.
Even having a login / pass from your personal account, we won’t do anything with it. Firstly, as soon as a device is registered under a certain login / password in the Beeline network, no other device can register under this login / password. Secondly, it is a hard fawn.
We scan routers, collect usernames / passwords from wifi. We look at what networks are in reach. Connect to them and sit like partisans. Even networks with a huge password will not stand, because in the router it is stored in open form. Well, so as not to scorch at all. We take a marker and write the login / password from this wifi network somewhere in an inaccessible place at the entrance. Under the stairs of the first floor, for example. Those. even if they come to you, you turn on the fool and say that right there under the stairs you found the username and password and the subscription: “Use everything, free wifi”.
In my case, I did not have the patience to collect all wifi accesses from all routers. The only network that I quickly found and which was in the visibility range of my laptop had good speed, but pings from 30ms to 7s. With AlfaNetworks, I had a stable signal, but these external wifi cards around the world have a reputation as an assistant to the driver, so sitting under them is fawn too.
I continued to collect wifi accesses. There were a lot of them and it bothered me. I wanted a network right now. The simplest and brilliant idea came to mind. Suppose I found a router with an open 80 port at 10.82.2.20. Standard dir300. Or anything else, it doesn’t matter. Turn off DHCP, and write the network settings:
gateway: 10.82.2.20 (the router that you found)
ip: 10.82.2.222 (from the bulldozer in the same subnet)
dns: 8.8.8.8 We
connect the network, and even without intrigue, we have high-quality Internet through a wire, and not through wifi. We go to the router, look - yes indeed, we are connected to it as if in lan.

Once again, we read, slowly and delving into each word: As a gateway, we register ANY active IP network and have a connection to it via LAN.
Fine? In my opinion, quite.
I could only check a few routers in my account for a normal tariff to select "who to be today."
Honestly, this is more likely a vulnerability not only (and not only) of Beeline, but of routers. But nonetheless.
Vulnerability # 3
Ability to connect / register locally on any router within the network and get internet from it.
Having received moral and aesthetic pleasure, I contacted the representatives of the provider and gave them all the best practices.
At the exit, having only a Beeline wire, without knowing the usernames / passwords, it was possible to get fast Internet for free. Just send 2 bytes.
Some details:
1. 99% of TrendNet routers have a standard username / password. For all the time I found only 1 or 2 routers from TrendNet, to which default accesses did not fit.
2. 0% of Zyxel routers have a standard login / password. Most likely, when setting up, they require you to change this password.
3. 50% of access to the LC do not change. Anyone familiar with the beeline knows that when concluding the contract, the installer makes the password for the personal account either equal to the login, or adds 1 character to the beginning or end of the login.
And here's another thing, on a fantasy level. Again, quite by accident, I came across a live router, registered it as a gateway and myself a local 192.168.0.222. I got the Internet, used it, and then went to the router settings (to 192.168.0.1). I don’t remember why. Maybe check something or something else. Imagine my surprise when the login form of the ADSL router from MTS was opened in front of me. I double-checked the network, looked at checkip.dyndns.com, upgraded the external IP - indeed, this is MTS Internet.
I stuck a Beeline wire, and got the Internet from MTS. I puzzled for a long time, what is the point and how is this possible. Connected to the process of the system administrator from work and specialists from Beeline. The only possible option that I came up with:
1. There is a dude who has both MTS and Beeline Internet, respectively, 2 routers.
2. Both routers are terminated to each other.
3. The Beeline router does not have an Internet and asks it from the MTS router.
4. “Beeline” router is not on the network 192.168.0.0/24
5. MTS router is on the network 192.168.0.0/24
6. Knowing the local IP beeline, inserting it as a gateway, I connect through it to the MTS router and have Internet from him.
Cool? It is noteworthy that on the 1st of the next month the device disappeared. Presumably, the dude turned off the Beeline.
Thanks to Beeline employees for the quick response. In particular, geran_utran and givtone. In fact, one often has to communicate with administrators and developers of a particular service about security and more often stumbles upon: "Yes, we will put you in prison, this is a matter of jurisdiction!" And other inadequate. The guys quickly fixed critical holes and attracted the right people. I was sure that I would have another month or two freebies until the entire Beeline network was reconfigured, but no, everything was decided within a day, as soon as they found the person responsible. Well done, in a word.
