Sednit hacker group specializes in attacks of isolated air-gapped networks
The cybercriminal group Sednit , which is also known as Sofacy, APT28, or Fancy Bear, has specialized in attacking various organizations for many years. We recently discovered that this group began to specialize in attacks from secure, isolated from the Internet air-gapped networks. For this, a special malicious program is used, with the help of which the theft of confidential computer data is carried out on a compromised network.

Earlier, we wrote about the criminal activity of this group, which used its own set of exploits to compromise legitimate websites and subsequently infect users with malware. The activity of this group was also reported by FireEye in its report on the group.APT28 , as well as Trend Micro in the Operation Pawn Storm report . In this article, we will focus on a new attack area of this group, which uses the Win32 / USBStealer malware to steal sensitive data from computers on networks that are isolated from the Internet.
Our research indicates that the Sednit group has been using Win32 / USBStealer malware since at least 2005. The objectives of these attacks are various government organizations in Eastern Europe. Several versions of this malware have been used in attacks of varying degrees of complexity.
One of the security measures that can be used by the enterprise security service to prevent the leak of confidential data of computers connected to the corporate network is its isolation by technical means from the Internet. However, the use of removable media may be the starting point for the leak of such data. At the same time, it is assumed that some employee of the enterprise can transfer corporate data to a USB drive, and they will be copied to a computer that has access to the worldwide network.
This scenario is used by the Sednit team when operating Win32 / USBStealer . In this case, the scheme for obtaining confidential data using malware will be multi-stage and consists of five stages.
Stage 1
At the first stage, the attackers compromise a computer that has Internet access (for example, an employee’s home computer). Let's call it Computer A. In the process of compromising, Computer A becomes infected with the dropper of a malicious program that we detect as Win32 / USBStealer.D . The executable file of this dropper is called USBSRService.exe , and its fake resource section indicates that this file is the installer of the legitimate Russian program USB Disk Security .
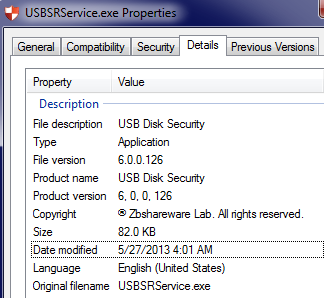
Fig. Metadata dropper the Win32 / USBStealer .
The main logic of the dropper is as follows:

Fig. The contents of the AUTORUN file.
When writing files to a removable drive, the dropper modifies the file’s metadata, namely, their “Last Access” and “Last Write” timestamps to those values that correspond to their counterparts in Windows system files. They are assigned attributes of system and hidden files. Thus, the illusion of a certain "system" of malicious files is created. It is also worth noting that the elements of the resource section decrypted in the memory are encrypted back after the file writing operations are performed, which excludes their removal from the memory by any forensic analysis tools.
Stage 2
When an infected USB drive is inserted into a computer that is isolated from the Internet network of the enterprise, Win32 / USBStealerautomatically installs itself in the system. This will happen when the autorun function is enabled on this computer. We call this computer, which runs in an isolated air-gapped network, Computer B. As soon as Win32 / USBStealer takes control, it lists all the disks currently connected to the system and, depending on the type of disk, uses a different scheme of its behavior.
The meaning of this last step is to group files of interest to the malicious code into one local directory. This step can be called preparatory to the real exfiltration of data. It will happen as soon as the same removable drive is inserted again into the USB port of Computer B. The file types that are of interest to the malicious program are listed below.
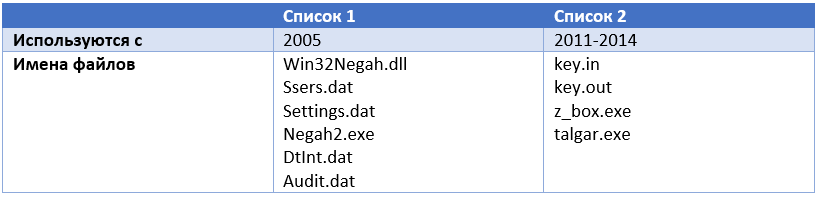
The initial usage period is calculated based on the compilation date of the executable files from which these lists were extracted. We found very few links to most of these file names in open sources. Perhaps because they belong to a narrow specialization software. It is also interesting that the name Talgar (talgar.exe) coincides with the name of the city of Almaty region in southeast Kazakhstan.
A malicious program searches for these files everywhere on hard drives, except directories whose names match the names of the following anti-virus products: Symantec, Norton, McAfee, ESET Smart Security, AVG9, Kaspersky Lab, Doctor Web.
Stage 3
This stage assumes the fact that the user inserts the infected USB drive back into Computer A, after he has already visited the isolated Computer B in the second stage. At this step, the malware component on computer A issues a set of Win32 / USBStealer commands that it must execute in step 4. To do this, the necessary commands are written to an encrypted file with the name COMPUTER_NAME.in in the root of the drive.
Stage 4
It is assumed that in the fourth stage, the same infected medium will again go to Computer B. In this case, the malware bot instructions that it must execute are already stored there. At this stage, the files selected by the attackers should be copied from the directory that was created on Computer B in the second stage (grouping of files). Then, at the final stage, they will be sent to the remote server of the attackers.
At this point, Win32 / USBStealer decrypts the batch file ( COMPUTER_NAME.in ), which was reset to the root of the USB drive in the previous step. This file contains the commands that the bot must execute sequentially. A command is identified by a double-byte identifier followed by a command argument.

The 0x0003 and 0x0005 commands operate on a special file that the malware creates on the local drive of Computer B. It contains file information templates in the format “Root = Path = Day”. Each time you boot Windows, Win32 / USBStealer executes the 0x0002 command for the files in this list.
The 0x0008 command is used to detect files that may be of interest to attackers. We can assume that the attackers start the attack with this command, and then use the 0x0002 and 0x0003 commands to collect data.
For teams that perform operations of copying files to removable media, a special backup method is provided. If the malicious program cannot copy files to the media, for example, it is write-protected, the files will be copied to a special directory on the local drive. In the future, malicious code will try to copy them from there when another infected medium is connected.
Stage 5
At this stage, the infected USB drive again enters Computer A. In this case, the malicious program transfers the files copied from Computer B to the remote server.
Conclusion Win32 / USBStealer
Malicious Softwareshows the specific focus of the Sednit group of attackers on corporate users of air-gapped networks. We also noticed the following interesting features:
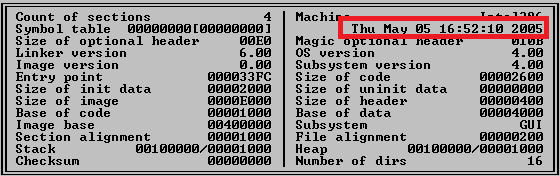
Fig. Compilation date of the malicious file (Timestamp).
Some questions still remain open. For example, in what particular way, the initial infection of Computer A malware occurred. We can assume that phishing messages were used for this. It may be noted that the FireEye report we mentioned at the beginning of this article about this group contains information about the phishing campaign. At the same time, the following text was indicated in the messages: “USB Disk Security is the best software to block threats that can damage your PC or compromise your personal information via USB storage.”

Earlier, we wrote about the criminal activity of this group, which used its own set of exploits to compromise legitimate websites and subsequently infect users with malware. The activity of this group was also reported by FireEye in its report on the group.APT28 , as well as Trend Micro in the Operation Pawn Storm report . In this article, we will focus on a new attack area of this group, which uses the Win32 / USBStealer malware to steal sensitive data from computers on networks that are isolated from the Internet.
Our research indicates that the Sednit group has been using Win32 / USBStealer malware since at least 2005. The objectives of these attacks are various government organizations in Eastern Europe. Several versions of this malware have been used in attacks of varying degrees of complexity.
One of the security measures that can be used by the enterprise security service to prevent the leak of confidential data of computers connected to the corporate network is its isolation by technical means from the Internet. However, the use of removable media may be the starting point for the leak of such data. At the same time, it is assumed that some employee of the enterprise can transfer corporate data to a USB drive, and they will be copied to a computer that has access to the worldwide network.
This scenario is used by the Sednit team when operating Win32 / USBStealer . In this case, the scheme for obtaining confidential data using malware will be multi-stage and consists of five stages.
Stage 1
At the first stage, the attackers compromise a computer that has Internet access (for example, an employee’s home computer). Let's call it Computer A. In the process of compromising, Computer A becomes infected with the dropper of a malicious program that we detect as Win32 / USBStealer.D . The executable file of this dropper is called USBSRService.exe , and its fake resource section indicates that this file is the installer of the legitimate Russian program USB Disk Security .

Fig. Metadata dropper the Win32 / USBStealer .
The main logic of the dropper is as follows:
- It monitors the connection to the system of a removable drive by creating a window with a callback function that will be called if such an event occurs.
- As soon as a removable drive is inserted into the system, the dropper will decrypt several elements of its resource section of the executable file. One of them is another Win32 / USBStealer executable file , which is copied to a removable drive under the name USBGuard.exe . The second element of the resource section is the AUTORUN.INF file, the contents of which are presented below.
- Files are copied to the root of the removable drive and if the autostart function is enabled, they will be executed as soon as the drive is inserted into the computer with autostart enabled, or by double-clicking on the drive icon (see AUTORUN.INF format below). The Windows Startup setting was eliminated back in 2009 with the KB971029 update . However, our data shows that attackers started using Win32 / USBStealer four years earlier, that is, in 2005. In addition, for computers that operate on air-gapped networks, the lack of updates required is considered quite common.
- In the last step, the malicious program copies an empty file called destktop.in to the root of the disk . This serves as a signal for the malicious program that this drive has already been connected to a computer that has Internet access.

Fig. The contents of the AUTORUN file.
When writing files to a removable drive, the dropper modifies the file’s metadata, namely, their “Last Access” and “Last Write” timestamps to those values that correspond to their counterparts in Windows system files. They are assigned attributes of system and hidden files. Thus, the illusion of a certain "system" of malicious files is created. It is also worth noting that the elements of the resource section decrypted in the memory are encrypted back after the file writing operations are performed, which excludes their removal from the memory by any forensic analysis tools.
Stage 2
When an infected USB drive is inserted into a computer that is isolated from the Internet network of the enterprise, Win32 / USBStealerautomatically installs itself in the system. This will happen when the autorun function is enabled on this computer. We call this computer, which runs in an isolated air-gapped network, Computer B. As soon as Win32 / USBStealer takes control, it lists all the disks currently connected to the system and, depending on the type of disk, uses a different scheme of its behavior.
- If the detected drive is removable and is marked as a desktop.in file located in the root of the drive (i.e., this detected drive was already present in the system with the ability to connect to the Internet), then the malware creates a directory in the root of this drive, where The computer name is used as the name. This operation allows operators to distinguish between computers into which an infected drive was inserted. Subsequently, this data will be used when sending data to the attacker server, when the drive returns to Computer A connected to the Internet.
- If the drive is not removable, Win32 / USBStealer carries out special preparations for the procedure for subsequent exfiltration (theft) of data.
The meaning of this last step is to group files of interest to the malicious code into one local directory. This step can be called preparatory to the real exfiltration of data. It will happen as soon as the same removable drive is inserted again into the USB port of Computer B. The file types that are of interest to the malicious program are listed below.
- Files with the extensions “.skr”, “.pkr” or “.key”. The first two relate to the PGP Desktop cryptographic application files. They store public and private encryption keys. The third extension is often used by other cryptographic tools to store similar keys.
- Files whose names match the list below. We found two lists of such files, they are listed in the table below.

The initial usage period is calculated based on the compilation date of the executable files from which these lists were extracted. We found very few links to most of these file names in open sources. Perhaps because they belong to a narrow specialization software. It is also interesting that the name Talgar (talgar.exe) coincides with the name of the city of Almaty region in southeast Kazakhstan.
A malicious program searches for these files everywhere on hard drives, except directories whose names match the names of the following anti-virus products: Symantec, Norton, McAfee, ESET Smart Security, AVG9, Kaspersky Lab, Doctor Web.
Stage 3
This stage assumes the fact that the user inserts the infected USB drive back into Computer A, after he has already visited the isolated Computer B in the second stage. At this step, the malware component on computer A issues a set of Win32 / USBStealer commands that it must execute in step 4. To do this, the necessary commands are written to an encrypted file with the name COMPUTER_NAME.in in the root of the drive.
Stage 4
It is assumed that in the fourth stage, the same infected medium will again go to Computer B. In this case, the malware bot instructions that it must execute are already stored there. At this stage, the files selected by the attackers should be copied from the directory that was created on Computer B in the second stage (grouping of files). Then, at the final stage, they will be sent to the remote server of the attackers.
At this point, Win32 / USBStealer decrypts the batch file ( COMPUTER_NAME.in ), which was reset to the root of the USB drive in the previous step. This file contains the commands that the bot must execute sequentially. A command is identified by a double-byte identifier followed by a command argument.

The 0x0003 and 0x0005 commands operate on a special file that the malware creates on the local drive of Computer B. It contains file information templates in the format “Root = Path = Day”. Each time you boot Windows, Win32 / USBStealer executes the 0x0002 command for the files in this list.
The 0x0008 command is used to detect files that may be of interest to attackers. We can assume that the attackers start the attack with this command, and then use the 0x0002 and 0x0003 commands to collect data.
For teams that perform operations of copying files to removable media, a special backup method is provided. If the malicious program cannot copy files to the media, for example, it is write-protected, the files will be copied to a special directory on the local drive. In the future, malicious code will try to copy them from there when another infected medium is connected.
Stage 5
At this stage, the infected USB drive again enters Computer A. In this case, the malicious program transfers the files copied from Computer B to the remote server.
Conclusion Win32 / USBStealer
Malicious Softwareshows the specific focus of the Sednit group of attackers on corporate users of air-gapped networks. We also noticed the following interesting features:
- The operation has been carried out for almost 10 years. We detected a file with malware with a compilation date of May 2005, as shown in the screenshot below. The compilation date of the file is also related to the version of the compiler that was used to compile the file at that time. Other malware files that were detected also have realistic compilation dates, which allows us to say that this data is not fake.
- The obvious focus of the attack. As we already mentioned, the names and file extensions that are used for theft allow us to talk about the obvious focus of this attack.

Fig. Compilation date of the malicious file (Timestamp).
Some questions still remain open. For example, in what particular way, the initial infection of Computer A malware occurred. We can assume that phishing messages were used for this. It may be noted that the FireEye report we mentioned at the beginning of this article about this group contains information about the phishing campaign. At the same time, the following text was indicated in the messages: “USB Disk Security is the best software to block threats that can damage your PC or compromise your personal information via USB storage.”
