Developer Vulnerability in Raindrop.io
Good day, dear readers!
Today I learned about an interesting site Raindrop.io. I think some of you have already heard about him, so I’ll explain to those who are not in the know. This service is a smart bookmark repository, an analogue of Pocket, but not many people realize that its use is not as secure as we would like.
Description from the developer:
Frankly, the service interested me. It is absolutely free, there is an application for Android, browser extensions, easy to use and convenient. True, not everything is as cool as it seems at first glance. Among all the many advantages, there is one very, very vulnerable “BUT”!
Having examined the capabilities of the service superficially, I came across one very interesting feature. All bookmarks of each user can be obtained in the form of RSS and for this you only need to know a unique URL of the form: raindrop.io/feeds {key}
where, {key} is a sequence of 6 letters of different register.
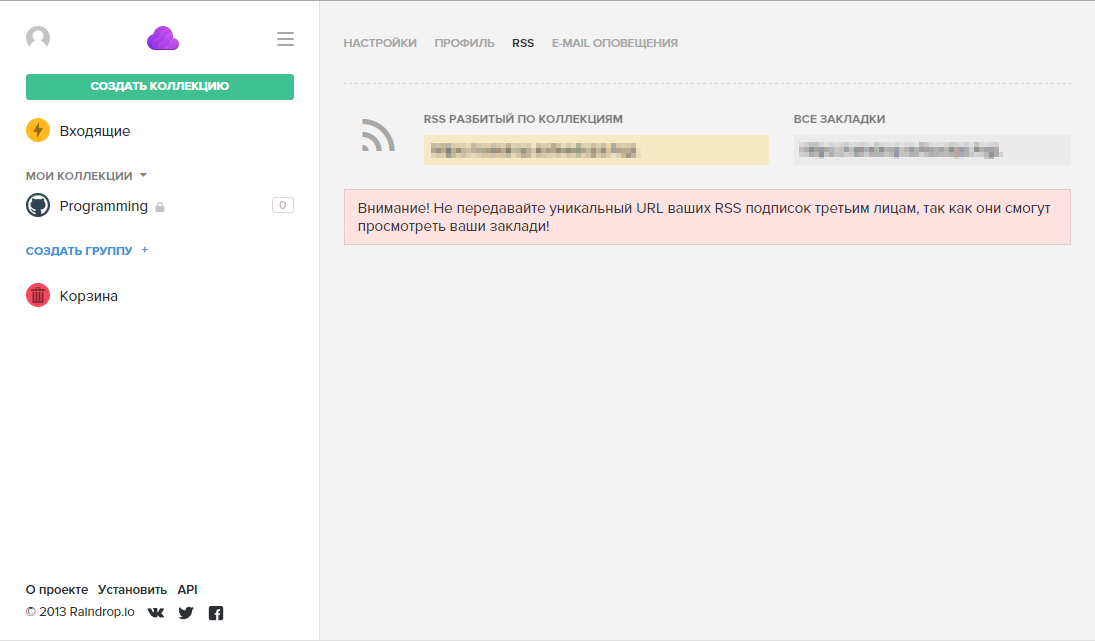
Without thinking for a second, I decided to try to get someone else's bookmarks by choosing the right key. After a couple of minutes of searching manually, it was found that if the key is correct, we get a page with user feeds, otherwise - the message “key invalid!” And error 404. Without thinking twice, it was decided to quickly sketch out a small program for selection and not to suffer. The elementary task was solved in about 5 minutes and a simple console program in C # was already looking for the treasured keys from the repository of other people's bookmarks and carefully saved them to a file.
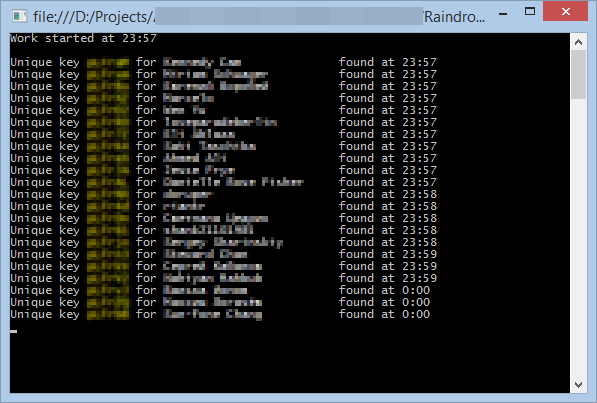
I want to note that even using the first 4 characters of your key and leaving the rest to chance, more than 20 unique keys were found in less than 5 minutes. After waiting another 5 minutes, about 15 more keys were found.
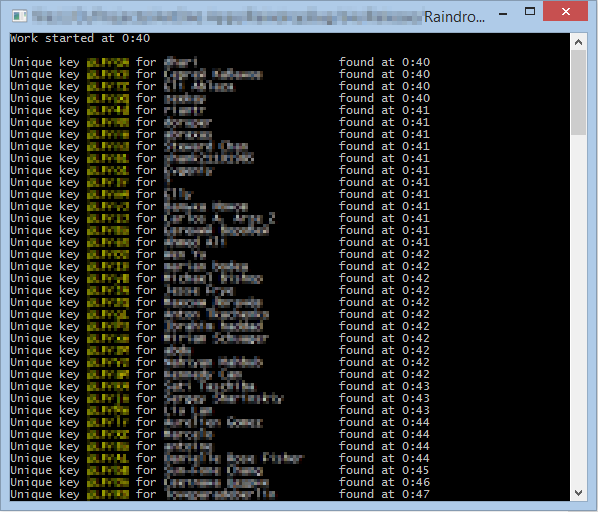
It is also important that the server did not block requests, although they were all from the same IP and sent to the site without any delay.
Morality: not every feature implemented by the developer for the convenience of using a particular product is safe for user data.
Thank you all for your attention! Be vigilant when developing new projects.
Today I learned about an interesting site Raindrop.io. I think some of you have already heard about him, so I’ll explain to those who are not in the know. This service is a smart bookmark repository, an analogue of Pocket, but not many people realize that its use is not as secure as we would like.
Description from the developer:
Raindrop stores not just bookmarks, but also related content, depending on the type of page. If this is an article, it will be cut and saved along with the bookmark. The same goes for video, photo or presentation. Thus, you can organize thematic collections with different content.
Frankly, the service interested me. It is absolutely free, there is an application for Android, browser extensions, easy to use and convenient. True, not everything is as cool as it seems at first glance. Among all the many advantages, there is one very, very vulnerable “BUT”!
Having examined the capabilities of the service superficially, I came across one very interesting feature. All bookmarks of each user can be obtained in the form of RSS and for this you only need to know a unique URL of the form: raindrop.io/feeds {key}
where, {key} is a sequence of 6 letters of different register.

Without thinking for a second, I decided to try to get someone else's bookmarks by choosing the right key. After a couple of minutes of searching manually, it was found that if the key is correct, we get a page with user feeds, otherwise - the message “key invalid!” And error 404. Without thinking twice, it was decided to quickly sketch out a small program for selection and not to suffer. The elementary task was solved in about 5 minutes and a simple console program in C # was already looking for the treasured keys from the repository of other people's bookmarks and carefully saved them to a file.

I want to note that even using the first 4 characters of your key and leaving the rest to chance, more than 20 unique keys were found in less than 5 minutes. After waiting another 5 minutes, about 15 more keys were found.

It is also important that the server did not block requests, although they were all from the same IP and sent to the site without any delay.
Morality: not every feature implemented by the developer for the convenience of using a particular product is safe for user data.
Thank you all for your attention! Be vigilant when developing new projects.
