The activity of the "GosSOPKI" has increased

What is GosSOPKA?
In January 2013, President Vladimir Putin signed a decree on the creation in Russia of a system for detecting, preventing and eliminating the effects of computer attacks (GosSOPKA) on information resources located in our country, in diplomatic missions and consulates abroad.
Its key tasks, in accordance with the presidential decree, should be to predict situations in the field of information security, to ensure the interaction of owners of IT resources in solving problems related to the detection and elimination of computer attacks with telecom operators and other organizations carrying out information protection activities . The system’s task list also includes assessing the degree of protection of a critical IT infrastructure against computer attacks and determining the causes of such incidents.
Putin ordered the FSB to organize work on the creation of a state anti-hacker system. GOSPKA was supposed to confront the most dangerous cyber attacks, behind which are well-organized groups of cybercriminals and the state. Over time, it was planned to consider it as a serious threat to the country and the cumulative damage caused to the economy by numerous less dangerous attacks.
In December 2014, President Vladimir Putin approved the concept of this state. In March 2015, the FSB published an extract from this document containing data on how it will be arranged.
Security blogger Sergey Borisov gives in his article a diagram of the territorial structure, the area of responsibility and the scheme of interaction between GOSPKA.
In accordance with the concept of territorial structure GosSOPKA is:

Area GosSOPKA centers of responsibility displayed in the following diagram:
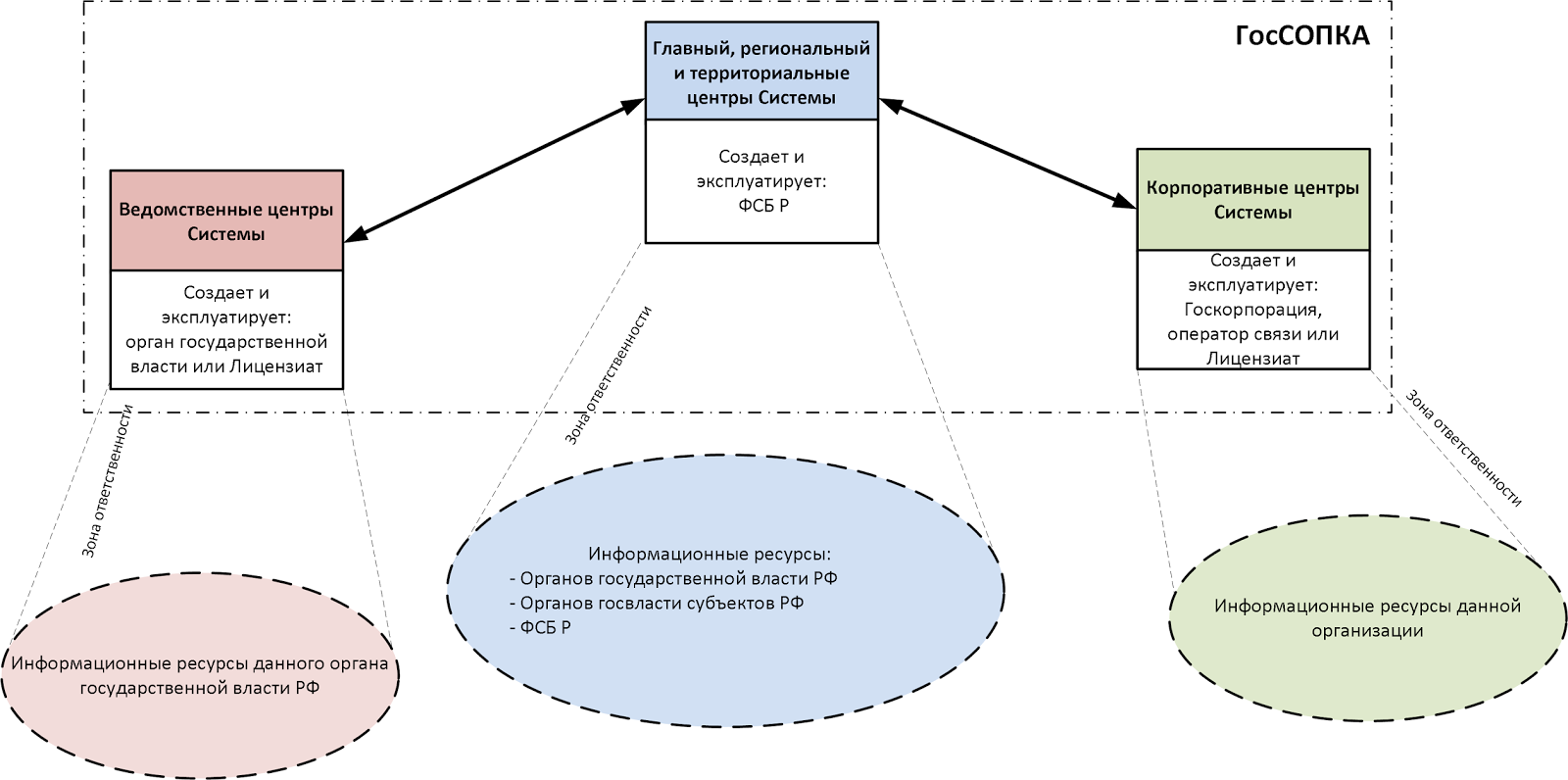
With this in mind, and so the same functions shown in the Concept, we have the following scheme of interaction GosSOPKA:

July 19, 2017 it became known that the Council of the Federation approved the Law on the Security of Critical Information Infrastructure, developed by the Federal Security Service (FSB) and submitted to the State Duma by the Government in December 2016. The document entered into force from the beginning of 2018. The
law IT classification of objects of critical information infrastructure and involves the creation of a register of such objects, while determining the rights and obligations of both the owners of the objects and the authorities that protect these objects.
The document also assumes the creation of a state system for detecting, preventing and eliminating the consequences of computer attacks on Russia's information resources (GosSOPKA), which will ensure the collection and exchange of information about computer attacks.
More information on the development stages of this system can be found at TAdviser .
New orders for the State Bureau
On September 6, 3 (out of six) orders issued by the Federal Security Service of Russia (FSB) were approved and registered with the Ministry of Justice.
Order No. 366 “On the National Computer Incident Coordination Center” is praised in the Russian media as a completely new structure that will replace the CIB, and which will begin to fight hackers of all stripes.
The full text of the order can be found at the link .
According to their official page:
The Computer Incident Response Center in the Information and Telecommunication Networks (ITS) of the Government of the Russian Federation (GOV-CERT.RU) coordinates the activities of interested organizations and departments in the field of prevention, detection and elimination of the consequences of computer incidents that occur in the ITS of the Russian government authorities. Federation. GOV-CERT.RU solves the following tasks:
- provision of advisory and methodological assistance in carrying out measures to eliminate the consequences of computer incidents in the ITS of the state authorities of the Russian Federation;
- analysis of the causes and conditions for the occurrence of incidents in the ITS of public authorities of the Russian Federation
- development of recommendations on ways to neutralize actual threats to information security;
- interaction with Russian, foreign and international organizations that respond to computer incidents; accumulation and analysis of information about computer incidents.
The second order No. 367, “On Approval of the List of Information Provided to the State Bureau of Emergency Situations and the Procedure for Submitting Information to the State Bureau of Emergency Situations”, the full text of the order is available here .
Unfortunately, there are questions on the standardization of information exchange on incidents, on technical solutions for joining GOSPKA, on what to do to small offices that do not have money for joining corporate centers of GOSPKA, etc. are not considered in this document.
Third order, under the number №368 "On approval of the procedure for the exchange of information on computer incidents between the subjects of critical information infrastructure of the Russian Federation, between the subjects of critical information infrastructure of the Russian Federation and the authorized bodies of foreign states, international, international non-governmental organizations and foreign organizations operating in the field of computer incidents, and the procedure for obtaining by the subjects of critical information oh infrastructure of the Russian Federation information on the means and methods of cyber attacks and the methods of prevention and detection. "
The order approves the procedure for the exchange of information about incidents, as well as the procedure for obtaining information about attack methods, methods of their prevention and detection by subjects of the CII. It also does not provide details about the formats and protocols for the exchange of information. It is not clear what to do to participants of international payment systems or subsidiaries of foreign organizations who must promptly send data on incidents and are now forced to do this only through NCCI and without guarantee that NCCI will not block such a transfer, considering it a threat to national security .
The remaining documents are planned to be released no earlier than the end of the year.
Other Cloud4Y blog articles:
→ Myths and misconceptions regarding the Tier-certification system of Uptime Institute (external link)
→Solution for storing and processing BigData (including PD) (external link)
→ History of IT outsourcing (external link)
→ Backup cloud-to-cloud: what it is and why it is needed (Habr)
