Cisco's Next Next Generation Security Solution (NGFW + NGIPS + AMP)
So it happened. Cisco has announced its new solution - FirePOWER for ASA ( presentation in Russian ); the result of the integration of Sourcefire technologies with Cisco native solutions, and more precisely, with the Cisco ASA 5500-X multifunctional security platform.
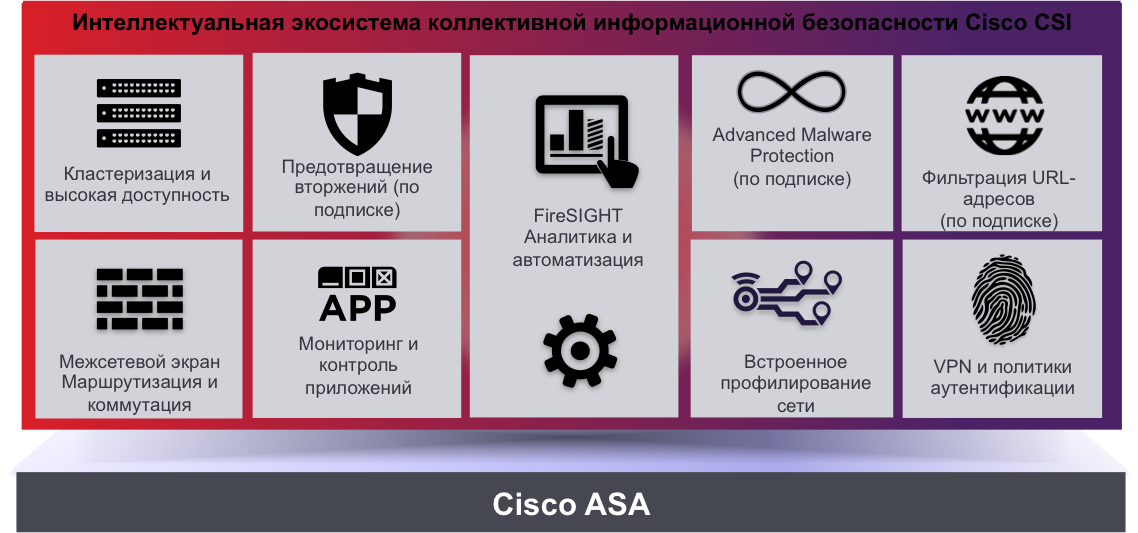
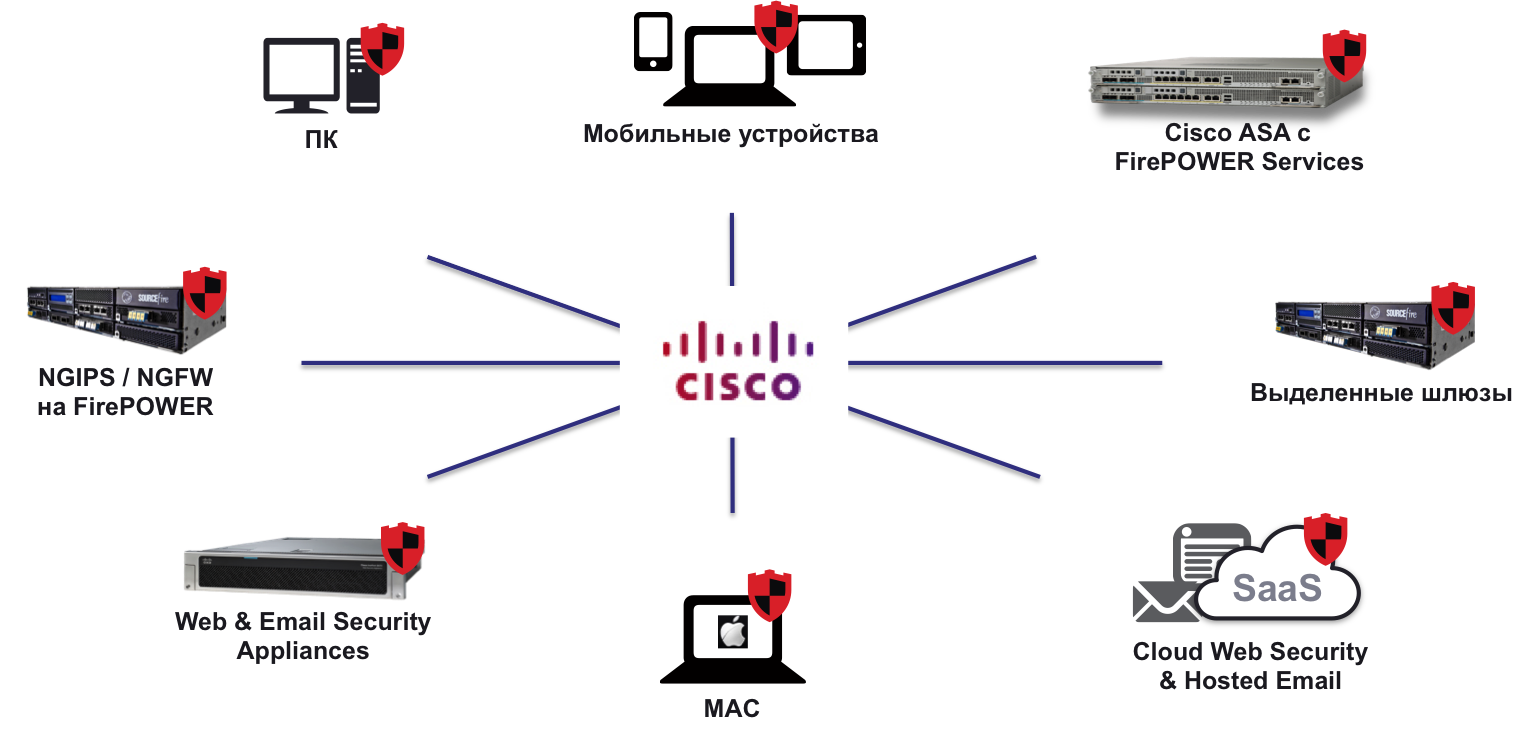
It should be noted that this is not the first joint product. Back in the spring, just six months after the acquisition of Sourcefire, we integrated the Advanced Malware Protection (AMP) malware detection and reflection system into our Cisco Web Security (physical, virtual and cloud solution) Internet access control and protection tools and electronic protection Cisco Email Security (physical, virtual and cloud solution), thereby expanding the platform for detecting malicious code not only at the network or endpoint level, but also at the application level.
A few months later, on September 16, we announced the following integration result - our Cisco ASA security platform was replenished with new features that allow:
And all this in addition to the existing ones on the Cisco ASA 5500-X:
We already wrote about NGFW , NGIPS , and AMP , which are the basis of the new Cisco solution (descriptions of these solutions are available in Russian and on our website). But I would like to recall its key features.
First, Cisco ASA with FirePOWER has built-in security event correlation. Anyone familiar with Cisco’s native Intrusion Prevention Tools (Cisco IPS) remembers that they have a mechanism such as a Meta Event Generator or a local correlation mechanism that can detect multivector threats that use several methods of intrusion at once. Each such method can be characterized by events that individually are not of interest and have the lowest priority. However, collectively, these events can mean a serious targeted threat. Previously, to detect such multivector threats, external correlation and event management systems (SIEMs) were required, which cost companies too much (both in terms of price and in terms of implementation efforts). In Cisco IPS, and then in Cisco ASA with FirePOWER this feature is built-in, which allows you to detect and prevent attacks until they reach their goal, and not after analysis on SIEM. The difference between the new solution is that Sourcefire technologies use more information and data sources for correlation.
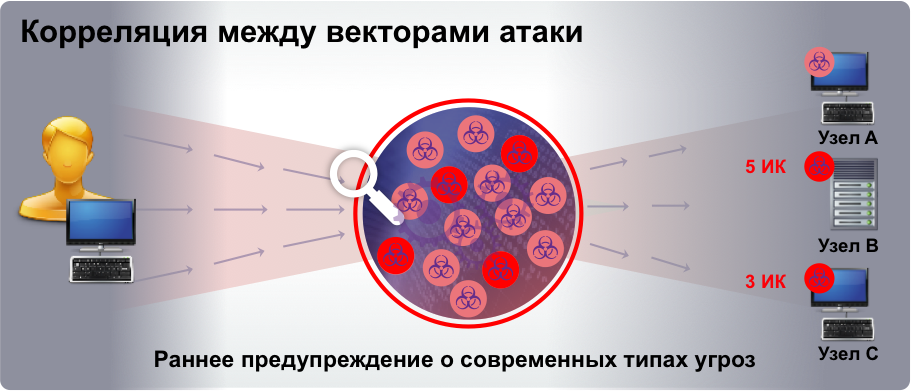
The second interesting feature of Cisco ASA with FirePOWER is the threat prioritization, based on the criticality of the attacked nodes. In other words, we can use the context of the attack to separate important events from unimportant ones, to prioritize the efforts of security specialists to repel threats. Cisco IPS had a similar mechanism called Risk Rating, which allows you to evaluate each threat from a business point of view. At Cisco ASA with FirePOWER, prioritization is further enhanced and automated as much as possible.

By the way, automation is another highlight of Sourcefire and Cisco ASA with FirePOWER technologies. In addition to automating the settings of signatures and rules in the security policy (this is done based on the analysis of network and application traffic and recognition of nodes, devices, protocols, applications, operating systems, etc. used in the network), the policies themselves can dynamically adapt depending on changes in the situation Networks - the emergence of new services, nodes, users, and, of course, threats.

Continuing the topic of correlation, one cannot fail to mention such a possibility of Cisco ASA with FirePOWER as the use of signs (indicators) of compromise, allowing to operate not only on events from a single security device (for example, from an intrusion detection system sensor), but on events from diverse security tools scattered across network. For example, a network scan detected by IPS can be “combined” with the fact of interacting with the botnet command server defined by the NGFW firewall and executing malicious code identified by the AMP malicious code reflection system agent. These three disparate events may serve as an indicator (indicator of compromise, IOC) that an attack is being prepared against the company or that the company's network is already compromised by a targeted threat.
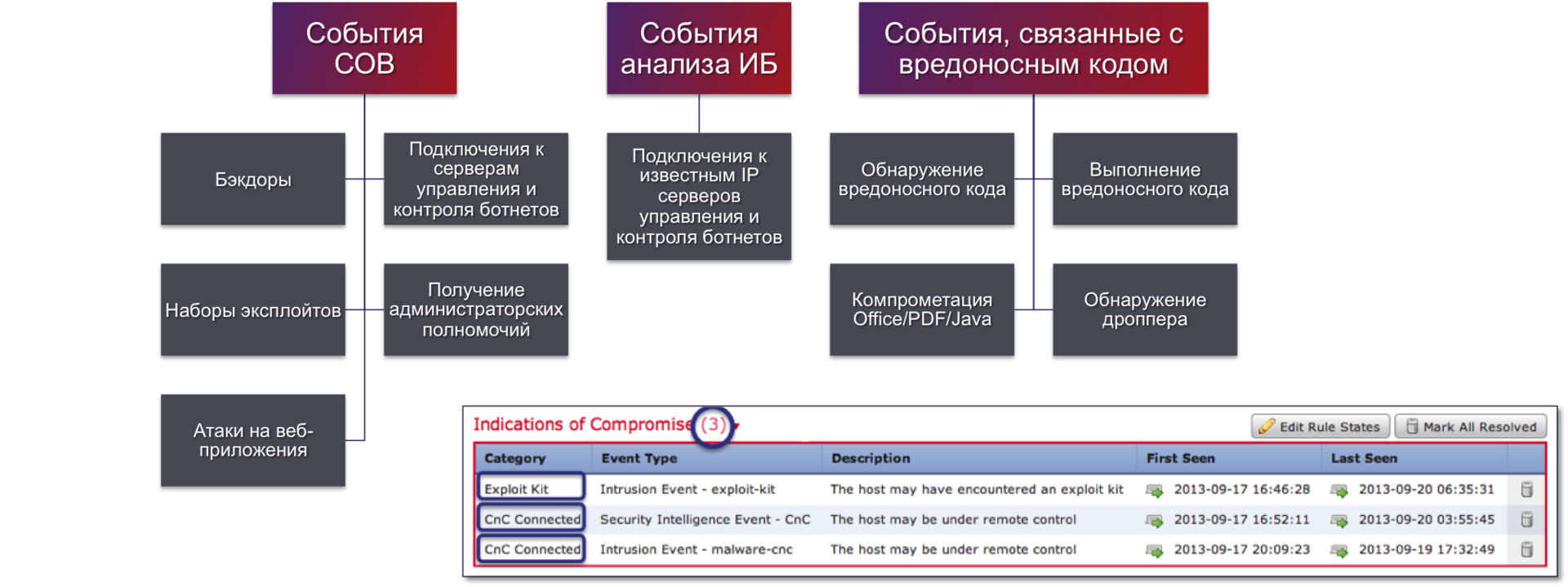
Finally, the last on the list, but not the last in importance, is the retrospective security function, which allows you to monitor the fact of compromise of network nodes that could have occurred due to circumvention of perimeter protection, unauthorized installation of a 3G / 4G modem or access point, connecting an infected flash drive and other reasons. Using post-factum analysis, we can detect already completed facts of malware entering the organization, we can quickly monitor and localize infected nodes, trace the distribution chain of malicious code and analyze the reasons for compromise (for example, vulnerability in Acrobat Reader or Firefox).

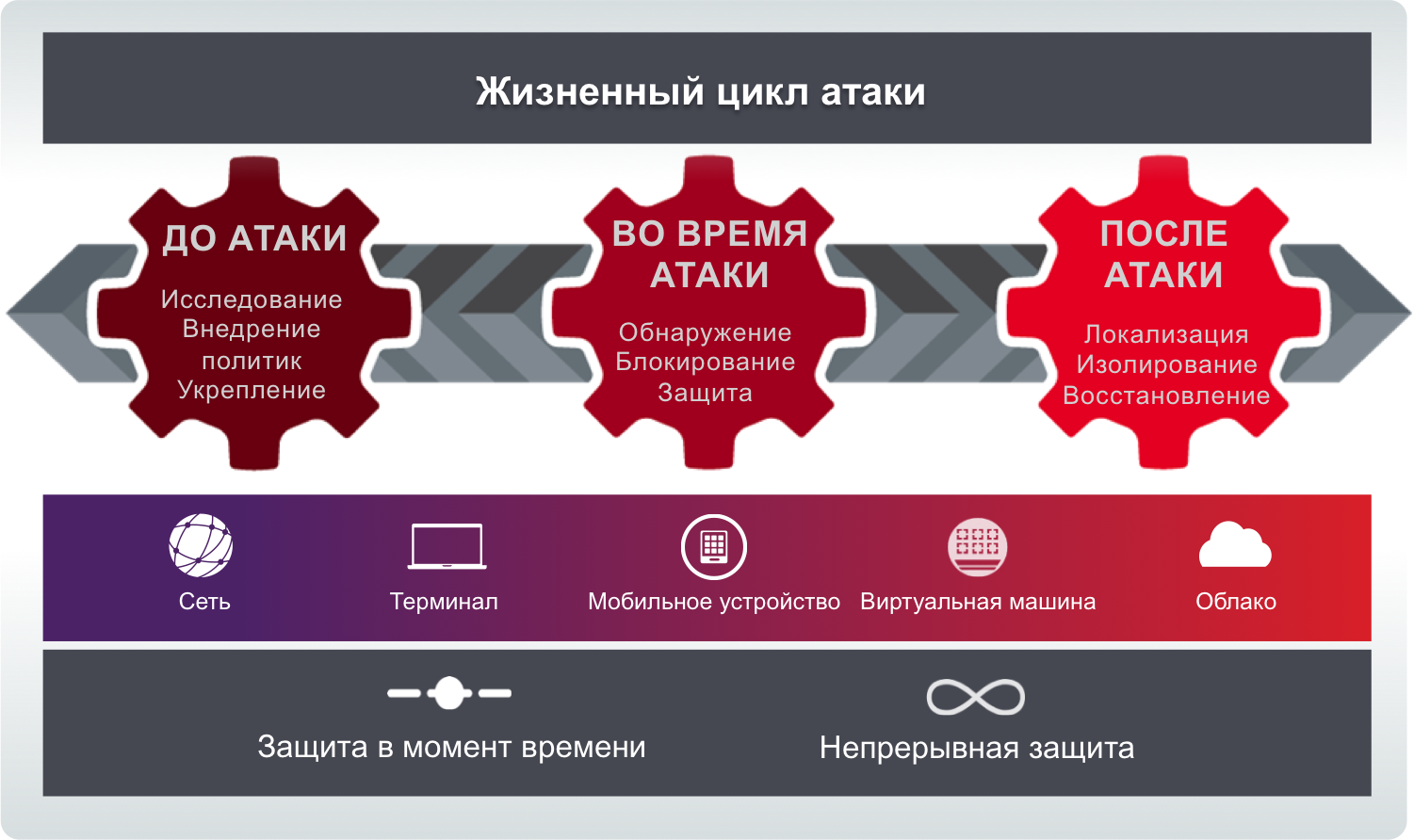
All of these features reflect the concept that underpinned Cisco's security solutions after integrating with Sourcefire. This concept involves the fight against threats at all stages of their life cycle:
The indicated three-link concept “BEFORE - TIME - AFTER" is implemented in all our solutions - Cisco Cyber Threat Defense, Cisco ISE, Cisco ESA / WSA, Sourcefire NGIPS / NGFW / AMP, etc. Cisco ASA with FirePOWER continues this tradition.
Since the new Cisco ASA with FirePOWER functionality works on the entire Cisco ASA 5500-X lineup - from the Cisco ASA 5512-X to the Cisco ASA 5585-X (including all intermediate ones - 5515, 5525, 5545 and 5555), the question is logical , and what is the performance of this solution? It should be noted that it depends on two parameters - the model itself and the functionality used (NGFW, NGIPS, AMP - in different combinations). The minimum performance is 100 Mb / s (for the Cisco ASA 5512-X), the maximum is 15 GB / s (for the Cisco ASA 5585-X). If you need more performance, it is better to focus on dedicated Sourcefire 8300 physical devices operating at speeds up to 60 Gbit / s in NGIPS mode and up to 120 Gbit / s in NGFW mode.
The logical question is, how is the Cisco ASA with FirePOWER managed? Currently, this requires only two solutions - ASDM (for managing a single device) or CSM (for centralized management of multiple devices) and FireSIGHT Manager. ASDM / CSM allow you to manage the functionality of the traditional Cisco ASA ITU, VPN subsystems, and also allow you to configure the network functionality of the security platform - clustering, multiple contexts, routing, etc.
FireSIGHT, already described by us earlier , manages all newly acquired functionality - NGFW, NGIPS, URL filtering and AMP. In the near future, the integration of both consoles into one Cisco ASA with FirePOWER management solution is planned.
The solution itself is already available for order and use. At the same time, for existing users of Cisco ASA, it’s enough to activate the license for the necessary new functionality (NGFW, NGIPS, AMP - in any combination). There is no waiting for the delivery of physical devices (excluding the module for the older Cisco ASA 5585-X model - it has a hardware FirePOWER module), nor is it necessary to obtain additional import permits. And there are no special problems with testing this solution - it’s enough to have a Cisco ASA 5500-X in your network and request a test key from Cisco (for 45 days) to test all the described functionality. In other words, we allow you to save your existing investments in the Cisco ASA 5500-X and use this platform to expand the protective functionality.

It should be noted that this is not the first joint product. Back in the spring, just six months after the acquisition of Sourcefire, we integrated the Advanced Malware Protection (AMP) malware detection and reflection system into our Cisco Web Security (physical, virtual and cloud solution) Internet access control and protection tools and electronic protection Cisco Email Security (physical, virtual and cloud solution), thereby expanding the platform for detecting malicious code not only at the network or endpoint level, but also at the application level.

A few months later, on September 16, we announced the following integration result - our Cisco ASA security platform was replenished with new features that allow:
- control applications ( Next Generation Firewall function )
- Detect and repel attacks ( Next Generation IPS feature )
- control Internet access ( URL filtering function )
- Detect and neutralize malicious code ( Advanced Malware Protection feature ).
And all this in addition to the existing ones on the Cisco ASA 5500-X:
- traditional firewall (stateful firewall function)
- Active Directory integration to bind security policies to user names rather than IP addresses (Identity Firewall feature)
- Interoffice VPN subsystem (Site-to-Site or IPSec VPN)
- secure remote access subsystem (Remote Access or SSL VPN function)
- clustering subsystem and high availability.
Distinctive features
We already wrote about NGFW , NGIPS , and AMP , which are the basis of the new Cisco solution (descriptions of these solutions are available in Russian and on our website). But I would like to recall its key features.
First, Cisco ASA with FirePOWER has built-in security event correlation. Anyone familiar with Cisco’s native Intrusion Prevention Tools (Cisco IPS) remembers that they have a mechanism such as a Meta Event Generator or a local correlation mechanism that can detect multivector threats that use several methods of intrusion at once. Each such method can be characterized by events that individually are not of interest and have the lowest priority. However, collectively, these events can mean a serious targeted threat. Previously, to detect such multivector threats, external correlation and event management systems (SIEMs) were required, which cost companies too much (both in terms of price and in terms of implementation efforts). In Cisco IPS, and then in Cisco ASA with FirePOWER this feature is built-in, which allows you to detect and prevent attacks until they reach their goal, and not after analysis on SIEM. The difference between the new solution is that Sourcefire technologies use more information and data sources for correlation.

The second interesting feature of Cisco ASA with FirePOWER is the threat prioritization, based on the criticality of the attacked nodes. In other words, we can use the context of the attack to separate important events from unimportant ones, to prioritize the efforts of security specialists to repel threats. Cisco IPS had a similar mechanism called Risk Rating, which allows you to evaluate each threat from a business point of view. At Cisco ASA with FirePOWER, prioritization is further enhanced and automated as much as possible.

By the way, automation is another highlight of Sourcefire and Cisco ASA with FirePOWER technologies. In addition to automating the settings of signatures and rules in the security policy (this is done based on the analysis of network and application traffic and recognition of nodes, devices, protocols, applications, operating systems, etc. used in the network), the policies themselves can dynamically adapt depending on changes in the situation Networks - the emergence of new services, nodes, users, and, of course, threats.

Continuing the topic of correlation, one cannot fail to mention such a possibility of Cisco ASA with FirePOWER as the use of signs (indicators) of compromise, allowing to operate not only on events from a single security device (for example, from an intrusion detection system sensor), but on events from diverse security tools scattered across network. For example, a network scan detected by IPS can be “combined” with the fact of interacting with the botnet command server defined by the NGFW firewall and executing malicious code identified by the AMP malicious code reflection system agent. These three disparate events may serve as an indicator (indicator of compromise, IOC) that an attack is being prepared against the company or that the company's network is already compromised by a targeted threat.

Finally, the last on the list, but not the last in importance, is the retrospective security function, which allows you to monitor the fact of compromise of network nodes that could have occurred due to circumvention of perimeter protection, unauthorized installation of a 3G / 4G modem or access point, connecting an infected flash drive and other reasons. Using post-factum analysis, we can detect already completed facts of malware entering the organization, we can quickly monitor and localize infected nodes, trace the distribution chain of malicious code and analyze the reasons for compromise (for example, vulnerability in Acrobat Reader or Firefox).

All of these features reflect the concept that underpinned Cisco's security solutions after integrating with Sourcefire. This concept involves the fight against threats at all stages of their life cycle:
- Before they appear on the perimeter of the network, the functionality of the firewall and URL filtering solves this problem.
- In the process of attack - this task is solved by the intrusion prevention and anti-malware subsystems.
- After getting inside the network, this task is solved by the functionality of retrospective analysis, correlation and work with signs of compromise.

The indicated three-link concept “BEFORE - TIME - AFTER" is implemented in all our solutions - Cisco Cyber Threat Defense, Cisco ISE, Cisco ESA / WSA, Sourcefire NGIPS / NGFW / AMP, etc. Cisco ASA with FirePOWER continues this tradition.
Performance
Since the new Cisco ASA with FirePOWER functionality works on the entire Cisco ASA 5500-X lineup - from the Cisco ASA 5512-X to the Cisco ASA 5585-X (including all intermediate ones - 5515, 5525, 5545 and 5555), the question is logical , and what is the performance of this solution? It should be noted that it depends on two parameters - the model itself and the functionality used (NGFW, NGIPS, AMP - in different combinations). The minimum performance is 100 Mb / s (for the Cisco ASA 5512-X), the maximum is 15 GB / s (for the Cisco ASA 5585-X). If you need more performance, it is better to focus on dedicated Sourcefire 8300 physical devices operating at speeds up to 60 Gbit / s in NGIPS mode and up to 120 Gbit / s in NGFW mode.
Managing ASA with FirePOWER
The logical question is, how is the Cisco ASA with FirePOWER managed? Currently, this requires only two solutions - ASDM (for managing a single device) or CSM (for centralized management of multiple devices) and FireSIGHT Manager. ASDM / CSM allow you to manage the functionality of the traditional Cisco ASA ITU, VPN subsystems, and also allow you to configure the network functionality of the security platform - clustering, multiple contexts, routing, etc.
FireSIGHT, already described by us earlier , manages all newly acquired functionality - NGFW, NGIPS, URL filtering and AMP. In the near future, the integration of both consoles into one Cisco ASA with FirePOWER management solution is planned.
As a summary
The solution itself is already available for order and use. At the same time, for existing users of Cisco ASA, it’s enough to activate the license for the necessary new functionality (NGFW, NGIPS, AMP - in any combination). There is no waiting for the delivery of physical devices (excluding the module for the older Cisco ASA 5585-X model - it has a hardware FirePOWER module), nor is it necessary to obtain additional import permits. And there are no special problems with testing this solution - it’s enough to have a Cisco ASA 5500-X in your network and request a test key from Cisco (for 45 days) to test all the described functionality. In other words, we allow you to save your existing investments in the Cisco ASA 5500-X and use this platform to expand the protective functionality.
