Response Policy Zones (RPZ) guard the network

My experiment with opening a recursive DNS server for everyone was so successful that I urgently had to change the rules of the game. Instead of completely closing recursive DNS, I decided to restrict access to the most popular domains in attacking domains using the RPZ (Response Policy Zone) mechanism.
RPZ is the functionality of the Bind DNS server, the proper use of which allows you to solve the following problems:
- block botnet and malware communications with control centers (C&C);
- reduce the load on the caching DNS and communication channel;
- block access to the list of "prohibited" sites (both for enterprises and for providers);
- redirect users to local resources.
Blocking botnet and malware communications
 | Many Botnets and Malware use DNS to communicate with management centers (C&C), which complicates the process of identifying and dealing with them. An example of such technologies is FastFlux (known since November 2006) and DGA (Domain Generation Algorithm). FastFlux - domain (s) with a large number of A-records that change frequently (TTL - 5 minutes) are used to communicate with C&C. In a more complex implementation, these entries may point to infected / hacked servers and computers acting as proxies. Blocking communications of such malware over IP is impossible due to their large number and frequent changes. BredoLab is one of the famous botnet that used FastFlux technology. BredoLab was used: to infect computers with other malware (Zbot aka Zeus, SpyEye, TDSS, HareBot, Blakken aka Black Energy 2) to send spam and conduct attacks. Read more about BredoLab here . |
| Using DGA technology, malware generates a large number of domains (up to 50 thousand) according to certain rules, some of which are checked and used every day to communicate with C&C. Cryptolocker - one of the most known ransomware programs to date - used this algorithm. After the computer was infected, Cryptolocker tried to contact C&C and, upon successful connection, download the public key, which is used for encryption. lcxgidtthdjje.org, kdavymybmdrew.biz, dhlfdoukwrhjc.co.uk, xodeaxjmnxvpv.ru are examples of domains used by Cryptolocker. To prevent these threats, you can use RPZ, blocking malware communications with C&C. The RPZ zone for protection against such threats can be maintained manually (using data from specialized forums, blogs and websites) or use the subscription service. | 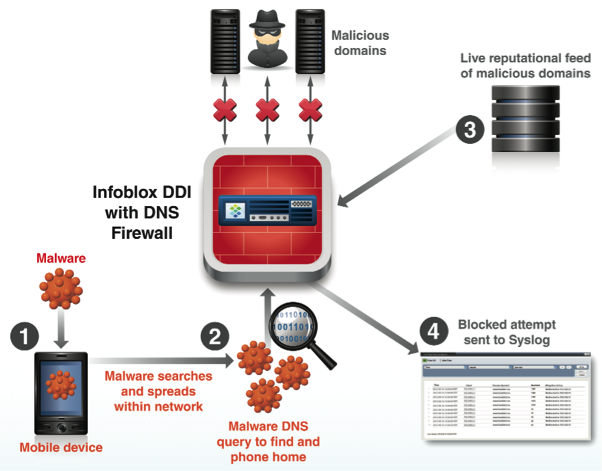 |
- SpamHaus - the cost of a subscription depends on the type of organization and the number of users;
- Surbl - the cost of a subscription depends on the type of organization and the number of users;
- InternetIdentity - the cost is not clear;
- ThreatStop - A subscription sold by Infoblox under the brand name DNS Firewall. The cost depends on the model of the device. On September 18, Infoblox holds a webinar on this topic in Russian, you can register here .
Reducing the load on the caching DNS and communication channel
The activity of botnet agents can lead to a significant increase in the load on the caching DNS and communication channel. All the “right” administrators restrict access to their caching DNS servers, and this traffic comes from authorized clients. Spurious load on the DNS server can be both constant and periodic.
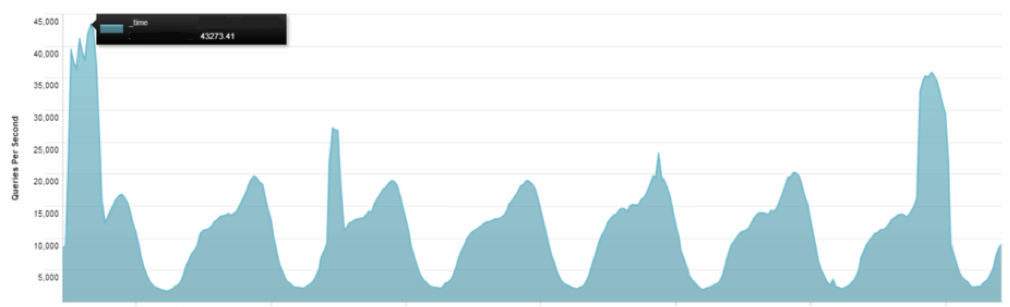
In the above figure, for 2 hours, the load grew from the standard 15 thousand requests per second to 43 thousand requests. For attacks, amplification was used and the server response (in 4K) exceeded the request by 60 times. Accordingly, an additional load of 28 thousand requests per second generated outgoing traffic of 875 Mb / s.
I scanned one of the networks / 16 of the Moscow telecom operator (to which I am connected). In the evening, 69 devices were found that respond to DNS queries and are accessible from the Internet. My (average in parameters) Linksys EA3200 router can process from 1000 requests per second (4Kb packet size) to 3500 requests per second (small packet size), that is, generate 31Mb / s of outgoing traffic at 0.5Mb / s of incoming. That is, 69 detected devices can generate a stream of 2 Gb / s and significantly load the operator’s network.
All spurious traffic on my open recursive DNS (see the previous article ) was generated by only 3 domains: webpanel.sk, energystar.gov and doleta.gov.
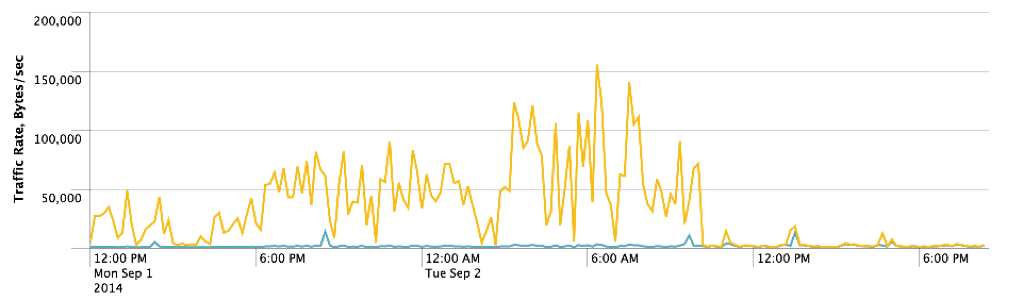
Blocking these domains with RPZ (I used NODATA for the answer) allowed us to reduce the load on the network, since the request size almost coincides with the size of the server response. Conducting an attack has become meaningless.
Blocking access to the list of prohibited sites
Blocking access to domains on the lists of banned sites is useful for both enterprises and Internet providers. With restrictions on access within enterprises, everything is trivial and there are no problems in implementation. Do not forget that you need to block user access to public DNS.
Providers can use RPZ to execute FZ, since not everyone has the ability to pass traffic through DPI, and blocking access by IP is fraught with a loss of customer loyalty. In this case, the restrictions are implemented in this way:
- The registry of banned sites is divided into 2 groups:
- Restrictions imposed on the whole domain;
- Restrictions imposed on a specific section of the site;
- Sites that fall under the blocking of the whole domain are registered in the PRZ zone;
- Routing to the remaining sites is prescribed in such a way that packets pass through either DPI or through a proxy server. As a last resort, it is possible to carry out blocking through IP.
Redirecting users to local resources
In addition to simply blocking access to resources (NXDOMAIN, NODATA, DROP), you can change the response of the DNS server. Such a change in answers may be required, for example:
- to warn users that their computers are infected with malware, botnet agents, or when accessing sites that distribute malware. Additionally, providers can show anti-virus advertisements, and enterprise administrators can specify the phone number and email of IT services;
- to warn users that this resource is blocked. Providers can indicate the reason for blocking (Federal Law), and for corporate users you can display a list of blocked domains and a sample statement of their own free will (for those who disagree);
- redirection of users to local resources or local (gray) IP addresses of servers (an example is given in this habr-article).
Configuring RPZ on BIND 9.10
To use RPZ effectively, all DNS queries should only come to your DNS. This can be achieved in two ways:
- block access to other DNS;
- Automatically redirect all DNS queries with RPZ enabled.
1. Initially, it is necessary to define a list of RZP zones and their parameters with a response-policy expression.
response-policy {zone "whitelist" policy passthru; zone "badlist" policy disabled;};Bind checks the request by RPZ according to the zone order defined in the responce-policy. The most important is the additional policy parameter, which allows you to override the rules for processing requests specified at the zone level. This parameter can take the following values:
- given - the actions defined in the zone are performed (default value);
- disabled - the zone is disabled;
- passthru - the response of the DNS server is not modified, but getting into the zone is reflected in the log files;
- drop - the server ignores the request (does not respond);
- nxdomain - the server responds with NXDOMAIN (non-existing domain);
- nodata - the server responds with NODATA (no record);
- tcp-only - a truncated message is sent, which forces the client to execute a request over TCP (protection against DrDoS);
- cname domain-name - the server overwrites all responses to the specified domain.
2. Then define a list of zones using the standard format. For local zones, type master; for RPZ feed, type slave.
zone "badlist" {type master; file "master/badlist"; allow-query {none;}; };3. Define the zone (comments on the format in the text)
$TTL 1H
@ SOA LOCALHOST. named-mgr.example.com (1 1h 15m 30d 2h)
NS LOCALHOST.
; QNAME policy records. There are no periods (.) after the owner names.
nxdomain.domain.com CNAME . ; (.) - возврат NXDOMAIN
*.nxdomain.domain.com CNAME . ; (.) - возврат NXDOMAIN
nodata.domain.com CNAME *. ; (*.) - возврат NODATA
*.nodata.domain.com CNAME *. ; (*.) - возврат NODATA
bad.domain.com A 10.0.0.1 ; меняем ответ на нужный
AAAA 2001:2::1
bzone.domain.com CNAME garden.example.com.
ok.domain.com CNAME rpz-passthru. ; не делаем изменений
; меняем зону x.bzone.domain.com на x.bzone.domain.com.garden.example.com
*.bzone.domain.com CNAME *.garden.example.com.
; Правила блокировки по IP
8.0.0.0.127.rpz-ip CNAME .
32.1.0.0.127.rpz-ip CNAME rpz-passthru.
; Правила блокировки по имени и IP сервера доменов
ns.domain.com.rpz-nsdname CNAME .
48.zz.2.2001.rpz-nsip CNAME .
; Блокировка по IP клиента
112.zz.2001.rpz-client-ip CNAME rpz-drop.
8.0.0.0.127.rpz-client-ip CNAME rpz-drop.
; принуждение клиента запроса зон по TCP
16.0.0.1.10.rpz-client-ip CNAME rpz-tcp-only.
example.com CNAME rpz-tcp-only.
*.example.com CNAME rpz-tcp-only.
RZP is a convenient mechanism for increasing network security and restricting access to resources .
List of sources
- dnsrpz.info
- www.spamhaus.org/faq/section/ISP%2520Spam%2520Issues#164
- www.infosecurity.ru/cgi-bin/mart/arts.pl?a=101219
- www.bleepingcomputer.com/virus-removal/cryptolocker-ransomware-information
- www.infoblox.com/products/infrastructure-security/dns-firewall
- ftp.isc.org/isc/bind9/cur/9.10/doc/arm/Bv9ARM.ch06.html
- www.zytrax.com/books/dns/ch7/rpz.html
- www.zytrax.com/books/dns/ch9/rpz.html
Vadim Pavlov
UPD1:
Infoblox offers passive testing of DNS Firewall (RPZ) + Feed.
You can register and access this link: www.infoblox.com/catchmalware
Installation requires VmWare version 5.0 and higher and vCenter Server.
