Security Week 36: Telnet should be closed
 Telnet is a very old protocol. Wikipedia reports that it was developed in 1969, was actively used for many years for remote access to computers and servers, both under Unix / Linux and for Windows systems (telnet could be enabled in Windows NT and in Windows 2000) . The same Wikipedia reports that using Telnet has gradually faded away in favor of a more secure SSH protocol. And so it happened, apart from the millions of autonomous network devices — mostly routers and IP cameras that “respond” to this protocol, often without the knowledge of the owner.
Telnet is a very old protocol. Wikipedia reports that it was developed in 1969, was actively used for many years for remote access to computers and servers, both under Unix / Linux and for Windows systems (telnet could be enabled in Windows NT and in Windows 2000) . The same Wikipedia reports that using Telnet has gradually faded away in favor of a more secure SSH protocol. And so it happened, apart from the millions of autonomous network devices — mostly routers and IP cameras that “respond” to this protocol, often without the knowledge of the owner. Two weeks ago we discussed vulnerabilities in Mikrotik routers . But that vulnerability still has something to crack. Last week’s studyKaspersky Labs shows that the majority (three quarters) of all attacks on an IoT device are attacks on the Telnet protocol. If your device is responsible for this protocol, especially if it is available from the Internet - consider whether it is time to stop it. The only exception is: if you are Telving Star Wars .
Kaspersky Lab experts collected statistics in the traditional way - using hanipots. Actually, if you assemble a system that responds to port 23 via the Telnet protocol from any available hardware, connect it to the Internet directly and wait a couple of minutes, you will see login attempts using common default passwords. These previously infected systems are trying to expand the botnet by constantly scanning the Internet for new vulnerable devices. The hanipotes used for the research are a bit more complicated: they not only record the attempt to log in, but also record what exactly the attackers are trying to do after the “successful” penetration.
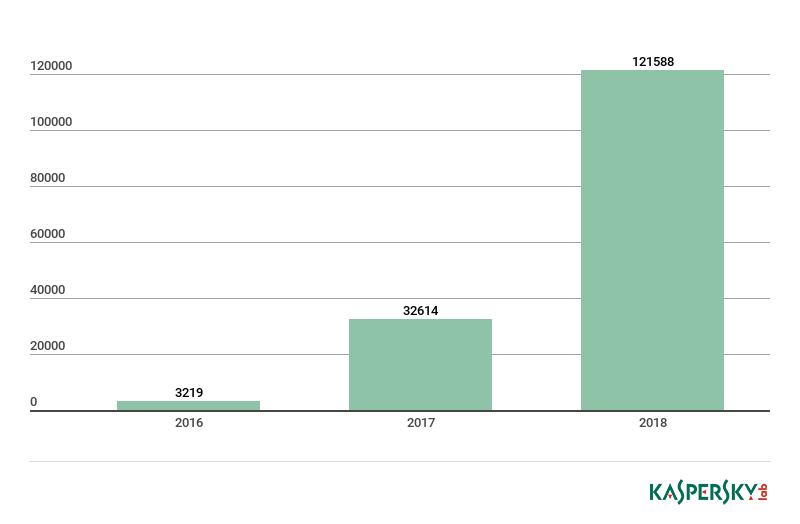
Here are some common numbers. The number of malware options for IoT devices is constantly growing: in the 7 months of this year, almost three times more modifications were recorded than in 2017. The most common attempts are to attack the Telnet protocol (75.40% of all attacks), in second place is SSH (11.59% - on it, it is also advisable to at least disable the login using a password, and even better, reassign the port). The rest (13.01%) is an attack on other protocols, such as the custom control interface of the same Mikrotik routers.
Every fifth attack resulted in the download of one of the malware variants for the Mirai botnet. Creators botnet already caught, but its source code was laid out in open access, so the capture of those responsible for the start of the epidemic in 2016 could not prevent further attacks. You can read more about Mirai here , but the picture below clearly shows what sets the login — the password the botnet is trying to expand.
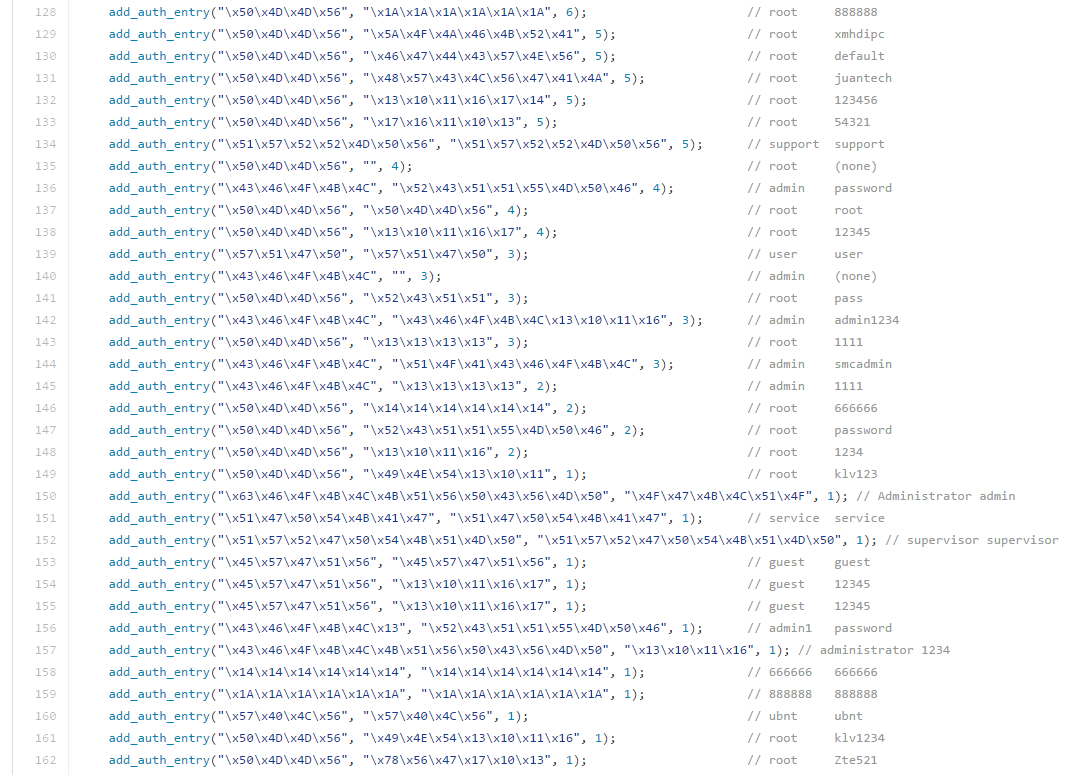
From these pairs it is possible to identify a vulnerable device: an IP camera, a set-top box, a digital video recorder, a network printer, and so on. There is a certain competition between the creators of botnets: hence the large number of requests to any devices that receive them via Telnet or SSH, and the tendency to change the password after a successful attack — otherwise the next one will try to install its monitoring software on the device.
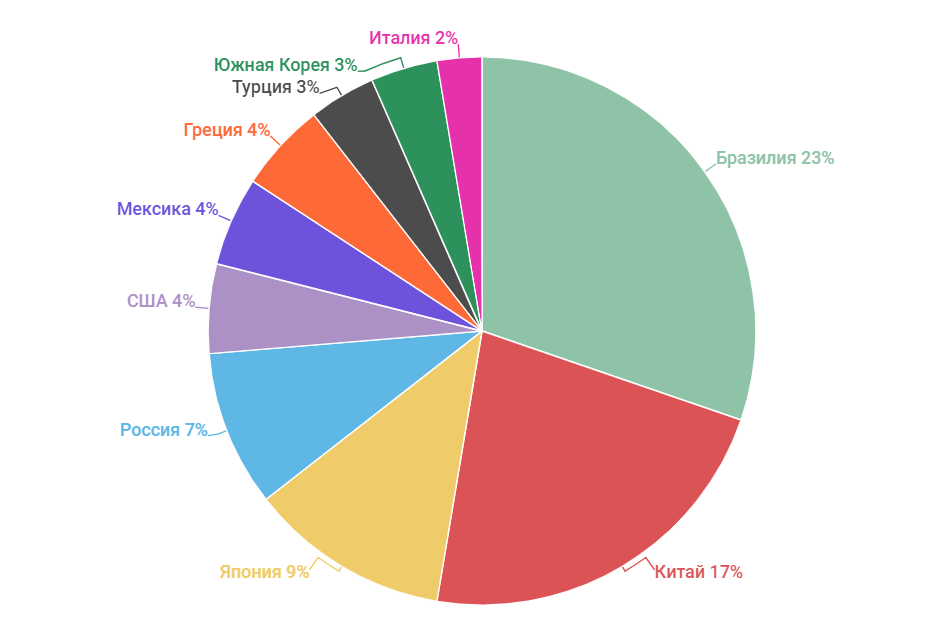
Country "attacking" are distributed like this. In the first place is Brazil, a country that has already been mentioned in the news about IoT botnets. A total of “hanipotes” recorded 12 million attacks with 86,560 unique IP addresses, another 27,000 IPs participated in the distribution of malware. Interestingly, the number of attacking IPs turned out to be much less than the total number of infected devices. There can be several explanations: finding infected devices behind NAT, using only a small part of a botnet for attacks, or something else. As is usually the case, tracing the actions of cybercriminals provides only part of the overall picture.
It is possible to estimate the power of a botnet when it is used as intended. In 2016, the power of attack on the DNS provider Dyn exceeded1 terabit per second, it was produced from more than 100 thousand devices controlled by the Mirai botnet. However, Kaspersky Lab experts rightly point out that the “paradise life” with millions of devices that are closed only with the default password will end with time. The next stage is still the exploitation of vulnerabilities in IoT devices, which does not require a default password. Such more complex attacks can conduct a botnet Reaper.
Here are some examples of vulnerabilities given: gaining full control over the D-Link 850L routers; IP cameras with “ direct access ” feature from outside by serial number with further password brutforsom; Video surveillance system with access to the simplest and easily fake cookies.
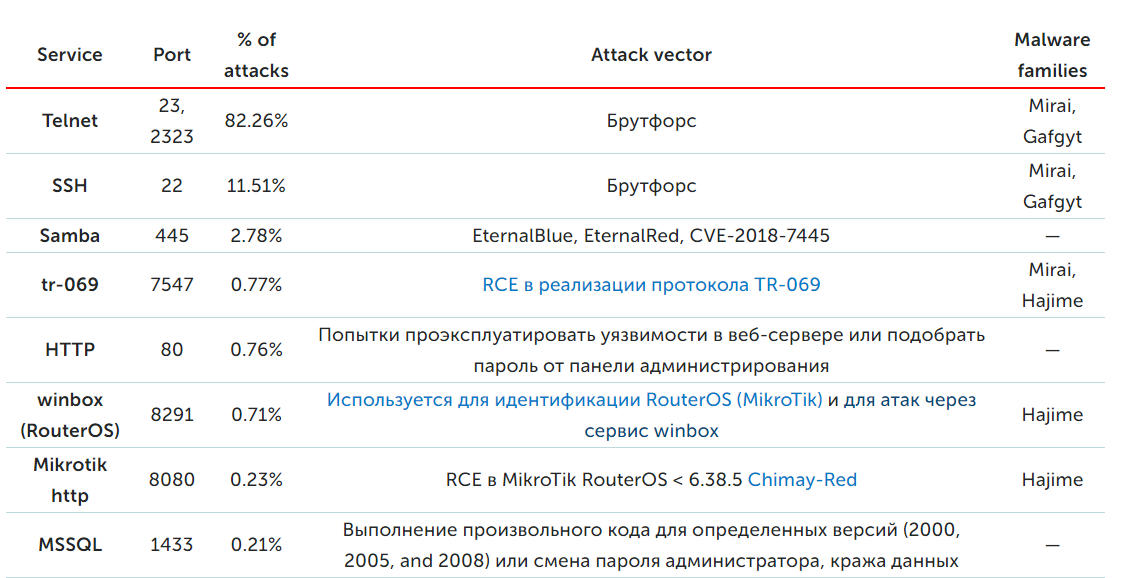
But this is all in the future, but for now the table above makes it clear that more than 90% of attacks on IoT are banal brute force. Vulnerabilities are not required yet . I will not even talk about specialized administration interfaces, but a lot has been written in the report and about them .
This is a complete lack of basic remedies. Twenty years ago, it was in the order of things to connect to the mail server using the unprotected POP3 protocol, to transfer passwords to the messenger server in clear text. The internet was young and naive. Now produce devices with such an attitude to security - well, if to put it very gently, short-sighted. What to do? First of all, do not make IoT devices accessible from the network. VPN all to help. Of course, this advice is useless for those who have an IP camera, but there is no idea what Telnet and VPN are.
Should we hope that manufacturers will gradually improve the security of IoT devices? This will not cancel the availability of millions of obviously vulnerable products in the network, which, unlike smartphones and laptops, have not been updated for years. And everything is so bad that the well-known cryptographer Bruce Schneier called for state regulation of the industry - well, to the fact that in relation to the actual cryptography is perceived in the bayonets. Are there any other ways? Not very clear.
Here is the latest news for you . Vulnerability found in routers WD My Cloud. I quote: “Since the implementation of the Western Digital network storage CGI interface allows cookies to be used for authentication, the attacker can submit an HTTP request during the session to execute any command, including the cookie string: username = admin”.

Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
