How and why to protect Internet access at the enterprise - part 2
In the first part I told why it is worth protecting Internet access and what technical solutions should be able to do. In the same I will tell you what is in the arsenal of Cisco and typical methods for solving the problem.
As a rule, the choice is made between the solutions of the classes “proxy server” and “new generation firewall”. There are also cloud scenarios, but we will touch them only in passing.
The most conservative and decades-proven way to solve the problem. A proxy server or literally "intermediary server" accepts requests from users, checks them for compliance with the policy and establishes a connection with the Internet resource on its own behalf. Typically, a proxy server is installed in the perimeter network (DMZ), and direct routed Internet access is denied.
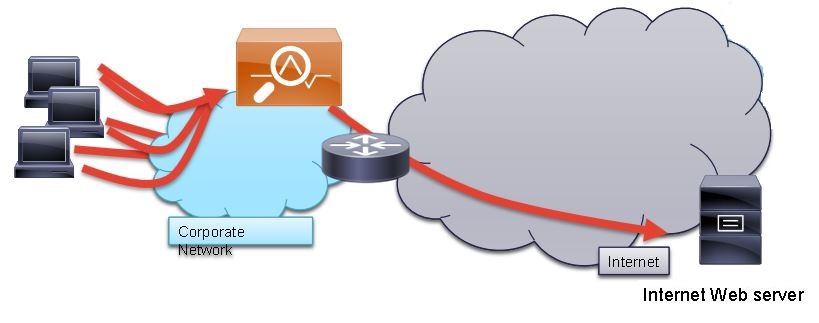
Naturally, user workstations are unaware of the existence of a proxy server. There are several ways to tell them about it:
All branches can be released through one proxy server, the main thing is that users can establish a TCP connection with it. If in each branch there is broadband Internet access, and the channels between the offices have pumped up, then it is better to install a proxy server in each branch and manage them centrally. In the case of WSA, licenses are acquired by the number of users, and WSA virtual machines are free, so they are easy and simple to deploy in each branch.
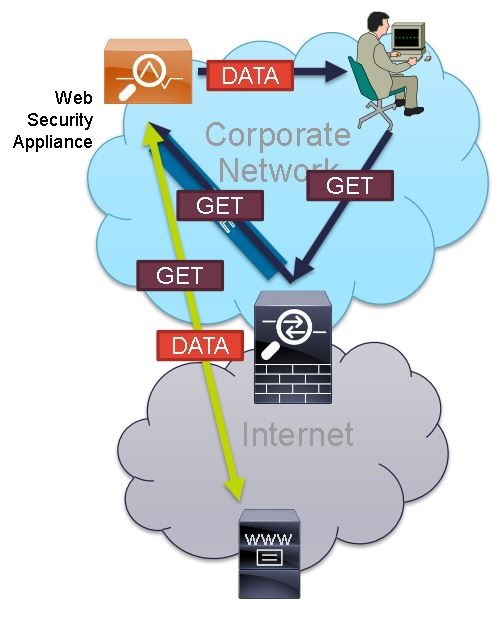
Of course, we all don’t like to configure anything on all workstations at once, and fortunately there is an implementation option with WCCP. WCCP is an open source traffic redirection protocol developed by Cisco. Using it, you can check all web traffic passing through a router, switch, or Cisco ASA, and the rest of the traffic will go as before. Minimum settings are made on network equipment, but nothing is configured on hosts. Below is a schematic of how WCCP works.
And now about the sad. Only direct-written applications are aware of the existence of proxy servers, and they pick up proxy server settings from the OS. If the application was written simply by hand, then in the application itself or its config, it is possible to explicitly set the proxy server. In all other cases, you have to "pick holes" in the firewalls and configure exceptions. The same thing has to be done if the application works on ports or protocols that the proxy server does not process, for WSA it is all but HTTP / S, FTP / S, SOCKS.
Of course, creating exceptions for ports or stations / users is a deplorable option that leads to unnecessary workload for staff and excessive access rights. There will be more incorrect applications than you expect, for example, bank clients, applications of your own design, server applications, applications for working with tax, pension funds, tender sites, partners, etc.
Custom applications must be managed with the next generation of firewalls. An alternative is the use of proxy servers of some manufacturers, which can be installed “in the gap” and which can route all traffic through themselves. The main disadvantage here is the addition of an additional point of failure in the infrastructure.
About NGFW and Sourcefire on Habré already wrote , so I will not repeat. NGFWs are installed in the gap, often instead of the old firewalls, and pass all traffic through themselves, understanding and controlling any protocols. No host configuration is required.
* Commercial break *
Remember that Sourcefire is the best NGIPS in the world with NGFW functionality. Sourcefire NGIPS / NGFW can be implemented as a separate FirePOWER device, or run as a software module on your existing Cisco ASA. ASA must be 5500-X series and have an SSD drive. The 5585-X will additionally require an SSP module replacement. ASA will work as usual, playing the role of a coarse filter, and Sourcefire will deal with the most intelligent tasks for already allowed connections.
Obviously, the functionality of the two solutions intersects, and you cannot immediately determine what you need.
If you are faced only with the task of complex filtering of Internet access and reducing the bill from the provider, then your choice is Cisco WSA.
If basic filtering is sufficient, there are many non-standard applications and it’s time to update your network security tools, then you should look towards Sourcefire NGIPS / NGFW.
The most correct option is to use both solutions.
It is usually chosen by the most demanding organizations and it looks like this:
The table below shows the key differences between the solutions and it will help you make your choice
This class of solutions has not yet gained popularity in Russia and is not a fact that it will ever gain. All traffic from users to Internet resources is encrypted and sent to the cloud service. After checking for compliance with policies, traffic is redirected to Internet resources and the requested data is returned to the user. This solution is easiest to consider as a Cisco WSA, located in the cloud and slightly limited in functionality.
As with traditional proxies, there are two options for redirecting users to the cloud service
Cloud solutions are most in demand in the retail, financial industries and any other geographically distributed companies or companies with a large number of mobile employees.
That's probably all for today. I would be grateful for the feedback and participation in the survey!
Stay tuned;)
How and why to protect Internet access at the enterprise - part 1
Overview of the new generation firewall and intrusion prevention systems SourceFire FirePower
What’s what in “NGFW | NGIPS | UTM ” and UTM vs. NGFW - One Shade of Gray
As a rule, the choice is made between the solutions of the classes “proxy server” and “new generation firewall”. There are also cloud scenarios, but we will touch them only in passing.
Proxies - Cisco Web Security Appliance (WSA)
The most conservative and decades-proven way to solve the problem. A proxy server or literally "intermediary server" accepts requests from users, checks them for compliance with the policy and establishes a connection with the Internet resource on its own behalf. Typically, a proxy server is installed in the perimeter network (DMZ), and direct routed Internet access is denied.
Naturally, user workstations are unaware of the existence of a proxy server. There are several ways to tell them about it:
- Auto-tuning script in the form of a PAC-file placed on a server in a local network. The server address is advertised via DHCP. This option is simple and works even at stations not in the domain. The same simplicity also ruins it - there are several attacks with server spoofing that allow directing user traffic through the attacker
- Changing registry keys on each host - can be done using domain policies, centralized management tools, or manually
All branches can be released through one proxy server, the main thing is that users can establish a TCP connection with it. If in each branch there is broadband Internet access, and the channels between the offices have pumped up, then it is better to install a proxy server in each branch and manage them centrally. In the case of WSA, licenses are acquired by the number of users, and WSA virtual machines are free, so they are easy and simple to deploy in each branch.
Of course, we all don’t like to configure anything on all workstations at once, and fortunately there is an implementation option with WCCP. WCCP is an open source traffic redirection protocol developed by Cisco. Using it, you can check all web traffic passing through a router, switch, or Cisco ASA, and the rest of the traffic will go as before. Minimum settings are made on network equipment, but nothing is configured on hosts. Below is a schematic of how WCCP works.
And now about the sad. Only direct-written applications are aware of the existence of proxy servers, and they pick up proxy server settings from the OS. If the application was written simply by hand, then in the application itself or its config, it is possible to explicitly set the proxy server. In all other cases, you have to "pick holes" in the firewalls and configure exceptions. The same thing has to be done if the application works on ports or protocols that the proxy server does not process, for WSA it is all but HTTP / S, FTP / S, SOCKS.
Of course, creating exceptions for ports or stations / users is a deplorable option that leads to unnecessary workload for staff and excessive access rights. There will be more incorrect applications than you expect, for example, bank clients, applications of your own design, server applications, applications for working with tax, pension funds, tender sites, partners, etc.
Custom applications must be managed with the next generation of firewalls. An alternative is the use of proxy servers of some manufacturers, which can be installed “in the gap” and which can route all traffic through themselves. The main disadvantage here is the addition of an additional point of failure in the infrastructure.
Next Generation Firewalls - Cisco Sourcefire NGFW
About NGFW and Sourcefire on Habré already wrote , so I will not repeat. NGFWs are installed in the gap, often instead of the old firewalls, and pass all traffic through themselves, understanding and controlling any protocols. No host configuration is required.
* Commercial break *
Remember that Sourcefire is the best NGIPS in the world with NGFW functionality. Sourcefire NGIPS / NGFW can be implemented as a separate FirePOWER device, or run as a software module on your existing Cisco ASA. ASA must be 5500-X series and have an SSD drive. The 5585-X will additionally require an SSP module replacement. ASA will work as usual, playing the role of a coarse filter, and Sourcefire will deal with the most intelligent tasks for already allowed connections.
Proxy or NGFW - what to choose?
Obviously, the functionality of the two solutions intersects, and you cannot immediately determine what you need.
If you are faced only with the task of complex filtering of Internet access and reducing the bill from the provider, then your choice is Cisco WSA.
If basic filtering is sufficient, there are many non-standard applications and it’s time to update your network security tools, then you should look towards Sourcefire NGIPS / NGFW.
The most correct option is to use both solutions.
особенно с точки зрения выполнения моей квоты It is usually chosen by the most demanding organizations and it looks like this:
- NGIPS / NGFW is installed in the core of the network or on the perimeter, which filters user access by groups in AD, protocols, applications, etc.
- Allowed web traffic is redirected via WCCP to Cisco WSA, which decrypts SSL traffic, caches requests, transfers individual files to the DLP system, scans antivirus attachments, and much more
- Since NGFW performs pre-filtering, the load on the WSA is significantly reduced and you can deploy it as a VM. In turn, NGFW is freed from the tasks of URL filtering and intercepting SSL traffic, which allows you to save on licenses and choose a model with lower performance
The table below shows the key differences between the solutions and it will help you make your choice
| WSA | NGFW | |
|---|---|---|
| URL Filtering | + | + |
| Reputation Filtering | + | + |
| Access Control by AD Group and Application | + | + |
| Data caching | + | - |
| Quoting traffic by time and volume | + | - |
| Intrusion detection system | Zombie Detection Only | + Industry Leader |
| Scanning downloaded files with anti-virus engines | + Webroot, Sophos, McAfee | - |
| Protocol support | HTTP / S, FTP / S, SOCKS | Any |
| Ability to create custom profiles for applications | - | + OpenAppID |
| AMP - protection against zero-day vulnerabilities | + | + |
| Interception and verification of SSL traffic | + | On a separate device In the near future on-box decryption |
| Export files using ICAP | + | - |
| Availability as VM | + | + |
| Centralized management | + | + |
Cloud Solutions - Cisco Cloud Web Security (CWS)
This class of solutions has not yet gained popularity in Russia and is not a fact that it will ever gain. All traffic from users to Internet resources is encrypted and sent to the cloud service. After checking for compliance with policies, traffic is redirected to Internet resources and the requested data is returned to the user. This solution is easiest to consider as a Cisco WSA, located in the cloud and slightly limited in functionality.
As with traditional proxies, there are two options for redirecting users to the cloud service
- “Hosted” - registry settings are made on the hosts or an agent is installed or Cisco Anyconnect is used
- WCCP-like — Agent on Cisco routers or Cisco ASA firewalls redirects all web traffic to CWS
Cloud solutions are most in demand in the retail, financial industries and any other geographically distributed companies or companies with a large number of mobile employees.
That's probably all for today. I would be grateful for the feedback and participation in the survey!
Stay tuned;)
How and why to protect Internet access at the enterprise - part 1
Overview of the new generation firewall and intrusion prevention systems SourceFire FirePower
What’s what in “NGFW | NGIPS | UTM ” and UTM vs. NGFW - One Shade of Gray
Only registered users can participate in the survey. Please come in.
What topic would you like to see in the next article?
- 69.5% • Authentication and authorization of users to access the Internet - AD, ISE, passive and active web forms, NTLM 103
- 49.3% • Checking domain membership, antivirus and OS updates before giving the user access to the Internet 73
- 41.2% • Difficulties in protecting the web traffic of virtual workstations (VDI), tablets and smartphones, workstations with shift workers 61
