Internet Explorer will block obsolete ActiveX controls
The team of developers of the web browser Internet Explorer has announced another security feature called Out-of-date ActiveX control blocking , which will help users protect themselves from drive-by download attacks. This is an additional security option for browser versions 8-11 on Windows 7 SP1 +, which will block out-of-date (deprecated) IE plugins (using the ActiveX environment). From the point of view of safety, the function belongs to the type of so-called. explot mitigation and will protect against 1day exploits used by cybercriminals to automatically install malware through exploit kits. The new security setting will appear in the browser with the following patch tuesday, i.e. August 12th.

A similar feature is included with EMET 5.0 and is calledAttack Surface Reduction (ASR) . ASR allows you to block the browser from playing Flash Player or Java content for untrusted IE zones, that is, for the Internet zone. The new IE Out-of-date ActiveX control blocking security setting works on a similar principle, but does not completely prohibit the use of potentially unsafe browser plug-ins (see the ASR link), but only those for which a new version has already been released. Internet Explorer Playable Content, such as Java Plugins or Flash Player, Use ActiveXsince it is regulated by Microsoft to embed relevant content in a web page and successfully play it in IE. Depending on which version of the application requires playback content, the browser, based on the new option, decides whether or not to give the user a warning.
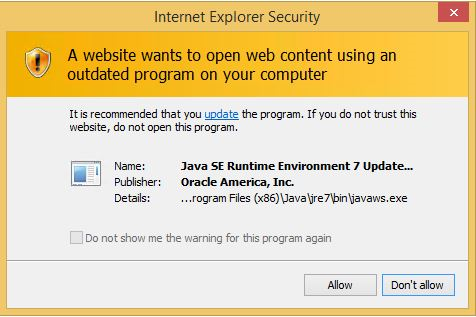
Fig. This will look like a warning that the content being played requires an application version that is already outdated. Screenshot taken from MS post .
IE developers clarify that while it comes to blocking outdated versions of Oracle Java software. To do this, the system file versionlist.xml will be used, in which versions of plugins or software will be added as necessary (most likely we are talking about Flash Player). In addition, to ensure compatibility with corporate users, the new security feature will not block legacy ActiveX controls for corporate Intranet Zone and Trusted Sites Zone.
Earlier, we wrote that in June and July, Microsoft released updates MS14-035 and MS14-037 , which introduced additional security options from vulnerabilities like use-after-free (UAF).

be secure.

A similar feature is included with EMET 5.0 and is calledAttack Surface Reduction (ASR) . ASR allows you to block the browser from playing Flash Player or Java content for untrusted IE zones, that is, for the Internet zone. The new IE Out-of-date ActiveX control blocking security setting works on a similar principle, but does not completely prohibit the use of potentially unsafe browser plug-ins (see the ASR link), but only those for which a new version has already been released. Internet Explorer Playable Content, such as Java Plugins or Flash Player, Use ActiveXsince it is regulated by Microsoft to embed relevant content in a web page and successfully play it in IE. Depending on which version of the application requires playback content, the browser, based on the new option, decides whether or not to give the user a warning.

Fig. This will look like a warning that the content being played requires an application version that is already outdated. Screenshot taken from MS post .
IE developers clarify that while it comes to blocking outdated versions of Oracle Java software. To do this, the system file versionlist.xml will be used, in which versions of plugins or software will be added as necessary (most likely we are talking about Flash Player). In addition, to ensure compatibility with corporate users, the new security feature will not block legacy ActiveX controls for corporate Intranet Zone and Trusted Sites Zone.
Earlier, we wrote that in June and July, Microsoft released updates MS14-035 and MS14-037 , which introduced additional security options from vulnerabilities like use-after-free (UAF).

be secure.
